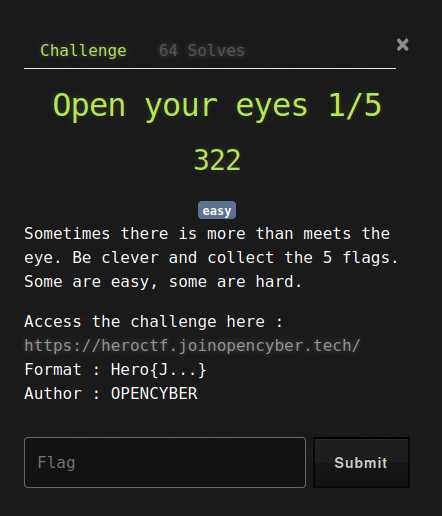
Open your eyes 1/5
Table of Contents
Overview
- 74 solves / 261 points
- Difficulty: Easy
- Overall difficulty for me (From 1-10 stars): ★★☆☆☆☆☆☆☆☆
Background
Sometimes there is more than meets the eye. Be clever and collect the 5 flags. Some are easy, some are hard.
Access the challenge here : https://heroctf.joinopencyber.tech/
Format : Hero{J…}
Author : OPENCYBER
Find the flag
In this challenge, we can access the challenge machine in https://heroctf.joinopencyber.tech/:
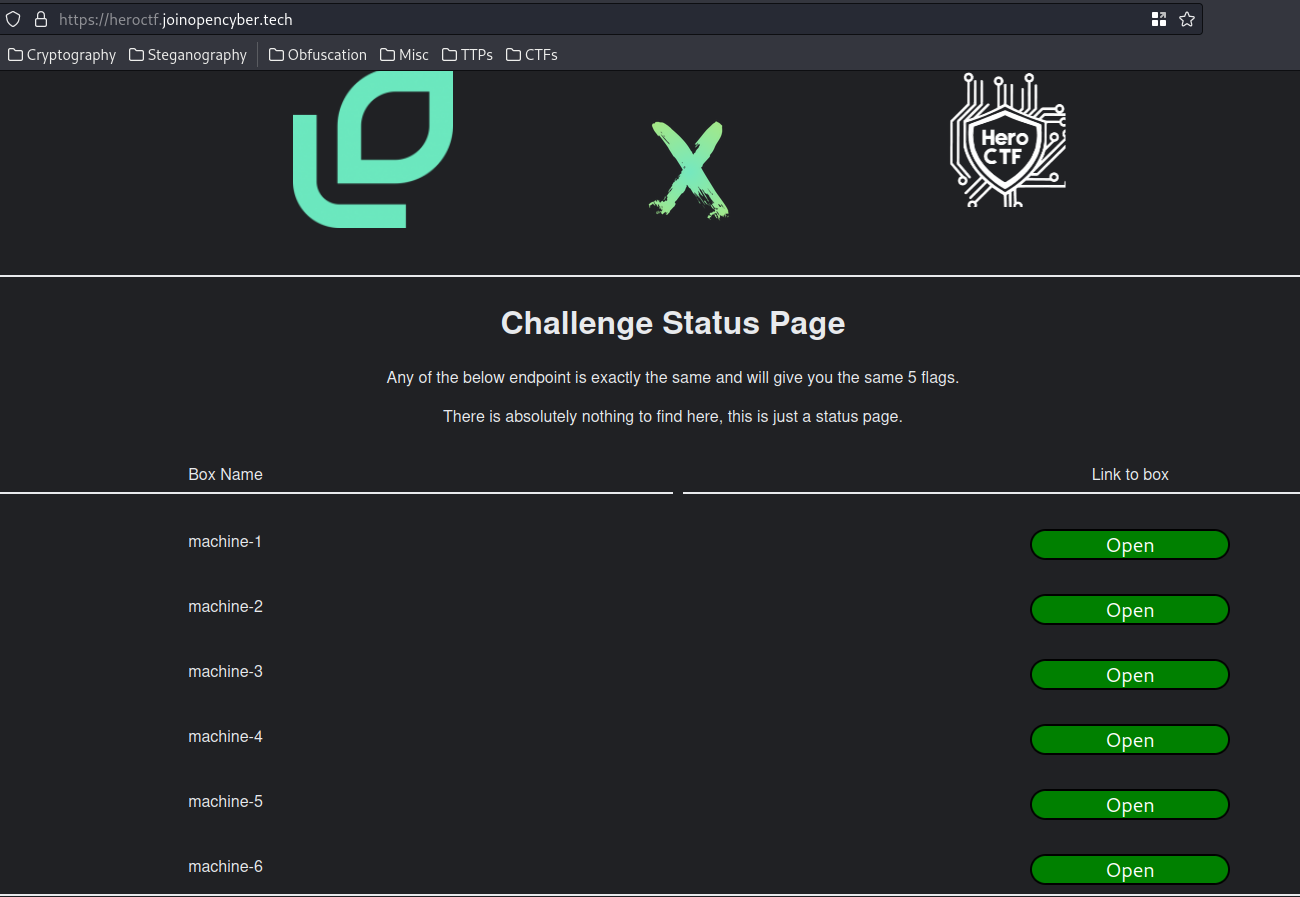
Home page:
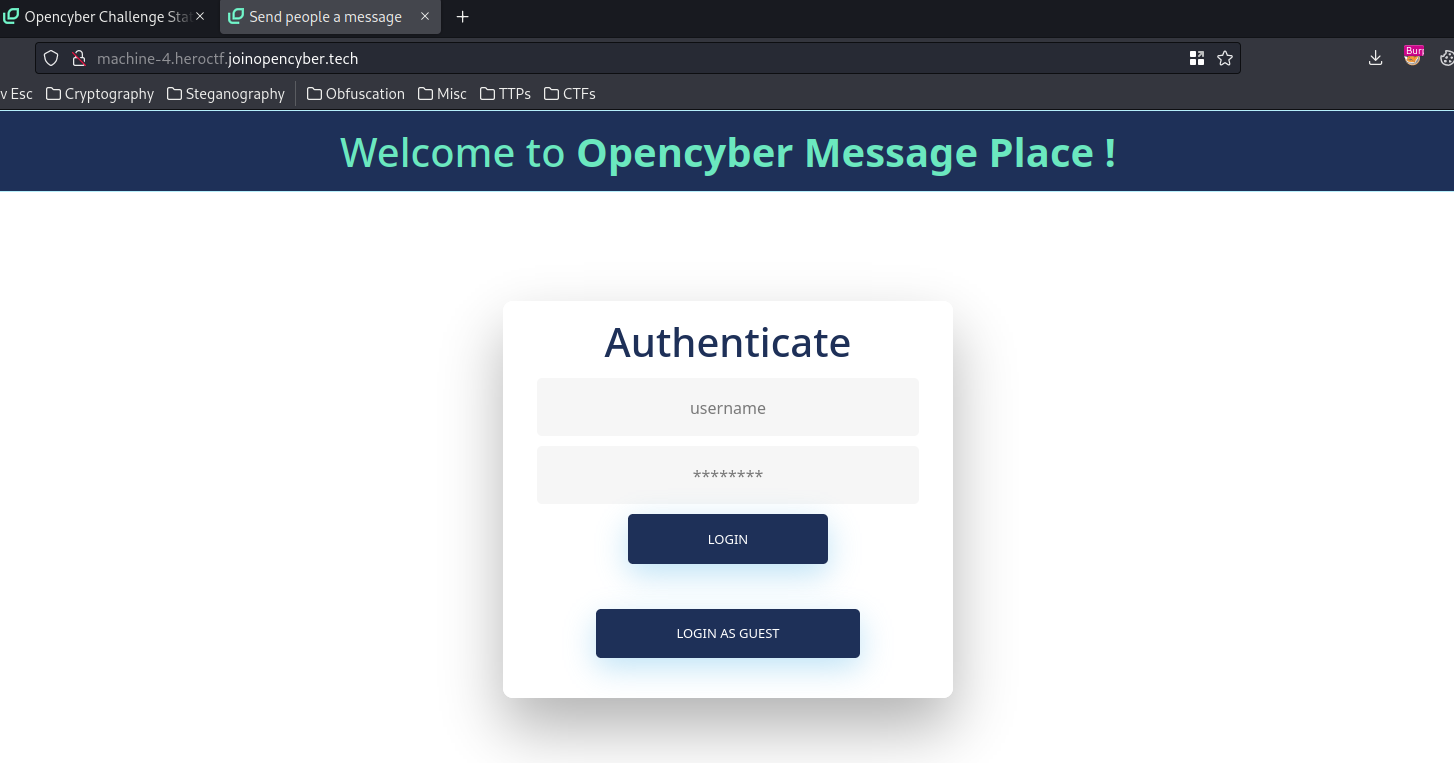
In here, we can “LOGIN AS A GUEST” or “LOGIN”.
Let’s login as a guest first:
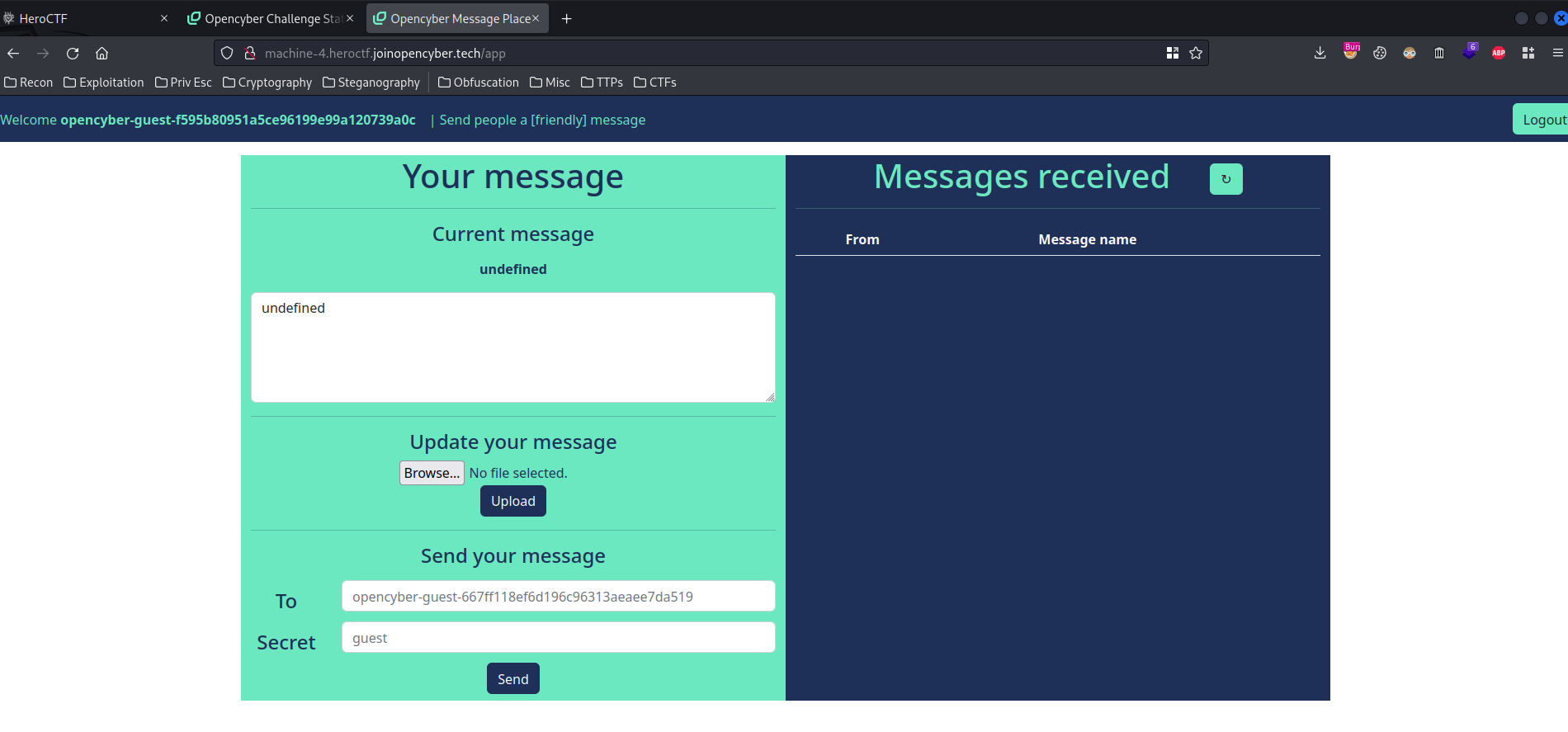
In here, we can send some messages to someone.
Since JavaScript is a client-side language, we can poke around in the source code.
To do so, I’ll open up the “Debugger” tab:
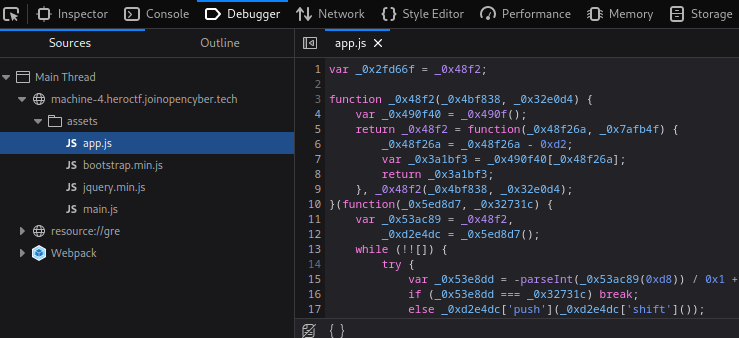
As you can see, it has 2 main JavaScript files: app.js, main.js.
But before we look at the main.js, I found something weird in app.js:
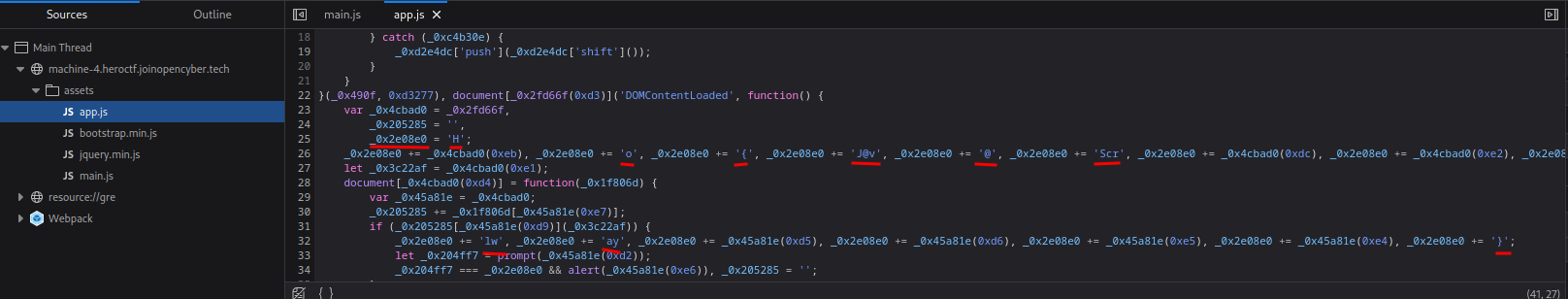
Hmm… I can see the flag format! (Hero{.*})
Now, we can dynamically deobfuscate those JavaScript code!
Note: You can read my recent “PwnMe Qualifications : “8 bits””’s web challenge writeup: Beat me!. It’s a web challenge that exploiting client-side game and dynamically deobfuscating JavaScript code.
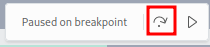
That being said, let’s add a breakpoint to variable _0x2e08e0:
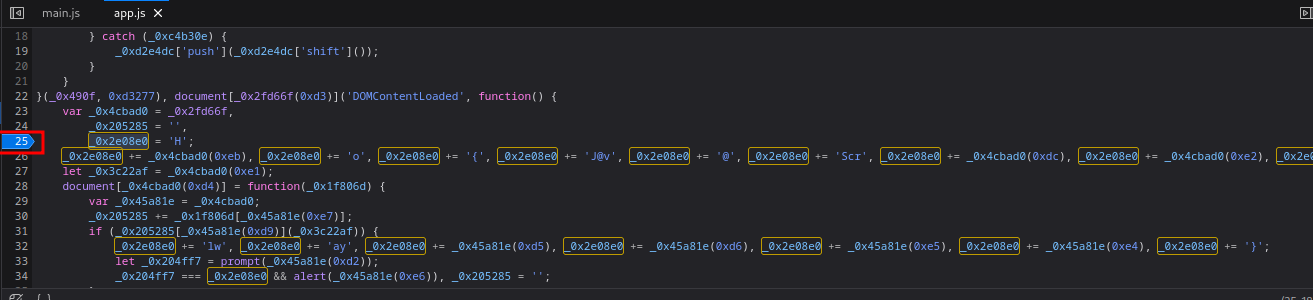
Then refresh the page:
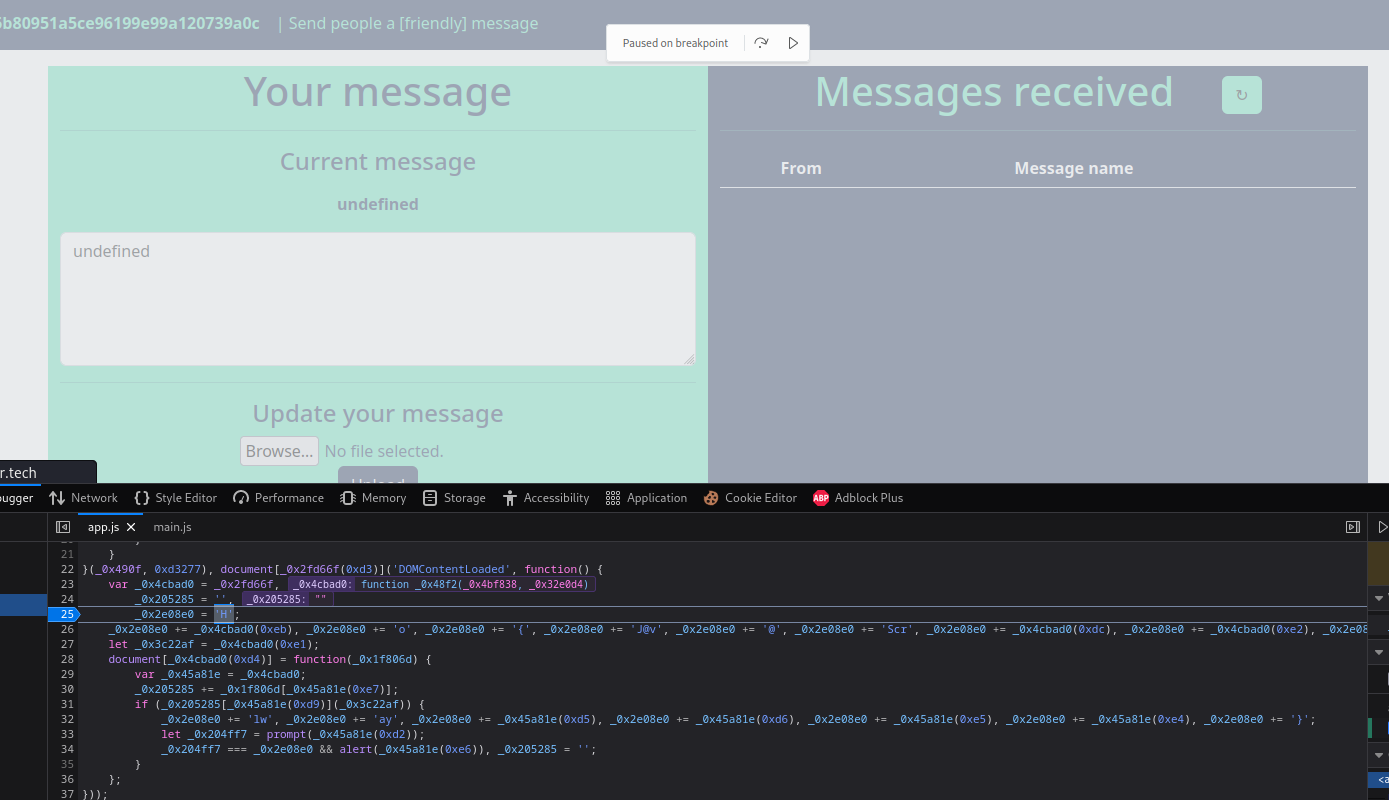
Next, click the “Step Over” button twice:
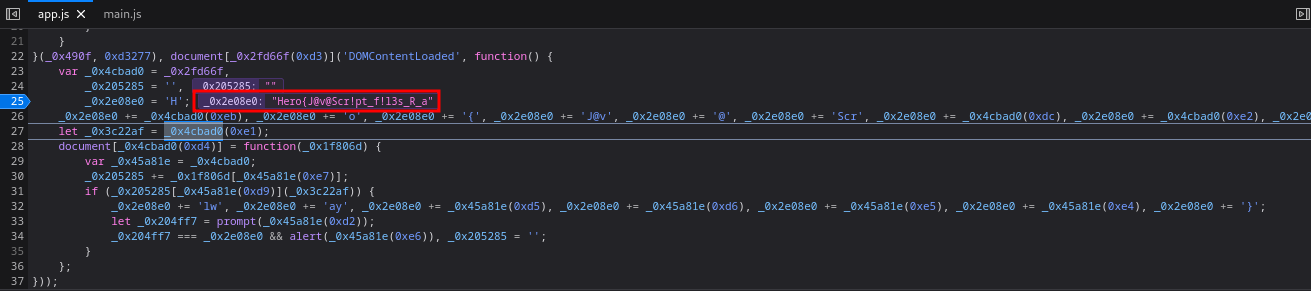
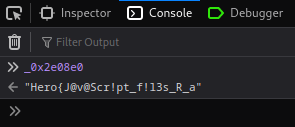
Nice! We found half of the flag:
However, we can’t step over again, as the if statement in line 31 won’t get passed.
If you look closely, variable _0x45a81e is function _0x4cbad0():
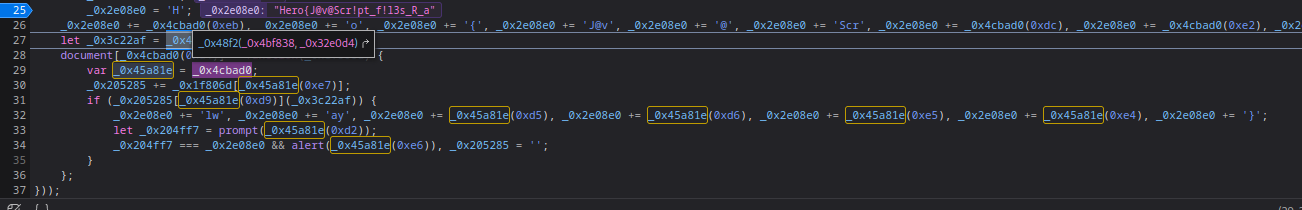
So, we can concatenate the full flag via variable _0x45a81e!
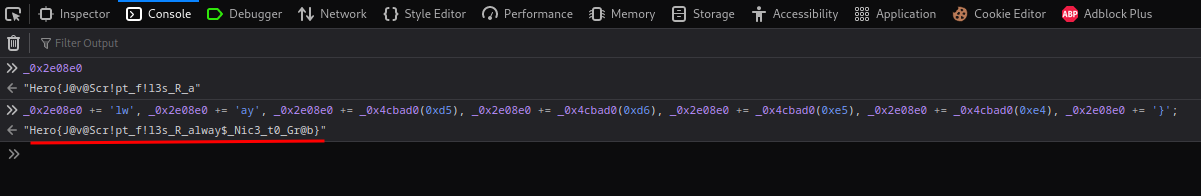
- Flag:
Hero{J@v@Scr!pt_f!l3s_R_alway$_Nic3_t0_Gr@b}
Conclusion
What we’ve learned:
- Dynamically Deobfuscating JavaScript Code