Background
In this challenge, you'll learn more about XXE(XML external entity injection). As usual, let's start the instance via the Start button on the top-right, and browse the website.
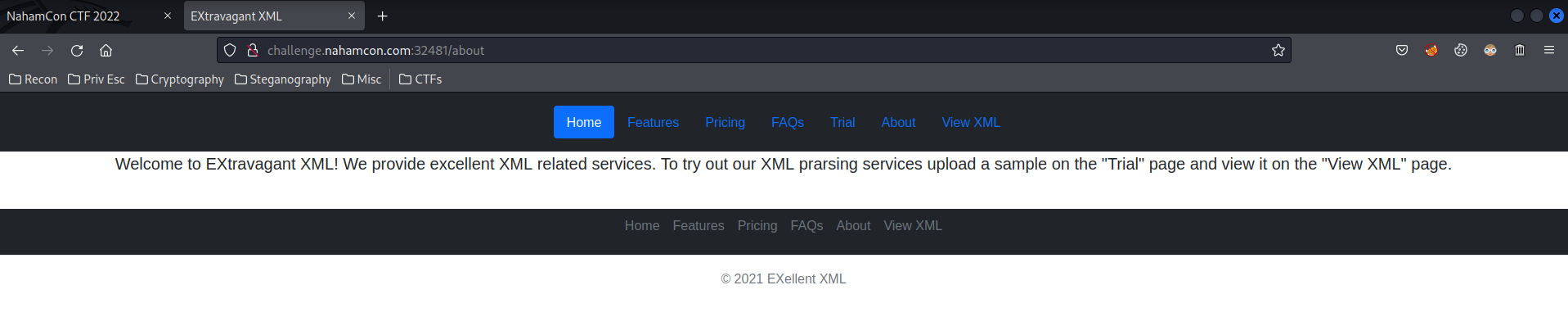
In the about page, we can see the site is using XML parsing, and we can upload a sample in Trial page, and view it on the View XML page. Hmm… Maybe we can do a XXE, or XML external entity injection?? Next, I started to google XXE file upload exploit, and I found one PDF explaining that exploit in exploit-db. It said:
"If the application allows user to upload svg files on the system, then the XXE can be exploited using them, and a SVG file is to define graphics in XML format."
Then I found a XXE inside SVG upload payload at PayloadsAllTheThings.
Let's copy and paste it to our text editor. Also, According to the background of this challenge, the flag is in /var/www, so let's modify the path from "file:///etc/hostname" to "file:///var/www/flag.txt", and save it as a SVG file.
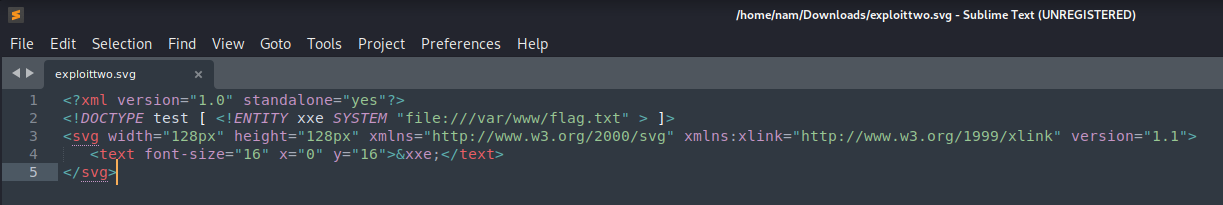
Now, upload the SVG payload to Trial page.
Upload successful!! Let's go to the View XML page to see is it work!
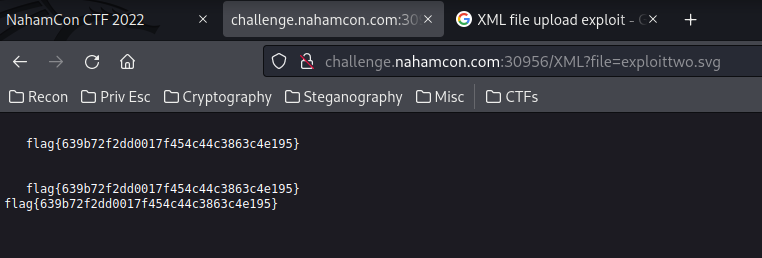
Yes!! We've the flag!
Trivia
Before I realized it's a XXE, I've tried to upload a php reverse shell, but it doesn't work. Lol