Calc
Overview
- Overall difficulty for me: Medium
In this challenge, we can start a docker instance:
Find the flag
Home page:
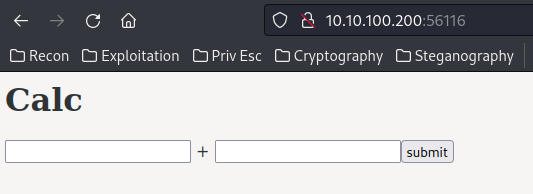
As you can see, we can do calcalation in here.
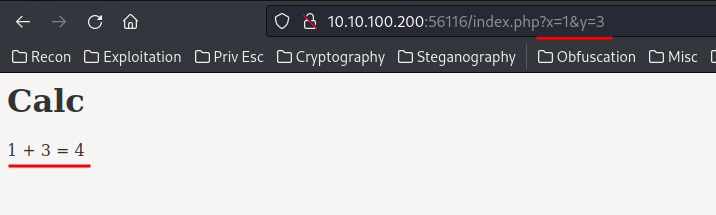
Hmm… Looks like we can do something weird to the GET parameter?
Maybe it’s vulnerable to command injection??
According to HackTricks, we can use this payload:
ls %0A id # %0A Execute both (RECOMMENDED)
Note:
%0Ameans new line character in URL encoding.
Let’s test this payload!
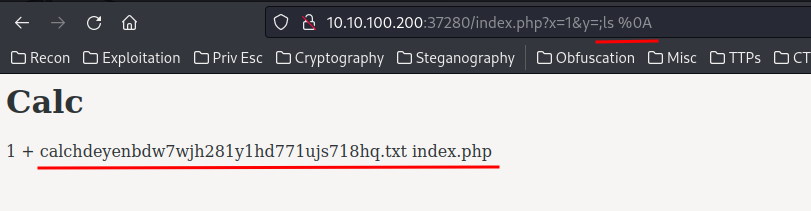
It works!
The calchdeyenbdw7wjh281y1hd771ujs718hq.txt file looks weird to me, let’s cat that file:
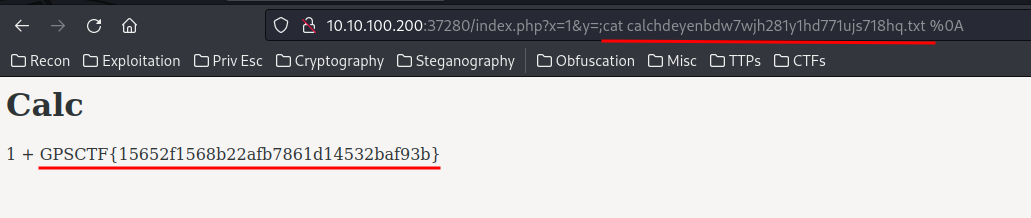
We found the flag!
Conclusion
What we’ve learned:
- Exploiting Command Injection