Blue Baby Shark
Overview
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Find the flag
In this challenge, we can download a file:
┌[siunam♥earth]-(~/ctf/VU-Cyberthon-2023/Network-Security/Blue-Baby-Shark)-[2023.02.25|15:54:42(HKT)]
└> file Blue\ Baby\ Shark.pcapng
Blue Baby Shark.pcapng: pcapng capture file - version 1.0
It's a packet capture file!
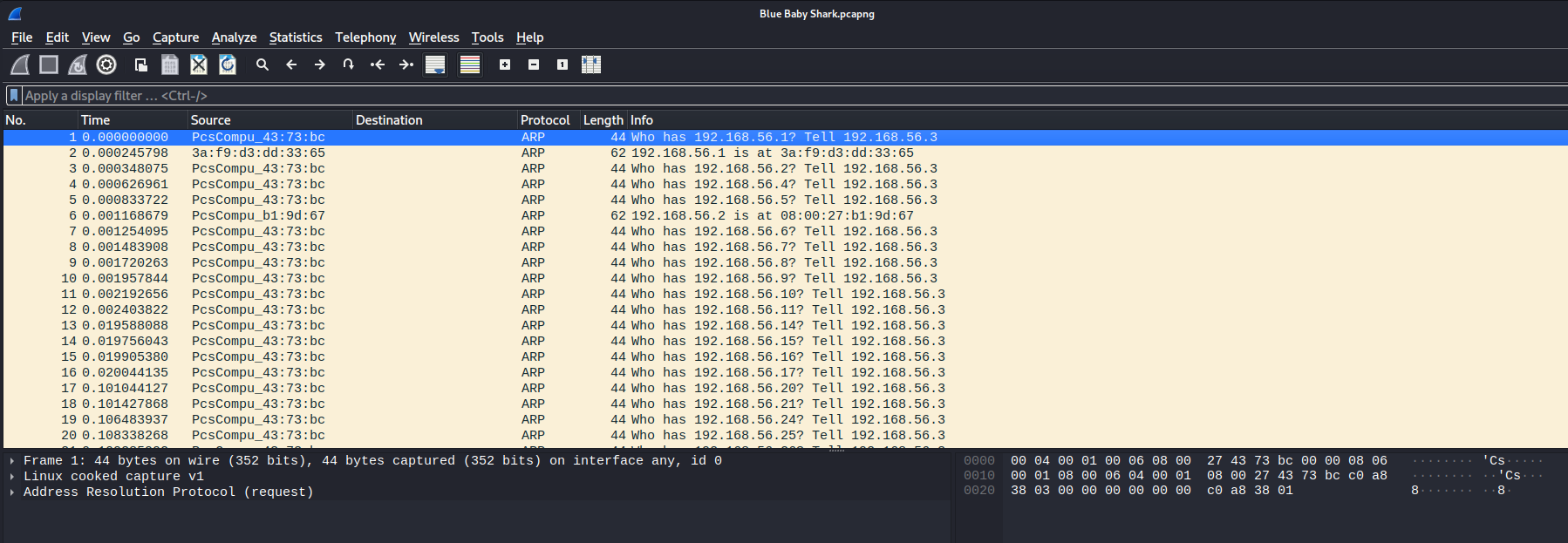
Let's open it in WireShark:
┌[siunam♥earth]-(~/ctf/VU-Cyberthon-2023/Network-Security/Blue-Baby-Shark)-[2023.02.25|15:55:32(HKT)]
└> wireshark Blue\ Baby\ Shark.pcapng
Let's look at the "Protocol Hierarchy" in "Statistics" tab:
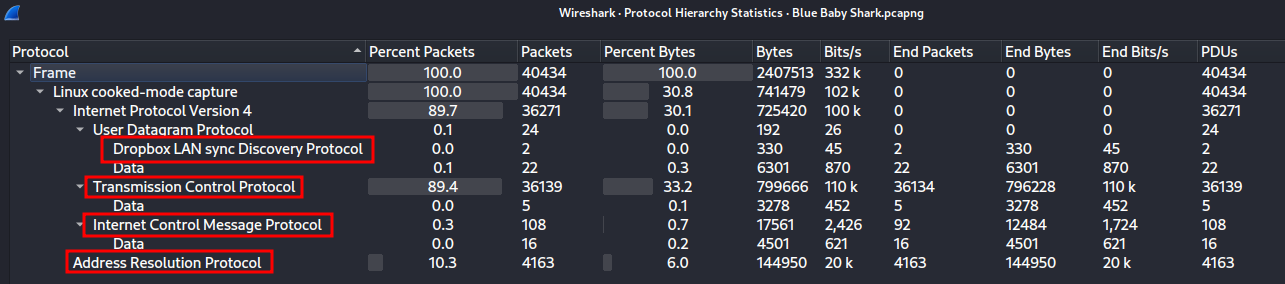
In here, we see there are 3 protocols: Dropbox LAN sync Discovery, TCP, ICMP.
The Dropbox protocol looks very interesting, as sometimes bad actors will use Dropbox to host their C2 (Command and Control) infrastructure:
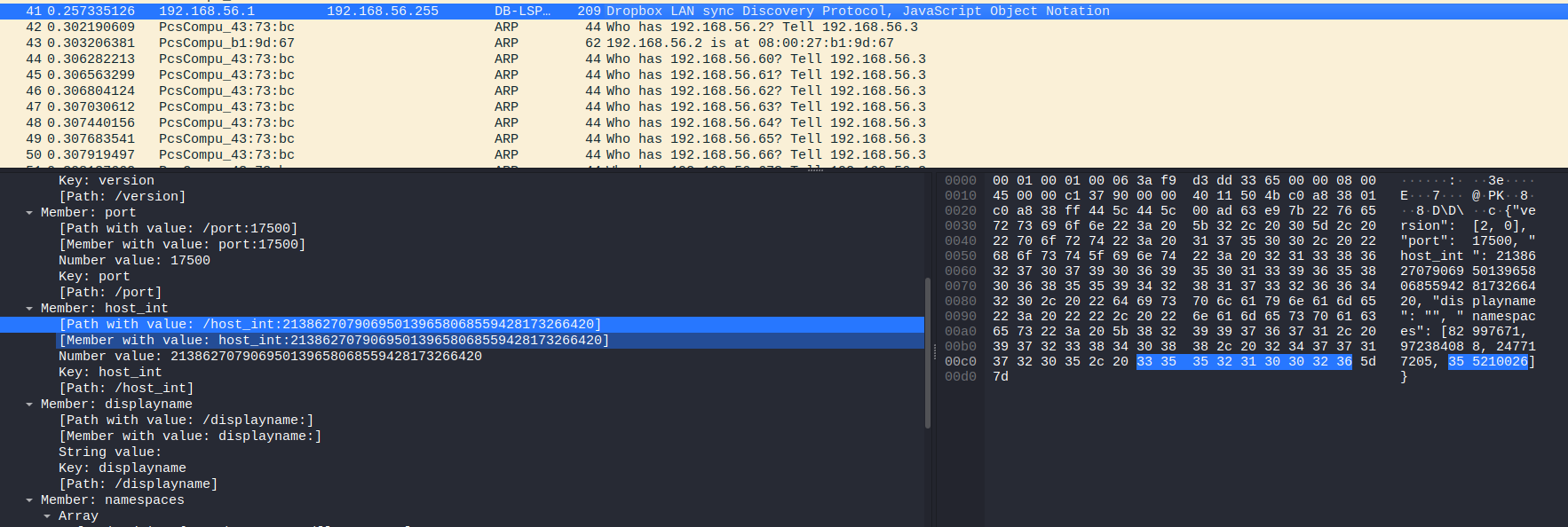
Hmm… No idea what we can do with that at the moment.
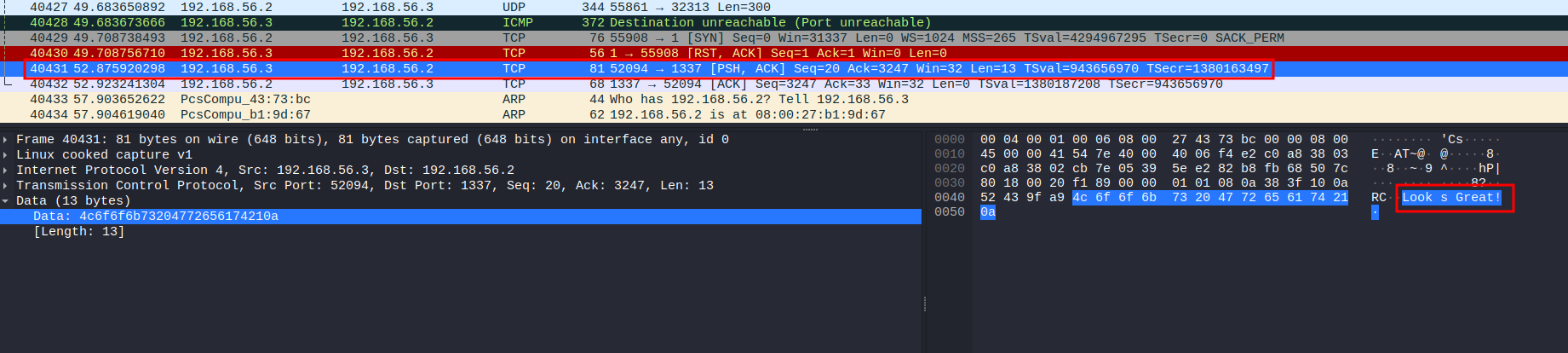
In the bottom of the packet capture, I saw that very sussy data.
Let's follow it's TCP stream:
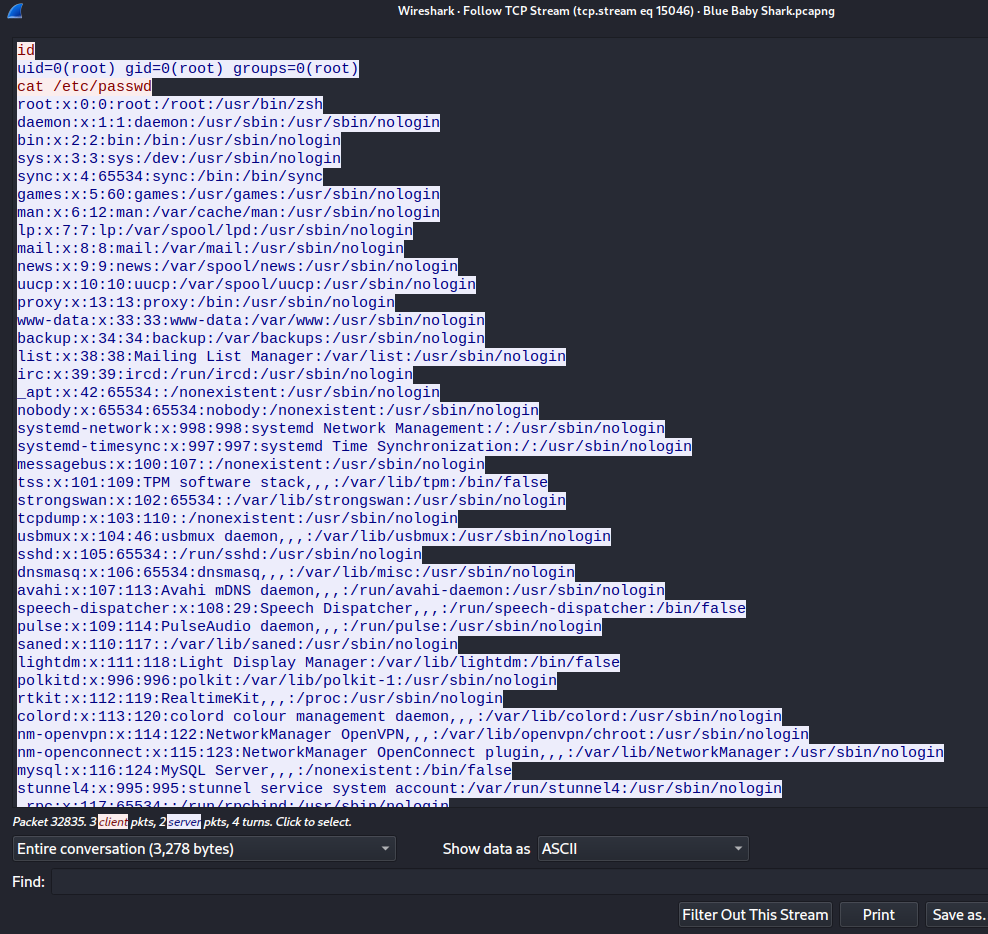
Oh! Looks like we found some commands traffic's data!
When you scroll down, we can see the flag:
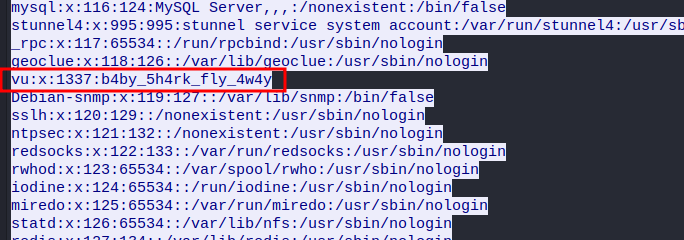
- Flag:
VU{b4by_5h4rk_fly_4w4y}
Conclusion
What we've learned:
- Analyzing How A Bad Actor Infiltrate A System Via Inspecting Packets In WireShark