sus
Overview
- Overall difficulty for me (From 1-10 stars): ★★★★★★☆☆☆☆
Something about this audio is pretty sus…
Author: gsemaj
Difficulty: Easy
Find the flag
In this challenge, we can download a file:
┌──(root🌸siunam)-[~/ctf/BuckeyeCTF-2022/Misc/sus]
└─# file sus.wav
sus.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 48000 Hz
Hmm… A sound file.
Let's fire up Audacity to find anything weird:
┌──(root🌸siunam)-[~/ctf/BuckeyeCTF-2022/Misc/sus]
└─# audacity sus.wav
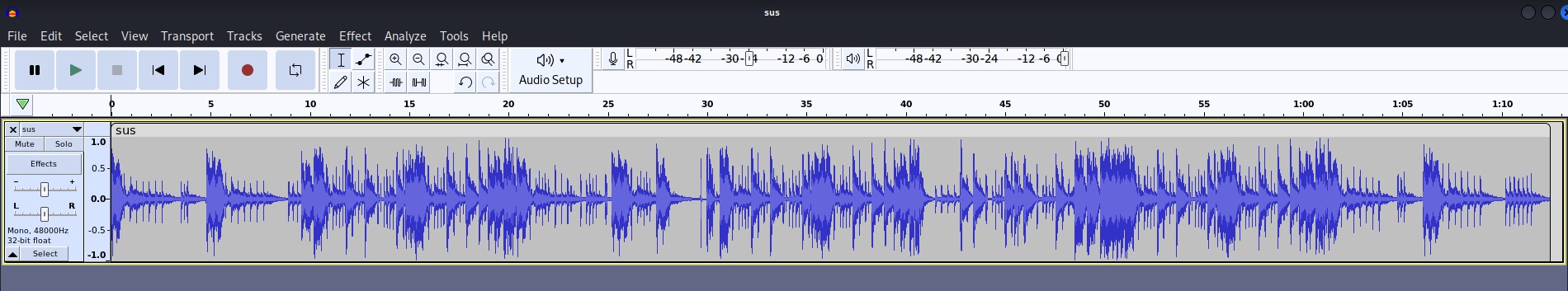
Nothing weird here. Let's switch to Spectrogram mode:
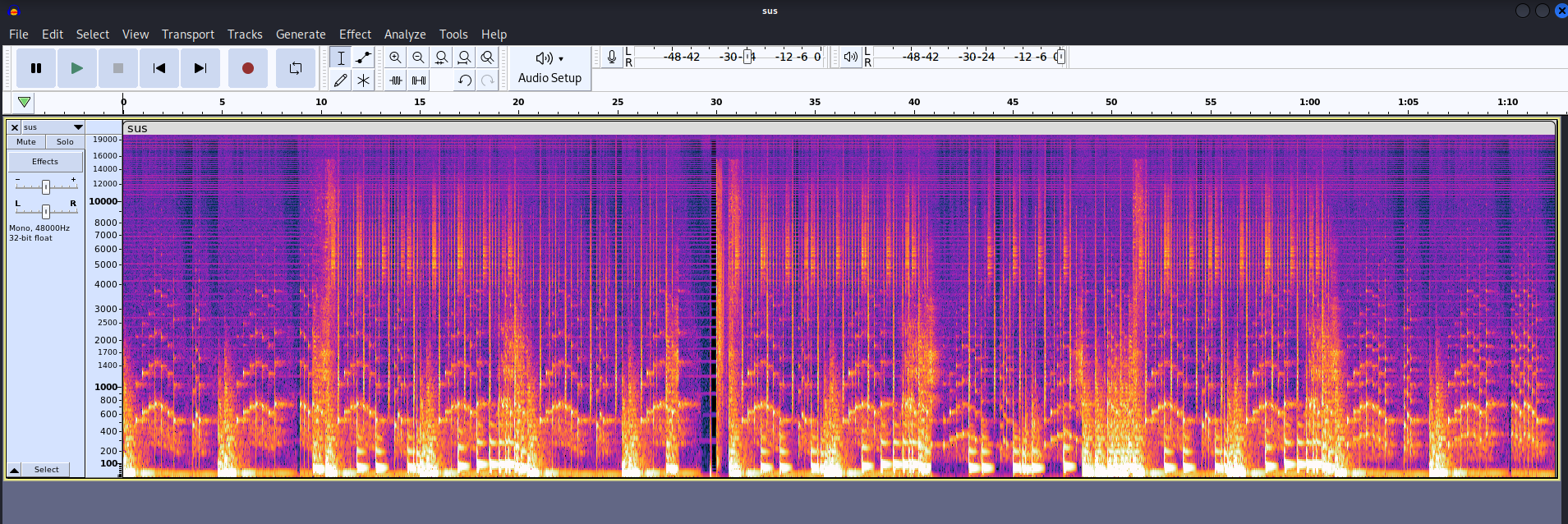
Still no dice.
Then, after I banging my head against the wall, I googled about audio steganography:
Let's look at this Medium blog!
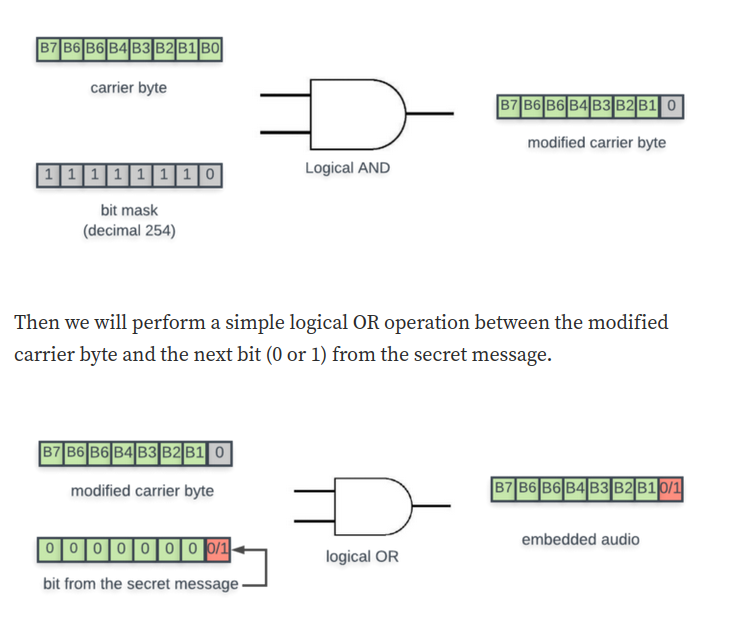
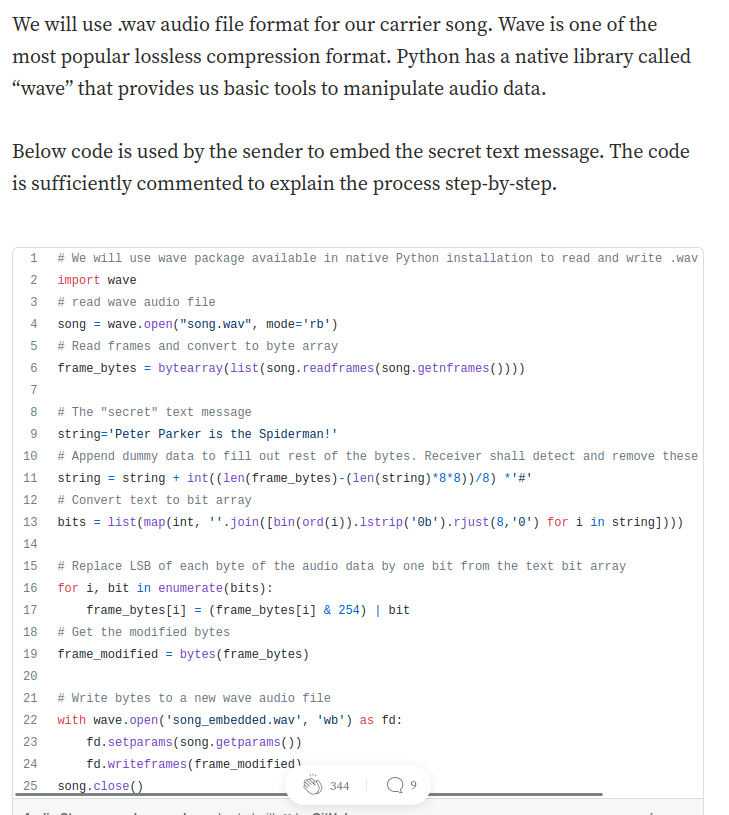
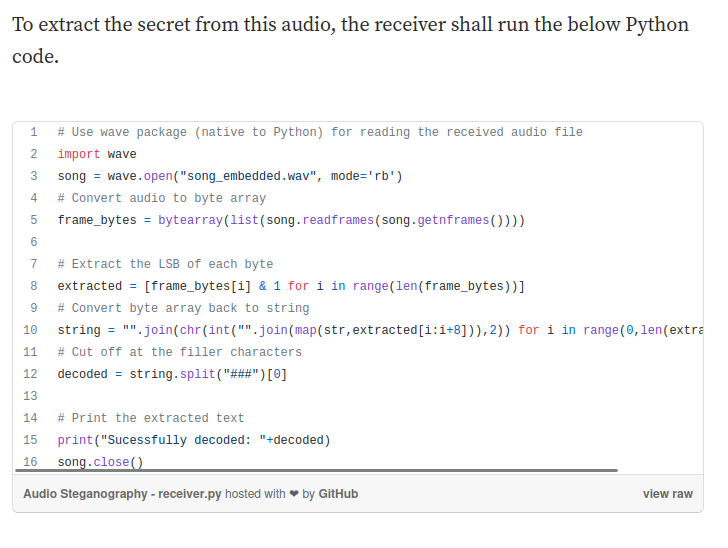
Hmm… Using LSB algorithm to hide hidden messages??
Let's copy and paste that receiver.py to our attacker machine!
#!/usr/bin/env python3
import wave
song = wave.open("sus.wav", mode='rb')
# Convert audio to byte array
frame_bytes = bytearray(list(song.readframes(song.getnframes())))
# Extract the LSB of each byte
extracted = [frame_bytes[i] & 1 for i in range(len(frame_bytes))]
# Convert byte array back to string
string = "".join(chr(int("".join(map(str,extracted[i:i+8])),2)) for i in range(0,len(extracted),8))
# Cut off at the filler characters
decoded = string.split("###")[0]
# Print the extracted text
print("Sucessfully decoded: "+decoded)
song.close()
Run that script!
┌──(root🌸siunam)-[~/ctf/BuckeyeCTF-2022/Misc/sus]
└─# python3 solve.py
Sucessfully decoded: buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}buckeye{4y000_p1nk_100k1n_k1nd4_5u5_th0}[...]
We got the flag!
Conclusion
What we've learned:
- Audio Steganography