Insecure direct object references | Dec 14, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Insecure direct object references! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab stores user chat logs directly on the server's file system, and retrieves them using static URLs.
Solve the lab by finding the password for the user carlos, and logging into their account.
Exploitation
Home page:
In here, we can see there is a Live chat link:
Hmm… Let's send something and intercept the request in Burp Suite:
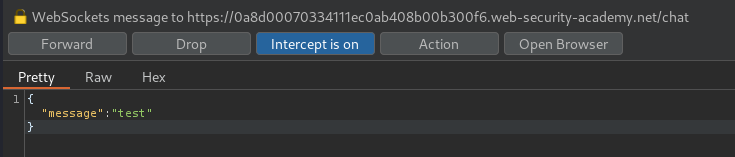
Nothing weird. How about the View transcript button?
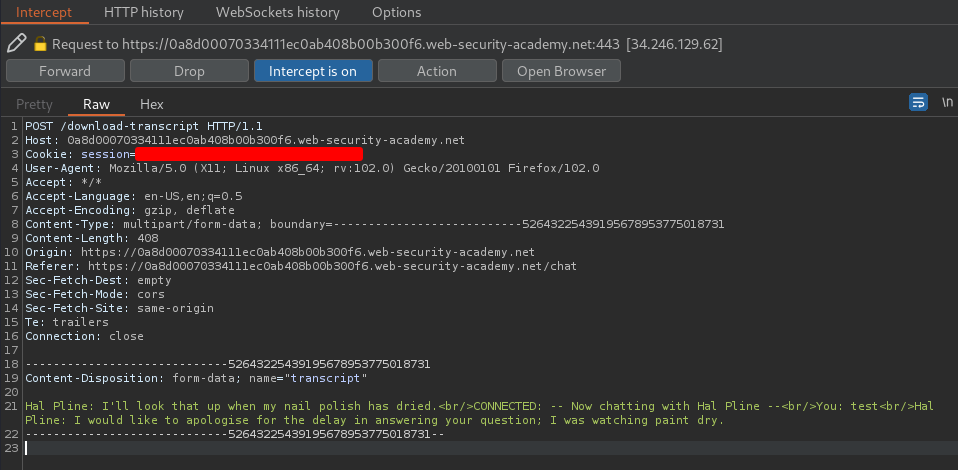
It's sending a POST request to /download-transcript with the transcript data.
Let's forward that request.
Then, we'll see this request, which is very interesting:
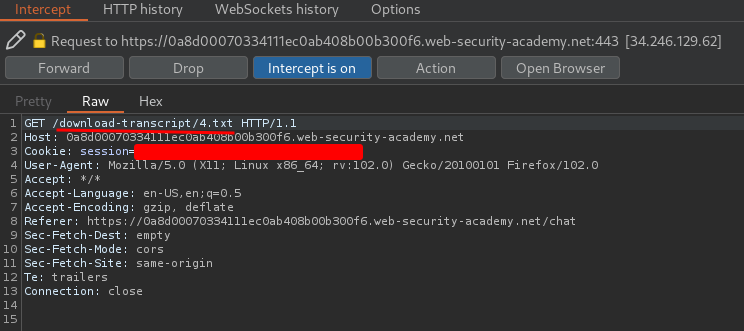
It's sending a GET request to /download-transcript/4.txt!
Hmm… What if I change the 4.txt to 1.txt? Or 2.txt, and so on?
To do so, I'll send that GET request to Burp Suite's Repeater and hit Send:
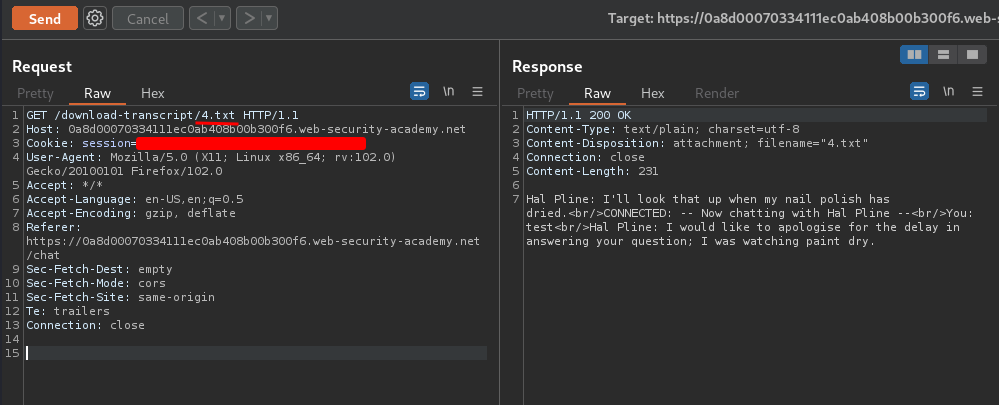
Now, we can see our own session's transcript.
How about I change it to 1.txt?
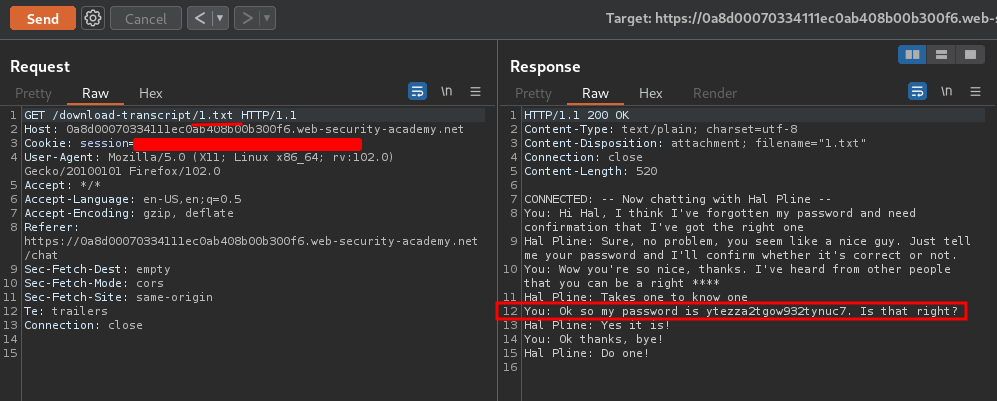
As you can see, we saw the first transcript in this live chat, and also someone's password! I'm guessing it's user carlos's password!
Let's login as user carlos!
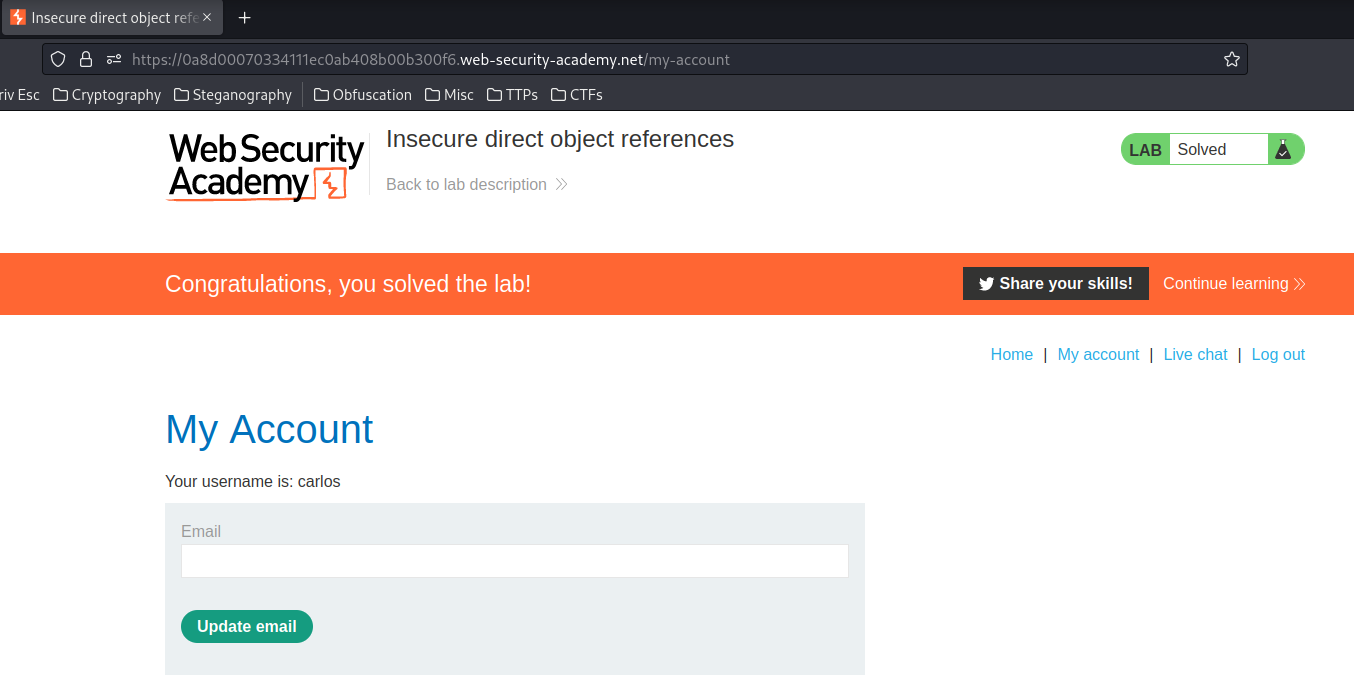
I'm in!
What we've learned:
- Insecure direct object references