kNOCk kNOCk
Table of Contents
Overview
- 198 solves / 50 points
- Difficulty: Intro
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Author: Braguette#0169
We have to monitor our network every day to make sure our admins don't help players get out of the game.
We are sending you a suspicious capture. Do your job !
Find the flag
In this challenge, we can download a file:
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|13:46:34(HKT)]
└> file Intro.pcapng
Intro.pcapng: pcapng capture file - version 1.0
It's a pcap (Packet capture) file! Let's open it via WireShark:
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|13:46:40(HKT)]
└> wireshark Intro.pcapng
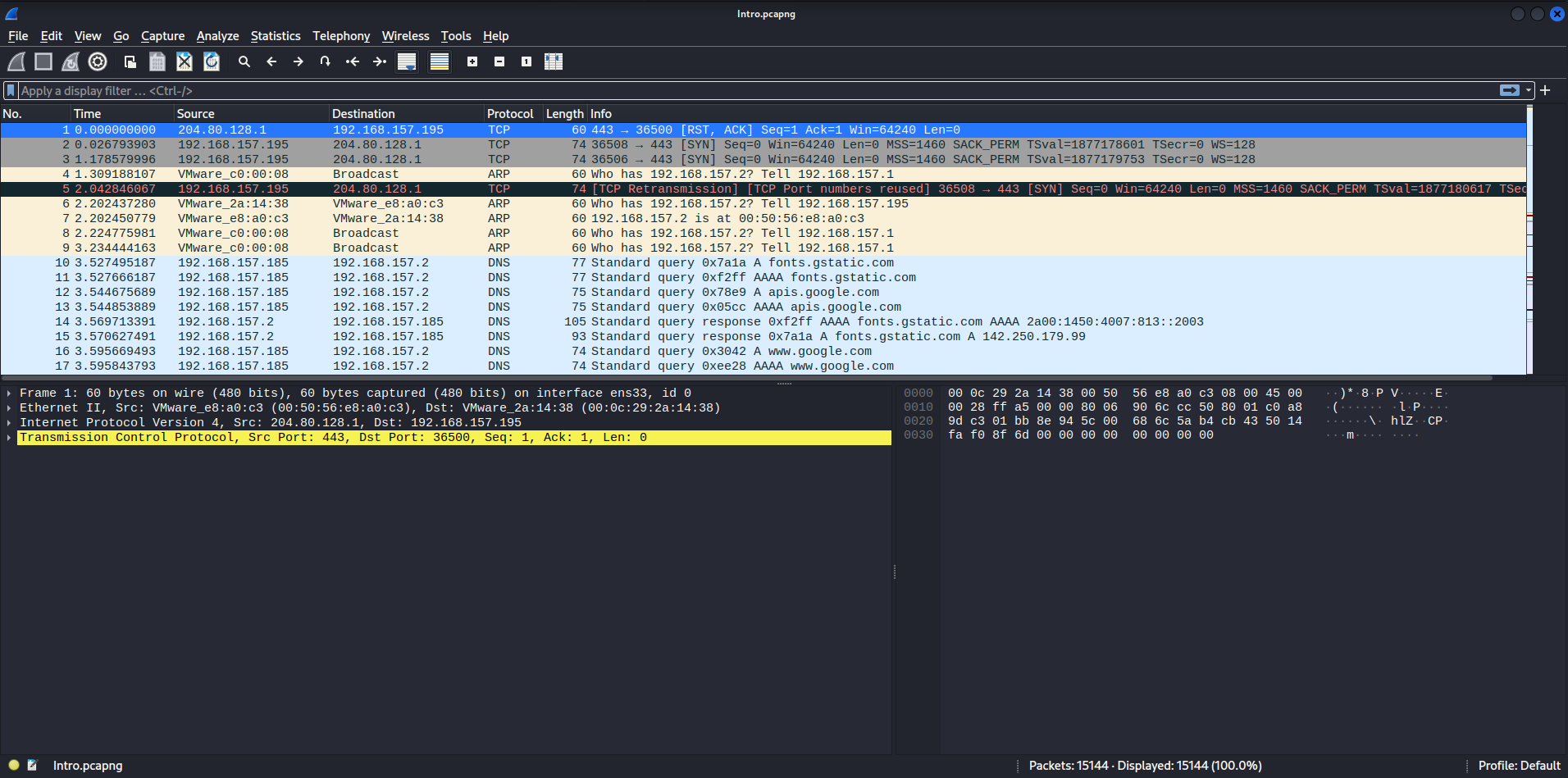
We can see that there are 15144 packets.
In "Statistics" -> "Protocol Hierarchy", we can see different protocols has been captured in this pcap file:
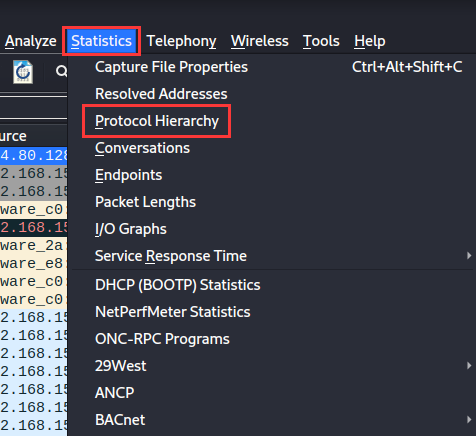

In TCP protocol, there are 6 HTTP packets, and the "Media Type" is interesting to us.
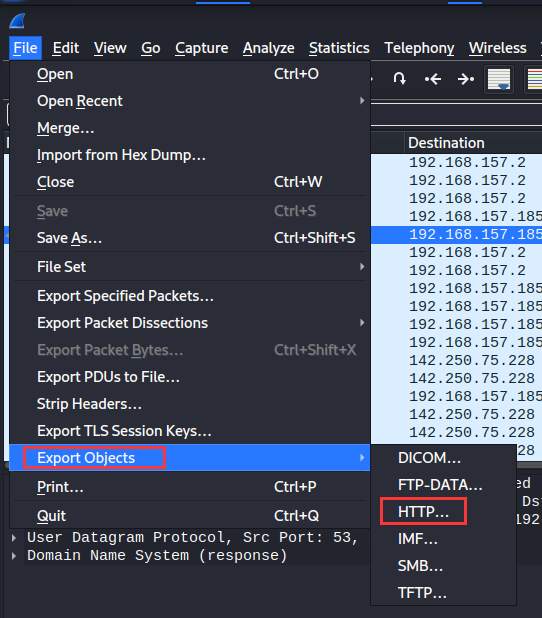
We can export that object:
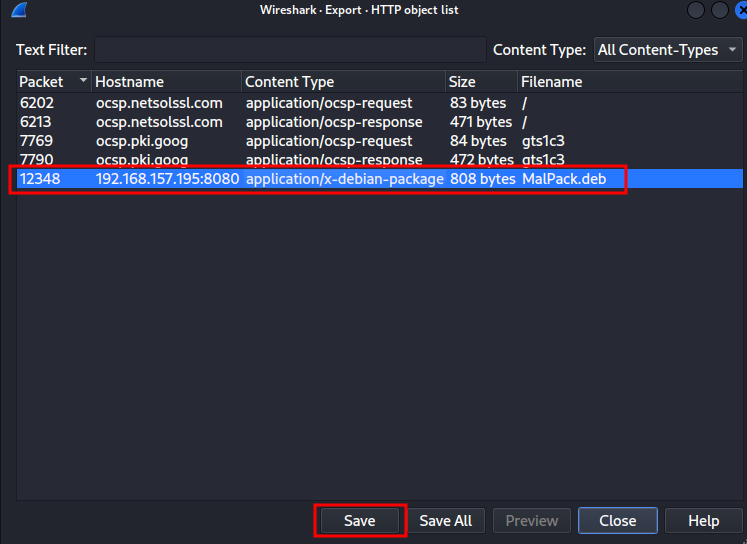
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|13:52:11(HKT)]
└> file MalPack.deb
MalPack.deb: Debian binary package (format 2.0), with control.tar.xz, data compression xz
As you can see, the MalPack.deb is a Debian package.
Hmm… That looks very, very sussy!
Let's view it's contents without extracting it:
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|13:57:06(HKT)]
└> dpkg -c MalPack.deb
drwxrwxr-x remnux/remnux 0 2023-04-13 18:50 ./
drwxrwxr-x remnux/remnux 0 2023-04-13 18:50 ./usr/
drwxrwxr-x remnux/remnux 0 2023-04-13 18:50 ./usr/local/
drwxrwxr-x remnux/remnux 0 2023-04-13 21:16 ./usr/local/bin/
-rwxrwxr-x remnux/remnux 46 2023-04-13 21:16 ./usr/local/bin/simplescript.sh
simplescript.sh… Let's take a look at that script by extracting the package!
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|14:00:02(HKT)]
└> dpkg-deb -xv MalPack.deb .
./
./usr/
./usr/local/
./usr/local/bin/
./usr/local/bin/simplescript.sh
┌[siunam♥earth]-(~/ctf/PwnMe-2023-8-bits/Forensics/kNOCk-kNOCk)-[2023.05.06|14:00:24(HKT)]
└> cat usr/local/bin/simplescript.sh
#!/bin/bash
echo "PWNME{P4ck4g3_1s_g00d_ID}"
Bam! We got the flag!
- Flag:
PWNME{P4ck4g3_1s_g00d_ID}
Conclusion
What we've learned:
- Exporting HTTP Object & Inspecting Debian Package