msfroggenerator2
Overview
- Overall difficulty for me (From 1-10 stars): ★★★★★★★★★★
Background
Author: ehhthing
Description
The Frog Software Foundation (FSF) made a customizable msfrog generator! Make your own msfrog today, now fully rendered client side using canvas ✨magic✨.
Make your msfrog here.
Source code: msfroggenerator2.tar.gz
Enumeration
Home page:
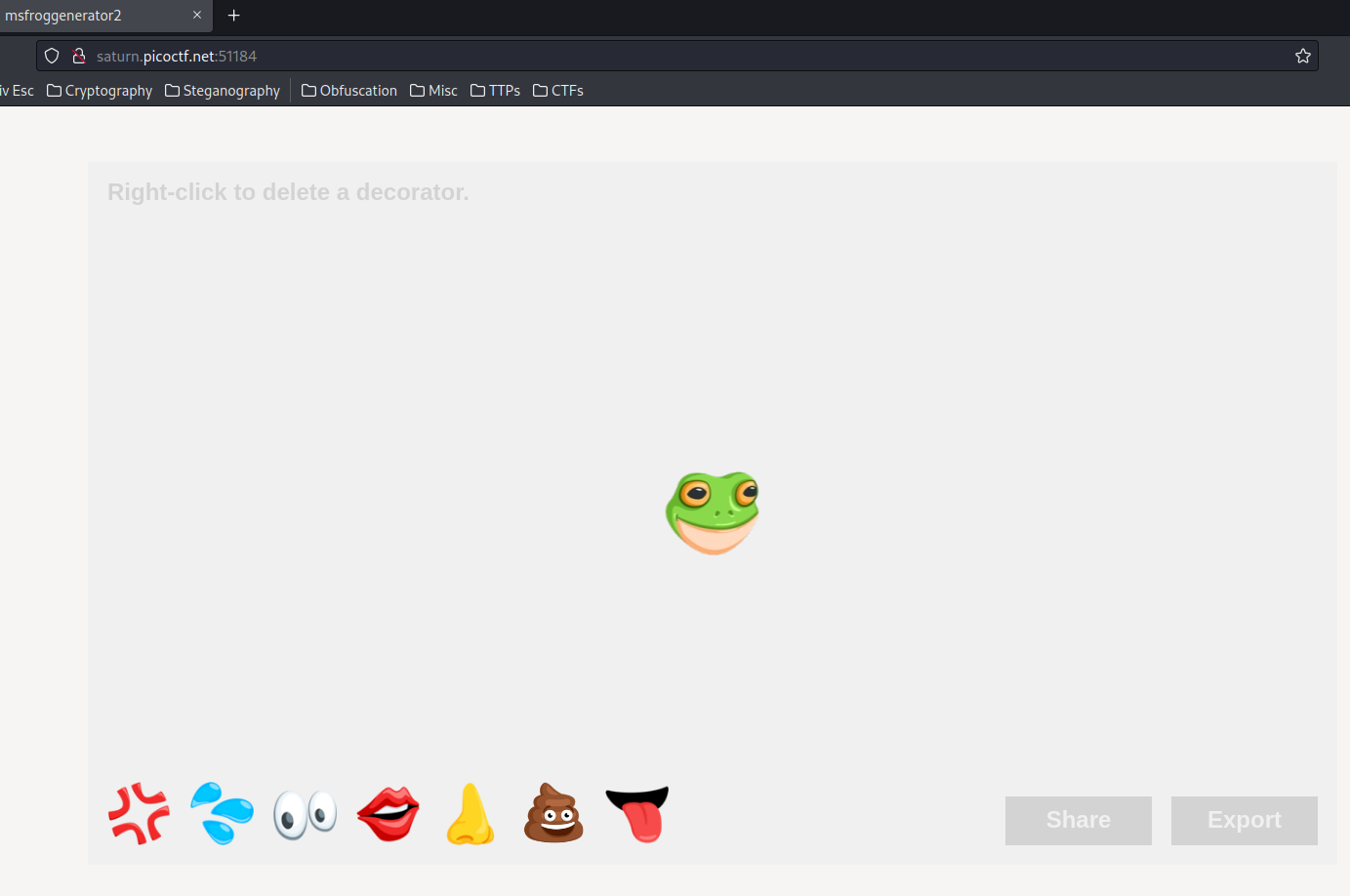
Hmm… We can add some decorators, then share and export the image?
In this challenge, we can download the source code:
┌[siunam♥earth]-(~/ctf/picoCTF-2023/Web-Exploitation/msfroggenerator2)-[2023.03.18|13:51:17(HKT)]
└> file msfroggenerator2.tar.gz
msfroggenerator2.tar.gz: gzip compressed data, from Unix, original size modulo 2^32 256000
┌[siunam♥earth]-(~/ctf/picoCTF-2023/Web-Exploitation/msfroggenerator2)-[2023.03.18|13:51:21(HKT)]
└> tar xvf msfroggenerator2.tar.gz
./
./api/
./api/.dockerignore
./api/Dockerfile
./api/package-lock.json
./api/package.json
./api/web.js
./bot/
./bot/.dockerignore
./bot/Dockerfile
./bot/bot.js
./bot/entrypoint.sh
./bot/package-lock.json
./bot/package.json
./bot/start_display.sh
./bot/web.js
./docker-compose.yml
./flag.txt
./openresty/
./openresty/static/
./openresty/static/designer.css
./openresty/static/designer.js
./openresty/static/index.html
./openresty/static/konva.min.js
./openresty/web.conf
./traefik/
./traefik/traefik.yml
./traefik/web.yml
But before we look into those files, let's have a quick look of the application.
Let's try the "Share" button:
Burp Suite HTTP history:
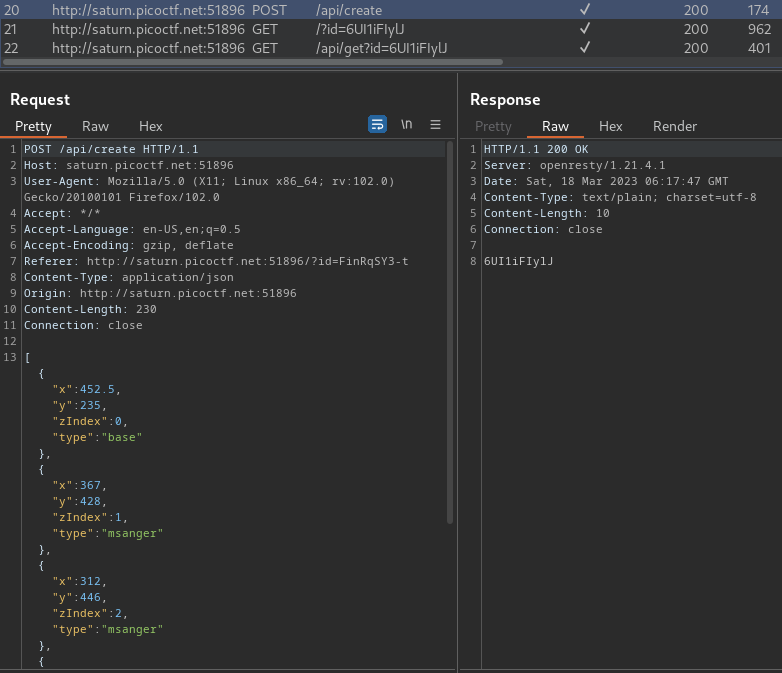
When we click that, it'll send a POST request to /api/create with JSON data of our decorators' location and type. If error, it responses an ID.
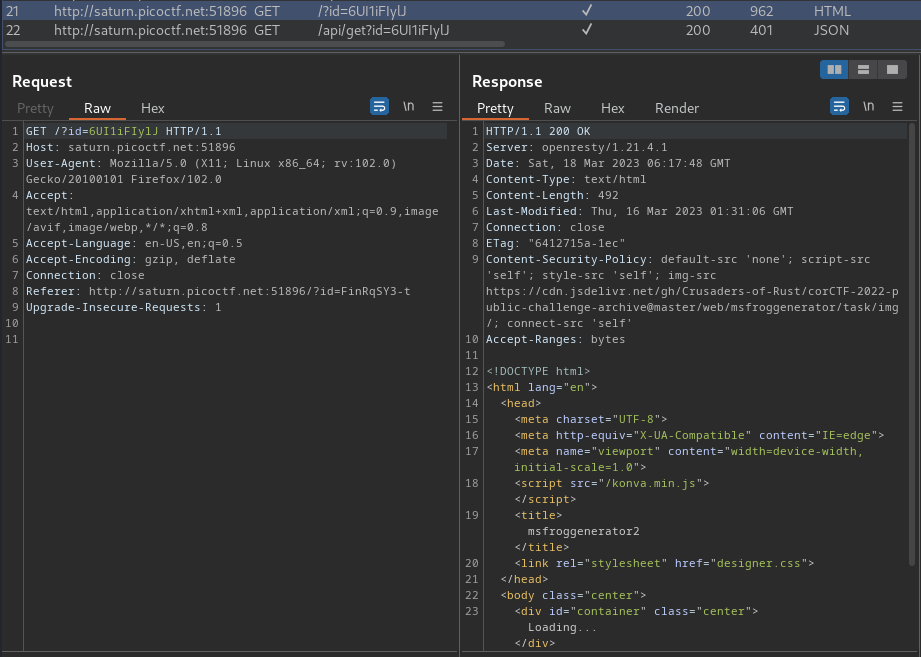
Then, it'll use that ID to send another GET request to /, with parameter id.
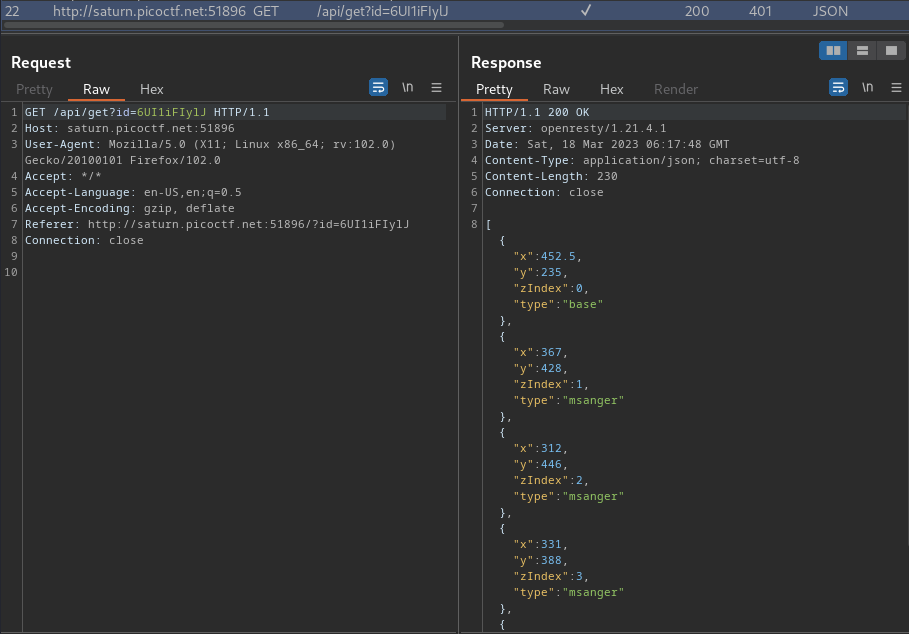
After that, it'll send another GET request to /api/get with that id parameter's value, then it responses the decorators' location and type.
How about the "Export" button?
It'll download an image file export.png:
Also, I don't see any request has been made, so it's been done in client-side, like JavaScript.
After digging around at the source code, I couldn't figure out the vulnerable code, exploitation flow…