User ID controlled by request parameter, with unpredictable user IDs | Dec 14, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: User ID controlled by request parameter, with unpredictable user IDs! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has a horizontal privilege escalation vulnerability on the user account page, but identifies users with GUIDs.
To solve the lab, find the GUID for carlos, then submit his API key as the solution.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
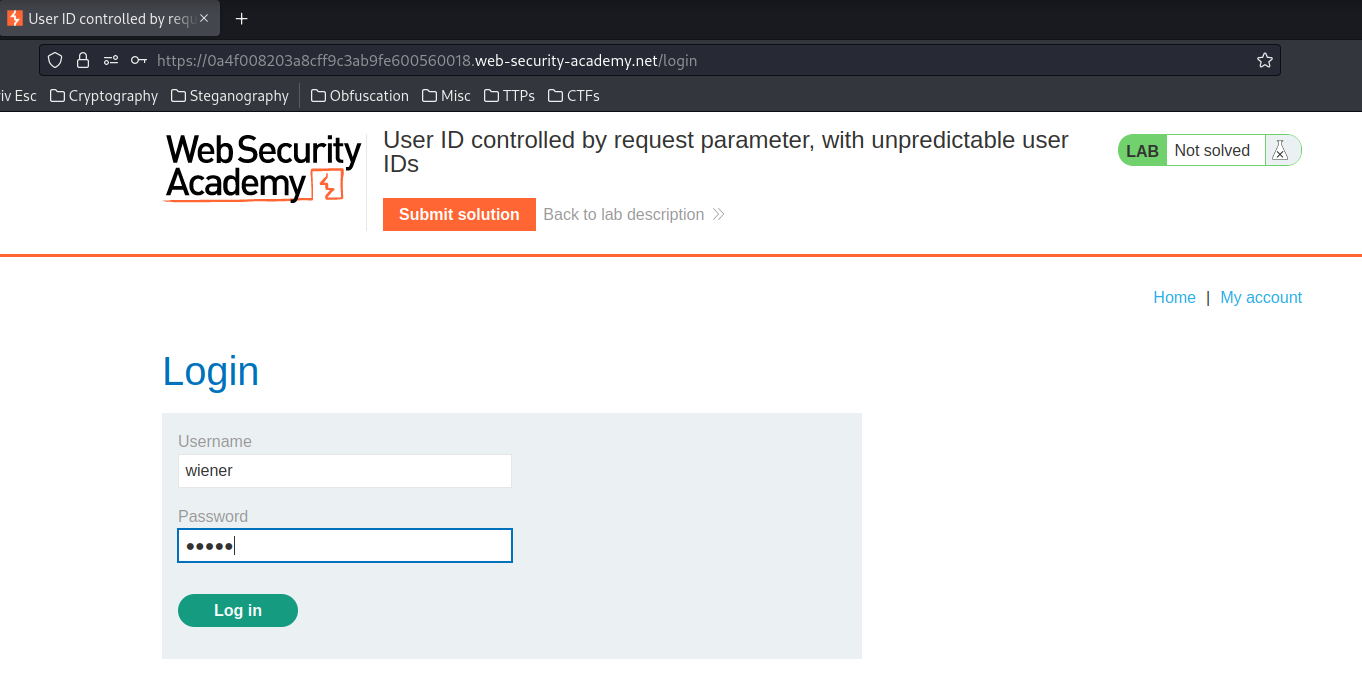
Login as user wiener:
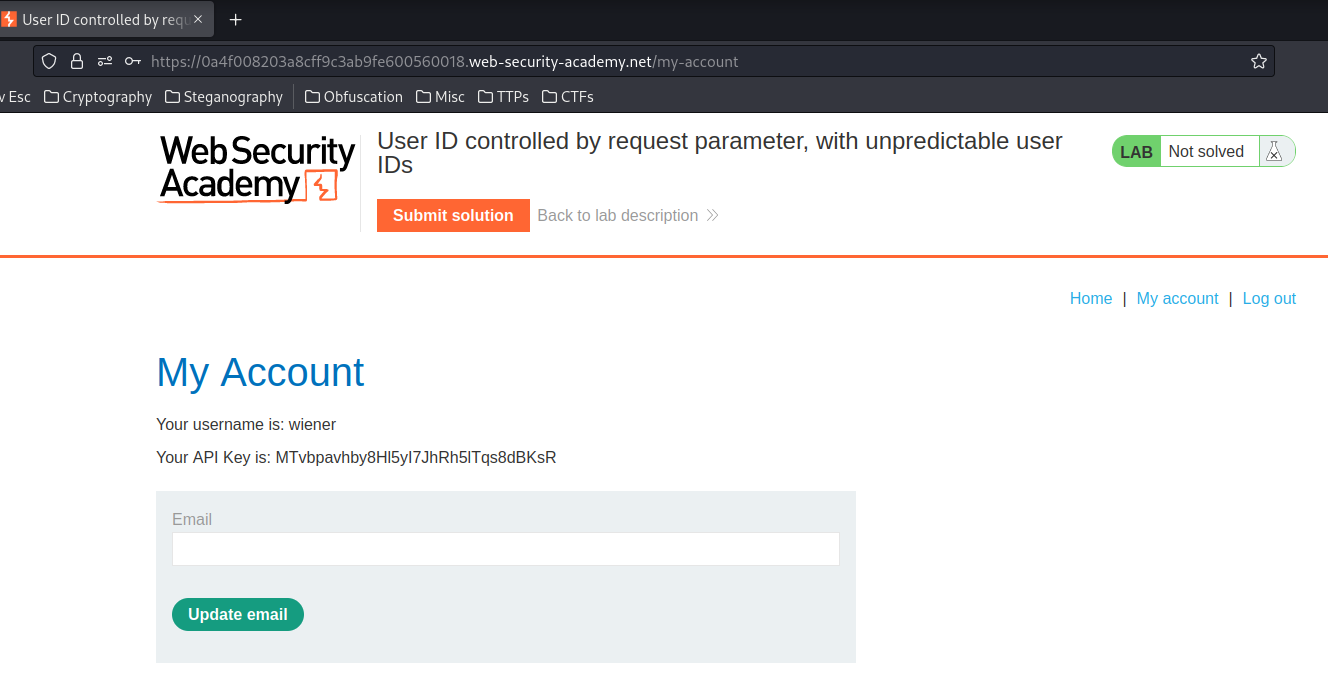
In the previous lab, we found that the My account link is supplying an id GET parameter, let's view the source again:
[...]
<section class="top-links">
<a href=/>Home</a><p>|</p>
<a href="/my-account?id=55b2eb8a-6a18-40f9-bd35-7c04b4939bae">My account</a><p>|</p>
<a href="/logout">Log out</a><p>|</p>
</section>
[...]
This time, it's using an GUID(Globally Unique Identifier).
Hmm… It seems like we couldn't guess another user…
Let's explore this site:
In the home page, we can view other people's posts:
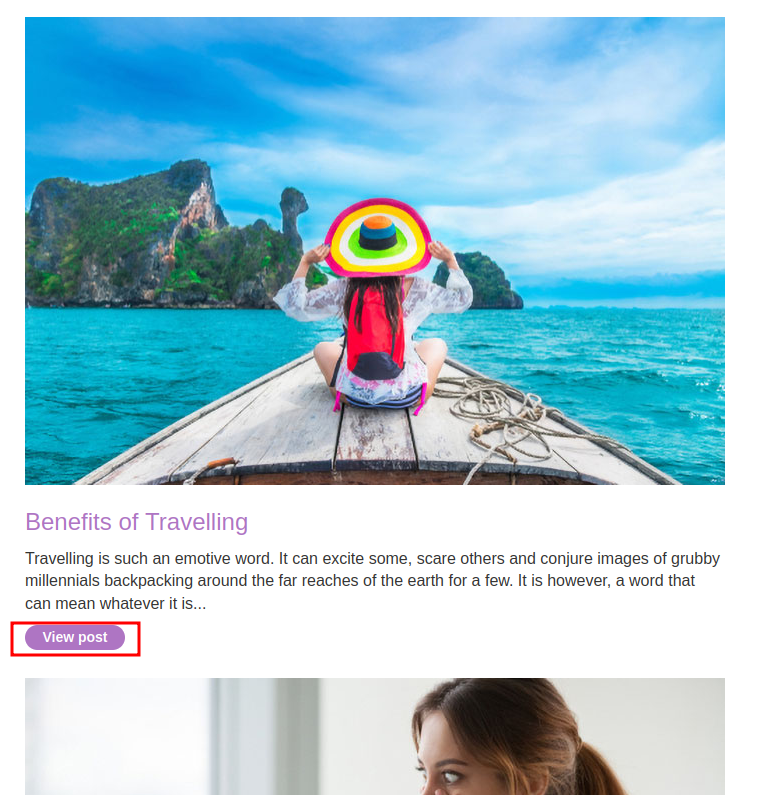
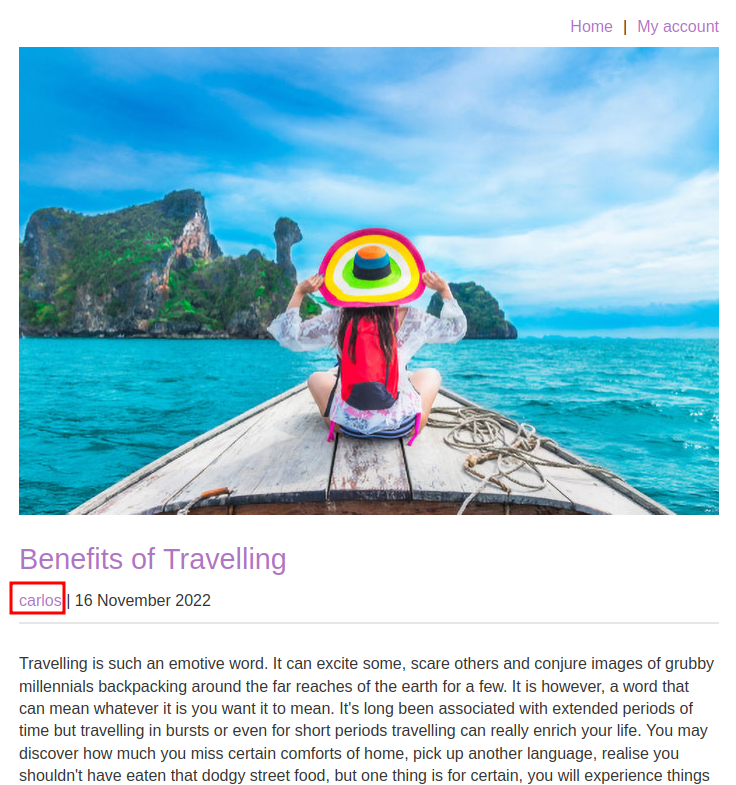
And you can see, it includes the author's name!
Let's view the source again:
<p><span id=blog-author><a href='/blogs?userId=2603c122-a7b8-4bda-b0eb-780b8fbc5016'>carlos</a></span> | 16 November 2022</p>
Oh! We found carlos GUID: 2603c122-a7b8-4bda-b0eb-780b8fbc5016!!
Now we can use his GUID to see his API key in the My account link!
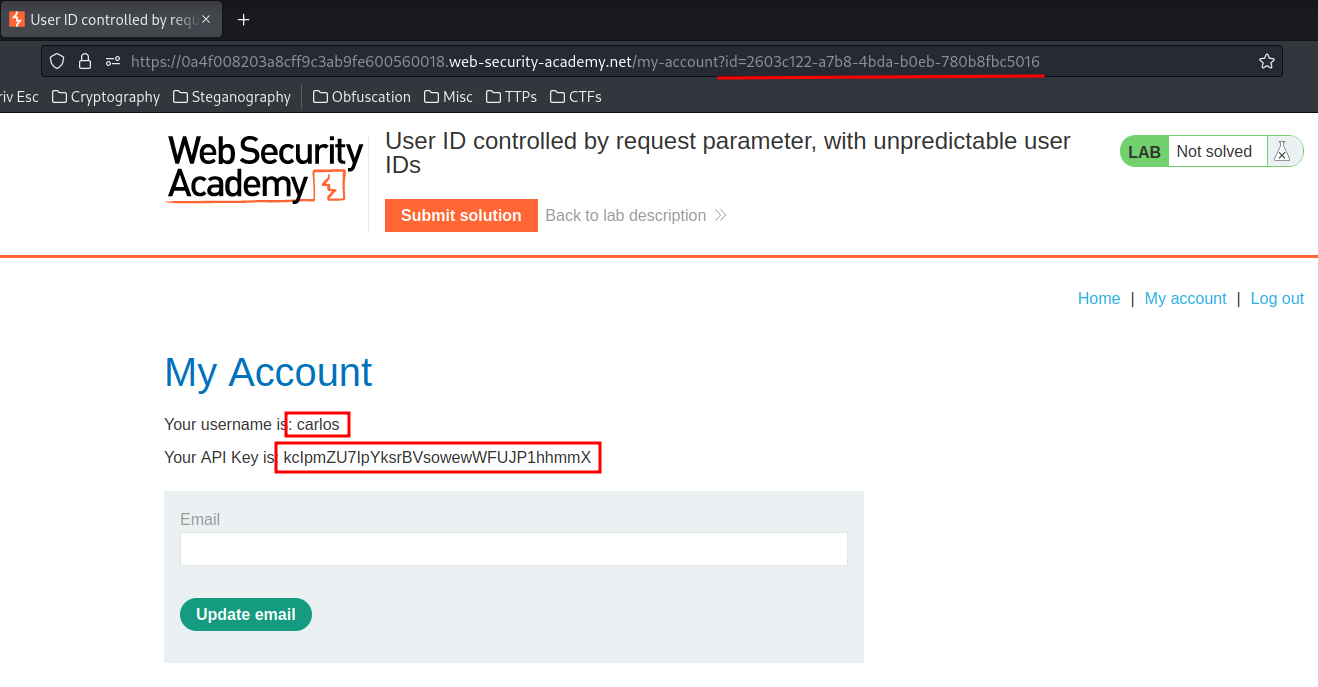
We're user carlos and found his API key!
What we've learned:
- User ID controlled by request parameter, with unpredictable user IDs