findme
Overview
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Author: Geoffrey Njogu
Description
Help us test the form by submiting the username as test and password as test!
The website running here.
Enumeration
Home page:
In here, we see there's a login page!
Let's try test:test:
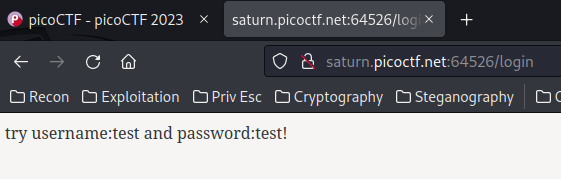
Nope. We need to try test:test!:
Now, what I would like to do is fire up Burp Suite, and proxying ALL the HTTP traffics.
Burp Suite HTTP history:
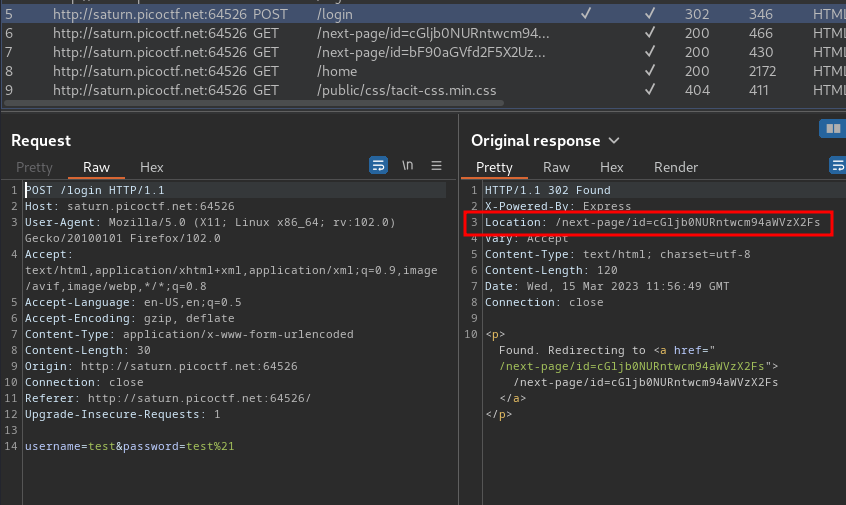
When we click the "test" button, it'll send a POST request to /login, with parameter username and password.
If we're authenticated, it'll redirect us to /next-page/id=cGljb0NURntwcm94aWVzX2Fs.
/next-page/id=cGljb0NURntwcm94aWVzX2Fs:
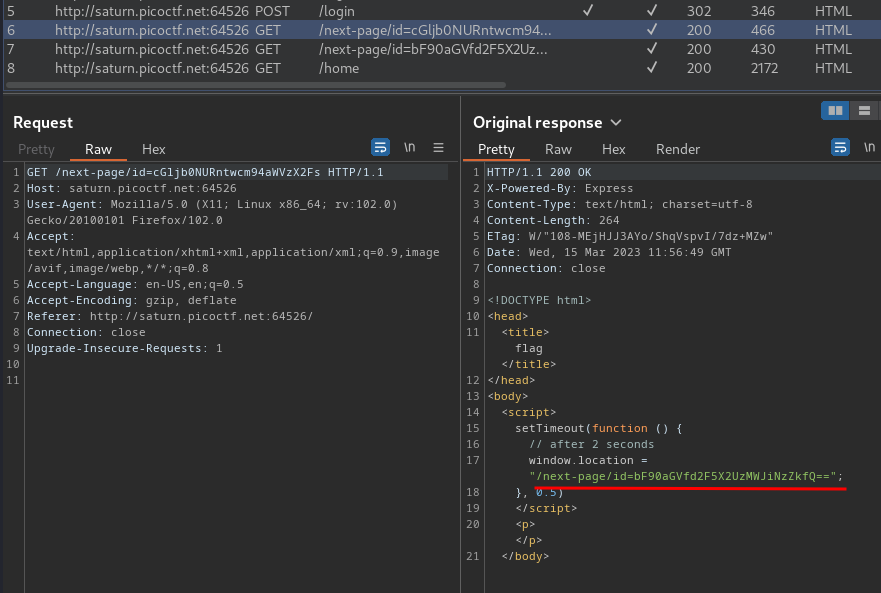
In this page, it has a JavaScript code:
setTimeout(function () {
// after 2 seconds
window.location = "/next-page/id=bF90aGVfd2F5X2UzMWJiNzZkfQ==";
}, 0.5)
After 2 seconds, it'll set the window object's location attribute to /next-page/id=bF90aGVfd2F5X2UzMWJiNzZkfQ==, which is redirecting us to that page.
/next-page/id=bF90aGVfd2F5X2UzMWJiNzZkfQ==:
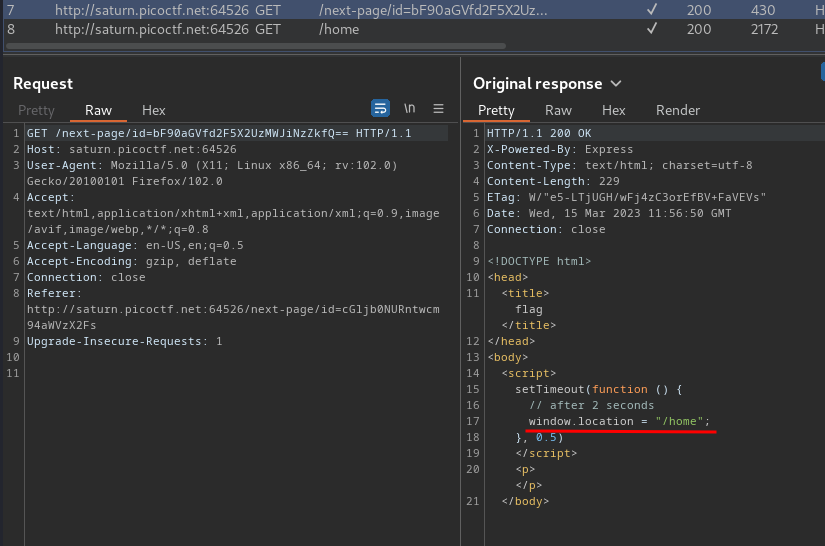
Then, it'll redirect us to /home.
Hmm… I wonder what are those id GET parameter's value:
cGljb0NURntwcm94aWVzX2FsbF90aGVfd2F5X2UzMWJiNzZkfQ==
In that string, there's a = character, which is a base64 encoding's padding string.
Armed with above information, we can base64 decode it:
┌[siunam♥earth]-(~/ctf/picoCTF-2023)-[2023.03.15|19:57:49(HKT)]
└> echo 'cGljb0NURntwcm94aWVzX2FsbF90aGVfd2F5X2UzMWJiNzZkfQ==' | base64 -d
picoCTF{proxies_all_the_way_e31bb76d}
Boom! We got the flag!
- Flag:
picoCTF{proxies_all_the_way_e31bb76d}
Conclusion
What we've learned:
- Proxying HTTP Traffics