Authentication bypass via flawed state machine | Dec 20, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Authentication bypass via flawed state machine! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★☆☆☆☆☆☆☆
Background
This lab makes flawed assumptions about the sequence of events in the login process. To solve the lab, exploit this flaw to bypass the lab's authentication, access the admin interface, and delete Carlos.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
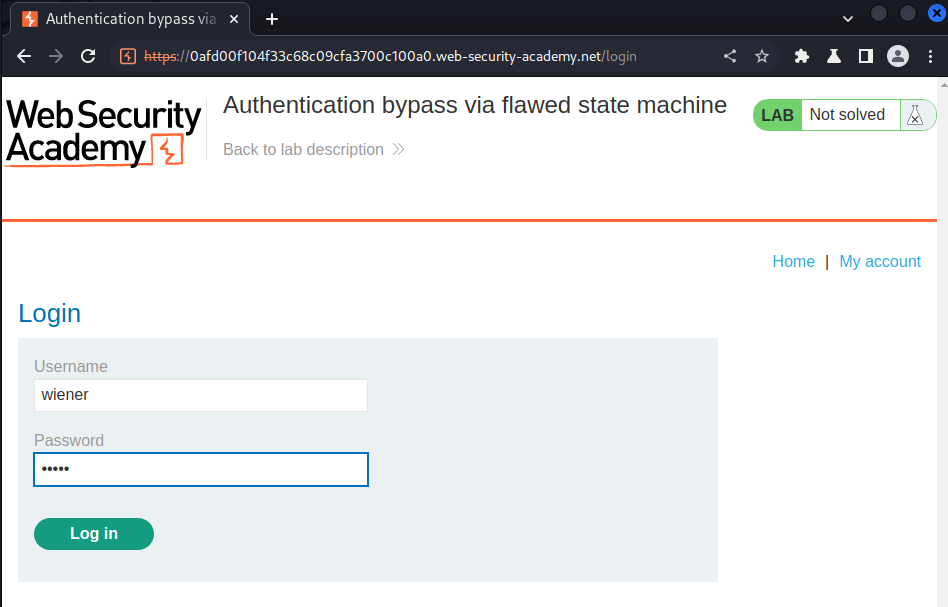
Login as user wiener:
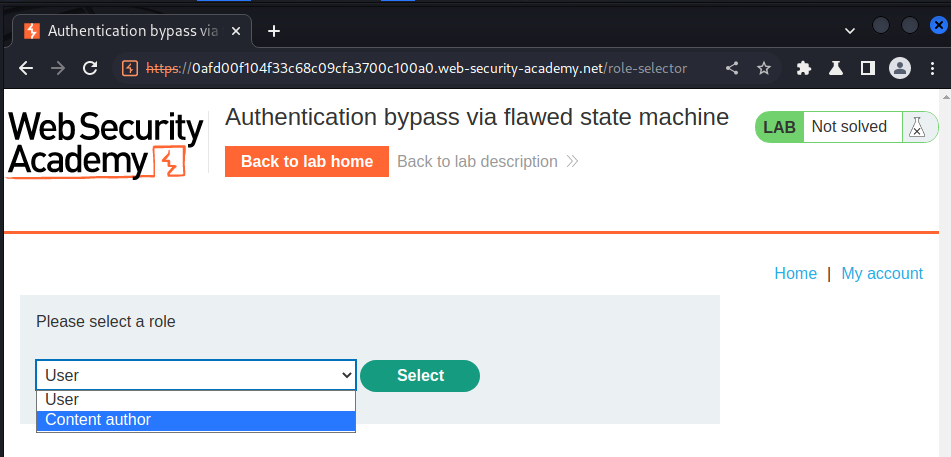
In here, we can choose a role: User or Content author.
Let's select User and intercept the request via Burp Suite:
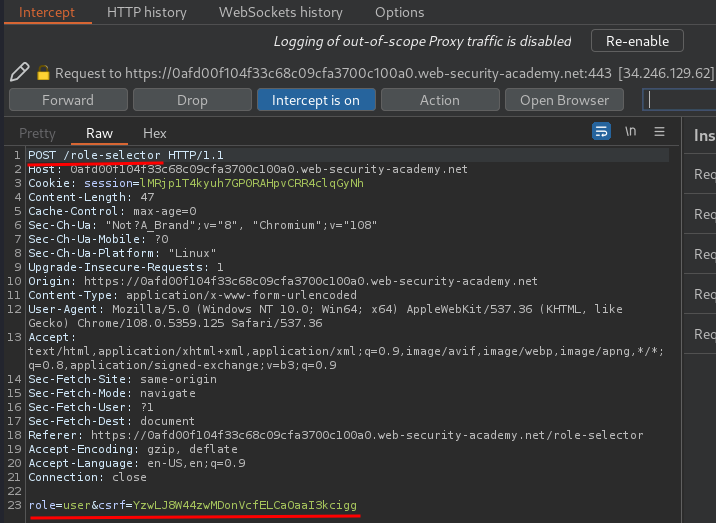
When we clicked the Select button, it'll send a POST request to /role-selector, with parameter role and csrf.
Let's forward that request and click the My account link:
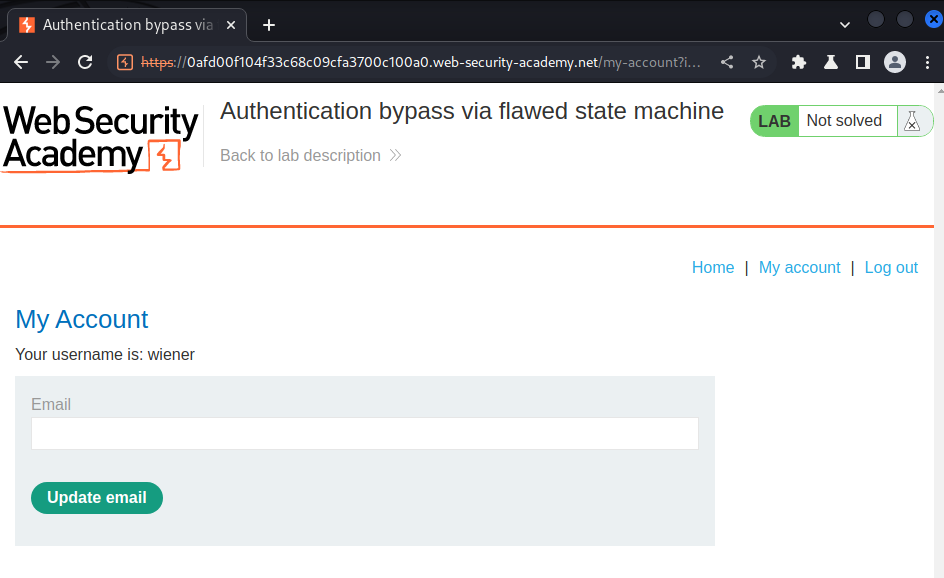
Now, what if we select Content author role?
It seems like no difference between those roles.
Let's try to reach to the admin panel /admin:
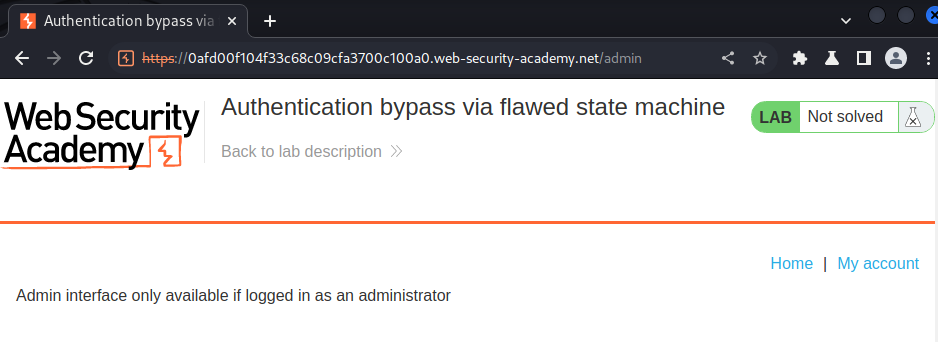
It's only available to administrator.
Now, let's try to log out and test something:
Then login and intercept the request via Burp Suite:
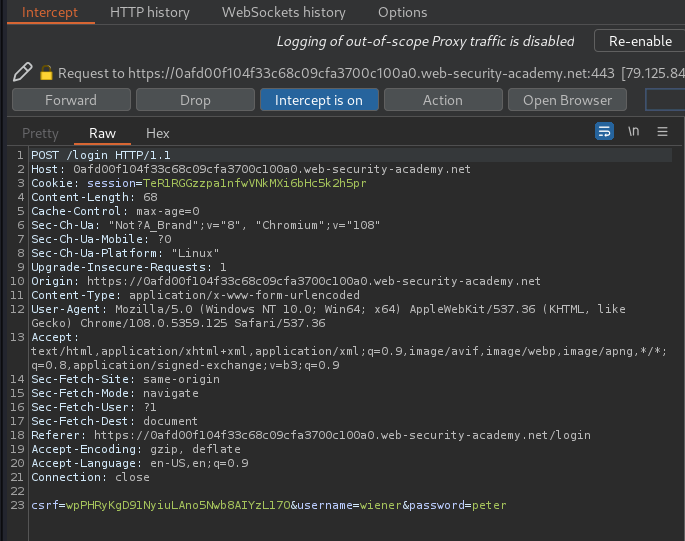
We'll forward the POST /login request:
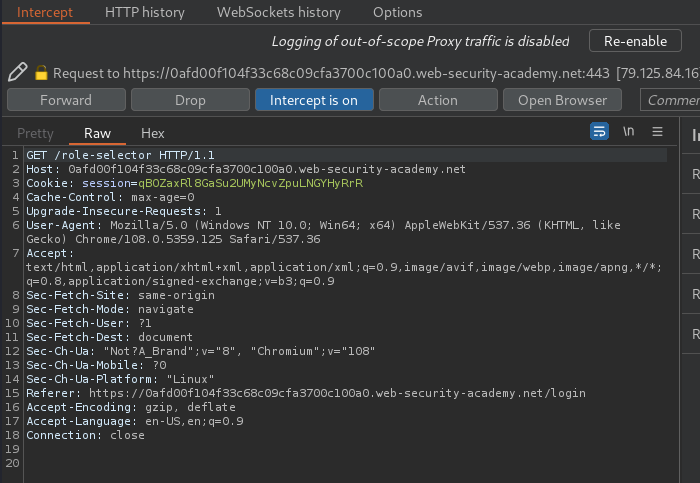
In here, what if I drop the GET /role-selector request?
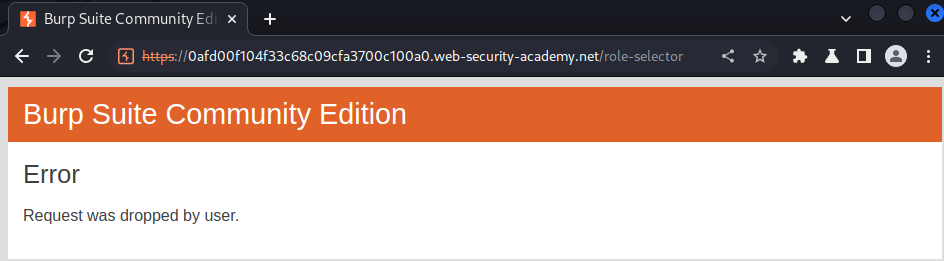
Then go to the home page:
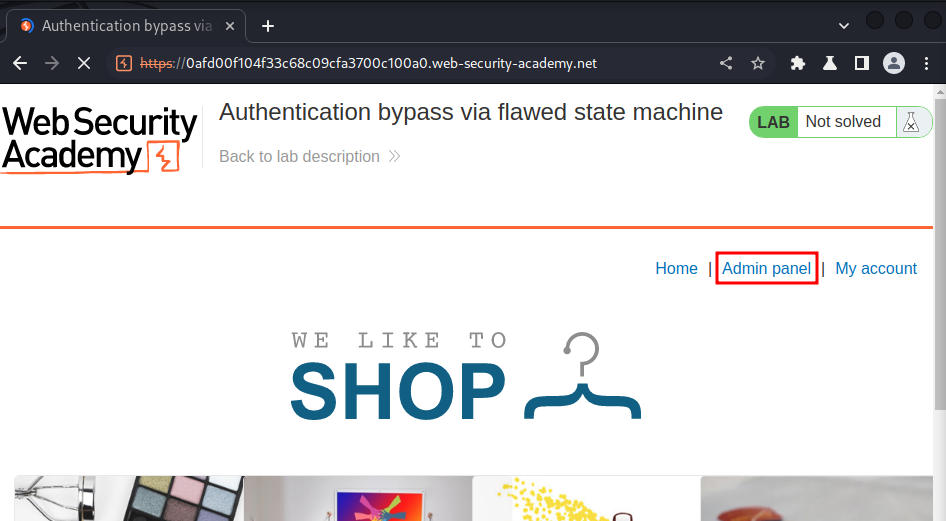
Hmm… We have admin access!
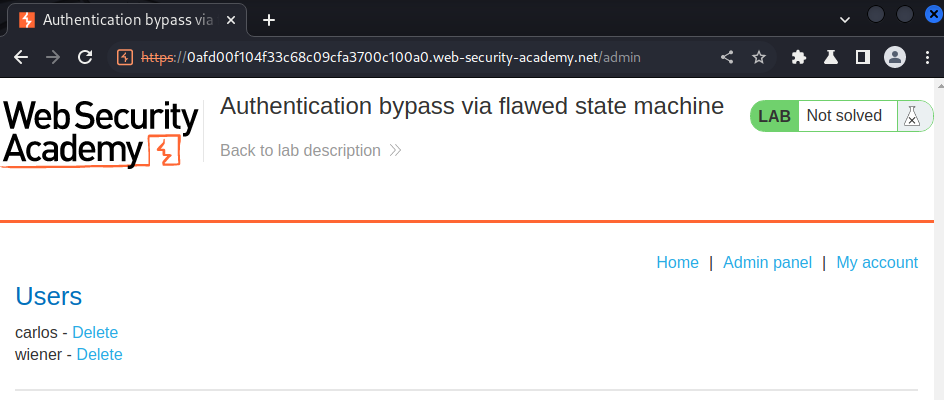
Let's delete user carlos!
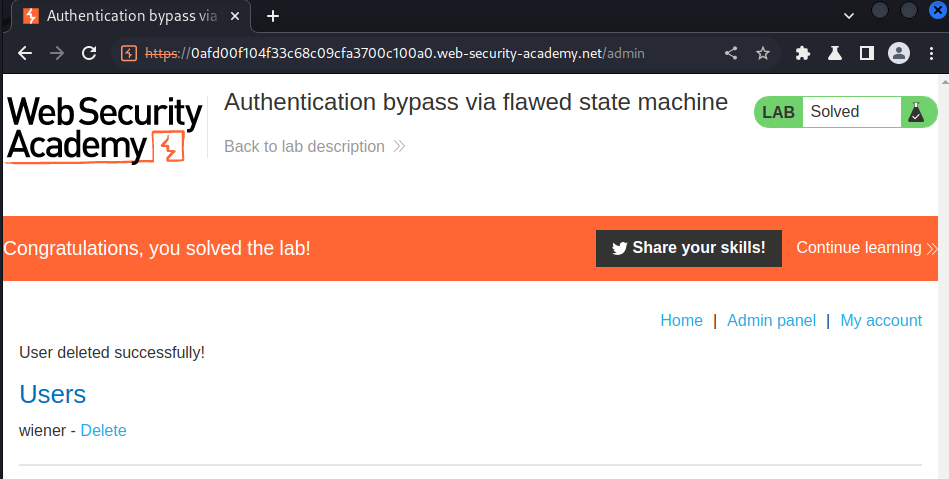
Nice!
What we've learned:
- Authentication bypass via flawed state machine