Background
As usual, let's download the theballoon file and see what it is.
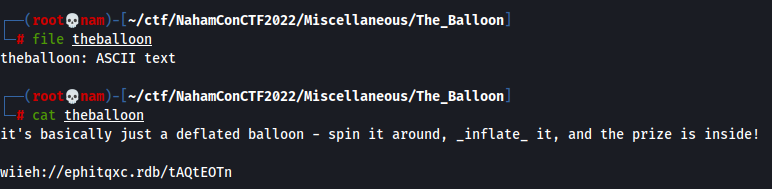
It's said it's defalted balloon(Compressed data), spin it around, _inflate_ it. Then, I saw a string that's rotated, and it reminds me Cicada 3301 stuff, as it looks a HTTPS scheme. Hmm… Let's use CyberChef to rotate that string. I'll use Rot13 recipe and manually change the amount.
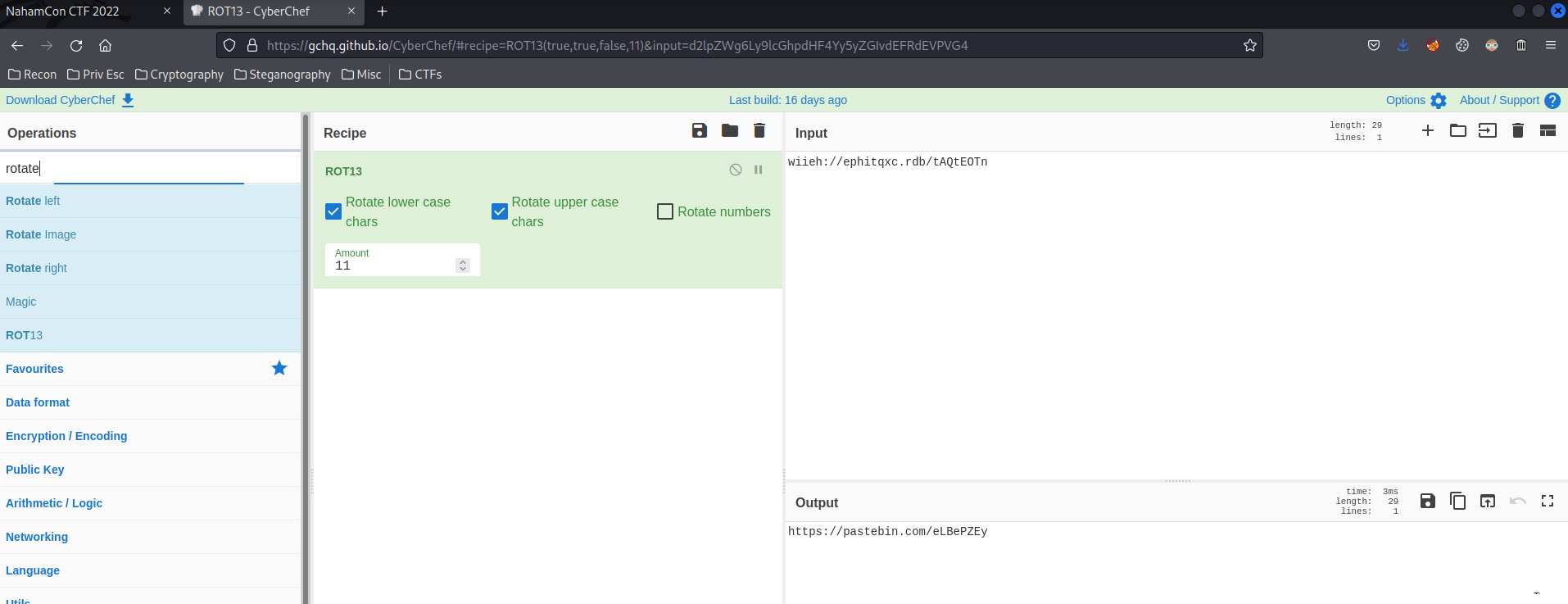
Oh… It's a pastebin link. Let's check that out.
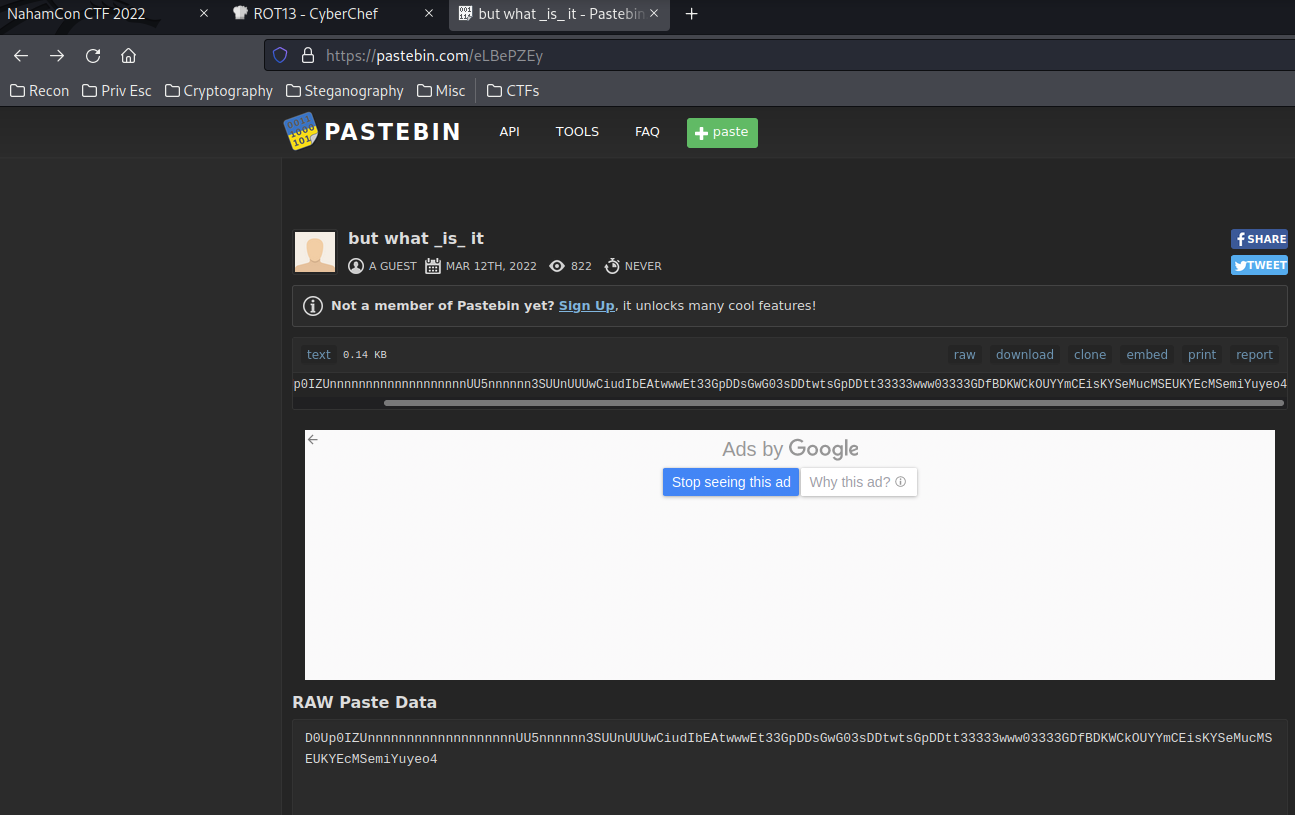
Weird string… Let's throw that into CyberChef again with the Raw Inflate recipe, as the theballoon file tells us to inflate it(Decompress).
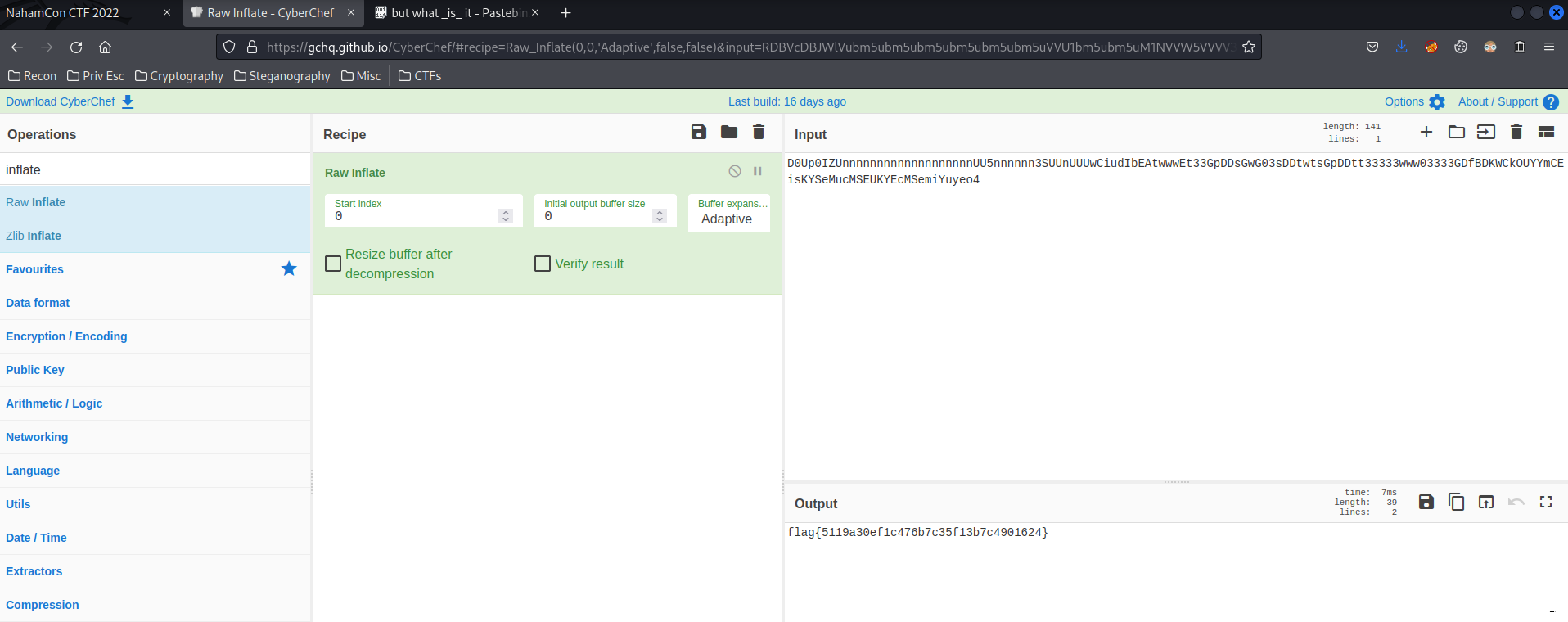
And voila!! That's the flag!