Reflected XSS into HTML context with nothing encoded | Dec 29, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you’ll learn: Reflected XSS into HTML context with nothing encoded! Without further ado, let’s dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a simple reflected cross-site scripting vulnerability in the search functionality.
To solve the lab, perform a cross-site scripting attack that calls the alert function.
Exploitation
Home page:
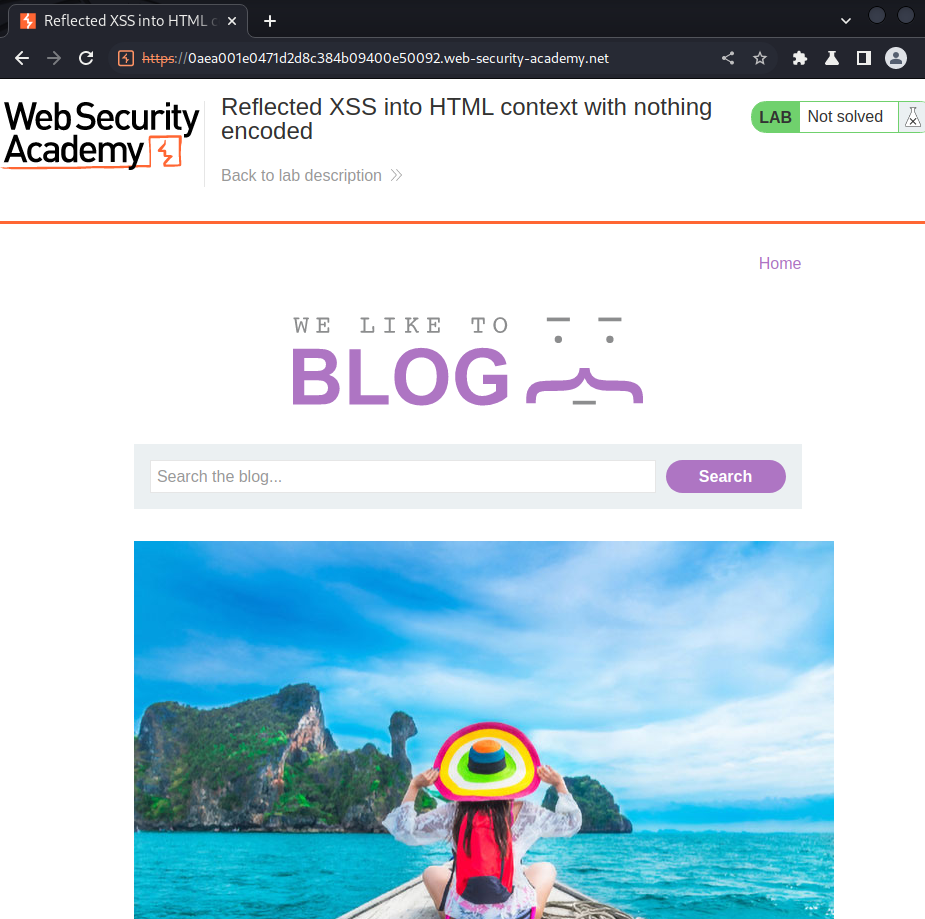
In here, we can see there is a search box.
Let’s search something:
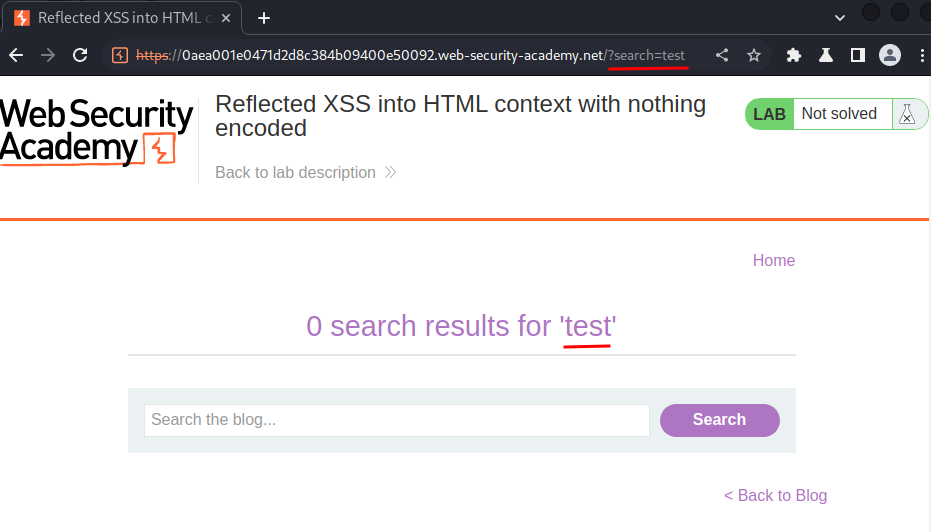
When we clicked the Search button, it’ll send a GET request to /, with parameter search.
Also, our input is reflected to the web page.
Let’s try to inject a JavaScript function called alert():
<script>alert(document.domain)</script>
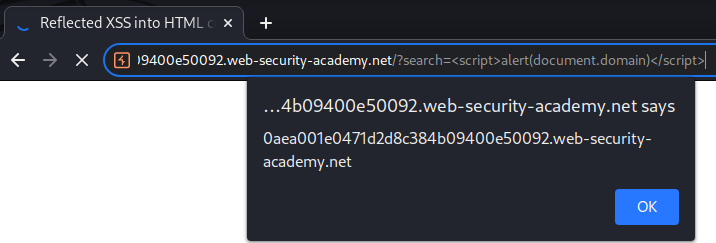
As you can see, we successfully injected a JavaScript that under attacker’s control!
What we’ve learned:
- Reflected XSS into HTML context with nothing encoded