Web of Lies
-
98 Points / 79 Solves
-
Overall difficulty for me (From 1-10 stars): ★★★★★★★★★☆
Background
We found more weird traffic. We’re concerned he’s connected to a web of underground criminals.
Find the flag
In this challenge, we can download a file:
┌[siunam♥earth]-(~/ctf/RITSEC-CTF-2023/Forensics/Web-of-Lies)-[2023.04.02|13:34:41(HKT)]
└> file weboflies.pcapng
weboflies.pcapng: pcapng capture file - version 1.0
It’s a packet capture file!
We can open it via WireShark:
┌[siunam♥earth]-(~/ctf/RITSEC-CTF-2023/Forensics/Web-of-Lies)-[2023.04.02|13:34:42(HKT)]
└> wireshark weboflies.pcapng

In “Statistcs” -> “Protocol Hierarchy”, we can view which protocol is being captured:
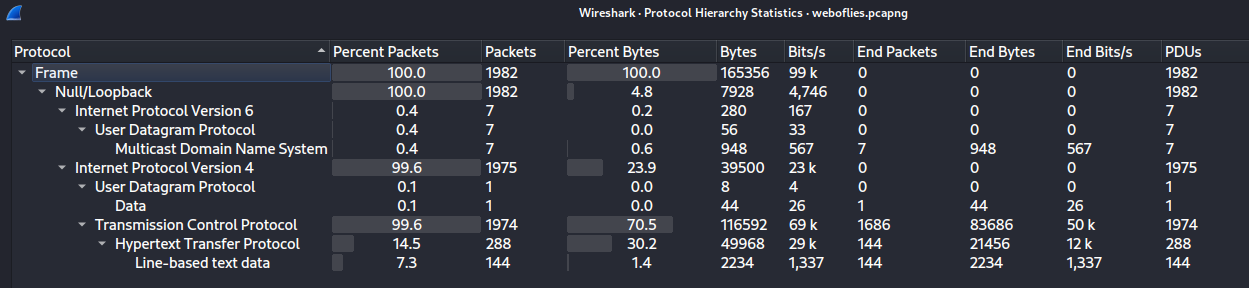
As you can see, it has some HTTP packets.
Let’s “Follow HTTP Stream”!
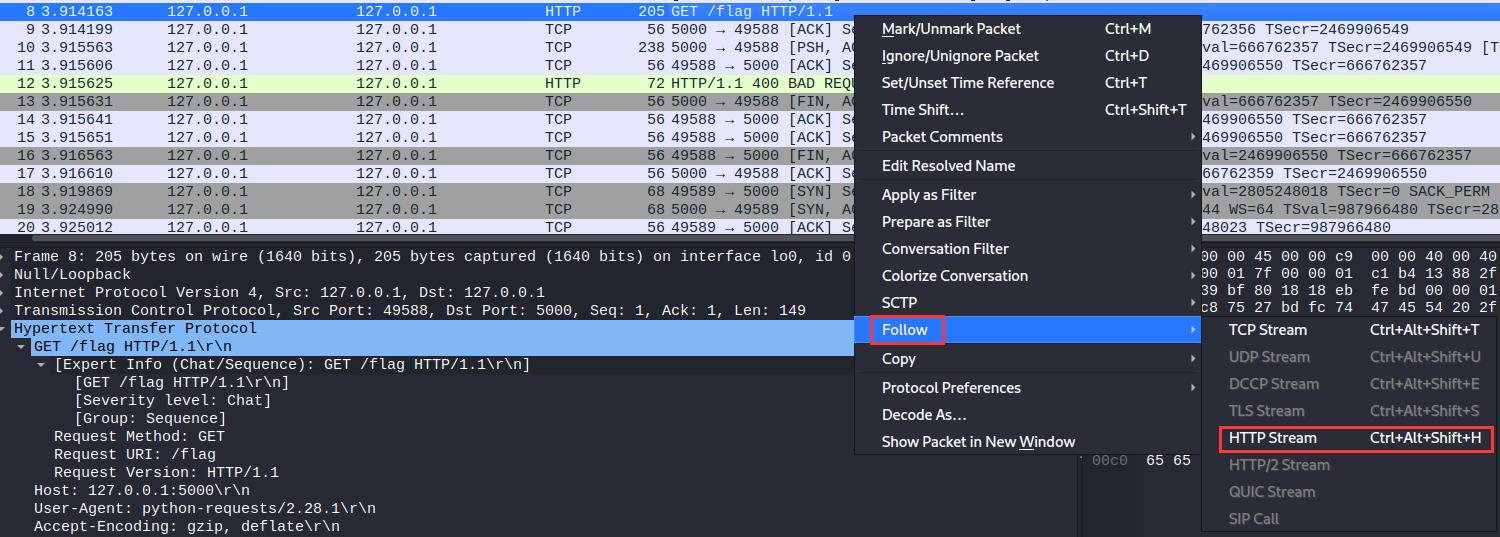
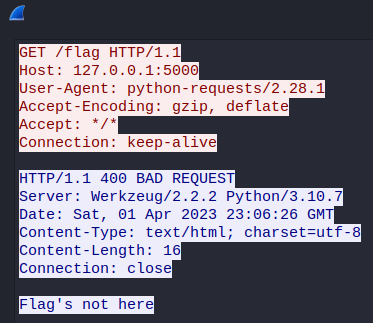
Hmm… “Flag’s not here”.
In WireShark, we can export all the HTTP object via:
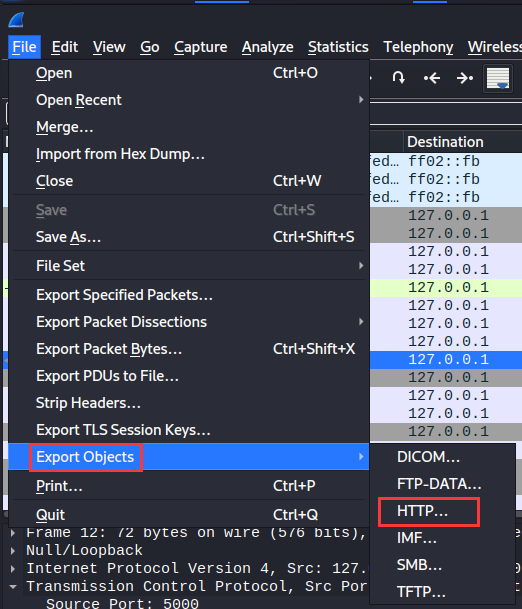

Then cat all of them:
┌[siunam♥earth]-(~/ctf/RITSEC-CTF-2023/Forensics/Web-of-Lies/http)-[2023.04.02|13:42:59(HKT)]
└> cat *
Flag Not Found
[...]
Flag's not here
[...]
Umm… All of them are not the real flag…
After fumbling around, I still don’t know what can I do with those packets…